How telecom companies safeguard against cyber threats
Protect your telecommunications business against cyber threats. Safeguard sensitive data and fortify your network to stay resilient against potential attacks.

Telecom companies protect their supply chain from cyber threats with SecurityScorecard
Telecommunication companies, internet service providers, and cloud providers (TICPs) are a pillar of modern connectivity, linking people and companies across the globe. This inherently makes them prime targets for nation-state actors and motivated cybercrime groups. TICPs leveraging SecurityScorecard gain immediate insights, enabling proactive measures to minimize the risk of breaches arising from vendors and business partners.
-
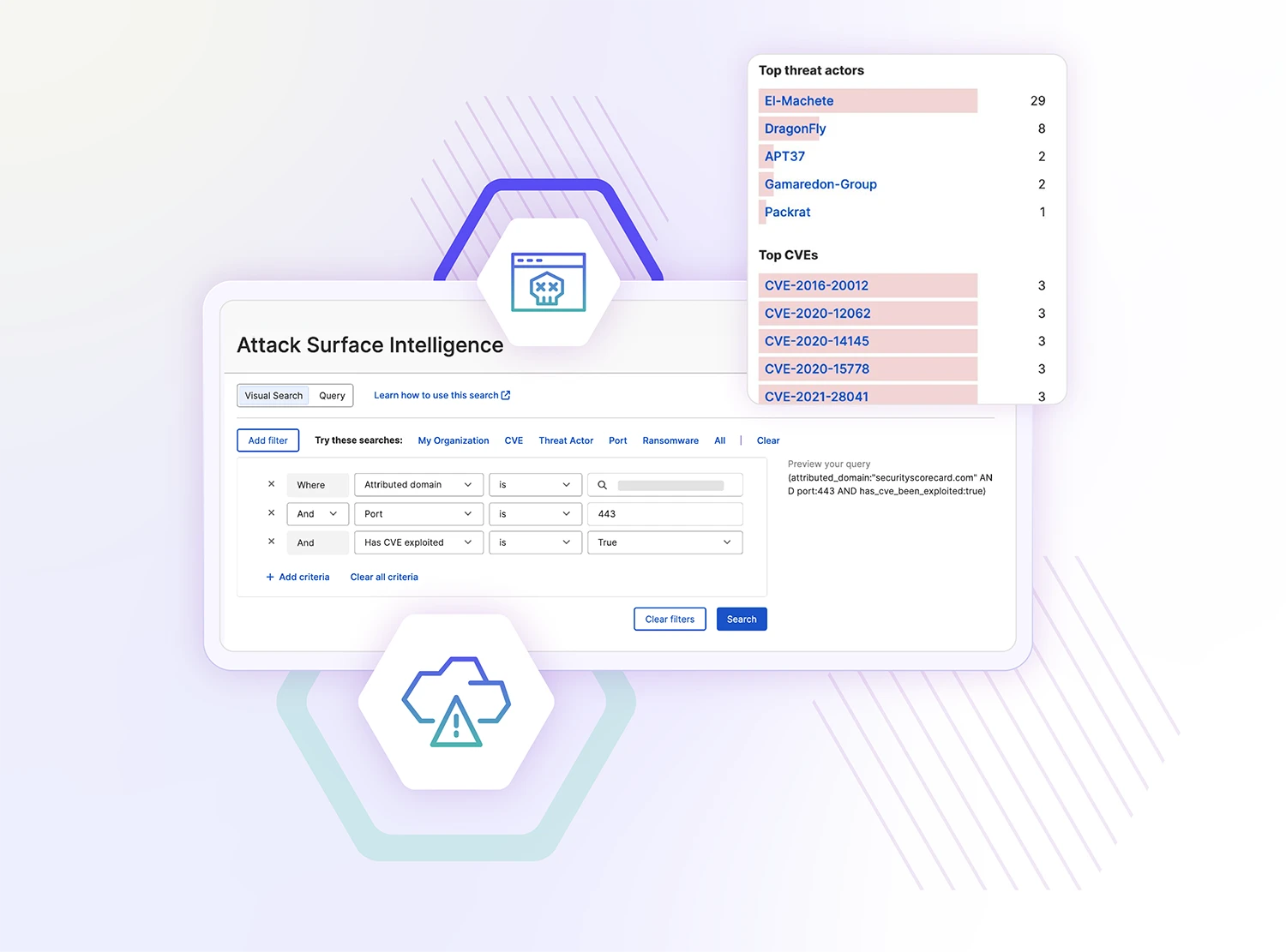
Protect your attack surface from cyber threats
Learn how cyber risks impact your security rating and prioritize mitigation efforts to improve your cybersecurity posture. SecurityScorecard empowers you with customizable remediation plans so you can take your telecom business on the path towards meeting your goals.
