Introducing MAX — Take supply chain cyber risk management to the MAX
What is Cyber Risk Quantification? A Comprehensive Guide

As cybercriminals discover new ways to expand the threat landscape, cyber security professionals need to be able to predict their next move and stay ahead of evolving cyber threats. But in order to do so, businesses must be aware of their vulnerabilities, have a clear view of their cybersecurity posture, and have an understanding of their associated risks. In this blog, we will look at how cyber risk quantification (CRQ) can help simplify cybersecurity risk in a way the entire organization can understand.
Let’s take a closer look.
What is cyber risk?
Cyber risk is the general term used to describe any risk associated with a company’s use of information technology systems. It includes the risk of financial loss, service disruption, and reputational damage that results from IT failure. This failure may be due to equipment malfunction, but it can also occur from cyberattacks or data breaches.
What is cyber risk quantification (CRQ)?
Cyber Risk Quantification (CRQ) is the process of assessing the potential financial impact of an individual cyber threat to your business. CRQ evaluates operational risk, efforts to reduce risk, risk exposure, and risk mitigation.
Quantifying cyber risk puts a monetary value on the potential impact of each prospective threat. In doing so, cybersecurity professionals gain a better picture of how to prioritize each threat as well as how to communicate the risk to the broader organization and management team. From there, they can then focus efforts on mitigating the highest-impact risks first, optimizing their overall ability to protect the network.
What are the benefits of cyber risk quantification?
There are many reasons to quantify cyber risk. Some of the leading benefits of the CRQ process include:
Improving accuracy of risk assessments
In today’s cyber landscape, there are a variety of threats, including insider threats, ransomware, DDoS attacks, data breaches, and more to be on the lookout for. With more qualitative processes, it’s easy to get lost in the weeds while trying to determine what to fortify first. With CRQ, security teams are guided by potential financial impact instead of more ambiguous assessments or gut feelings as they determine which threats are most pressing and should be prioritized.
Making more informed decisions
IT leaders can use CRQ data to better understand the real impact of different threats as well as their probability of occurrence. Because the highest priority risks are better identified, these leaders can make more informed decisions regarding where to direct resources to optimize security and minimize the total financial risk of the business at large.
Exemplifying the importance of cybersecurity to top management
Many cybersecurity professionals struggle to articulate the importance of certain investments and initiatives to upper management. Those in management are more reluctant to allocate funds for new software or infrastructure when they see it as a cost center with negligible benefits. With CRQ, however, the cybersecurity team can present the benefits and risks in terms of something management is extremely familiar with: money.
Gaining a competitive advantage
CRQ allows security teams to respond to threats in a targeted way that is optimized for cost-efficiency. By enabling teams to direct resources strategically, CRQ also helps those teams do more with less. Any time efficiency is improved and costs are optimized, it’s good for the overall health of the business. Not only that, but the act of using cyber risk quantification in the first place sends a signal to stakeholders that an organization takes cyber risk seriously and is more likely to have better technological maturity and cyber resilience.
Understanding and developing effective strategies for risk mitigation
The quantitative nature of CRQ also allows teams to better estimate the value and effectiveness of different risk mitigation strategies. For example, it can help them choose between different software, infrastructure, or vendors as they shore up security because they know which are more likely to yield a better ROI based on the cost of potential risks being mitigated.
Cyber risk quantification frameworks to consider
Any organization that wants to implement cyber risk quantification must first decide what methods or frameworks to use in doing so. There are both qualitative and quantitative methodologies for risk analysis. The most common qualitative method is a Matrix or Heatmap, while quantitative methods include Bowtie, FAIR, Probability/Impact Analysis, and Monte Carlo analysis.
The Factor Analysis of Information Risk (FAIR), was developed by the global technology standard-setter The Open Group and provides guidelines for how, exactly, to go about quantifying security risk in terms of financial impact. The risk model components that make up FAIR provide a common language and methodology for talking about risk, outline criteria for how to collect data to use in calculations, different measurement scales for risk factors, and constructs for analyzing complex scenarios.
Probability/Impact Analysis quantifies risk based on its dollar value, which is not only beneficial for prioritizing risk remediation, but for reporting purposes as well. By quantifying risks based on their monetary value, concerns surrounding cyber security posture and risk impact can be better communicated to organizational decision makers including C-level executives and boards.
The Monte Carlo analysis uses a computer simulation to identify the probability of disruptions and their possible outcomes based on an action. The Monte Carlo analysis runs thousands of randomly generated scenarios to identify the probability of a risk occurring. By having a clear idea of where threats are present, and how they occur, businesses can quantitatively assess the level of risk and choose a decision that provides the best balance of benefit against risk.
