Introducing MAX — Take supply chain cyber risk management to the MAX
Investigation into Breached Australian Organizations

Executive Summary
- In mid-March, two Australian financial and professional services firms reported data breaches.
- The SecurityScorecard Threat Research, Intelligence, Knowledge, and Engagement (STRIKE) Team investigated these incidents using SecurityScorecard’s products, Attack Surface Intelligence data, exclusive access to network flow (NetFlow) data, and publicly-available information.
- The available data suggests possible suspicious activity on both organizations’ networks.
- While this data does not offer conclusive information into the origins of the reported breaches, it suggests that attackers may have initially used phishing to compromise employee credentials. Some traffic may further suggest the reuse of these credentials.
Background
In mid-March, two Australian financial and professional services firms reported data breaches. These were followed by a series of cyber incidents affecting large Australian firms throughout 2022 and early 2023. As a result, some reporting on the incidents presented them as indications of systematic shortcomings in the country’s cyber defenses.
The affected financial services organization reported that threat actors were able to steal data by first compromising an employee’s credentials and then using them to access two service providers’ resources containing the customer data the attackers stole. This firm subsequently amended its initial estimate of the breach’s scope to disclose that it exposed fourteen million individuals’ private information. It further noted that the threat actor group claiming responsibility for the incident had attempted to hold the stolen data for ransom, but did not name the group in question.
Meanwhile, the other affected firm reported that its breach originated with a subsidiary, from which an unauthorized party accessed the firm’s document management system.
Methodology
Using access to network flow (NetFlow) data furnished by a strategic partner, SecurityScorecard’s STRIKE Team researchers sampled the traffic that occurred over roughly one month leading up to the breach disclosures and involved a group of IP addresses that SecurityScorecard’s ratings platform attributes to the affected organizations. Researchers selected those IP addresses where SecurityScorecard has observed issues, as these findings indicate that the assets they affect could be particularly vulnerable to malicious activity.
To identify which IP addresses within the traffic sample may merit further investigation, researchers first uploaded the IP addresses appearing in them to SecurityScorecard’s internal threat intelligence platform (TIP). This platform contains data from traffic samples collected during previous investigations into reported breaches, suspected ransomware attacks, disruptive events, and other cyber incidents. IP addresses appearing in multiple events’ traffic samples may be related to threat activity.
The STRIKE Team next filtered the traffic sample’s contents by byte count, isolating its largest data transfers. Large data transfers can represent exfiltration, so threat actors could have used the IP addresses receiving these transfers while stealing data from the affected organizations. Researchers then narrowed these results further by searching for the IP addresses in the public cybersecurity information-sharing platform VirusTotal, focusing on those addresses other cybersecurity vendors have already linked to malicious activity.
Having compiled a list of IP addresses worthy of closer attention, researchers returned to the original traffic samples to collect additional information about these IP addresses’ behavior in relation to the target organization and within the specific monitoring period. Then, they searched these IP addresses in SecurityScorecard’s Attack Surface Intelligence product and VirusTotal for additional context.
Finally, researchers looked for files containing the domains of the affected companies, including that of the subsidiary from which one of the breaches originated. Such files can offer insights into threat actors’ attempts to target the organizations whose domains they contain.
Findings: Communication with IP Addresses Appearing in SecurityScorecard’s Internal TIP
292 IP addresses from the affected organizations’ traffic samples have previously appeared in SecurityScorecard’s internal TIP. Of these, the vendors that contribute detections to VirusTotal have already deemed 127 malicious. In most cases, the behavior reflected within the traffic samples resembles low-level probing or scanning rather than activity related to the reported breaches; the strategic partner furnishing the NetFlow data has identified many of them as scanners and many others only briefly communicated with the target IP addresses and transferred small amounts of data to them. All 127 vendor-detected IP addresses are available in an appendix below.
The activity involving the IP addresses discussed at greater length below may offer additional insights into the incidents and could, in particular, reflect attempts to access target systems remotely.
