SecurityScorecard Investigation and Response to New and Widespread OpenSSL 3.X Vulnerability
-
February 24, 2025Massive Botnet Targets M365 with Stealthy Password Spraying Attacks
-
February 13, 2025Lazarus Group is Infecting Open-Source Code. Are You at Risk?
-
February 6, 2025Insurance Carriers Face Unprecedented Supply Chain Cyber Threats
-
January 29, 2025Operation Phantom Circuit: North Korea’s Global Data Exfiltration Campaign
-
January 21, 2025Security Assessment of the Top 100 U.S. Gov’t Contractors
Executive Summary
- News surfaced of a widespread and critical vulnerability affecting OpenSSL versions 3.0 and above on October 25, with details to be made available on November 1.
- Prior to the vulnerability’s publication, SecurityScorecard developed an emergency informational signal to give customers visibility into products that may be affected. That signal is now available in SecurityScorecard’s ratings platform and visible in our threat intelligence platform, Attack Surface Intelligence.
- SecurityScorecard’s STRIKE team began an investigation into this vulnerability shortly after its publication and identified IP addresses Internet infrastructure linked to malicious activity that could lead or have already led to threat actors to identify vulnerable products. Links include ties to APT-C-23 (an APT group believed to conduct espionage on behalf of Hamas) as well as the Kimsuky and Lazarus groups (Democratic People’s Republic of Korea).
Background
On October 25, open source security specialist Mark Cox announced that the OpenSSL 3.0.7 update to be released on November 1 would correct a new, critical vulnerability found to affect OpenSSL versions 3.0 and forward. Other commentators subsequently warned that the vulnerability would prove to be especially significant, meriting the rapid isolation of any publicly exposed OpenSSL 3.x services. Given OpenSSL’s wide use in other products, the extent of the vulnerability is likely quite considerable.
Findings
Extent of Vulnerability
SecurityScorecard analyzed the data coming from our global sensor network to assess the distribution of affected services and identify possible exploitation of the vulnerability. As reflected below, SecurityScorecard observed affected products in use on every continent except for Antarctica, with particularly heavy clusters of observations in Europe and the U.S.
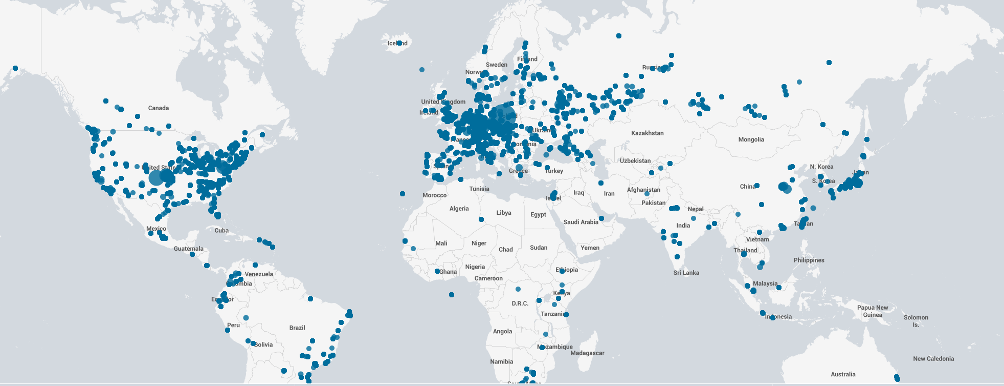
Global Distribution of Vulnerable OpenSSL in the Last Seven Days shown from the Splunk visualization of data powering SecurityScorecard’s Attack Surface Intelligence (ASI)
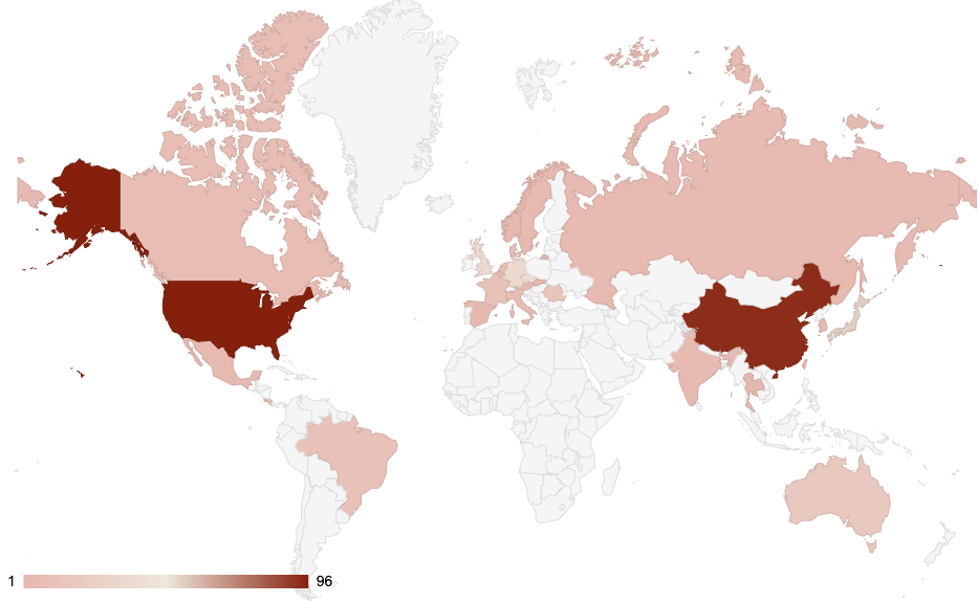
By number of observations in the last seven days, as of 10:30 PM EST on October 29, the following are the twenty countries that saw the heaviest concentrations of products using affected versions:
- United States (1617 observations, roughly 27.3 percent of the total)
- Russia (775 observations, roughly 13.1 percent of the total)
- Japan (449 observations, roughly 7.6 percent of the total)
- Germany (442 observations, roughly 7.5 percent of total)
- China (334 observations, roughly 5.6 percent of the total)