-
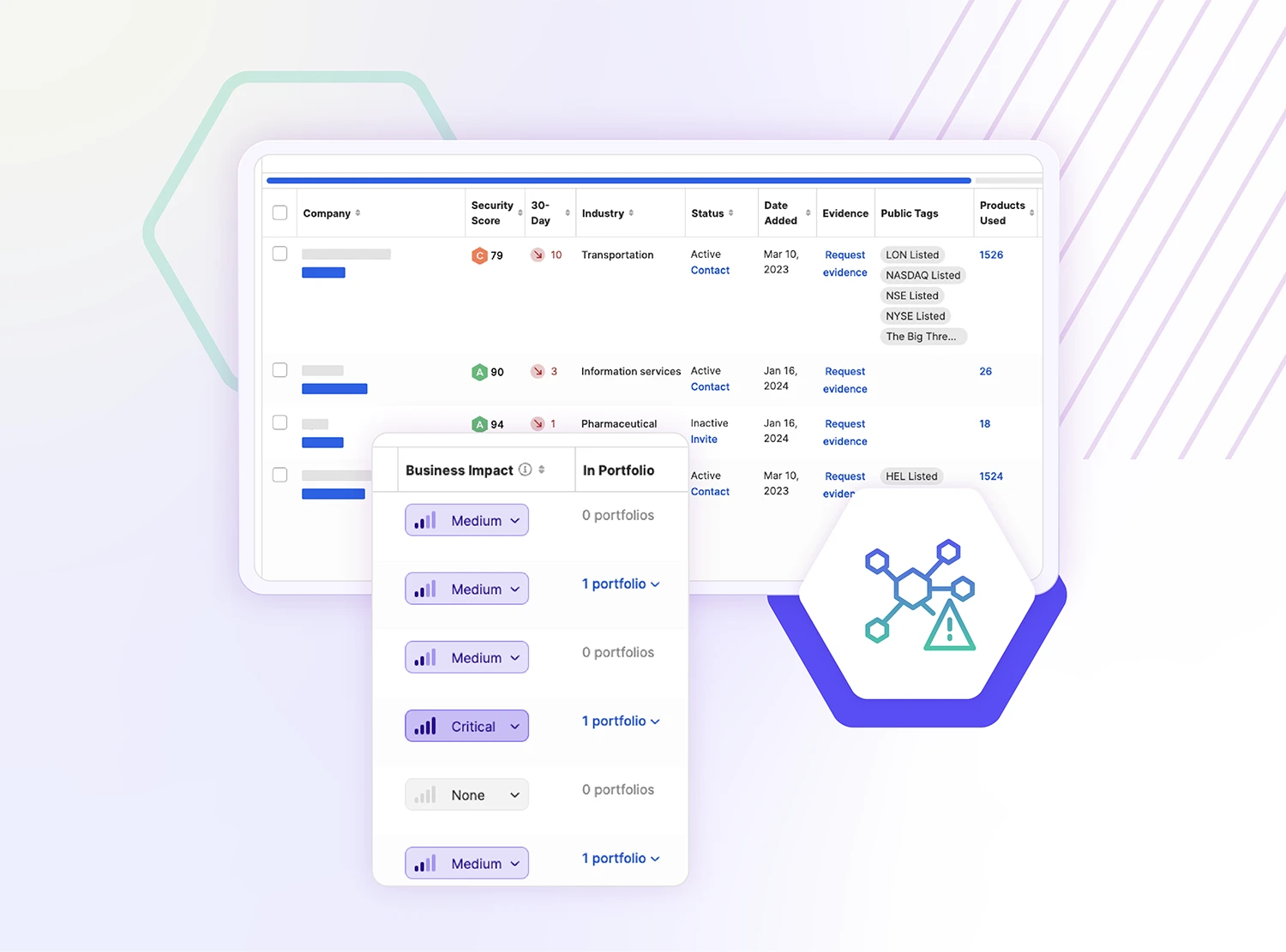
Discover threats in your supply chain
Vendors in your supply chain often lead to cyber incidents. That’s why over 3,000 customers rely on SecurityScorecard to identify and resolve cybersecurity issues across their supplier ecosystem.
