Ransomware Affiliates Exploit Recently-Discovered PaperCut Vulnerability
Executive Summary
- On April 26, security researchers announced the discovery of CVE-2023-27350 and CVE-2023-27351, vulnerabilities in the PaperCut print management software solution.
- Researchers have observed threat actors exploiting the more severe of the two vulnerabilities, CVE-2023-27350, to deliver the LockBit strain of ransomware.
- The SecurityScorecard Threat Research, Intelligence, Knowledge, and Engagement (STRIKE) Team leveraged SecurityScorecard’s Attack Surface Intelligence tool and its exclusive access to network flow (NetFlow) data to identify activity possibly linked to the group exploiting the vulnerability.
- Attack Surface Intelligence identified a population of servers the vulnerability might affect, but the available NetFlow data did not offer clear evidence of activity linked to the group exploiting it.
- Other traffic data may reflect suspicious activity but does not offer clear evidence of the deployment of the LockBit ransomware.
Background
On April 26, security researchers announced the discovery of CVE-2023-27350 and CVE-2023-27351, vulnerabilities in the PaperCut print management software solution. PaperCut has reported that suspicious behavior detected by a customer on April 18 brought them to the company’s attention. After the customer observed the anomalous behavior on their PaperCut server, further investigation revealed that attackers had exploited the then-unknown vulnerabilities. PaperCut’s subsequent analysis of additional customer reports led the company to conclude that the earliest activity suggesting possible exploitation of these vulnerabilities appeared on April 14. The warning further notes that PaperCut is normally accessible through web management ports at port 9191 or 9192 and provides indicators of compromise (IoCs), including domains that have served the malicious downloads threat actors deployed after exploiting CVE-2023-27350 and hashes of the files downloaded. The advisory contains the following domains:
- Windowservicecemter[.]com
- Anydeskupdate[.]com
- Anydeskupdates[.]com
- Netviewremote[.]com
- Updateservicecenter[.]com
- Windowcsupdates[.]com
- Windowservicecentar[.]com
- Windowservicecenter[.]com
- Winserverupdates[.]com
One external investigation found that threat actors had exploited the more severe of the two vulnerabilities, CVE-2023-27350, to deliver the LockBit strain of ransomware. CVE-2023-27350 enables remote code execution (RCE); attackers leveraged it to run a PowerShell script that allows them to download and execute a file containing malicious payload analysts identified as the LockBit strain of ransomware.
Other analysts have observed data theft activity that also exploits CVE-2023-27350, which they attribute to a Cl0p ransomware affiliate, Lace Tempest. In this case, the attackers exploited CVE-2023-27350 to run PowerShell commands that ultimately delivered the TrueBot malware to target systems, after which they deployed a Cobalt Strike beacon, carried out additional reconnaissance and lateral movement, and finally identified and exfiltrated the target organization’s files.
Methodology
To identify possible targets for exploitation of CVE-2023–27350, STRIKE Team researchers searched SecurityScorecard’s Attack Surface Intelligence tool for IP addresses where the ports specified in PaperCut’s advisory are open and where PaperCut appears to be in use by employing the following queries (and port:9191 ‘papercut’) and (and port:9192 ‘papercut’).
Researchers then collected a two-month sample (February 27, 2023-April 27, 2023) of traffic involving these potential target IP addresses using a strategic partner’s NetFlow data. They then searched within the resulting sample for traffic that could reflect targeting of the vulnerable products or may otherwise be suspicious. Researchers first identified the traffic involving the ports mentioned in the advisory. Researchers next focused on the largest data transfers in the traffic sample because large data transfers are a common feature of ransomware and other data extortion attacks and could represent data exfiltration. Finally, researchers submitted all of the IP addresses in the sample to SecurityScorecard’s internal threat intelligence platform (TIP) to compare them to those collected in previous investigations into similar activity. IP addresses appearing in multiple events’ traffic samples may, therefore, be related to threat activity.
