Real-Time Third-Party Cyber Risk Management for Your Supply Chain
Take control of your vendor ecosystem with unrivaled security data and risk intelligence. Continuously monitor third-party risk, identify vulnerabilities, and work with vendors to remediate critical issues – all in one platform.
Instantly understand the cyber risk of any third-party
Ninety-eight percent of organizations are connected to at least one vendor that’s had a breach in the last two years. As the global attack surface continues to expand, security and vendor risk management teams need complete visibility into their entire supply chain.
Automate your third-party risk management workflows, uncover hidden vulnerabilities, and collaborate with your partners to build a secure supply chain.
A view inside
Supercharge your third-party cyber risk management capabilities
Reduce risk to your business
-
Identify risks against your business posed by third parties
Your supply chain can put your business at risk. With SecurityScorecard, you gain a complete understanding of risk across your supply chain.
-
Move fast to remediate critical issues
Risk identification helps you understand what might impact you. Risk remediation reduces the likelihood that an attacker can successfully breach your organization. SecurityScorecard gives you the tools you need to proactively remediate cyber risks in your supply chain.
-

Continuous monitoring
Poor cybersecurity practices are often systemic in an organization. SecurityScorecard continuously monitors your third-parties to ensure that issues don’t reappear and alerts you when new issues are found.
-
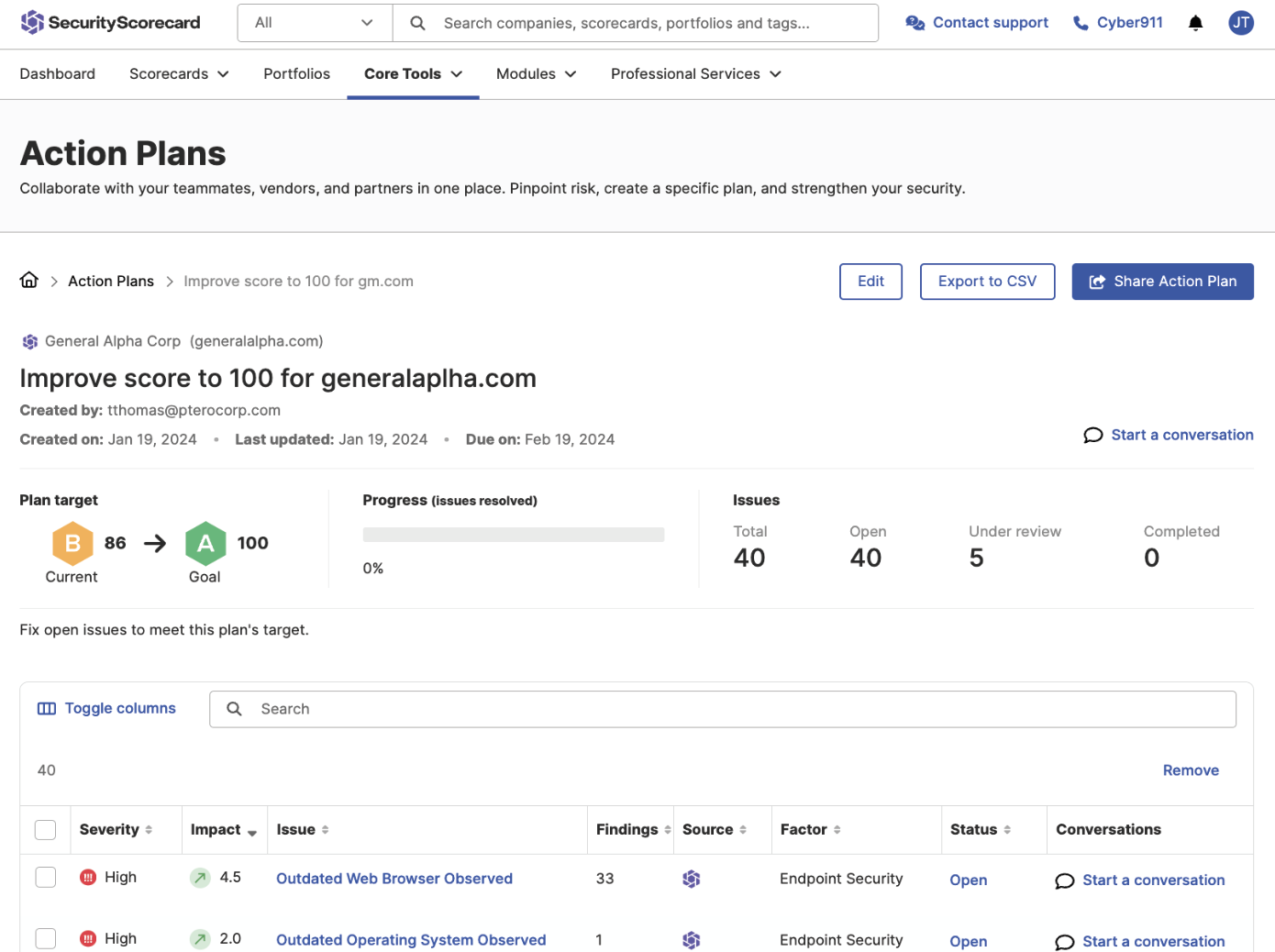
Score and Action Plans
Streamline collaboration with internal stakeholders and their third-parties in one dashboard, and create plans for your vendors to improve their security posture
- Generate dynamic remediation plans
- Prioritize critical vulnerabilities and assign individuals to fix issues
- See progress in real time, saving hours and reducing ecosystem risk. Eliminate email back and forths, manual spreadsheets
-
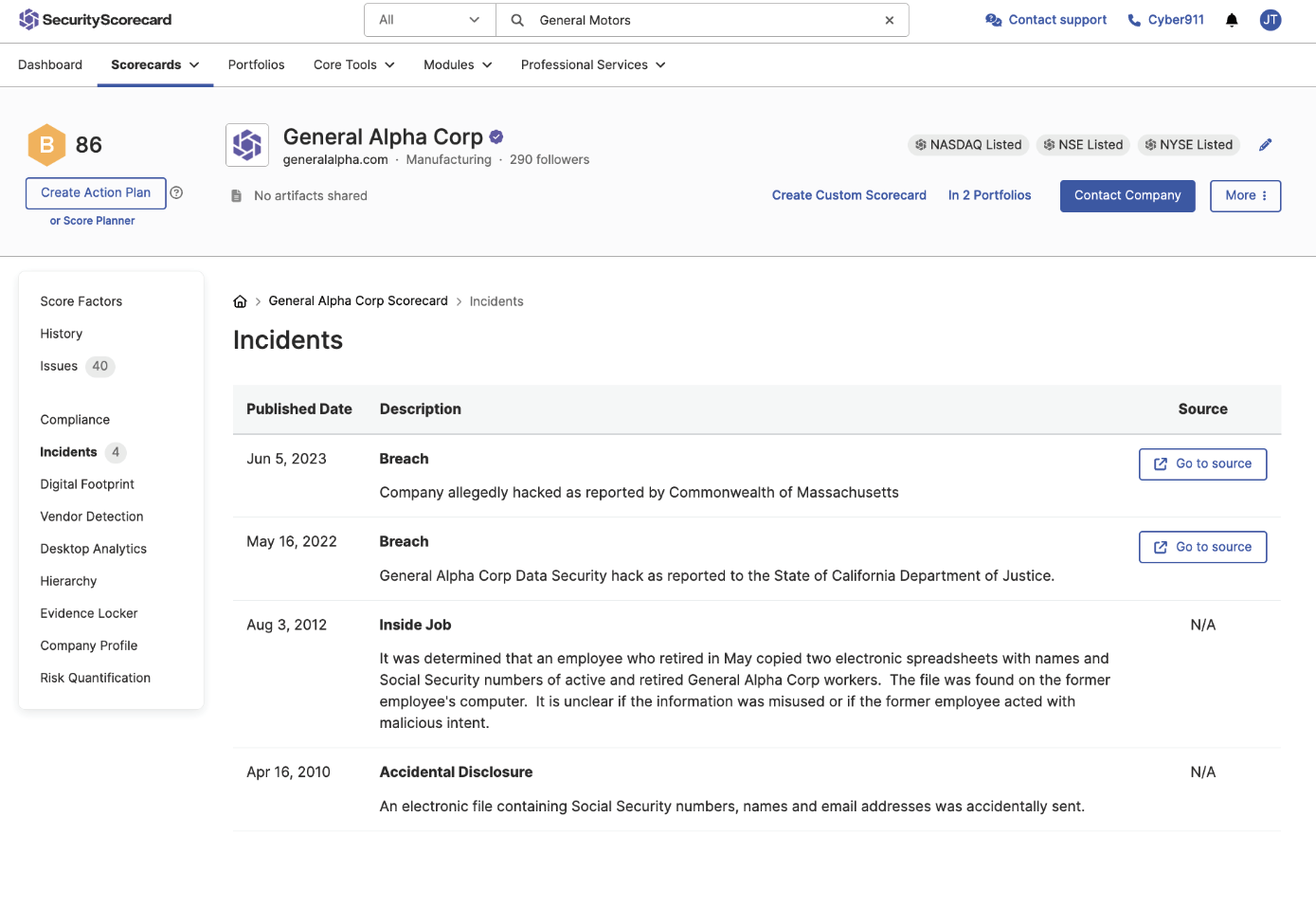
Incidents and Breaches
Continuously monitor and assess your third-parties with breach and incident data to ensure compliance and safeguard your supply chain against potential cyber threats.