- Czechia 308 observations, roughly 5.2 percent of the total)
- United Kingdom (260 observations, roughly 4.4 percent of the total)
- France (258 observations, roughly 4.4 percent of the total)
- Australia (183 observations, roughly 3.1 percent of the total)
- Netherlands (134 observations, roughly 2.2 percent of the total)
- Canada (132 observations, roughly 2.2 percent of the total)
- Poland (73 observations, roughly 1.2 percent of the total)
- Singapore (67 observations, roughly 1.1 percent of the total)
- Italy (66 observations, roughly 1.1 percent of the total)
- Brazil (54 observations, roughly 0.9 percent of the total)
- Israel (51 observations, roughly 0.9 percent of the total)
- India (39 observations, roughly 0.7 percent of the total)
- Denmark (39 observations, roughly 0.7 percent of the total)
- Switzerland (36 observations, roughly 0.6 percent of the total)
- Sweden (33 observations, roughly 0.6 percent of the total)
Global Distribution of Products
SecurityScorecard subsequently queried its scan data to analyze the geographic distribution of affected products observed in a twenty-four hour period from October 28 to 29. Overall, Apache httpd was particularly heavily represented within these results: of the 474 total observations, 331 were observations of Apache httpd. However, broken down by country, China accounted for the highest concentrations of affected products, with observations of Microsoft Windows RPC and Apache httpd in use there accounting for the two largest percentages of observations (approximately 13 percent each) and Microsoft Windows netbios-ssn there accounting for the next highest percentage (roughly 12.6 percent). Apache httpd running in the U.S. was responsible for the next two highest concentrations, with a version using AlmaLinux responsible for approximately 8.1 percent and and a version using Fedora Linux responsible for approximately 7.6 percent of observations. After Apache httpd, OpenSSH was the second-most heavily represented product in this dataset, with sixty-one observations in total.
To see all OpenSSL hits in Attack Surface Intelligence (ASI), anyone with an account on SecurityScorecard (even a freemium account) can use the following query: https://platform.securityscorecard.io/#/asi/search/OpenSSL?sort=min_scorecard_grade (all raw text OpenSSL hits sorted by the minimum scorecard grade).
Another October 28 query of SecurityScorecard’s scan data to identify specific products observed using OpenSSL 3.x returned 116 results. Within these results, IP cameras were heavily represented: only five of the 116 were for products other than cameras. These results are, additionally, visible in SecurityScorecard’s Attack Surface Intelligence (ASI) tool’s findings for individual IP addresses (this information is available by port; the affected IP camera indicated below runs at port 80 and is therefore visible in the information for that port; affected versions of OpenSSH would similarly be visible in the findings for port 22 of IP addresses where it is in use). For a wider collection of results, users can search for affected products in ASI by using “OpenSSL” as a query.