45.232.73[.]84 and an IP address attributed to one of the affected organizations communicated via port 22 sixty times on March 3. Attack Surface Intelligence has revealed port 22 to be open and running a vulnerable version of OpenSSH at the organization-attributed IP address. Additionally, members of the VirusTotal community have observed 45.232.73[.]84 conducting brute force attacks against SSH services.
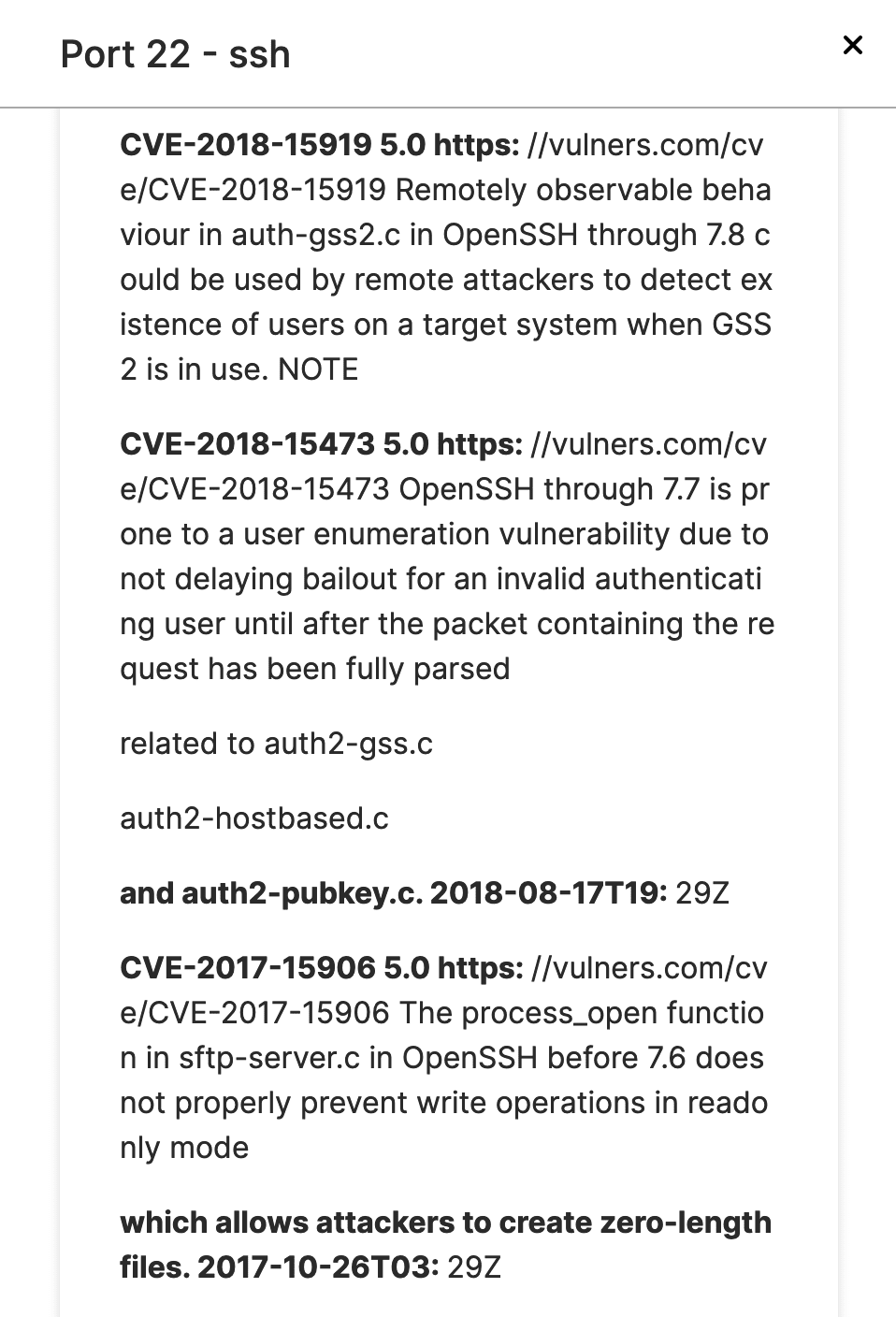
Image 1: Attack Surface Intelligence reflects the use of a version of OpenSSH that may be affected by numerous vulnerabilities at port 22 of an IP address attributed to a target organization.
