Microsoft ProxyNotShell Zero Days
Executive Summary
-
Researchers publicly disclosed two new Microsoft Exchange zero-day vulnerabilities, now tracked as CVE-2022-41040 and CVE-2022-41082, on September 29, with Microsoft subsequently confirming that they were under active exploitation.
-
In less than twenty-four hours after their first publication, SecurityScorecard developed an emergency informational signal to give customers visibility into potentially impacted Exchange servers.
-
SecurityScorecard’s STRIKE team began an investigation into these new vulnerabilities shortly after their publication.
-
Throughout our investigation, our attack surface intelligence (ASI) tool has revealed a large population of servers that may be subject to this vulnerability, and our global network flow analysis capability (available via professional services) has uncovered possible communication and data exfiltration between victim’s infrastructure and command-and-control (C2) infrastructure involved in the exploitation of these vulnerabilities.
-
SecurityScorecard has released two new issue types in the Network Security factor to highlight whether your organization or your vendors are at risk of breach due to these vulnerabilities.
Background
SecurityScorecard’s STRIKE team has begun investigating two newly reported Microsoft Exchange zero-day vulnerabilities. These CVEs are reported as CVE-2022-41040 and CVE-2022-41082 and currently only impact Microsoft Exchange on-premise servers.
Researchers from Vietnamese cybersecurity firm GTSC publicly disclosed the vulnerabilities on September 29, but first observed them while investigating an attack against critical infrastructure in August. Microsoft confirmed that they were under active exploitation. While they have not yet attributed them to a specific APT group, researchers noted similarities between the exploitation of this vulnerability and activity involving the China Chopper malware, which researchers have previously linked to multiple China-attributed APT groups.
Investigation
Attack Surface Exposure
Our investigation and analysis reveal that a large population of servers may be subject to this vulnerability based on the detection of Microsoft Exchange on-premise and Microsoft IIS servers. The graphic below can illustrate the scope of the problem by offering a view of the geographical distribution of servers potentially impacted by these two CVEs. The data shown comes from our global scanning platform, Horus, which powers parts of the SecurityScorecard Ratings capability and the Attack Surface Intelligence capability.
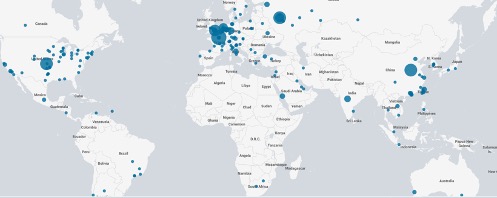
Furthermore, Attack Surface Intelligence reveals over 48,000 assets running Exchange servers with a variety of threat context at the time of this writing (9/30/2022), including other CVEs unrelated to ProxyShell, threat actor associations, and more.
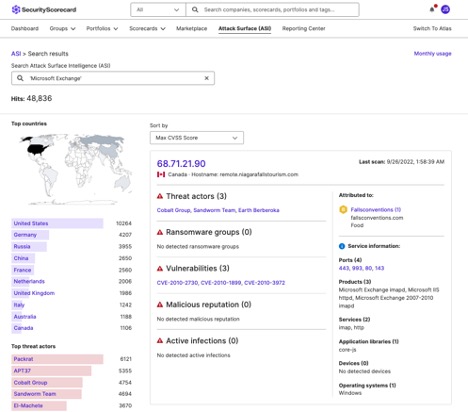
View of Microsoft Exchange servers with associated threat context from ASI
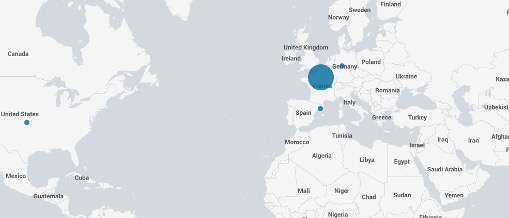
Based on IOCs provided by the community, we observed a number of entities potentially compromised by the aforementioned webshells “Xml.ashx”, “errorEE.aspx”, “RedirSuiteServiceProxy.aspx”, “pxh4HG1v.ashx” including at US-based educational institutions. Of 12 total IPs from the last 30 days of scans that returned results for these HTTP paths, 3 were Microsoft IIS servers. The false positives were other sites hosting non-malicious ASP.NET files. The following graphic shows the geographical distribution of possible post-exploitation activity for the above CVEs. This data point corresponds with Microsoft’s insights that there has been evidence of limited, targeted attacks conducted by adversaries using these vulnerabilities. Furthermore, we describe below how we linked the C2 IP published by GTSC back to possible data exfiltration victims using netflow analysis.