Researchers then narrowed these results further by searching for the IP addresses in the public cybersecurity information-sharing platform VirusTotal. They focused on those addresses that other cybersecurity vendors have already linked to malicious activity.
Having compiled a list of IP addresses worthy of closer attention, researchers next returned to the original traffic samples to collect additional information about these IP addresses’ behavior concerning the target organization within the specific monitoring period. They then searched these IP addresses in SecurityScorecard’s Attack Surface Intelligence product and VirusTotal for additional context.
Researchers next used the same partner data source to collect a sample of DNS queries, passive DNS (PDNS) data, and HTTP requests containing the domains PaperCut listed as IoCs and searched public records for WHOIS data related to the domains. The PDNS information identified the IP addresses to which these domains had resolved recently, allowing researchers to identify other possible suspicious communications in the traffic sample by searching for the IP addresses hosting the domains that served the malicious downloads of which PaperCut warned.
Findings
The queries to Attack Surface Intelligence revealed four IP addresses where PaperCut appears to be in use and port 9191 is open (the query for port 9192 returned no results). SecurityScorecard attributes all of these IP addresses to educational institutions: two institutions of higher education in the U.S. (one college and one university), one university in Canada, and one K-12 school in Japan.
The traffic sample indicates that eighty-six other IP addresses communicated with these four possible target IP addresses between February 27 and April 27. Four of these eighty-six IP addresses communicated with the possibly-affected IP addresses over ports 9191 or 9192 and three of these may reflect suspicious behavior. 8.222.149[.]1 contacted port 9192 of the Japanese school on March 3. 8.222.149[.]1 has one detection for malware in VirusTotal. The Japanese school subsequently communicated with 165.22.39[.]64 on March 6; 165.22.39[.]64 has nine detections in VirusTotal, and VirusTotal community members have observed it carrying out SSH brute force attacks and included it in collections of suspected malicious IP addresses. 165.22.39[.]64 also appears in nine of the feeds that contribute to Attack Surface Intelligence’s malicious reputation facet and in a traffic sample the STRIKE Team collected while investigating another breach claimed by LockBit.
