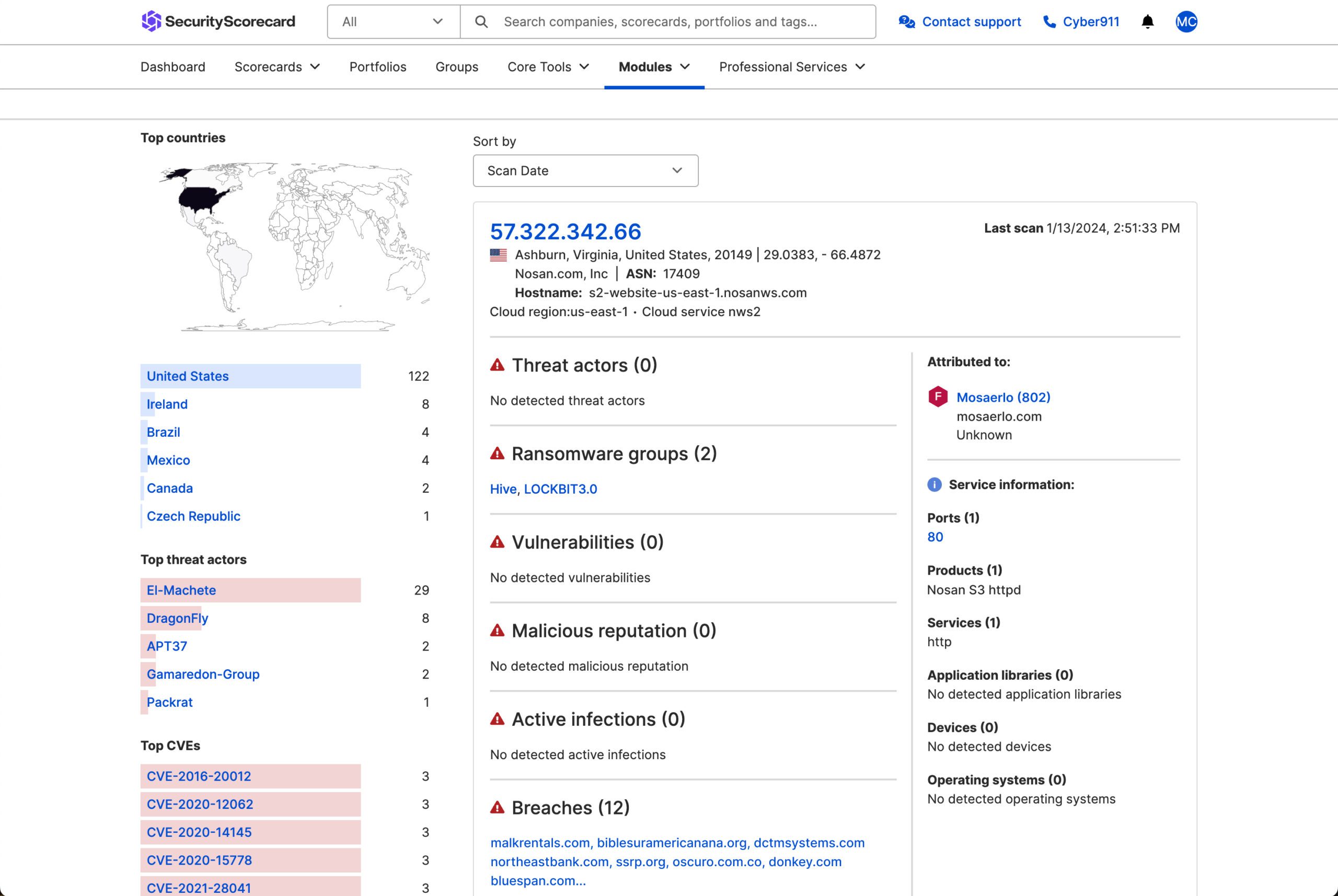
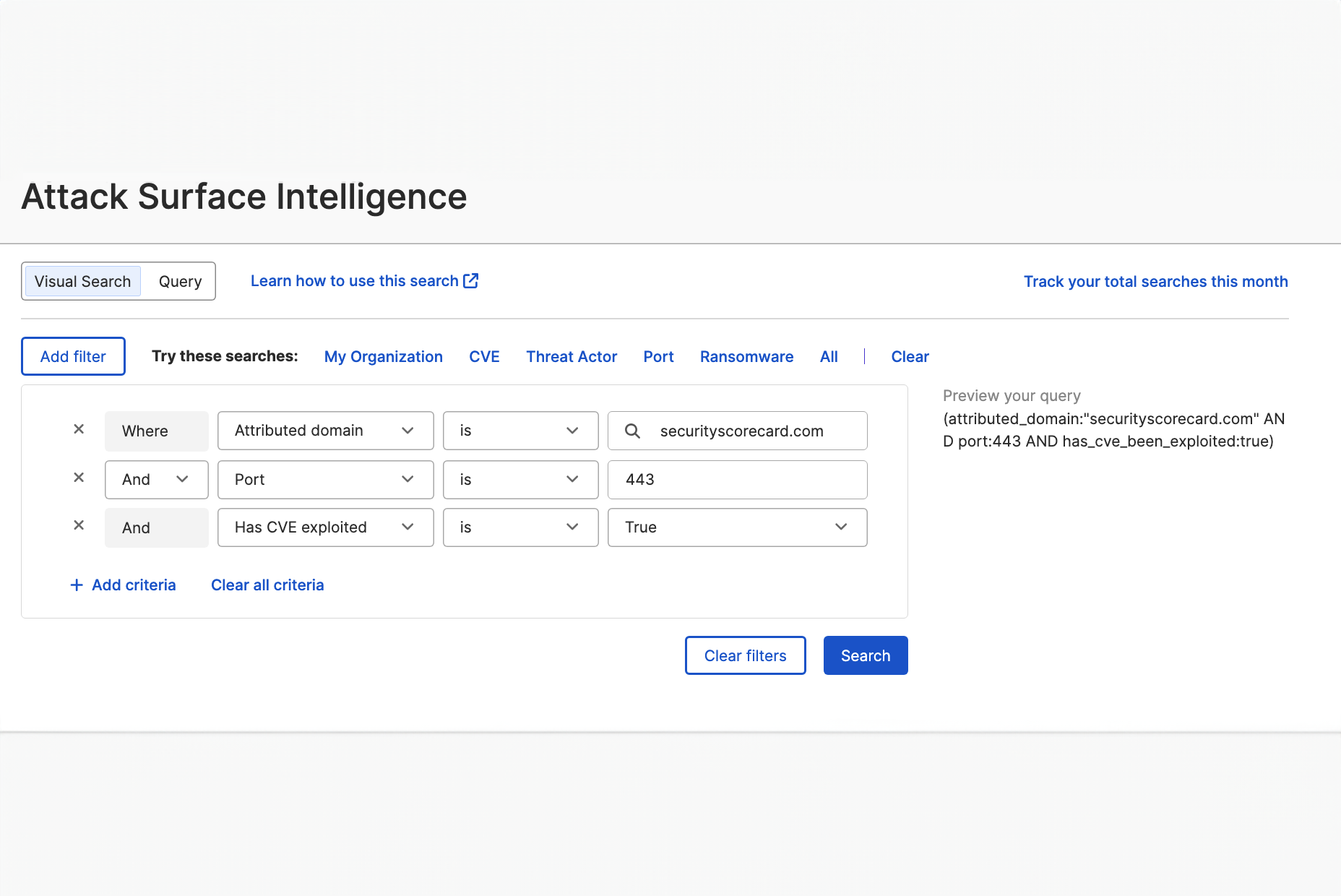
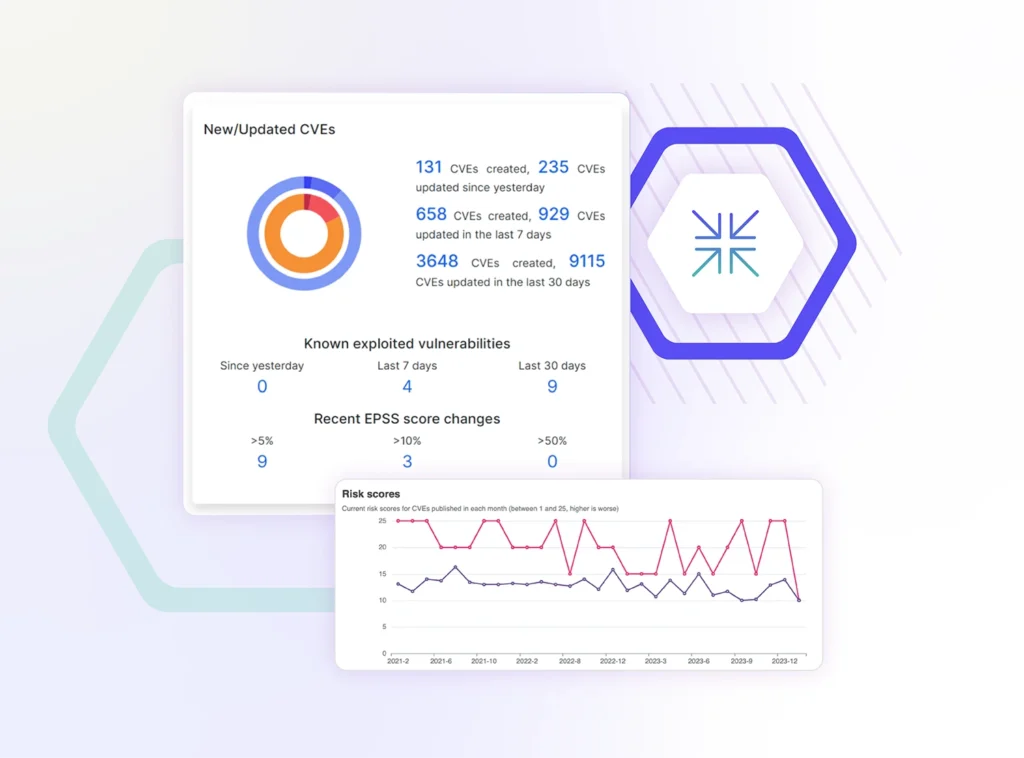