- Proactively mitigate risk and stay ahead of threats with real-time notifications of third-party breaches and incidents
- Get detailed insights into security incidents across your vendor ecosystem to better prioritize responses and enhance your third-party risk management strategy
-
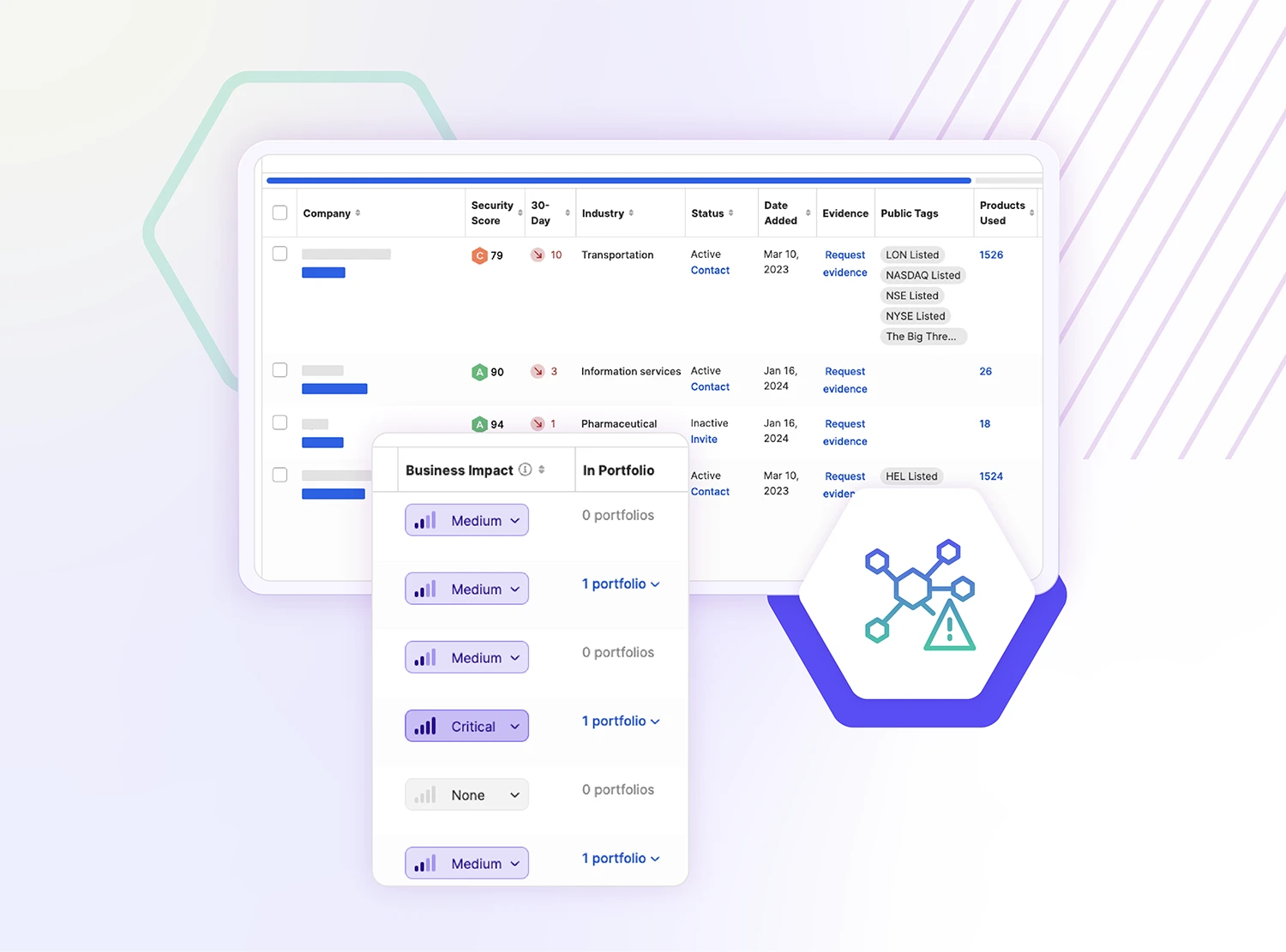