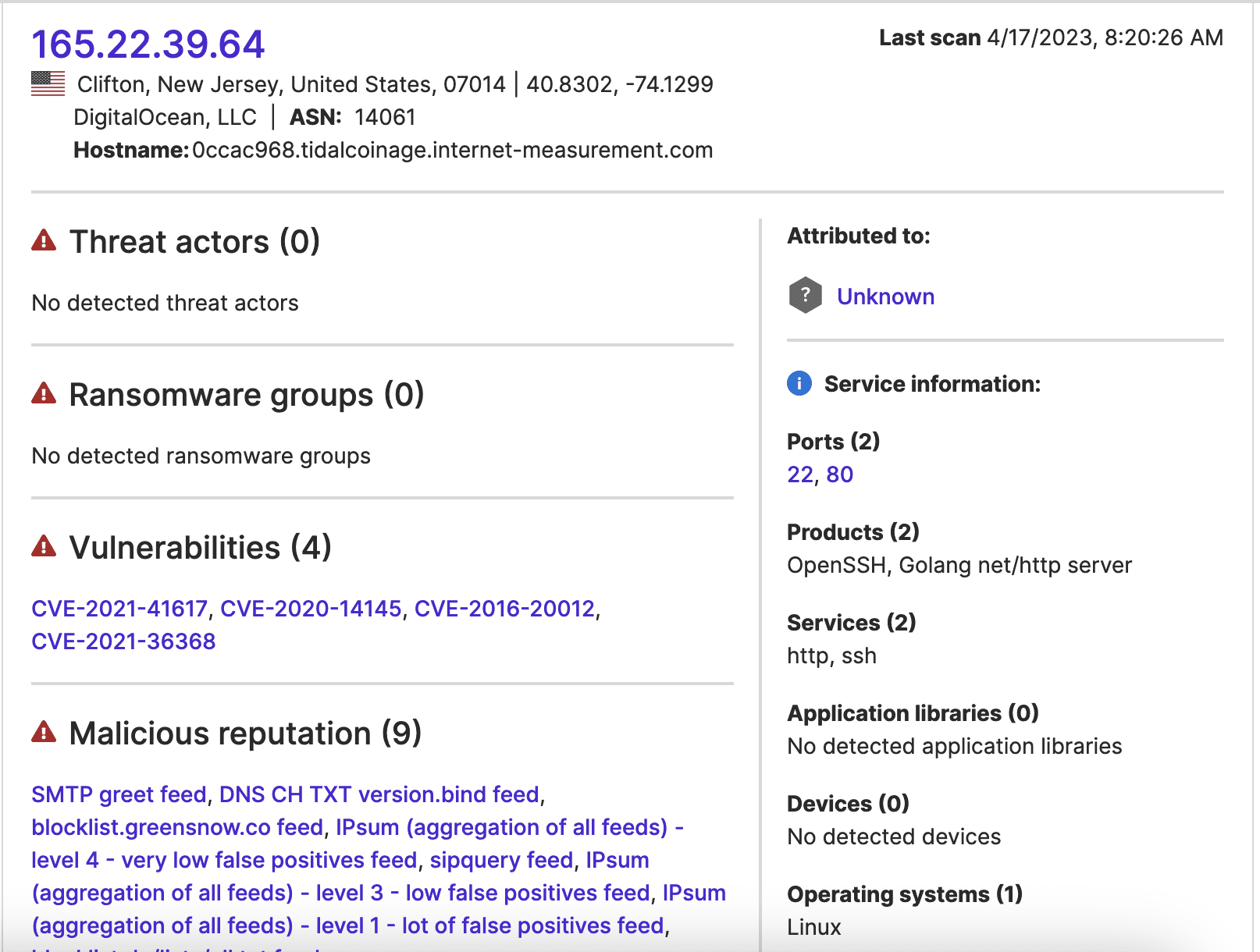
Image 1: Attack Surface Intelligence’s malicious reputation data indicates that previous research has linked 165.22.39[.]64 to malicious activity.
Port 9191 of the U.S. college contacted 129.81.255[.]94 on March 6, but this communication may be benign. SecurityScorecard attributes 129.81.255[.]94 to another US university, and this IP address has zero detections in VirusTotal.
Finally, port 9192 of the Canadian university contacted 165.232.76[.]155 on March 20. 165.232.76[.]155 has seven detections in VirusTotal and appears in eight feeds contributing to Attack Surface Intelligence’s malicious reputation facet.
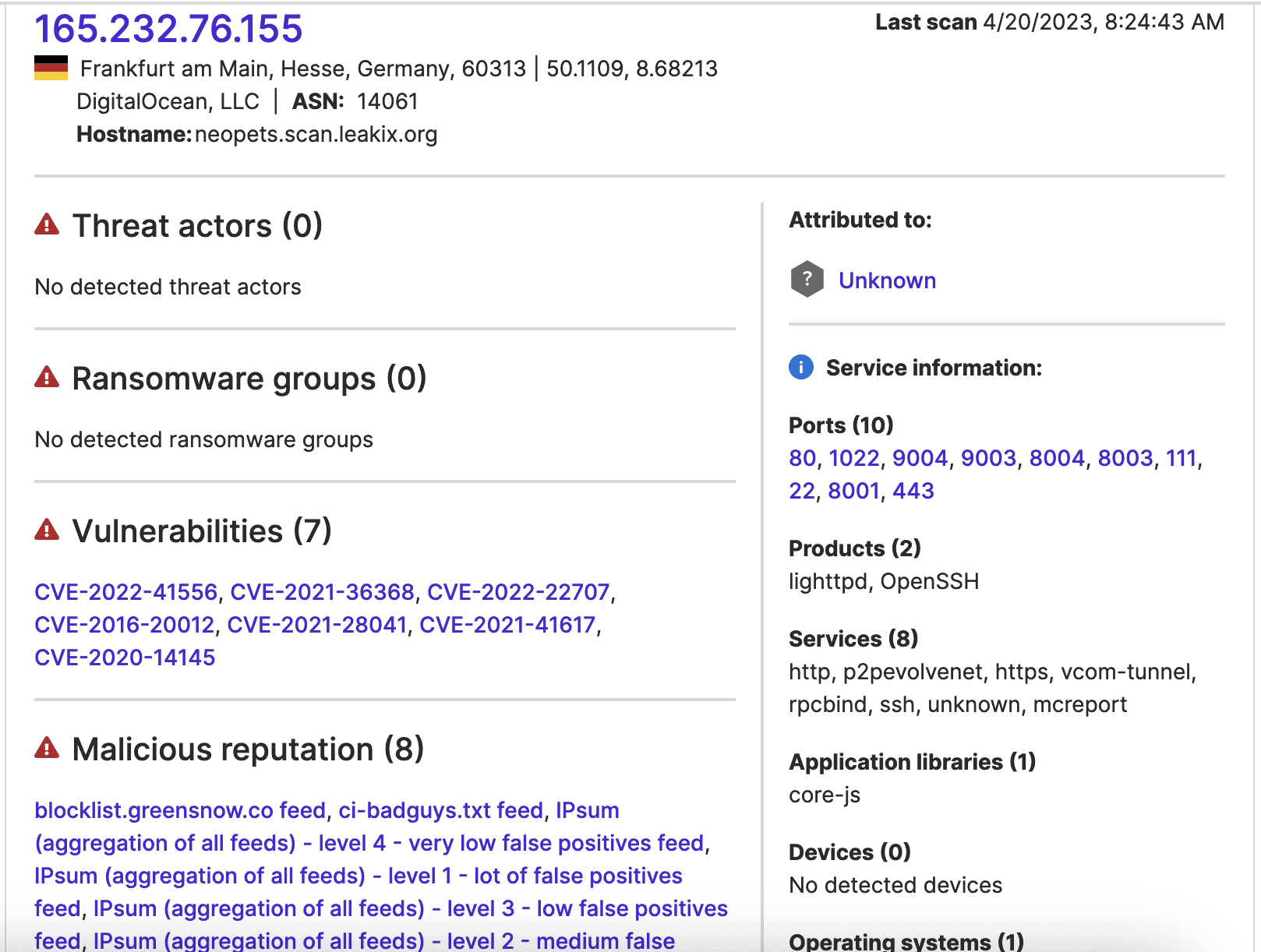
Image 2: Attack Surface Intelligence’s malicious reputation data indicates that previous research linked 165.232.76[.]155 to malicious activity.
The March 6 transfer from the Japanese school is also one of the largest in the traffic sample; it involved 12.29 MB. The IP address attributed to the U.S. university made a transfer of the same size (12.29 MB) to 146.190.224[.]160 on March 17. 146.190.224[.]160 has six detections in VirusTotal and appears in six feeds that contribute to Attack Surface Intelligence’s malicious reputation facet.