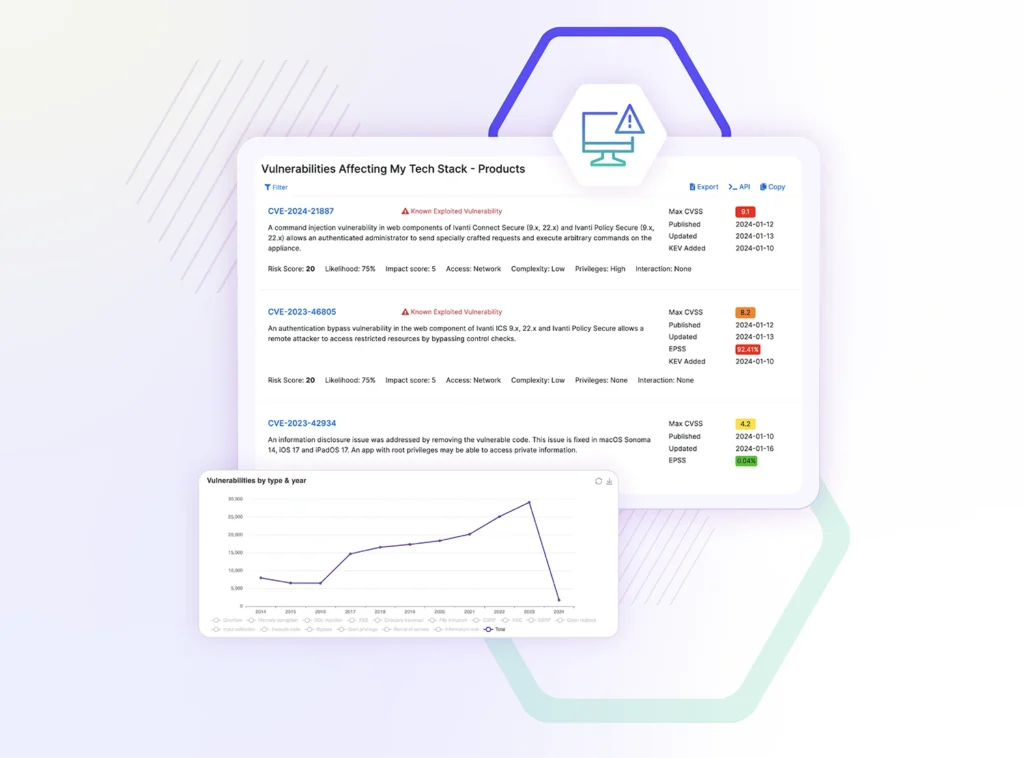
See what a hacker sees across your digital attack surface
Protect against threats as they arise with billions of curated real-time data points captured from around the world. Consolidate your external cyber defenses into a single, integrated platform.
