Introducing MAX — Take supply chain cyber risk management to the MAX
Cyber Risk Intelligence Update: STRIKE Team Investigation Identifies Possible Flax Typhoon Links to Higher Education

Executive Summary
- The SecurityScorecard Threat Research, Intelligence, Knowledge, and Engagement (STRIKE) Team conducted further research into indicators of compromise (IoCs) connected to the China-backed Flax Typhoon threat actor group. This has revealed additional IP addresses the group may use.
- A strategic partner’s network flow (NetFlow) data indicated repeated communication between four Chinese IP addresses and an IP address the STRIKE Team previously linked to Flax Typhoon.
- These IP addresses suggest a link between Flax Typhoon and a Chinese institution of higher education, Fudan University.
- The following are the additional, possibly Flax Typhoon-linked IP addresses attributed to Fudan University:
- 202.120.224[.]129
- 202.120.224[.]82
- 202.120.224[.]114
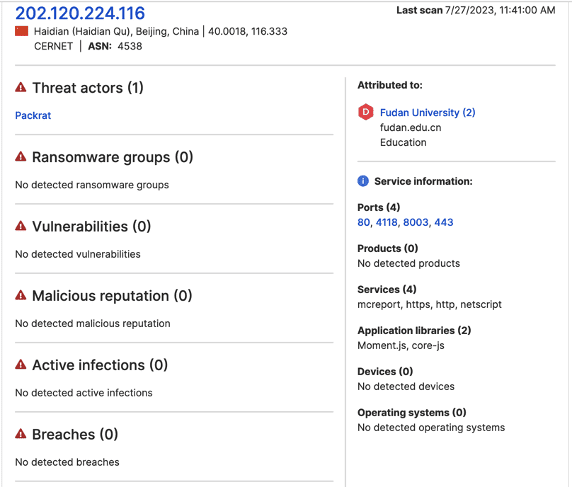
- 202.120.224[.]116
- The following are the additional, possibly Flax Typhoon-linked IP addresses attributed to Fudan University:
- Concerns about Fudan University’s possible role in PRC influence and intelligence operations have previously surfaced in public commentary. These findings may contribute to similar concerns in the cyber domain.
Background
Following Microsoft’s identification of Flax Typhoon, a new threat actor group believed to conduct espionage on behalf of the People’s Republic of China (PRC), the STRIKE Team used SecurityScorecard’s data to investigate the IoCs Microsoft supplied in its report. This investigation yielded a collection of new IP addresses featuring the same TLS certificates that Microsoft linked to Flax Typhoon.
Following this initial research, the STRIKE Team investigated these newly-identified Flax Typhoon resources further, using a strategic partner’s NetFlow data to sample the traffic involving them. During this subsequent research, the STRIKE Team observed a group of Chinese IP addresses communicating with one of the IP addresses SecurityScorecard previously linked to Flax Typhoon. Given Flax Typhoon’s reported role in PRC-backed espionage, the STRIKE Team conducted further research into these Chinese IP addresses to assess the possibility that they too are Flax Typhoon resources.
Findings
The NetFlow data that the STRIKE Team collected revealed repeated communication between an IP address that appears to host a VPN service used by Flax Typhoon (45.204.1[.]203) and four Chinese IP addresses:
- 202.120.224[.]129
- 202.120.224[.]82
- 202.120.224[.]114
- 202.120.224[.]116
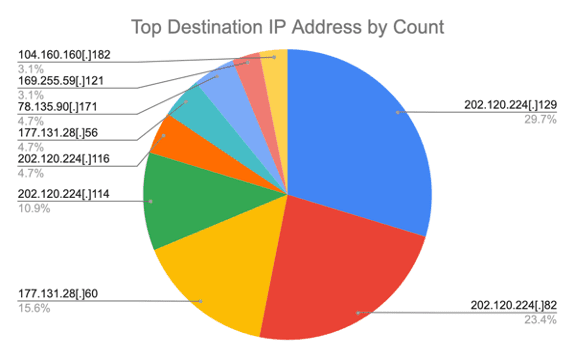
Researchers next consulted SecurityScorecard’s Attack Surface Intelligence tool to gather additional information about these IP addresses, noting a link between each IP address and Fudan University.