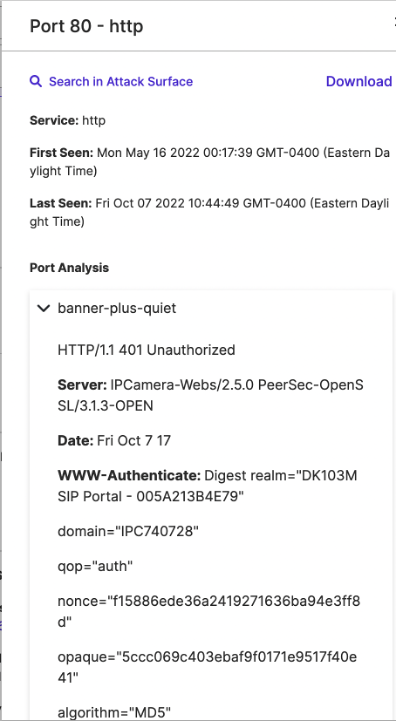
Attack Surface Intelligence (ASI) View of Vulnerable Product Running at Port 80
Investigation: Suspicious Traffic to IP Addresses Running Affected Products
In order to identify possible exploitation of the new vulnerability, our researchers leveraged SecurityScorecard’s exclusive access to IP network flow (netflow) data to analyze one week of traffic involving the ten most recently scanned IP addresses where SecurityScorecard detected OpenSSL version 3.x products. We then limited these results to flows that occurred over port 80 (where the detected products were observed running) and then consulted public cybersecurity resources to identify IP addresses previously linked to malicious activity. This yielded a total of twenty-one possibly malicious IP addresses that communicated with the possibly-affected IP addresses:
- 183.136.225[.]35 (Chinese ISP)
- Twelve vendors have linked 183.136.225[.]35 to malware or malicious activity and community members have observed it contacting HTTP and HTTPS honeypots.
- 92.118.39[.]30 (Romanian ISP)
- Ten vendors have linked 92.118.39[.]30 to malware or malicious activity and community members have observed it contacting HTTP and HTTPS honeypots.
- 194.26.228[.]174 (Russian ISP)
- Seven vendors have linked 194.26.228[.]174 to malware or malicious activity and community members have observed it contacting HTTP and HTTPS honeypots and conducting SSH brute force and DNS amplification attacks.
- 92.204.135[.]83 (United States ISP – GoDaddy)
- Six vendors have linked 92.204.135[.]83 to malware or malicious activity.
- 159.203.111[.]193 (United States ISP – Digital Ocean)
- Six vendors have linked 159.203.111[.]193 to phishing, malware, or malicious activity.
- The ISP involved in this traffic, DigitalOcean, is known to often host malicious C2 infrastructure.
- 151.106.38[.]95 (United States ISP – Digital Ocean)
- Six vendors have linked 151.106.38[.]95 to malware or malicious activity and a community member has observed it conducting aggressive network scans.
- 92.118.39[.]78 (United Kingdom ISP on US IP space)
- Six vendors have linked 92.118.39[.]78 to malware or malicious activity and a community member has observed it contacting HTTP and HTTPS honeypots.
- 61.147.15[.]65 (Chinese ISP – Chinanet)
- Six vendors have linked 61.147.15[.]65 to malware or malicious activity and community members have observed it contacting HTTP and HTTPS honeypots and identified it as a Metasploit command-and-control (C2) IP address.
- 93.184.220[.]29 (United Kingdom ISP)
- Three vendors have linked 93.184.220[.]29 to malware or malicious activity and 38 community members have identified it as part of infrastructure supporting malware including ransomware, cryptominers, and trojans and linked it to attempts to exploit known vulnerabilities.
- 142.93.208[.]149 (United States ISP – Digital Ocean)
- Three vendors have linked 142.93.208[.]149 to malware or malicious activity.
- 14.141.178[.]37 (Indian ISP)
- One vendor has linked 14.141.178[.]37 to malware.