Recurring communication over port 22 between these IP addresses could reflect attempts to access the target organization’s assets via SSH; in this context, it bears noting that forty-six other IP addresses (available in an appendix below) communicated with port 22 of the same IP address in the same period. Vendors have linked all of these IP addresses to malicious behavior. In total, these IP addresses were involved in 363 flows between February 12 and March 16; this would represent a smaller amount of communication than normally expected for brute force attacks, but if a login attempt were successful relatively early, it could account for a smaller overall number of flows from IP addresses linked to SSH brute force attempts.
An IP address attributed to one target organization and 173.199.15[.]254 communicated twenty-two times between February 13 and March 13. Remote access software company LogMeIn, Inc. is the organization that operates 173.199.15[.]254. While the software has many legitimate uses, threat actors often induce their targets to install legitimate remote access software (TeamViewer is especially common) on their devices to grant the attacker control, which can facilitate the deployment of ransomware. Traffic from a victim network to a LogMeIn-operated IP address may therefore reflect the attacker’s use of LogMeIn to control a victim device. 173.199.15[.]254 additionally appears in traffic samples collected from organizations affected by previous incidents. It is, therefore, possible that threat actors used this service for remote access to the affected organization.
Findings: Large Data Transfers
The traffic samples contain 118 IP addresses involved in large data transfers. Vendors have linked thirty-four of these to malicious activity. The majority of these IP addresses belong to hosting provider Digital Ocean. The traffic involving them could represent expected behavior (like transfers to and from backups). Still, given that threat actors have also abused these services in the past, these transfers may merit attention from personnel with internal visibility into the affected organizations’ networks. All IP addresses involved in these transfers are also available in an appendix below, but those linked to previous malicious activity may merit particular attention.
165.227.76[.]114 and 167.172.240[.]54, both of which communicated with one of the affected organizations, appear in VirusTotal collections titled “RemoteIPs,” which may suggest that other cybersecurity researchers have previously observed threat actors using them for remote access to target organizations.
A target organization IP address transferred approximately 3.19 MB to 138.197.169[.]210 on February 13. Many malicious files, some observed as recently as April 18, communicate with 138.197.169[.]210. Vendors detect the recently-observed file as ransomware, so communication between the target organization and 138.197.169[.]210 could reflect the operation of malware linked to the reported breach. The organization in question has disclosed that the actors responsible for the breach had attempted to hold company data for ransom, which likely indicates that the incident involved data theft and extortion and may suggest that the incident involved ransomware like that linked to the communicating file.
A different target organization IP address transferred approximately 12.29 MB to 46.101.13[.]77 on February 20. Approximately 2,600 files submitted to VirusTotal, many of them malicious, communicate with 46.101.13[.]77. A transfer to this IP address from one attributed to a recently-breached organization may reflect malware activity similar to that of the communicating files observed in VirusTotal.
Findings: Potentially Malicious Files Containing Target Domains
A file uploaded to VirusTotal on March 3 contains an email address from the subsidiary where one of the breaches originated and may reflect phishing targeting that company. One vendor detects this file as “HTML.Redirector.86”, and it contains the following URL: hxxps://cloudflare-ipfs.com/ipfs/QmQZ7b23pLVaaS8pYiWeZSD6QbAV4yePkhprG2buG9rrLN#[employee.name]@[subsidiaryname].com.
That URL, in turn, serves downloads of a file twenty-eight vendors have linked to phishing or otherwise detected as malicious. This could reflect activity that resulted in the breach, as threat actors could have leveraged credentials stolen through phishing to access the data exposed in the breach.
Conclusion
While this data does not offer definitive evidence about the origins of the reported breaches, it suggests that attackers may have initially used phishing to compromise employee credentials and some traffic may further suggest the reuse of these credentials.
The file discussed above could have enabled credential theft and subsequent traffic involving IP addresses linked to brute force attacks could reflect the reuse of these credentials alongside others as part of a brute force attempt. The large data transfers may further reflect exfiltration in which the earlier stages of the attack culminated.