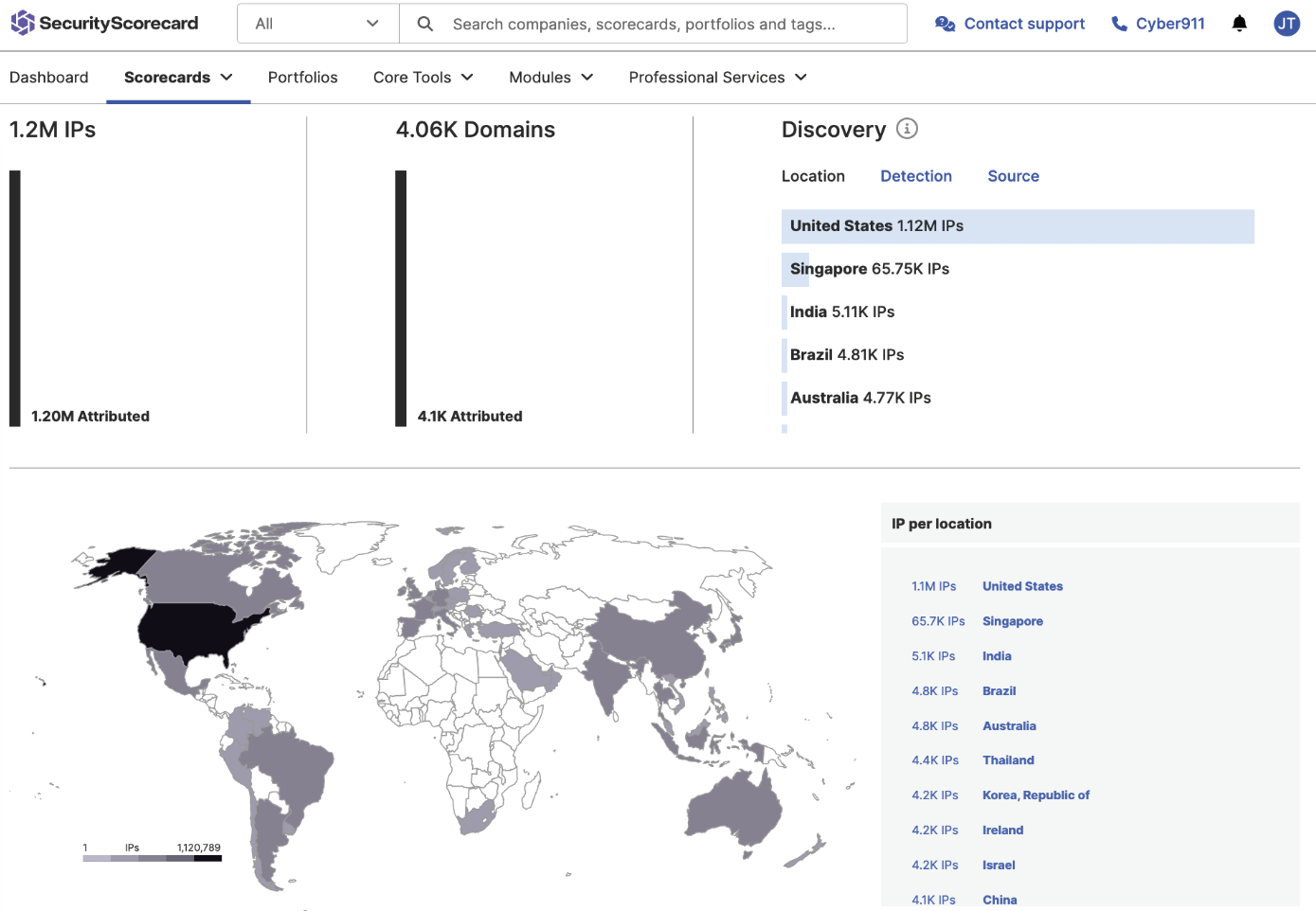
Digital Footprint
See the full picture of external attack surface for your supply chain, including potential vulnerabilities that hackers could exploit
- Leverage real-time monitoring to proactively identify risks
- Prioritize risk by identifying which parts of the attack surface pose the greatest threat