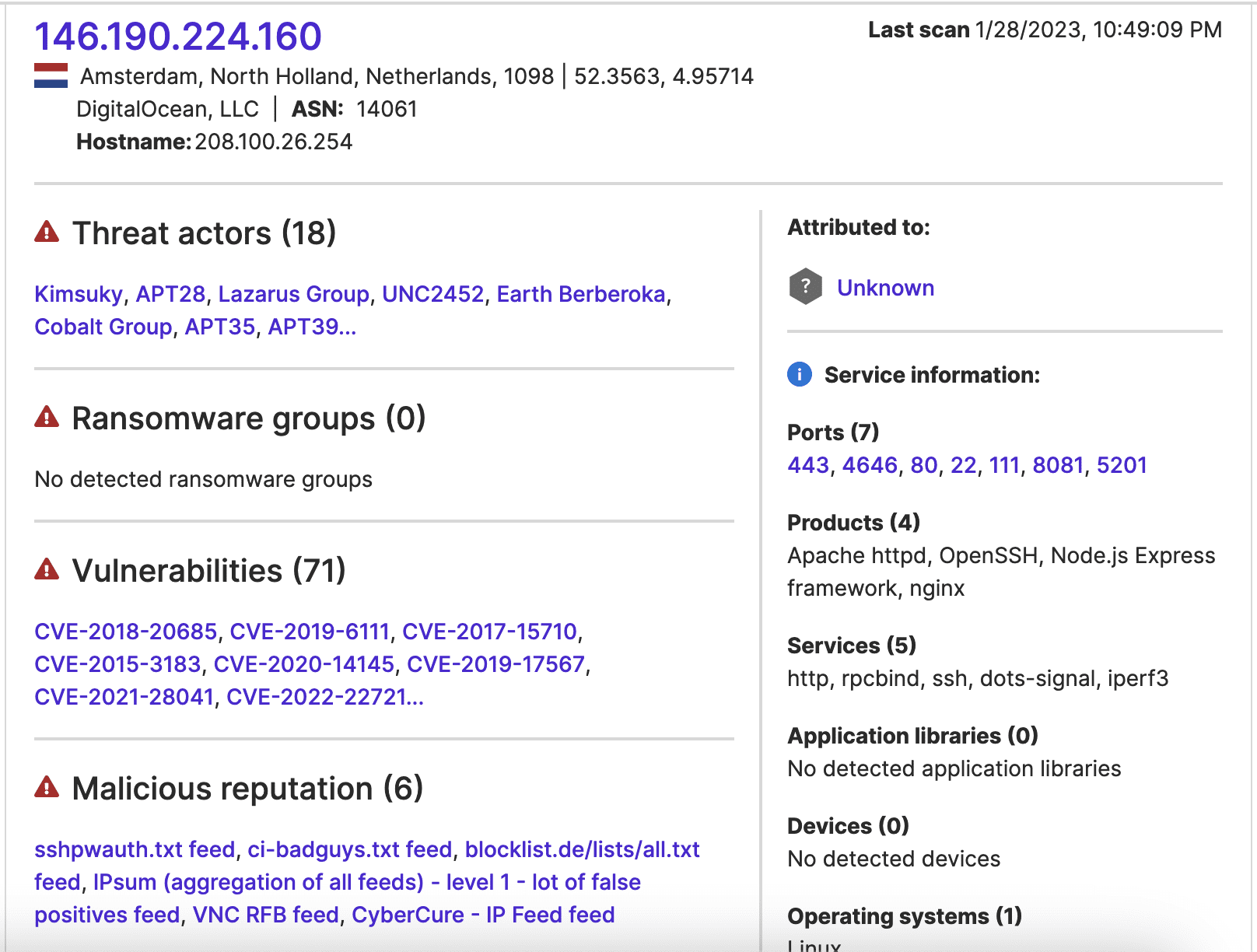
Image 3: Attack Surface Intelligence’s malicious reputation data indicates that 146.190.224[.]160 has also previously been involved in malicious activity
The last of the three largest transfers took place on February 28, when the university in Canada transferred approximately 12.09 MB to 167.172.183[.]6. 167.172.183[.]6 has one detection in VirusTotal, which suggests that a cybersecurity vendor has observed it conducting malicious activity in the past.
SecurityScorecard’s internal TIP revealed that twenty-eight of eighty-six IP addresses have appeared in previous investigations into possible ransomware and data theft extortion incidents. Other vendors have also linked twenty-one of these to malicious behavior. All are available in an appendix below, but more detailed and possibly relevant information was available about three.