Although SecurityScorecard cannot verify these hypotheses without internal visibility into the affected organizations’ networks, the available data appears to suggest them. The STRIKE Team could, moreover, furnish this data to the affected organizations upon request, should they determine that such data would aid their investigation.
Appendices:
VENDOR-DETECTED IP ADDRESSES APPEARING IN PREVIOUS INCIDENTS’ TRAFFIC SAMPLES
- 45[.]232[.]73[.]46
- 89[.]203[.]249[.]67
- 157[.]230[.]83[.]80
- 159[.]89[.]230[.]196
- 142[.]93[.]8[.]99
- 147[.]182[.]202[.]179
- 154[.]68[.]232[.]20
- 46[.]101[.]179[.]127
- 67[.]205[.]162[.]78
- 137[.]184[.]183[.]59
- 104[.]248[.]220[.]162
- 45[.]232[.]73[.]54
- 132[.]248[.]65[.]8
- 137[.]184[.]104[.]77
- 104[.]248[.]20[.]85
- 200[.]17[.]114[.]130
- 159[.]65[.]181[.]157
- 164[.]92[.]114[.]247
- 137[.]184[.]13[.]100
- 104[.]131[.]91[.]148
- 104[.]248[.]31[.]56
- 67[.]207[.]83[.]244
- 206[.]189[.]0[.]60
- 159[.]89[.]95[.]98
- 164[.]92[.]157[.]100
- 68[.]183[.]53[.]77
- 107[.]170[.]247[.]16
- 167[.]71[.]33[.]249
- 104[.]236[.]111[.]25
- 188[.]166[.]41[.]217
- 159[.]203[.]113[.]193
- 164[.]92[.]106[.]15
- 134[.]209[.]126[.]50
- 159[.]203[.]208[.]8
- 178[.]62[.]64[.]242
- 167[.]71[.]136[.]141
- 159[.]223[.]129[.]133
- 147[.]182[.]171[.]152
- 45[.]232[.]73[.]51
- 198[.]199[.]110[.]69
- 134[.]209[.]187[.]199
- 192[.]241[.]221[.]18
- 143[.]198[.]68[.]20
- 170[.]210[.]203[.]211
- 102[.]221[.]249[.]148
- 192[.]241[.]232[.]27
- 192[.]241[.]197[.]61
- 147[.]182[.]185[.]145
- 170[.]210[.]155[.]249
- 146[.]190[.]220[.]33
- 67[.]205[.]140[.]79
- 162[.]243[.]133[.]10
- 159[.]223[.]106[.]55
- 103[.]232[.]121[.]81
- 45[.]232[.]73[.]84
- 157[.]245[.]44[.]219
- 161[.]35[.]213[.]124
- 159[.]203[.]25[.]103
- 206[.]189[.]201[.]198
- 165[.]227[.]89[.]45
- 161[.]35[.]13[.]19
- 198[.]54[.]128[.]109
- 173[.]233[.]161[.]109
- 67[.]205[.]169[.]214
- 143[.]110[.]239[.]2
- 192[.]241[.]198[.]16
- 154[.]68[.]199[.]27
- 164[.]90[.]138[.]233
- 102[.]221[.]248[.]178
- 142[.]93[.]188[.]216
- 138[.]197[.]0[.]92
- 137[.]184[.]60[.]119
- 198[.]199[.]77[.]231
- 45[.]227[.]112[.]218
- 157[.]230[.]216[.]218
- 159[.]223[.]137[.]120
- 147[.]182[.]182[.]55
- 138[.]197[.]174[.]67
- 46[.]101[.]13[.]77
- 164[.]90[.]160[.]21
- 134[.]209[.]118[.]223
- 102[.]221[.]249[.]156
- 103[.]143[.]143[.]48
- 103[.]26[.]139[.]91
- 137[.]184[.]58[.]169
- 27[.]0[.]183[.]209
