Cybersecurity trust and transparency
SecurityScorecard is the only security ratings company that publishes live metrics on response time, refute rate, IP, and domain misattribution rates.

The largest proprietary risk and
threat intelligence dataset on the planet
Numbers updated in real time
-
Security Issues
Discovered Today

-

Companies
rated

-

Unique companies
followed

-

Active users
today

Refutes and accuracy
Any organization — at no cost — can always access and improve their security rating
-

Refute response time
SecurityScorecard responds to refute requests within 48 hours.
-

Findings refute rate
SecurityScorecard’s False Positive Rate is under 1%.
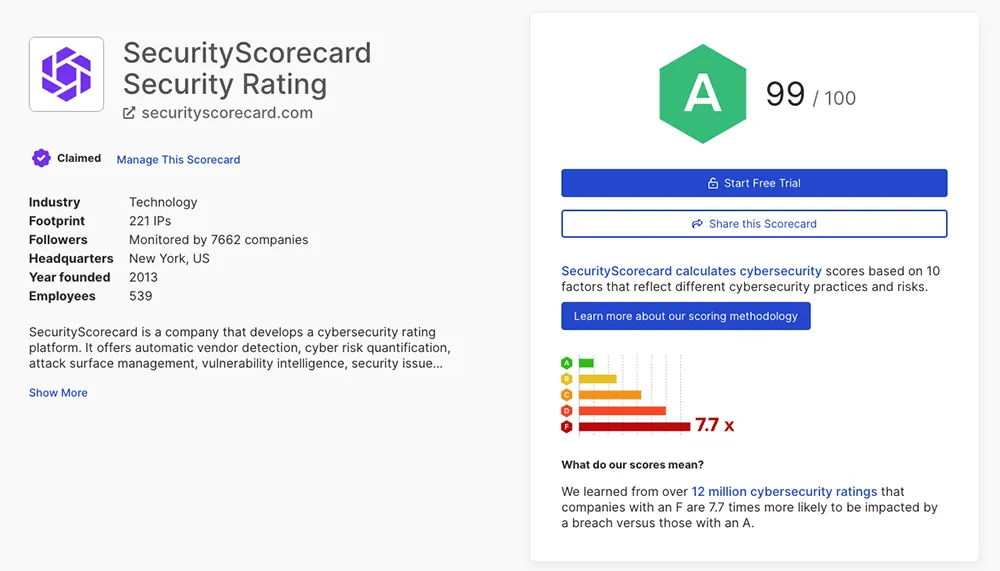
Response times and findings
Digital footprint metrics
IP MISATTRIBUTION RATE
This chart shows how long SecurityScorecard takes to respond to and resolve refute requests. (Response time displayed in hours, as a 7-day trailing average)DOMAIN MISATTRIBUTION RATE
Refute rate for scored findings.


Our mission
We make the world a safer place by transforming the way the world measures and manages cybersecurity risk across the entire digital ecosystem.
Data Transparency
We own 99% of our data in-house to deliver unparalleled accuracy and speed. Companies with an F rating are 13.8x more likely to get breached.
-
Data Sources
- IP addresses
- Exposed port mappings
- Fingerprints of services, products, libraries, operating systems, devices, and other internet-exposed resources, including version numbers
- Common Platform Enumeration (CPE) IDs
- Common Vulnerability Enumeration (CVE) Version 2 IDs
- Script output from Nmap, the open-source scanner that is one of the components of our own scanning framework

-
Scanning
We collect and own 99% of our own data.
- 4.1B IPs
- 1,400 ports globally
- Honeypots globally
- 12M companies monitored
- 100B vulnerabilities weekly

-
Signals
We monitor signals using a network of sensors spanning three continents.
- World’s largest network of sinkholes and honeypots
- Enriched with commercial and open-source intelligence

About our data
-
How we collect data
We have our own attribution and threat intelligence teams, who source almost all of the data we use (99%).
All of the data we use is ethically and lawfully obtained. We only collect data on entities, not on people.

-
How we score our findings
SecurityScorecard developed its breach prediction algorithm by using LLMs to analyze the root cause of 15,000 historical breaches.

-
How we validate our findings
We use multiple mechanisms to check our data quality:
- We monitor corrections from our users, which we aim to keep below thresholds.
- We look for patterns in corrections to deal with any underlying issues.
- We spot check attribution and findings data.
Any company can validate our findings, IP, and domain attributions to ensure their digital footprint is accurate.

-
Scoring and attribution changes
SecurityScorecard is committed to providing advanced notice of scoring enhancements. Before changes are released, they must go through a Change Committee board and undergo impact assessments.

Our Principles
SecurityScorecard fosters cybersecurity trust and transparency. We continuously rate more than 12 million entities worldwide by empowering organizations to contribute and verify their security ratings for free.

Collaboration: Our path to a safer world
Trust and transparency are built into all of our products and services from the moment an organization registers for a free account. SecurityScorecard believes cybersecurity is a collective responsibility, and everyone should have a voice in ensuring the accuracy of security ratings.
-
How we score
SecurityScorecard is the only company to provide complete transparency into our scoring methodology
-
Accuracy & attribution
A team of independent experts from Online Business Systems validated our methodology
-
Market validation
Marsh McLennan examined cybersecurity ratings’ correlation with reduced cyber insurance risk