Webshell Analysis
We attempted to look up the webshell file hashes posted by GTSC in VirusTotal and our in-house malware intelligence. For the hashes below, no existing downloads or API submissions were found from either, indicating that, for now, it is possible that EDR and AV vendors have not begun submitting detected files to these services.
Even the malware sample referenced by GTSC and reverse engineered (Dll.dll – 074eb0e75bb2d8f59f1fd571a8c5b76f9c899834893da6f7591b68531f2b5d82) has not yet been uploaded to VirusTotal as of the time of this writing (9/30/2022).
Netflow Analysis of Published IPs and C2 server
The researchers who first identified these vulnerabilities included the following IP addresses in the indicators of compromise (IoCs) associated with their exploitation:
-
125[.]212[.]220[.]48
-
5[.]180[.]61[.]17
-
47[.]242[.]39[.]92
-
61[.]244[.]94[.]85
-
86[.]48[.]6[.]69
-
86[.]48[.]12[.]64
-
94[.]140[.]8[.]48
-
94[.]140[.]8[.]113
-
103[.]9[.]76[.]208
-
103[.]9[.]76[.]211
-
104[.]244[.]79[.]6
-
112[.]118[.]48[.]186
-
122[.]155[.]174[.]188
-
125[.]212[.]241[.]134
-
185[.]220[.]101[.]182
-
194[.]150[.]167[.]88
-
212[.]119[.]34[.]11
SecurityScorecard used our exclusive access to network flow (netflow) data to collect a sample of traffic involving the above IP addresses. Our query returned 993,174 flows over a monitoring period lasting from July 30 to September 30. Other vendors have already linked all of the above IP addresses to malicious or suspicious activity, so even flows that likely represent malicious activity may not necessarily reflect exploitation of these specific vulnerabilities. However, of the hundreds of thousands of flows collected within the monitoring period, SecurityScorecard researchers were able to identify a handful more likely to specifically involve these new vulnerabilities.
As reflected in the signal discussed below (“Product Potentially Impacted by PowerShell Remote Code Execution”), the affected services normally run at ports 5985 or 5986. Researchers searched within the larger netflow dataset for traffic over those ports and identified five.
-
On August 17, 86.48.12[.]64 (one of the IoCs) transferred 126 bytes to port 5985 of 160.238.137[.]146, and, in response, 160.238.137[.]146 transferred 330 bytes to 86.48.12[.]64 on the same day.
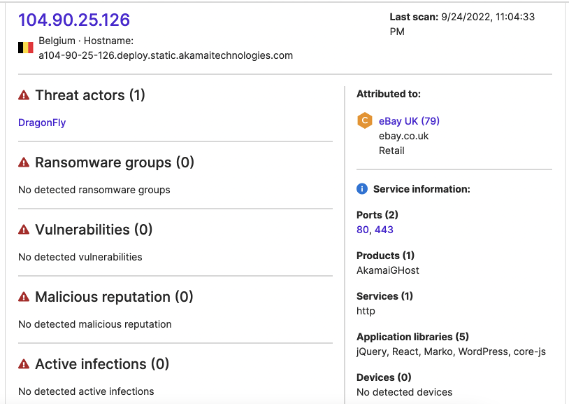
- On September 21, 23, and 27, two IP addresses, 104.90.25[.]126 and 69.55.53[.]168, transferred data to another IoC IP address, 185.220.101[.]182, over port 5986.
- 104.90.25[.]126 transferred 4.5 MB to 185.220.101[.]182 on September 21 and 27.
-
According to ASI, 104.90.25[.]126 is located in Belgium, belongs to Akamai, and is attributed to seventy-nine different organizations (presumably Akamai customers using services hosted at this IP address).