- 47[.]251[.]15[.]21
- 131[.]108[.]156[.]113
- 160[.]238[.]136[.]117
- 157[.]245[.]86[.]51
- 104[.]131[.]160[.]65
- 165[.]227[.]223[.]189
- 159[.]223[.]152[.]0
- 167[.]99[.]52[.]229
- 134[.]209[.]121[.]118
- 159[.]65[.]255[.]251
- 206[.]189[.]96[.]249
- 154[.]68[.]199[.]42
- 206[.]189[.]247[.]132
- 180[.]233[.]120[.]94
- 103[.]143[.]143[.]168
- 167[.]71[.]164[.]97
- 164[.]92[.]213[.]94
- 102[.]220[.]15[.]172
- 185[.]33[.]34[.]26
- 64[.]225[.]16[.]177
- 193[.]1[.]12[.]167
- 216[.]6[.]37[.]10
- 144[.]126[.]248[.]223
- 102[.]221[.]249[.]96
- 146[.]190[.]199[.]58
- 192[.]33[.]214[.]47
- 116[.]90[.]228[.]235
- 202[.]51[.]181[.]142
- 131[.]108[.]159[.]180
- 116[.]90[.]227[.]242
- 192[.]42[.]42[.]154
- 37[.]205[.]32[.]230
- 192[.]33[.]214[.]57
- 118[.]179[.]246[.]92
- 157[.]245[.]141[.]244
- 64[.]225[.]50[.]135
- 137[.]184[.]64[.]194
- 165[.]232[.]90[.]69
- 89[.]203[.]249[.]98
- 173[.]199[.]15[.]254
IP ADDRESSES COMMUNICATING WITH VULNERABLE ORGANIZATION IP ADDRESS OVER PORT 2
- 143[.]244[.]178[.]40
- 159[.]203[.]113[.]193
- 202[.]125[.]83[.]238
- 154[.]68[.]232[.]20
- 157[.]230[.]83[.]80
- 159[.]65[.]91[.]105
- 161[.]35[.]13[.]19
- 164[.]90[.]166[.]22
- 134[.]209[.]187[.]199
- 164[.]92[.]157[.]100
- 137[.]184[.]81[.]127
- 132[.]248[.]65[.]8
- 103[.]232[.]121[.]81
- 165[.]227[.]111[.]218
- 167[.]71[.]33[.]249
- 174[.]138[.]72[.]191
- 45[.]232[.]73[.]84
- 134[.]209[.]8[.]231
- 159[.]89[.]108[.]180
- 161[.]35[.]91[.]83
- 64[.]227[.]122[.]198
- 200[.]17[.]114[.]130
- 134[.]209[.]126[.]50
- 137[.]184[.]183[.]59
- 147[.]182[.]185[.]145
- 143[.]198[.]160[.]232
- 147[.]182[.]228[.]52
- 154[.]68[.]225[.]162
- 188[.]166[.]41[.]217
- 157[.]245[.]128[.]85
- 46[.]101[.]179[.]127
- 165[.]227[.]142[.]14
- 170[.]210[.]155[.]249
- 198[.]54[.]128[.]38
- 165[.]232[.]121[.]37
- 164[.]92[.]246[.]143
- 170[.]210[.]203[.]211
- 67[.]207[.]83[.]244
- 147[.]182[.]171[.]152
- 104[.]248[.]31[.]56
- 104[.]131[.]91[.]148
- 167[.]71[.]136[.]141
- 161[.]35[.]24[.]244
- 104[.]248[.]20[.]85
- 198[.]54[.]128[.]109
- 137[.]184[.]104[.]77
- 104[.]236[.]111[.]25
IP ADDRESSES INVOLVED IN LARGE DATA TRANSFERS
- 67[.]207[.]72[.]71
- 167[.]99[.]52[.]229
- 157[.]230[.]85[.]253
- 116[.]90[.]59[.]176
- 157[.]230[.]89[.]209
- 167[.]172[.]231[.]60
- 64[.]225[.]1[.]58
- 167[.]172[.]240[.]41
- 67[.]205[.]138[.]90
- 64[.]225[.]9[.]37
- 72[.]3[.]171[.]114
- 142[.]93[.]53[.]200
- 69[.]55[.]49[.]248