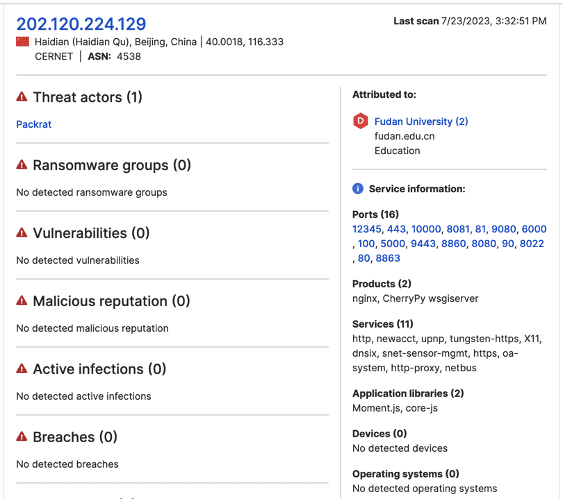
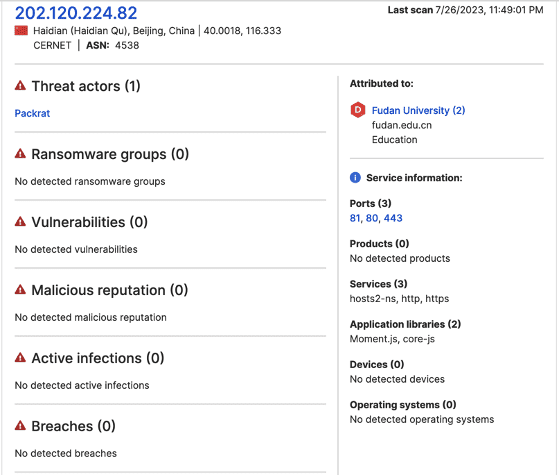
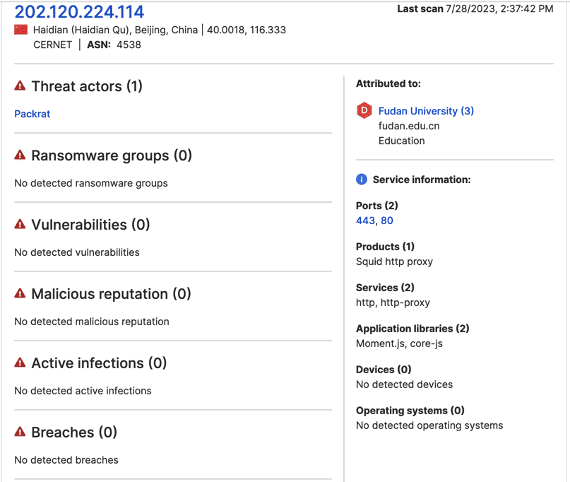
The STRIKE Team next collected publicly available information about Fudan University and noted that concerns about the university’s possible role in PRC intelligence and influence operations have recurred in Western coverage since at least 2011. The traffic data suggesting a link to a new China-linked threat actor group may offer further indication that these claims are well-grounded.
A 2011 article in the Telegraph regarding the establishment of new “spy schools” by the PRC noted that Fudan University hosted one such Intelligence College. It further quoted a University spokesperson, who explained that the College would “use Fudan’s existing computer science, law, management, journalism and sociology resources” to respond “to the urgent need for special skills to conduct intelligence work in the modern era.”
Later, a report on the links between Chinese universities and PRC-backed advanced persistent threat (APT) activity, which Georgetown University’s Center for Security and Emerging Technology published in March 2021, noted collaboration between Fudan University and Zheijiang University, another Chinese university with clearer ties to PRC-backed APTs. The report noted that a team composed of students from the two universities defeated a team of US-based students in DEFCON’s 2020 capture-the-flag (CTF) competition. As with many events that year, DEFCON took place remotely in 2020. This may have made the event more accessible by enabling attendees normally unable to travel to an in-person event in Las Vegas to participate remotely, but this increased accessibility may have also extended to actors with links to nation-state adversaries.
While the Georgetown report does not discuss further links between Fudan University and specific Chinese APT groups, it does note that APT1 had previously recruited students from Zheijiang University (the other university that contributed students to the DEFCON CTF team) and that the University had received funding from PRC national security projects including the National 242 Information Security Program, the Ministry of State Security 115 Program, and the National s219 Information Security Application Demonstration Project.
Reports that Fudan University intended to open a satellite campus in Budapest, Hungary also surfaced in 2021. These plans raised concerns, both in news media and the European Parliament, that the campus could enable espionage or influence operations by the PRC. One member of the European Parliament posed a series of questions regarding the establishment of Fudan’s Budapest campus to the European Commission on May 27, 2021, that concluded with the following: “Does the Commission consider Fudan University, or any other Chinese Communist Party-backed university development, to pose any form of threat to national security through Chinese espionage?” The European Commission’s response appeared to recognize the validity of such concerns (though not commenting on them directly), by noting, “Chinese influence and interference activities in Europe have steadily grown over the past years, including through engagement with academia.”
Conclusion
These findings suggest that the group’s activities reflect broader trends in PRC cyber activity like those discussed in the U.S. Department of Defense’s recently-published 2023 Cyber Strategy. The Strategy identifies the PRC as a “a broad and pervasive cyber espionage threat” to the U.S. and its allies and partners, noting that “effective state control” over its cybersecurity industry and “a large technology industry and workforce” both contribute to its capabilities.
Microsoft’s initial report on Flax Typhoon notes that it, like the more general PRC cyber activity discussed in the Strategy, has critical infrastructure in U.S. partner states. Some public reporting on Fudan University, meanwhile, suggests that its programs and students may have contributed to the development of the PRC’s cyber capabilities and workforce. The findings suggesting a link between Flax Typhoon and Fudan University may therefore reflect an overlap between the two dimensions of PRC cyber activity noted above (its strategic focus on particular industries and regions and its pursuit of advantages in cyberspace using of a wide variety of domestic resources, including its educated workforce).
Flax Typhoon traffic may have originated from the above Fudan University IP addresses but then contacted the IP address hosting its VPN (the previously-identified IP address with a Flax Typhoon-linked TLS certificate), either to administer the service in use there or to route traffic targeting a victim organization through it.
While it is possible that Flax Typhoon has used the above Fudan University-attributed IP addresses as a result of a relationship between the group and the University, other explanations for the traffic may merit consideration. Threat actors could, for example, have compromised the observed IPs and then repurposed them to malicious ends. However, in light of the above-discussed public reporting, this traffic may nonetheless contribute to the established concerns over links between Fudan University and the PRC’s intelligence services.
Recommendations
SecurityScorecard recommends that organizations in regions and industries that Flax Typhoon is known to target monitor their networks for communication with the IP addresses identified above and consider adding them to the relevant blocklists.
Despite concerns over Fudan University’s role in espionage, the possibility that some traffic involving Fudan University-attributed IP addresses represents legitimate academic activity also merits consideration. Blocking these IP addresses may therefore be less advisable for organizations with established, legitimate relationships to Fudan University, though the possible exploitation of apparently legitimate academic relationships for espionage complicates these considerations further.