- Initiate remediation for specific assets. Focus remediation efforts on the most vulnerable areas of your supply chain, and act before they can be exploited by malicious actors
-
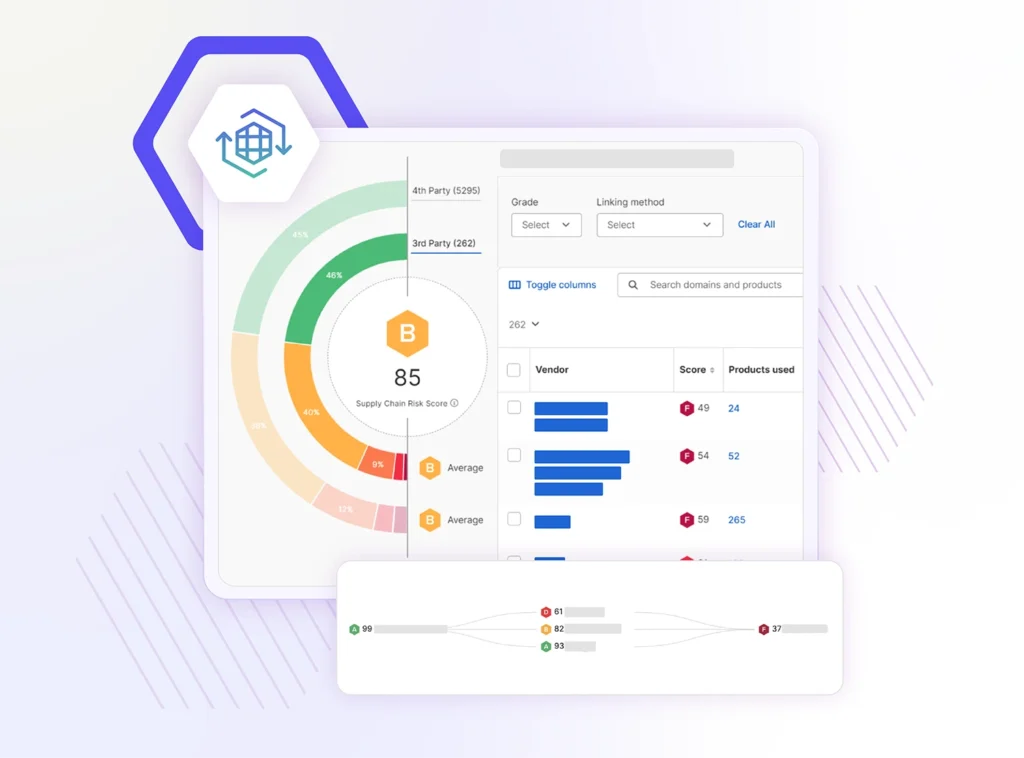
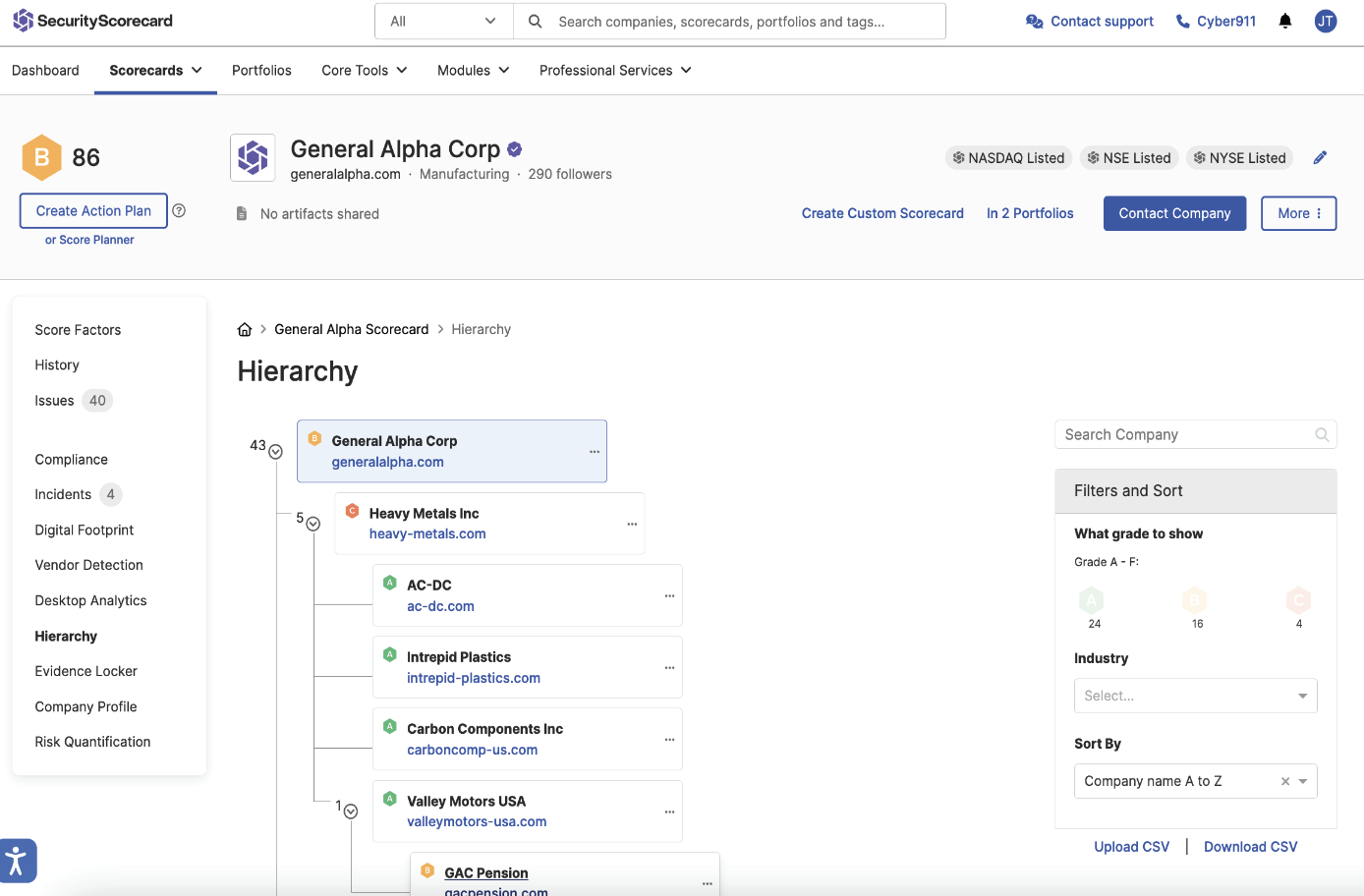
Hierarchy
View the overall risk of your parent organization and their subsidiaries.