Gain confidence in stopping cyber attacks with threat intelligence engineered for you
Mountains of information, sourced from disparate systems and riddled with inaccuracies, bombard SOC and TI teams, obscuring real threats. Sifting through the noise is a major task, demanding time, expertise, and an almost superhuman ability to find the needle in the haystack. SecurityScorecard’s Attack Surface Intelligence helps threat hunters prevent future disruptions with unrivaled, up-to-date, and precision-built global threat data from the clear and dark web in a single, consolidated platform.
A View Inside
Make informed decisions with clear and dark web data collected and curated by threat researchers for threat researchers


Automated attack surface discovery
- Become the hunter, not the hunted: Actively hunt and eliminate global threats with comprehensive IP scanning, domain attribution, and extensive CVE, threat actor, and malware tracking. All in one flexible search for unparalleled security.
- Transform your SOC: Move beyond static alerts, leverage advanced analytics to uncover true intent, and prioritize escalations for effective and timely remediation.
Leverage the power of SecurityScorecard’s AI and automation to constantly identify new vulnerabilities and associations so you are never caught off guard. - Navigate the clear and dark web with confidence: Illuminate murky corners of the internet and attribute attacks with context-rich threat intelligence collected and curated by threat hunters saving you hours from dissecting the noise and analyzing the patterns to make decisive decisions.
Critical Capabilities
-
Detect infected systems or networks
SecurityScorecard’s massive global sinkhole network provides information about infections from more than 150 malware families
-

Identify malicious infrastructure
SecurityScorecard’s malware attribution system digests and analyzes thousands of malware samples and indicators of compromise (IOCs) each day
-

Rapid refresh of massive global dataset
3.9 billion routable IP addresses scanned every 7 days across more than 1500 ports globally form the basis for the platform’s search index
-
Actionable insights that prevent breaches
Identify threat actors that are likely to impact your business. Take strategic and tactical actions to minimize exploitability across your attack surface
Hear from our customers
-
“SecurityScorecard’s threat intelligence showed more reliable attribution correlations than any other provider.”
Cybersecurity Analyst, Global Service and Technology Company1 / 0
FAQs
Why is Attack Surface Intelligence Important?
Attack Surface Intelligence (ASI) is crucial for organizations to identify, measure, and manage their exposure to cyber threats effectively. ASI provides visibility into all possible points of entry that an attacker could exploit, such as misconfigured systems, vulnerable applications, or exposed credentials.
By understanding and monitoring their attack surface, organizations can proactively reduce their risk of breaches and make sure they are prepared to respond to potential threats. This is particularly important for managing third-party risks, as organizations increasingly rely on a complex web of vendors and partners, each of which could introduce vulnerabilities into their ecosystem.
What is Attack Surface Intelligence?
Attack Surface Intelligence refers to the process of continuously discovering, analyzing, and managing an organization’s digital footprint, which includes all internet-exposed assets like IP addresses, domains, and applications.
It involves using advanced tools and techniques to map out an organization’s external and internal assets, identify vulnerabilities, and understand potential threats from an attacker’s perspective. This intelligence allows organizations to prioritize and mitigate risks, reducing their exposure to cyber threats and improving overall security posture.
What is an example of an attack surface?
An example of an attack surface is a company’s publicly accessible website that might have unpatched vulnerabilities in its underlying software. Another example is an exposed API with no proper authentication mechanisms. It could be exploited to gain unauthorized access to sensitive data.
Each digital asset, such as servers, endpoints, and cloud services, constitutes a part of the attack surface. Monitoring and securing these assets is critical to prevent potential cyber-attacks.
Explore More
There is much more to the SecurityScorecard platform