-
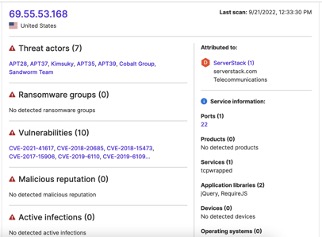
- 69.55.53[.]168 transferred 12.29 MB to 185.220.101[.]182 on September 23.
-
According to ASI, 69.55.53[.]168 is located in the United States, belongs to telecommunications company ServerStack, and suffers from several other CVEs known to be exploited by established threat actor groups.
-
- 104.90.25[.]126 transferred 4.5 MB to 185.220.101[.]182 on September 21 and 27.
Data Exfiltration to Published C2 Server
In addition to the above IoCs, GTSC isolated another IP address, 137[.]184[.]67[.]33, linking it in particular to command-and-control (C2) communications associated with the exploitation of these vulnerabilities. SecurityScorecard also collected netflow data reflecting the past two months of traffic to and from this C2 address. This query yielded 999,581 flows between July 30 and September 30. Notably, however, a smaller than usual portion of these flows, only 7,504 of 999,581, used port 443 (the standard port for HTTPS, over which a webshell would likely conduct its C2 communications). These 7,504 flows, in turn, involved 1,691 unique IP addresses. SecurityScorecard researchers then focused on the largest of these 7,504, identifying 40 that transferred 100 MB or more. These involved twenty-two IP addresses other than the C2 address:
-
162.243.189[.]2
-
52.217.15[.]72
-
52.85.151[.]66
-
31.13.71[.]52
-
162.159.130[.]233
-
104.126.118[.]235
-
74.125.172[.]200
-
31.13.71[.]14
-
200.236.31[.]2
-
104.18.122[.]25
-
104.18.125[.]25
-
52.218.110[.]40
-
47.11.203[.]156
-
197.210.79[.]42
-
108.29.53[.]30
-
96.241.221[.]82
-
24.190.36[.]111
-
172.253.122[.]128
-
96.244.150[.]197
-
67.63.67[.]12
-
52.217.47[.]104
-
206.62.165[.]53
Notably, many of these IP addresses appear to belong to large technology or telecommunications companies.
Amazon
-
52.217.47[.]104 (we attribute this to AWS S3 in particular)
-
52.217.15[.]72 (we attribute this to AWS S3 in particular)
-
52.85.151[.]66 (we attributed this to AWS Cloudfront in particular)
-
52.218.110[.]40 (we attribute this to AWS S3 in particular)
-
74.125.172[.]200 (we attribute this to 115 organizations, including Google and subsidiaries)
-
172.253.122[.]128 (we attribute this to seventeen organizations, including Google and subsidiaries)
-
31.13.71[.]52 (we attribute this to forty organizations including Meta and its subsidiaries)
-
31.13.71[.]14 (we attribute this to thirty-four organizations including Meta and its subsidiaries)
Cloudflare
-
162.159.130[.]233 (we attribute this to four organizations including Discord in addition to Cloudflare)
-
104.18.122[.]25 (we attribute this to three organizations including Docker in addition to Cloudflare)
-
104.18.125[.]25 (we attribute this to three organizations including Docker in addition to
Akamai)
-
104.126.118[.]235 (we attribute this to thirty-two organizations including various Akamai services and UK.com)
Verizon
-
108.29.53[.]30
-
96.241.221[.]82
-
96.244.150[.]197
Optimum
-
24.190.36[.]111 (we attribute this to seventeen organizations including telecommunications providers like Altice, Lightpathfiber, and Cablevision)
DigitalOcean
-
162.243.189[.]2 (we attribute this to CSS-Tricks and Journaldev in addition to DigitalOcean)
Zito Media
-
67.63.67[.]12
Reliance Jio Infocomm Ltd (an Indian telecommunications company doing business as Jio)
-
47.11.203[.]156
MTN Nigeria
-
197.210.79[.]42
The apparent exception: Universidade Federal do Paraná, a Brazilian university (we also attribute this to DroidDog, Phonedog, SourceForge Community Blog, Tmonews, and Wirefly)
-
200.236.31[.]2
Twelve vendors have previously linked 137[.]184[.]67[.]33 to malware and malicious activity, and the certificate observed when attempting a standard HTTPS connection to it is fairly recent. That certificate, issued for forum.congorepat[.]com (a domain hosted at 137[.]184[.]67[.]33), is only valid from August 28 to November 26 of this year.