- Continuously monitor the security posture of your parent organization and its subsidiaries in one hierarchical view.
- Understand common risks across your overall entity and quickly prioritize subsidiaries that require additional resources or attention to reduce their cyber risk.
-
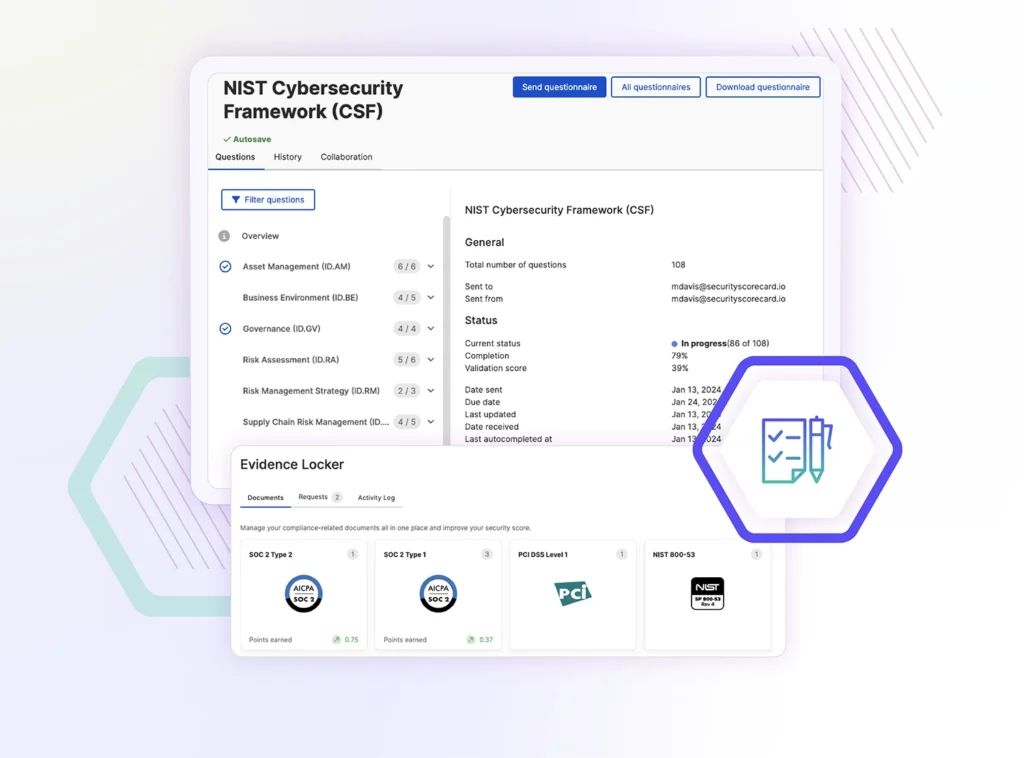
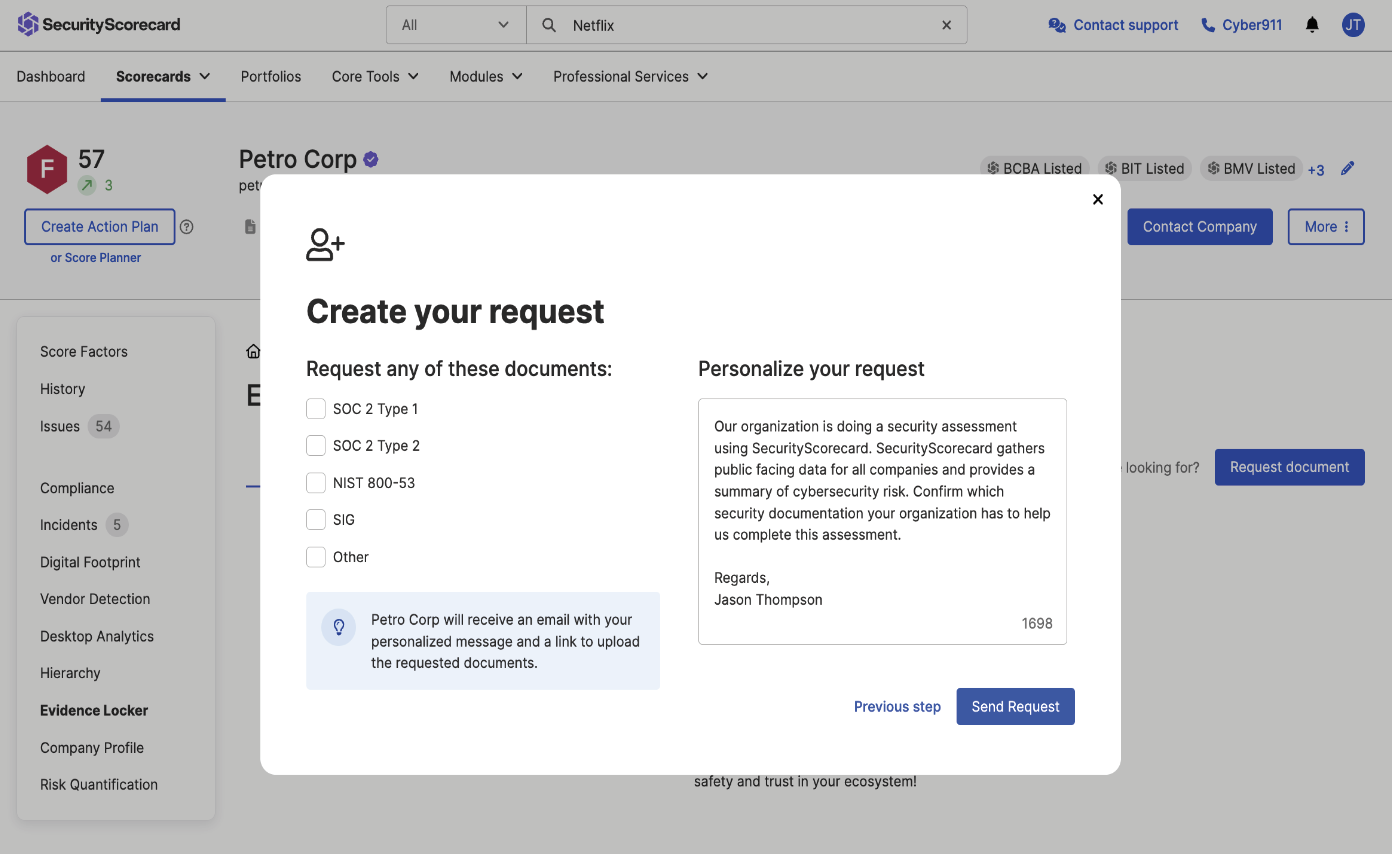
Evidence Locker
Managing compliance evidence is a job in itself. Whether you’re vetting potential vendors, or you are a vendor trying to demonstrate compliance to a prospect, curating multiple files for compliance evidence takes significant time and effort. With SecurityScorecard’s Evidence Locker, you can view and manage these files simply.