The U.S. college-attributed IP address made two transfers to 198.54.128[.]108 on March 7. Members of the VirusTotal community have identified 198.54.128[.]108 as a TOR exit node. While this does not necessarily indicate malicious activity, given that threat actors use TOR to conceal the origins of their activity, this traffic is at least suspicious. The same institution and 27.0.183[.]209 communicated on March 17. Three vendors detect 27.0.183[.]209. It recently served a download of a file which, while not malicious itself, has appeared alongside malicious downloads linked to the IcedID strain of malware and ransomware operations, including Maze and Conti. While communication with this IP address does not necessarily indicate that it served the same file to the U.S. college in question, it may merit further attention to verify that the activity represented by the communication is indeed benign. Similarly, both U.S. educational institutions communicated with 180.233.120[.]94 a total of sixteen times between March 6 and March 28. Two vendors have linked 180.233.120[.]94 to malware or other malicious activity. Like the previous IP address, 180.233.120[.]94 has recently served a download of a benign file that sometimes appears alongside malicious ones, including ransomware.
Finally, it may bear noting that many of these IP addresses (forty-one of eighty-six) belong to Digital Ocean, a large hosting provider; the traffic involving them could represent expected behavior (like transfers to and from backups), but given that threat actors have also abused Digital Ocean in the past, communication with these IP addresses may merit attention from personnel with internal visibility into the affected organizations’ networks.
The PDNS data collected by STRIKE Team researchers indicates that the IoC domains provided in PaperCut’s advisory resolve to the following IP addresses:
- 104.21.73[.]3
- 208.91.197[.]91
- 104.21.76[.]21
- 104.21.33[.]138
- 104.21.65[.]209
- 104.21.66[.]154
- 104.21.96[.]96
None of these IP addresses appear in the traffic sample, which indicates that it is unlikely the possibly affected organizations communicated with the particular domains listed in the advisory.
In addition to the IP addresses hosting them, researchers identified additional observables that could help detect other activity similar to that linked to the exploitation of CVE-2023-27350. Predictably, much of the WHOIS data for these domains is privacy-protected. Still, the information contained in the fields without redacted entries suggests a pattern that could inform efforts to defend against similar activity. All of the WHOIS records have the same creation date (April 12, 2023) and registrar (Tucows), and all but one of the domains’ records share a common registrant state/province and country (Charlestown, KN). By themselves, these features would be common to too many domains to help identify those that are potentially malicious, but together, they may reduce the number of resulting domains enough to help identify others involved in activity similar to that reported by PaperCut, especially if security personnel used the common features of the domain names (most pertain to updates of Microsoft products but contain variations or misspellings of the products referenced) to further analyze the result.
Mitigation
PaperCut has released an update patching the vulnerabilities for all currently supported versions of the affected products, so we advise that organizations using those products apply it. PaperCut has additionally advised those using versions for which the upgrade is not available or who are otherwise unable to patch their software to either close ports 9191 and 9192, block inbound traffic to their firewall’s web management portal, or limit servers’ allow lists to verified Site Servers’ IP addresses.
Conclusion
As with CVE-2023-28252, a ransomware group’s exploitation and discovery of CVE-2023-27250 may indicate a wider trend. The “in the wild” discovery of these vulnerabilities may indicate that threat actors are exploiting zero-day vulnerabilities more shortly after their discovery rather than saving newly-discovered vulnerabilities for later use.
Appendix: Vendor-Detected IP Addresses Appearing in Other Incidents’ Traffic Samples
- 45[.]232[.]73[.]46
- 138[.]68[.]74[.]198
- 161[.]35[.]119[.]216
- 102[.]221[.]249[.]148
- 167[.]172[.]219[.]157
- 143[.]198[.]177[.]98
- 64[.]227[.]90[.]185
- 137[.]184[.]190[.]205
- 102[.]221[.]249[.]156
- 27[.]0[.]183[.]209
- 198[.]54[.]128[.]108
- 160[.]238[.]136[.]117
- 180[.]233[.]120[.]94
- 154[.]68[.]199[.]42
- 89[.]203[.]150[.]42
- 202[.]51[.]181[.]142
- 102[.]220[.]15[.]172
- 37[.]247[.]239[.]155
- 194[.]36[.]94[.]157
- 185[.]49[.]250[.]215
- 170[.]231[.]99[.]204


