Transform vendor discovery into Supply Chain Detection
Leverage unmatched visibility, structured intelligence, and actionable insights to take control of third- and fourth-party risk. With automated vendor mapping, real-time exposure alerts, and seamless triage workflows, taking action on hidden supply chain threats become clear, evidence-backed decisions.
Discover Hidden Risks
Attackers are leveraging advanced techniques and AI-driven reconnaissance to identify and exploit the weakest links in your extended supply chain. Once inside any organization in your ecosystem—third or even fourth-party—they exploit the implicit trust between connected systems to reach their true target: you.
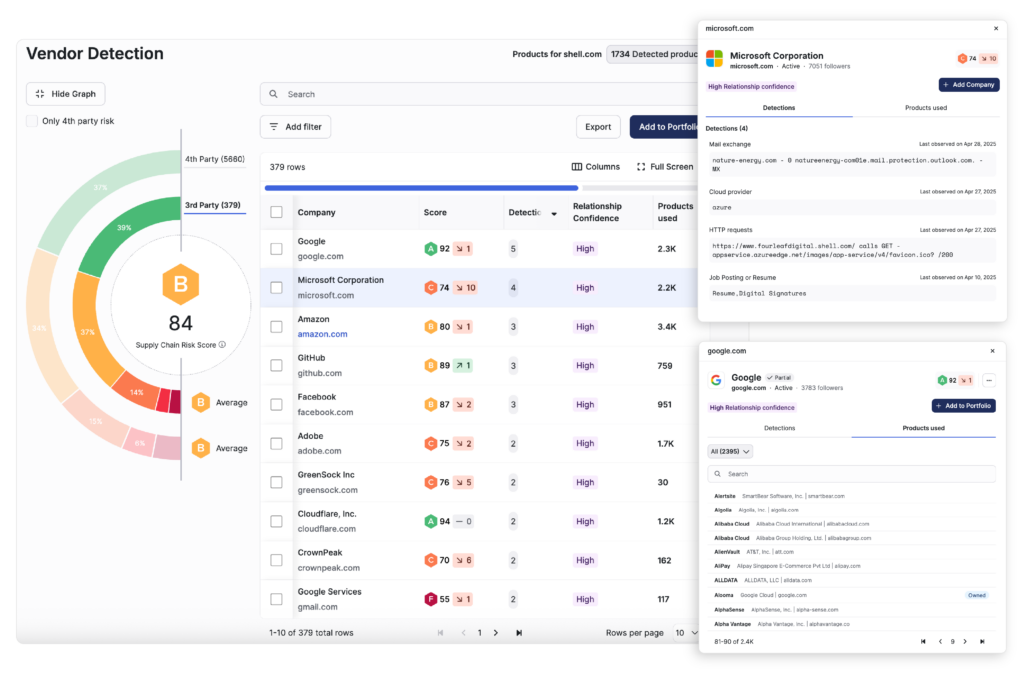
Automatic Vendor Detection enhances vendor identification to detect previously unknown vendors in and across your entire ecosystem so you can see the risk and take action.
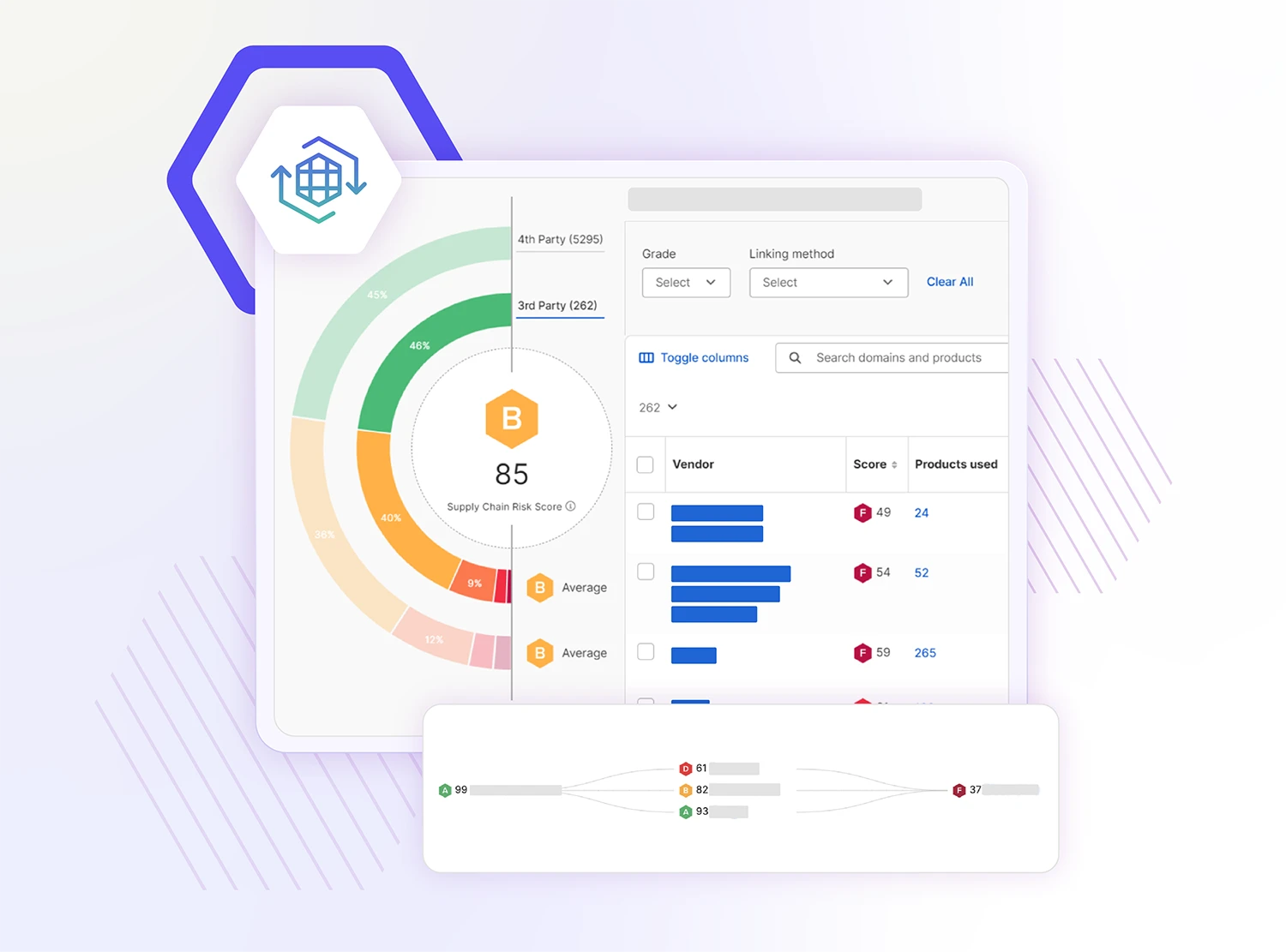
A View Inside
Uncover critical cyber risks hiding in plain sight with automated vendor identification.


Gain a Complete View
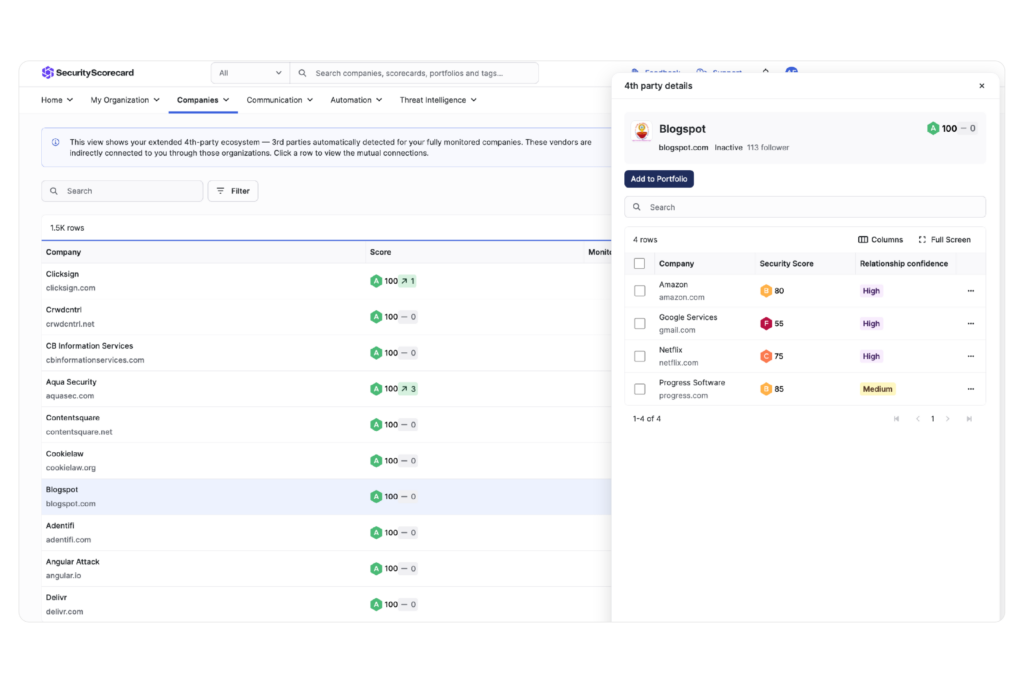
- Visualize your full vendor landscape: Automatically uncover third- and fourth-party connections, including hidden relationships and dependencies, to proactively mitigate concentration and systemic risks.