-
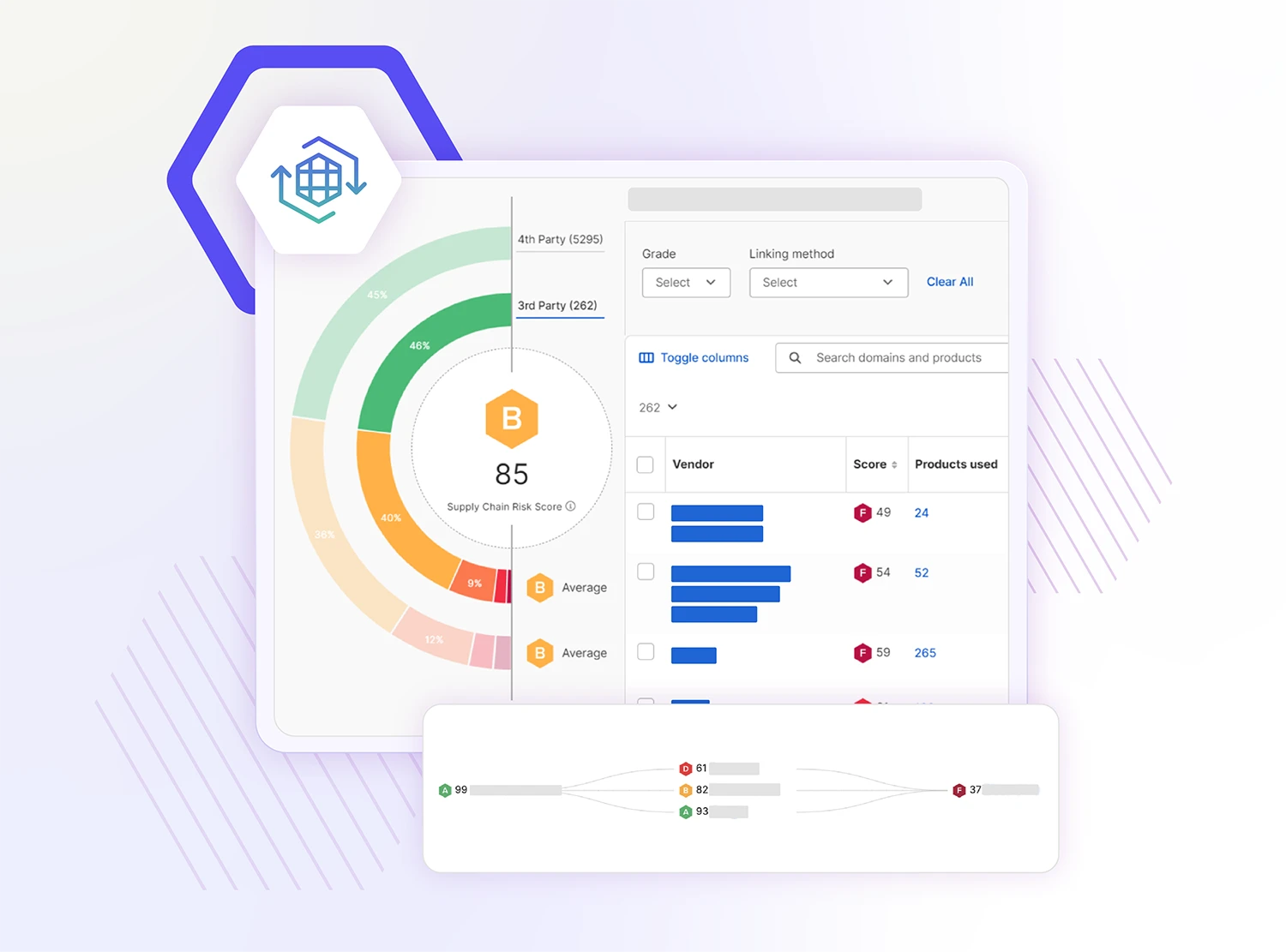
Uncover cyber risks across your vendor ecosystem
Determine your third-party supply chain to discover previously unknown cyber risks in your fourth-party network. See how your business is connected to high-risk suppliers, better understand the risks, and build plans to safeguard your telecom operations.