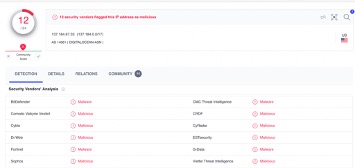
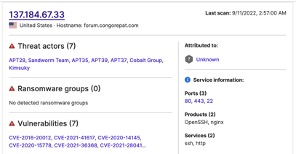
It is unclear if these large transfers between the C2 address and the above IP addresses reflect targeting of organizations to which SecurityScorecard has attributed those addresses by the threat actors exploiting these new vulnerabilities. While this may be a possibility, given that GTSC first observed these vulnerabilities while investigating an attack on critical infrastructure (which can include communications infrastructure), it bears noting that legitimate uses of DigitalOcean services (like moving data to or from a backup) can also involve large transfers.
Mitigation
New Ratings Issue Types
Following the publication of these two new vulnerabilities, SecurityScorecard rapidly developed emergency informational signals to inform customers that may be affected. These two new signals are:
Product Potentially Impacted by CVE-2022-41040 & CVE-2022-41082
- Description
-
Researchers have shared two Microsoft Exchange vulnerabilities (CVE-2022-41040 and CVE-2022-41082) with the security community. The first of these, CVE-2022-41040, a Server-Side Request Forgery (SSRF) vulnerability, can enable the second, CVE-2022-41082, a remote code execution (RCE) vulnerability. Having authenticated to a victim system, an attacker can leverage CVE-2022-41040 to trigger CVE-2022-41082and remotely execute code on a target system.
-
Microsoft Exchange is a popular business email solution run by many large enterprise organizations. The vulnerabilities only affect on-premise deployments. We detected evidence on your Digital Footprint that a self-hosted, on-premise Microsoft Exchange server is present and exposed to the public Internet. We discovered the microsoft-exchange service from our scanning platform and excluded from detection any assets not on premise. While this detected Microsoft Exchange service may not be vulnerable, verify immediately that it has not been exploited and put in place the recommended Microsoft Defender detections described in the references.
-
- Recommendation
-
No patch currently exists; however, monitor the Microsoft Security Response Center advisory in the references for this issue to keep abreast of relevant updates, including a patch release. Microsoft has posted several detection methods for the exploitation of these CVEs using Microsoft Defender for the Endpoint and Microsoft Defender Anti-Virus related to webshell exploitation, including the exister Chopper detections. If possible, remove the microsoft-exchange service from the public Internet and place it behind a firewall or VPN, so only internal users can access it. This will mitigate exploitation by non-organization entities, though this will not mitigate an insider threat or adversary already within the network looking to pivot off these vulnerabilities to gain higher-level access to systems.
-
- References:
-
CVE-2022-41040 Detail: https://nvd.nist.gov/vuln/deta…
-
CVE-2022-41082 Detai: https://nvd.nist.gov/vuln/deta…
-
Microsoft Security Response Center Advisory: https://msrc-blog.microsoft.co…
-
Azure Sentinel Query for ProxyShellPwn2Own Vulnerability Exploitation: https://github.com/Azure/Azure-Sentinel/blob/08a8d2b9c5c9083e341be447773a34b56b205dee/Detections/W3CIISLog/ProxyShellPwn2Own.yaml
-
Product Potentially Impacted by PowerShell Remote Code Execution
- Description
-
Researchers have shared two Microsoft Exchange vulnerabilities under active exploitation (CVE-2022-41040 and CVE-2022-41082) with the security community. The first of these, CVE-2022-41040, a Server-Side Request Forgery (SSRF) vulnerability, can enable the second, CVE-2022-41082, a remote code execution (RCE) vulnerability. Having authenticated to a victim system, an attacker can leverage CVE-2022-41040 to trigger CVE-2022-41082 and remotely execute code on a target system.