- 93.184.221[.]240 (United Kingdom ISP)
- Two vendors have linked 93.184.221.240 to malware and malicious activity and community members have identified it as part of infrastructure supporting malware including ransomware and trojans and linked it to phishing.
- 209.197.3[.]8 (United States ISP)
- Community members have identified 209.197.3[.]8 as part of infrastructure supporting malware including ransomware and trojans and linked it to phishing.
- 112.216.43[.]51 (Republic of Korea ISP)
- One vendor has linked 112.216.43[.]51 to malware and a community member has observed it contacting HTTP and HTTPS honeypots.
- 152.199.19[.]161 (United Kingdom ISP on US IP space)
- 26+ Community members have identified 152.199.19[.]161 as part of infrastructure supporting malware including the Emotet trojan and linked it to phishing including from Russian state actors.
- 34.107.221[.]82 (United States ISP – Google Cloud)
- One vendor has linked 34.107.221[.]82 to malware and community members have identified it as part of infrastructure supporting malware including ransomware and trojans.
- 47.88.91[.]115 (Chinese ISP – Alibaba)
- One vendor has linked 47.88.91[.]115 to malicious activity.
- 35.224.170[.]84 (United States ISP – Google Cloud)
- One vendor has linked 35.224.170[.]84 to malware and community members have deemed it suspicious.
- 64.227.120[.]229 (United States ISP – Digital Ocean)
- One vendor has linked 64.227.120[.]229 to malicious activity.
- 142.250.186[.]163 (United States ISP – Google)
- One vendor has linked 142.250.186[.]163 to malware and community members have linked it to fraud.
- 80.144.170[.]171 (German ISP)
- One vendor has linked 80.144.170[.]171 to malicious activity.
These results do not necessarily indicate active targeting of the soon-to-be-disclosed vulnerability. However, they may reflect the ease with which a threat actor could identify affected products. For example, activity originating from the addresses previously linked to network scans or attacks on HTTP and HTTPS honeypots could incidentally identify affected products running at HTTP and HTTPS ports initially accessed in the course of everyday operations.
While members of the wider cybersecurity community have observed each of these engaging in malicious activity, SecurityScorecard’s internal tracking via our in-house Malware Information Sharing Platform (MISP) deployment, which brings in both public and private feeds from the security community, can offer additional insights into their behavior. Of the IP addresses observed communicating with the sample group of IP where vulnerable products are in use, three appear in SecurityScorecard’s internal threat intelligence platform and may therefore be linked to malicious activity previously researched by SecurityScorecard. Those are:
- 93.184.220[.]29 (Link to ASI) – Researchers linked this IP address to activity attributed to Kimsuky, an advanced persistent threat (APT) group believed to act on behalf of the Democratic People’s Republic of Korea (North Korea) in 2021.
- 93.184.221[.]240 (Link to ASI) – Researchers linked this IP address to activity attributed to the Lazarus Group, an APT group believed to act on behalf of the Democratic People’s Republic of Korea (North Korea), in 2021.
- 209.197.3[.]8 (Link to ASI) – Our internal threat intelligence shows this same IP occuring in netflow tied to US state and local government attacks. Additionally, the IP previously appeared in activity tied to APT-C-23 (an APT group believed to conduct espionage on behalf of Hamas) in 2021 and a 2022 breach (possibly resulting from a ransomware attack) at a U.S.-based technology firm servicing the finance industry. A strategic partner’s APT DNS data also indicates that a domain with established ties to APT activity, cds.d2s7q6s2.hwcdn[.]net, has resolved to 209.197.3[.]8 for at least the past seven days.
SecurityScorecard researchers subsequently collected a sample of traffic to and from the vendor-detected IP addresses above. The five IP addresses that communicated with the vendor-detected IP addresses most frequently within a one-week monitoring period are the following:
- 103.26.37[.]171 (a medical center in the Philippines)
- 154.68.228[.]22 (Nigerian Research and Education Network)
- 154.68.195[.]210 (Nigerian Research and Education Network)
- 168.167.93[.]8 (Botswana ISP)
- 62.90.220[.]166 (Israeli ISP)
While not necessarily related to the exploitation of the new vulnerability, these communications may indicate targeting of organizations using those IP addresses. However, ASI does indicate that an affected product, OpenSSH, is in use at one of the Nigerian IP addresses listed above.