- Vendor Risk Managers leverage Evidence Locker to quickly vet your vendors’ or potential vendors’ compliance artifacts.
- Vendors can showcase their compliance evidence in one place and reduce the time spent sending artifacts to customers and prospects.
Critical capabilities
-

The world's most trusted security data
Harness the power of the world’s most trusted and accurate security intelligence to identify risk
-
Extensible platform designed to scale
An all-in-one, modular platform enables you to scale as your TRPM program matures
-

AI and analytics that drive results
Move beyond the hype and put your trust in SecurityScorecard’s decade of experience in AI and analytics
-

Industry leading threat & risk telemetry
See more than you ever thought possible with the industry’s leading proprietary intelligence dataset
Hear from our customers
-
"It is an absolutely necessary investment to have cyber-resilient companies in your business ecosystem."
Ronaldo Andrade CISO and Head of IT, Horiens Risk AdvisorsRead More1 / 0-
83 %
time reduction on self monitoring
-
Actionable Insights into supply chain risks
-
Streamlined approach to vendor assessments
-
-
"I can use SecurityScorecard data to make the logical leap that this is, in fact, a secure vendor. That allows us to save time and get to the conclusion we need to as quickly as we can."
Brian Harrell VP and Chief Security Officer, AvangridRead More1 / 0
FAQs
What is Third-party Risk Management?
Third-Party Risk Management (TPRM) refers to the process of identifying, assessing, and mitigating risks organizations face when engaging with external vendors, suppliers, and service providers. These risks can include cybersecurity vulnerabilities, regulatory compliance failures, financial risks, and reputational damage.
Third parties often have access to intellectual property, sensitive data, personally identifiable information (PII), protected health information (PHI), or systems. Therefore, it’s essential for businesses to continuously monitor these external partners for potential risks that could impact the organization’s security, performance, or compliance.
Who is Responsible for TPRM?
The responsibility for Third-Party Risk Management (TPRM) typically lies with multiple departments across an organization. The Chief Information Security Officer (CISO) and the Risk & Compliance teams usually oversee the implementation and monitoring of TPRM programs. Procurement Teams, Vendor Risk Managers, and IT Security Managers also play key roles in evaluating third-party vendors and ensuring they meet security standards.
Ultimately, various departments and people work together to manage vendors and ensure that cyber security third party management practices align with business goals and regulatory requirements.
Why is Third-Party Risk Management Important?
Third-party risk management is critical because it helps businesses protect themselves from cybersecurity breaches, financial losses, and compliance violations caused by external vendors. Proactively identifying potential risks within the vendor ecosystem helps security teams identify vulnerabilities, the security team ensures that vulnerabilities are discovered before the business can be exploited.
Since 63% of data breaches are linked in some way to third parties such as contractors, suppliers, or vendors that have access to a business system, third-party cyber security risk management helps organizations keep track of all their vendors,, reducing the likelihood of widespread risks.
A strong third-party risk management cyber security program also ensures compliance with industry regulations and reduces overall business risk by identifying vulnerabilities early on.
How to Evaluate Third Parties?
When evaluating third parties, it’s important to systematically assess their security, business continuity, and compliance with relevant regulations. This process typically includes:
- Risk Assessments: Initial and ongoing assessments of vendors’ security practices and risk levels.
- Security Ratings: Using platforms like SecurityScorecard to assign scores based on factors like network security, DNS health, and patching cadence.
- Questionnaires: Vendors complete standardized security questionnaires disclosing their compliance with industry standards.
- Continuous Monitoring: Continuously track vendor activities, incident reports, and vulnerability updates.