-
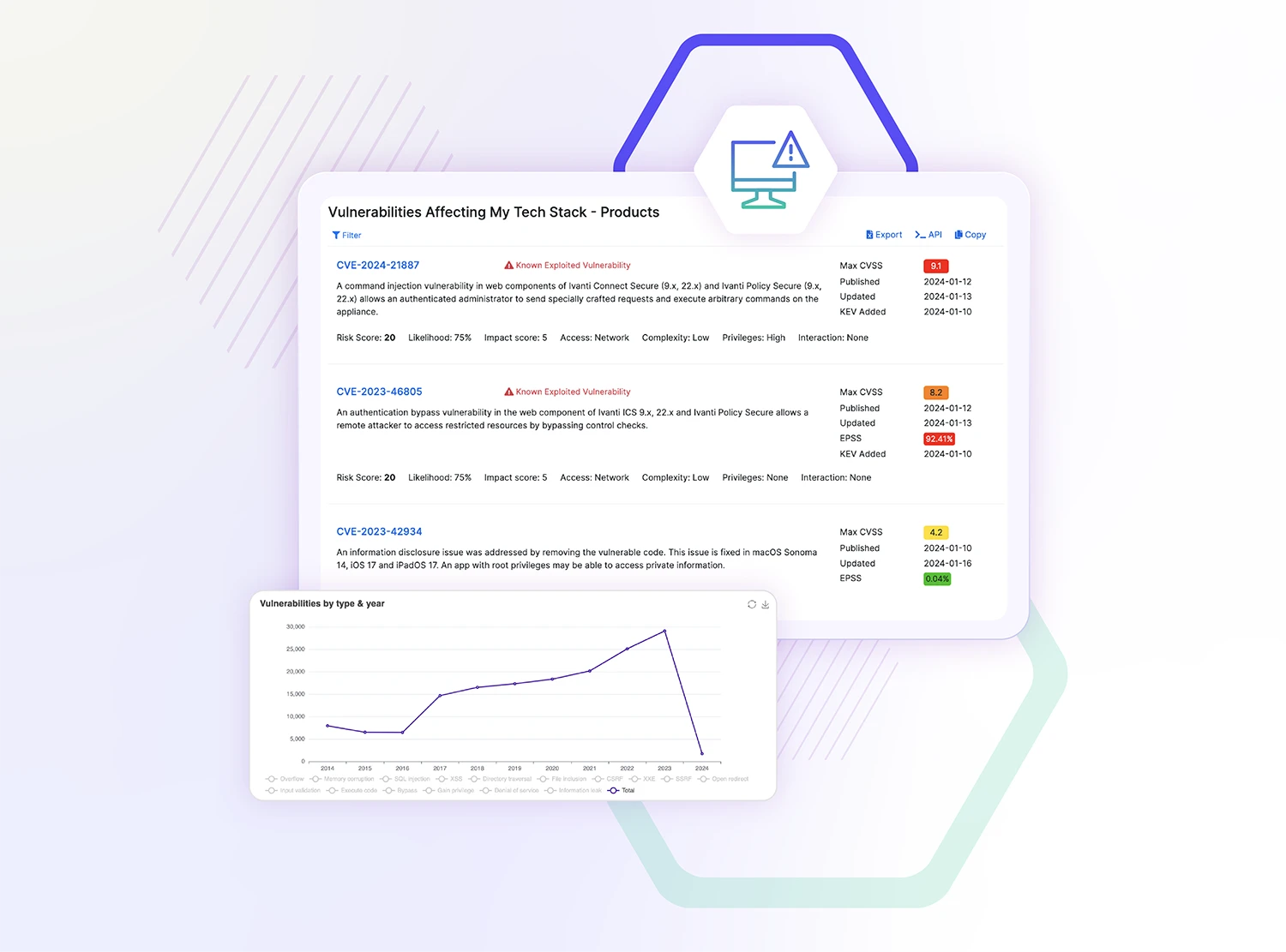
Empower your security response
Reduce time-consuming research and improve your response to emerging vulnerabilities. Quickly make prioritization and remediation decisions, take action to bolster your systems against vulnerabilities, and stay a step ahead of potential threats.
Hear from our customers
-
“SecurityScorecard has allowed me and my team to automate and scale many of the functions of our vendor risk management program as well as continuously monitor their internal and third-party security posture.”
Virgin Pulse Chief Information Security Officer1 / 0