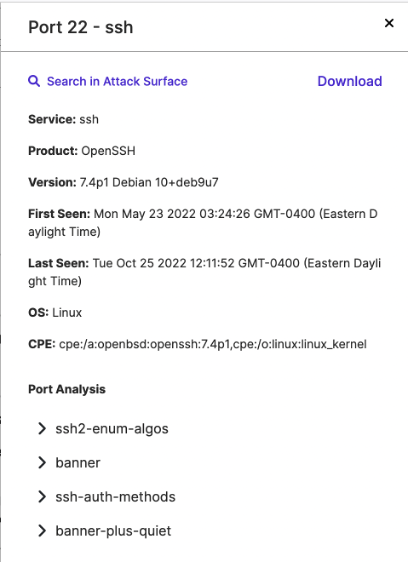
Attack Surface Intelligence (ASI) View of Vulnerable Product Running at Port 22 of IP Address Communicating with Suspicious IP Addresses
Mitigation for SecurityScorecard Customers
New Ratings Issue Type
In preparation for the publication of this new vulnerability, SecurityScorecard rapidly developed an emergency informational signal to inform customers that may be affected. This new signal is:
October 2022 OpenSSL 3.X Vulnerability.
Risk
We detected a version of OpenSSL with a critical vulnerability that could expose this organization to data theft and other types of attacks.
Description
OpenSSL (secure socket layer) is an open-source software library for applications that anonymize communications over computer networks and prevent malicious eavesdropping from threat actors. It is widely used by internet servers, including most HTTPS websites. A critical vulnerability for OpenSSL versions 3.0.0 through 3.0.6 could expose memory contents and reveal user information. Threat actors could also exploit this flaw remotely to compromise server private keys or execute malicious code. More details about the vulnerability, such as its CVE ID, will continue to emerge. The OpenSSL project will release a version 3.0.7 patch on November 1, 2022. We detected this vulnerability by identifying an affected version of SSL running on an open port, as indicated in the Findings table below.
Recommendation
Note the SSL versions in the Findings table below. Update vulnerable versions to the 3.0.7 patch as soon as it becomes available on November 1, 2022.
References
OpenSSL warns of critical security vulnerability with upcoming patch
Dig Deeper with SecurityScorecard Threat Intelligence
In addition to the visibility offered by the new signal in our ratings platform, SecurityScorecard’s other tools and services can support organizations’ efforts to respond to and defend against this vulnerability and its exploitation. SecurityScorecard’s new Attack Surface Intelligence (ASI) solution gives you direct access to SecurityScorecard’s deep threat intelligence data through a global tab on the ratings platform and via API, all of which can contribute to improved visibility into internal and external resources, supporting the infrastructure management advised above.
ASI analyzes billions of sources to provide deep threat intelligence and visibility into any IP, network, domain, or vendor’s attack surface risk, from a single pane of glass. This helps a variety of customers do more with the petabytes of data that form the basis of SecurityScorecard Ratings, including identifying all of an organization’s connected assets, exposing unknown threats, conducting investigations at scale, and prioritizing vendor remediation with actionable intelligence.
ASI is built into SecurityScorecard’s ratings platform through an enhanced Portfolio view or Global search across all Internet assets, leaked credentials, and infections and metadata from the largest malware sinkhole in the world. Access ASI today on the SecurityScorecard platform with 20 free search queries per month or request a demo on our website.
SecurityScorecard’s threat research and intelligence services could be the competitive advantage organizations need to stay ahead of fast-moving threat actors like those exploiting these new vulnerabilities. For more custom insights from our team with 100+ years of combined threat research and investigation experience, or more details on these findings, please contact us to discuss our Cyber Risk Intelligence as a Service (CRIaaS) offering. The above investigation can offer a trustworthy but preliminary view of our capabilities. Our team can continue diving into these details, especially with the ability to provide further support by working with on-site staff.
If you believe your organization to be under immediate threat from actors linked to this new threat, SecurityScorecard also provides managed incident response and digital forensics teams as a professional service driven by a large group of former law enforcement and private sector experts with decades of experience in the space. For immediate support from our teams, please contact us.