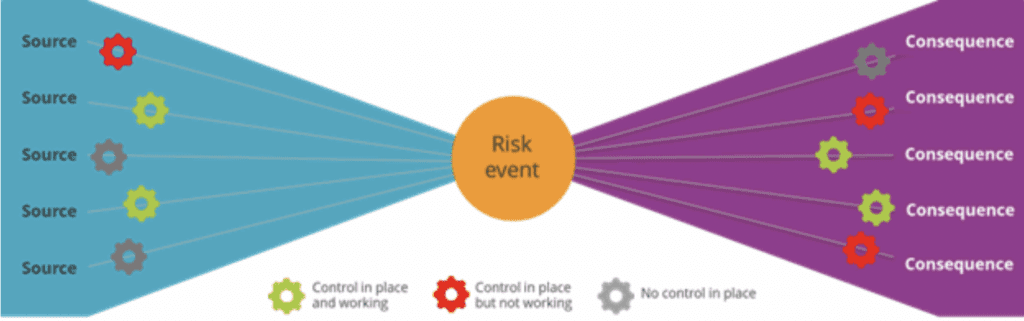
Bowtie risk analysis is another framework to consider, as it helps organizations map the cause and effects related to potential risks. Bowtie provides organizations with a clear view of aspects that contribute to a risk event and what consequences are likely to occur as a result.
What are the best methods for cyber risk quantification?
FAIR, Bowtie, and other risk frameworks offer many suggestions and best practices. Here, we’ve created a list covering many suggestions you can use to get started:
Establish third-party risk profiles and guidelines: The fact that you don’t likely have much technological oversight on how vendors and partners manage their security should be a source of concern. You can be just as impacted by a breach on their end as by a breach on your network. Before onboarding new vendors, establish guidelines and risk profiles to ensure you are efficiently managing the risk of third parties.
Create a comprehensive glossary of CRQ terminology: Because different groups of people often have different definitions of words like “threat” or “asset,” it’s a good idea to set clear definitions for each word used in your CRQ process, clearly explaining the intended meaning in that context.
Designate a security rating for each asset: You should have a clearly defined method for how to assign a security rating for each asset in your digital portfolio as a starting point for determining probabilities of impact.
Exterminate one threat at a time: Tackling only one threat at a time allows the IT team to be efficient and limits the impact of the corrections as they are made.
Prioritize cyber threats with high damage potential: Prioritize the threats that can do the most damage and make sure you accurately assess and quantify that potential damage.
Document processes: It’s never a good idea to keep your plans and processes in someone’s head or scattered across different emails and direct messages. You’ll save everyone headaches down the road if you clearly document the processes you develop in a way that’s accessible to all who may need them and customizable as you refine your strategies. Documentation also helps standardize processes so they can be repeated accurately and reliably.
- Identify the financial consequences: Depending on the type of data breach, the financial consequences can be significant, whether it is regulatory penalties, reputational costs, or legal liabilities. Businesses can use industry insights and data from previous cyber attacks to estimate the cost and impact on business finances to better understand the risk each vulnerability presents.
- Engage other divisions and IT processes with CRQ: When it comes to identifying potential risks, you’ll achieve a more comprehensive and holistic business view if you reach out to departments beyond IT. Those other departments — such as the finance, legal, and PR teams — may have insights into the impacts of various risks that wouldn’t have occurred to the IT team otherwise.
4 Reasons why cyber risk quantification is essential for business operations
Cyber risk goes beyond the IT department. Somebody downloading a virus has the potential to impact an entire organization’s operations. Being able to quantify cyber risk is now critical to businesses for these reasons:
The cyberattack surface is constantly evolving, subsuming more and more of an organization’s essential functions.
Qualitative measurements aren’t enough and don’t allow for prioritization of threats in a way that optimizes for budget and business impact.
Businesses can gain a competitive advantage when they better target their use of limited budgets and resources.
Cyber-attacks are becoming more complex and able to affect broader swaths of an organization in increasingly damaging ways.
How to quantify cyber risk
Quantifying cyber risks starts by leveraging a solution that will help streamline the entire process while offering a holistic view of the financial impact of cyber risk. SecurityScorecard’s Cyber Risk Quantification offering helps organizations translate their cyber risk into dollars, making it easy to understand the financial risk presented by a vulnerable network. If you want an easier way to describe risk to upper management, the ability to optimize cybersecurity investments, and to align risk management to your business needs, then your business needs CRQ with SecurityScorecard. Request a demo to learn more today.