-
Microsoft Exchange is a popular business email solution run by many large enterprise organizations. The vulnerabilities only affect on-premise deployments. We observed evidence that a self-hosted, on-premise Microsoft Exchange server with the remote PowerShell ports accessible is present on your network and exposed to the public Internet. Our scanning platform detected the microsoft httpapi or microsoft-httpapi service and either port 5985 or 5986 open. This indicates that the actor can not only see the Exchange server but also send commands to a remote powershell service that may be affected by the vulnerabilities. While the detected Microsoft Exchange service may not be vulnerable, verify immediately that it has not been exploited and put the recommended Microsoft Defender detections described in the references in place.
-
- Recommendation
-
No patch currently exists; however, monitor the Microsoft Security Response Center advisory in the references for this issue to keep abreast of relevant updates, including a patch release. Microsoft has posted several detection methods for the exploitation of these CVEs using Microsoft Defender for the Endpoint and Microsoft Defender Anti-Virus related to webshell exploitation, including the exister Chopper detections. If possible, remove the microsoft httpapi or microsoft-httpapi service from the public Internet and place it behind a firewall or VPN so only internal users can access it. This will mitigate exploitation by non-organization entities, though this will not mitigate an insider threat or adversary already within the network looking to pivot off these vulnerabilities to gain higher-level access to systems.
-
- References:
-
CVE-2022-41040 Detail: https://nvd.nist.gov/vuln/detail/CVE-2022-41040
-
CVE-2022-41082 Detai: https://nvd.nist.gov/vuln/detail/CVE-2022-41082
-
Microsoft Security Response Center Advisory: https://msrc-blog.microsoft.com/2022/09/29/customer-guidance-for-reported-zero-day-vulnerabilities-in-microsoft-exchange-server/
-
Azure Sentinel Query for ProxyShellPwn2Own Vulnerability Exploitation: https://github.com/Azure/Azure-Sentinel/blob/08a8d2b9c5c9083e341be447773a34b56b205dee/Detections/W3CIISLog/ProxyShellPwn2Own.yaml
-
Attack Surface Intelligence and Managed Threat Hunting with Cyber Risk Intelligence
In addition to the visibility offered by the new signals in our ratings platform, SecurityScorecard’s other tools and services can support organizations’ efforts to respond to and defend against these vulnerabilities and their exploitation. SecurityScorecard’s new Attack Surface Intelligence (ASI) solution gives you direct access to SecurityScorecard’s deep threat intelligence data through a global tab on the ratings platform and via API, all of which can contribute to improved visibility into internal and external resources, supporting the infrastructure management advised above.
ASI analyzes billions of sources to provide deep threat intelligence and visibility into any IP, network, domain, or vendor’s attack surface risk, from a single pane of glass. This helps a variety of customers do more with the petabytes of data that form the basis of SecurityScorecard Ratings, including identifying all of an organization’s connected assets, exposing unknown threats, conducting investigations at scale, and prioritizing vendor remediation with actionable intelligence.
ASI is built into SecurityScorecard’s ratings platform through an enhanced Portfolio view or Global search across all Internet assets, leaked credentials, and infections and metadata from the largest malware sinkhole in the world. Access ASI today on the SecurityScorecard platform with 20 free search queries per month or request a demo on our website.
SecurityScorecard’s threat research and intelligence services could be the competitive advantage organizations need to stay ahead of fast-moving threat actors like those exploiting these new vulnerabilities. For more custom insights from our team with 100+ years of combined threat research and investigation experience, or more details on these findings, please contact us to discuss our Cyber Risk Intelligence as a Service (CRIaaS) offering. The above investigation can offer a trustworthy but preliminary view of our capabilities. Our team can continue diving into these details, especially with the ability to provide further support by working with on-site staff.
If you believe your organization to be under immediate threat from actors linked to this new threat, SecurityScorecard also provides managed incident response and digital forensics teams as a professional service driven by a large group of former law enforcement and private sector experts with decades of experience in the space. For immediate support from our teams, please contact us.