- 138[.]68[.]226[.]62
- 104[.]131[.]32[.]51
- 134[.]213[.]80[.]13
- 139[.]59[.]199[.]38
- 72[.]32[.]131[.]23
- 159[.]223[.]150[.]165
- 165[.]22[.]12[.]234
- 157[.]230[.]89[.]254
- 157[.]245[.]223[.]249
- 103[.]62[.]38[.]34
- 98[.]129[.]118[.]207
- 157[.]245[.]86[.]51
- 138[.]68[.]61[.]224
- 64[.]225[.]50[.]135
- 159[.]89[.]246[.]130
- 146[.]190[.]223[.]190
- 143[.]198[.]7[.]33
- 138[.]197[.]80[.]154
- 143[.]198[.]3[.]241
- 167[.]71[.]87[.]161
- 167[.]71[.]165[.]23
- 159[.]203[.]67[.]117
- 142[.]93[.]204[.]192
- 67[.]205[.]168[.]237
- 119[.]9[.]108[.]191
- 24[.]199[.]86[.]5
- 142[.]93[.]88[.]15
- 139[.]59[.]161[.]189
- 165[.]227[.]114[.]254
- 134[.]209[.]118[.]223
- 134[.]209[.]121[.]118
- 68[.]183[.]212[.]230
- 147[.]182[.]182[.]55
- 134[.]213[.]160[.]147
- 157[.]230[.]93[.]231
- 147[.]182[.]160[.]142
- 104[.]236[.]33[.]200
- 198[.]211[.]101[.]32
- 164[.]92[.]213[.]94
- 146[.]20[.]176[.]192
- 108[.]166[.]30[.]181
- 68[.]183[.]118[.]113
- 204[.]48[.]20[.]248
- 164[.]90[.]143[.]171
- 119[.]9[.]108[.]180
- 178[.]62[.]106[.]90
- 206[.]189[.]243[.]5
- 104[.]248[.]120[.]134
- 146[.]20[.]128[.]101
- 159[.]223[.]152[.]0
- 143[.]198[.]164[.]162
- 134[.]213[.]221[.]227
- 103[.]44[.]34[.]135
- 46[.]101[.]13[.]77
- 134[.]122[.]16[.]106
- 134[.]209[.]117[.]245
- 162[.]243[.]163[.]45
- 147[.]182[.]141[.]172
- 147[.]182[.]140[.]74
- 159[.]203[.]25[.]103
- 104[.]248[.]232[.]179
- 119[.]9[.]108[.]211
- 206[.]189[.]0[.]60
- 146[.]190[.]199[.]58
- 184[.]106[.]10[.]77
- 64[.]225[.]16[.]177
- 162[.]243[.]150[.]9
- 143[.]198[.]68[.]20
- 68[.]183[.]117[.]137
- 167[.]172[.]133[.]224
- 142[.]93[.]65[.]171
- 165[.]227[.]76[.]114
- 157[.]245[.]143[.]218
- 178[.]62[.]12[.]52
- 198[.]211[.]109[.]100
- 45[.]55[.]62[.]201
- 134[.]209[.]26[.]59
- 157[.]245[.]92[.]141
- 137[.]184[.]197[.]118
- 144[.]126[.]228[.]62
- 162[.]243[.]164[.]77
- 167[.]172[.]17[.]193
- 147[.]182[.]145[.]49
- 157[.]230[.]12[.]202
- 159[.]65[.]60[.]123
- 165[.]232[.]33[.]163
- 134[.]209[.]89[.]106
- 157[.]230[.]29[.]126
- 45[.]55[.]66[.]33
- 164[.]92[.]179[.]10
- 167[.]172[.]240[.]54
- 134[.]122[.]60[.]50
- 137[.]184[.]156[.]75
- 137[.]184[.]222[.]107
- 164[.]90[.]148[.]5
- 134[.]122[.]20[.]189
- 167[.]99[.]248[.]77
- 138[.]197[.]169[.]210
- 134[.]209[.]201[.]18
- 164[.]92[.]132[.]174
- 134[.]122[.]23[.]52
- 159[.]203[.]70[.]236
- 142[.]93[.]147[.]109
- 161[.]35[.]156[.]237
- 103[.]44[.]35[.]157