- Better understand vendor relationships: Leverage confidence scores to assess the strength and relevance of each vendor connection for more precise risk analysis.
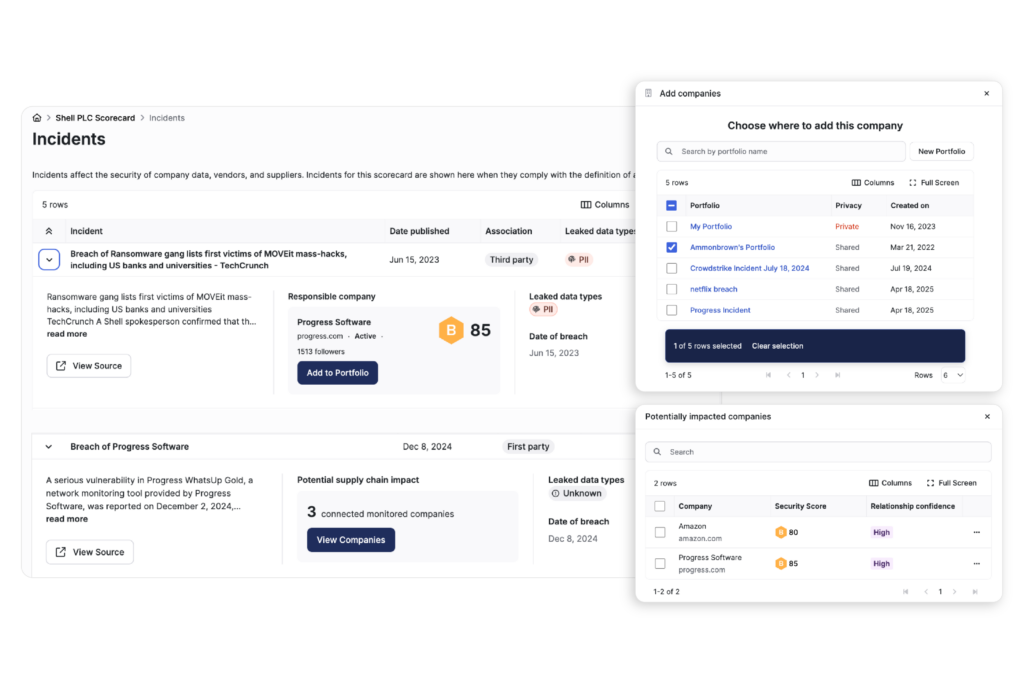
- Swiftly respond to vendor risks during a breach: AVD integrates with SecurityScorecard’s Incidents Page, providing real-time breach insights so you can immediately assess potential supply chain impact and take action.
- Make informed moves: Layered detection and enriched evidence give you clarity on where to act, reducing uncertainty in your risk decisions.
- Maximize ROI with streamlined workflows: Spend less time digging through data and more time collaborating with vendors and resolving critical issues.
Critical Capabilities
-

Reveal Hidden Vendor Relationships
Automatically detect third- and fourth-party vendors and validate connections with Relationship Confidence Scores for a clearer view of your supply chain.
-
Illuminate Product Usage Across Tiers
Identify technologies used by third- and fourth-party vendors to uncover concentration risks and improve oversight.
-

Real-Time Risk Monitoring & Threat Intelligence
Monitor vendors for breaches, ransomware, and data exposures using real-time threat intelligence and shared data insights.
-

Streamlined Oversight with Actionable Insights
Quickly filter, search, and manage vendors with a user-friendly interface that highlights risk posture and enables easy portfolio tracking.
Hear From Our Customers
-
“SecurityScorecard has allowed me and my team to automate and scale many of the functions of our vendor risk management program as well as continuously monitor their internal and third-party security posture.”
Chief Information Security Officer, Virgin Pulse1 / 0
Explore More
There is much more to the SecurityScorecard platform