New Intrusion Campaign Targeting Users of Popular Business Communication Software
Executive Summary
- On March 29, cybersecurity vendors announced that a new intrusion campaign had targeted users of business communication software company 3CX’s desktop client through a supply-chain attack.
- Initial reports have attributed the activity to the threat actor group tracked as Labyrinth Chollima, which is believed to conduct espionage on behalf of the North Korean government.
- Shortly after warnings of the attack, the SecurityScorecard Threat Research, Intelligence, Knowledge, and Engagement (STRIKE) Team began its investigation.
- Our Attack Surface Intelligence tool has revealed a large population of IP addresses where possibly affected 3CX software is in use.
- Our global network flow (NetFlow) analysis capability (available via professional services) has uncovered possibly suspicious communications involving these IP addresses.
Background
On March 29, cybersecurity vendors announced that a new intrusion campaign had targeted users of business communication software company 3CX’s desktop client, 3CXDesktopApp, through a supply-chain attack. On March 30, 3CX offered further comment, noting that a recent update to the Windows and Mac OS versions of the 3CX desktop client had included a compromised library.
The versions containing this library could engage in malicious activity, including beaconing to threat actor infrastructure and delivering additional malware as a second-stage payload. It could eventually lead, in some cases (though their number is reportedly quite limited), to hands-on-keyboard activity by an attacker.
The company’s announcement regarding the attack notes that, in most cases, the malicious files appear dormant.; 3CX believes the attack was highly targeted, with the truly active stage of malicious activity enabled by the compromised files being limited to those cases of greatest interest to the threat actors responsible for it.
Analysts further noted that the behavior and encryption key of the malicious files downloaded by the compromised 3CX installer match those observed in previous activity attributed to Labyrinth Chollima – an advanced persistent threat (APT) group that the cybersecurity community believes to act on behalf of the government of the Democratic People’s Republic of Korea (DPRK). More specifically, researchers assess that it likely serves Bureau 121 of the DPRK’s Reconnaissance General Bureau (RGB).
The indicators of compromise (IoCs) contained in the available reports regarding this activity include beaconing domains, registrant email addresses for two of those domains, and file hashes, which are listed in the Appendix of this report. STRIKE Team researchers consulted internal and external data sources to identify further information.
Methodology
STRIKE Team researchers first consulted public WHOIS records for the domains other vendors had already included in their IoC lists in order to identify any possibly relevant information those records may contain. They then consulted a strategic partner’s passive DNS data to identify the IP addresses to which the domains had resolved most recently.
Researchers next consulted SecurityScorecard’s Attack Surface Intelligence tool to identify IP addresses belonging to possible targets of this campaign, first querying it for IP addresses where a 3CX product and Windows or Mac operating systems were in use.


Images 1-2: Attack Surface Intelligence revealed a large number of IP addresses where the affected software may be in use.
To narrow these results further, researchers additionally searched for IP addresses located in the United States and linked to the energy industry, knowing that Labyrinth Chollima has mainly targeted organizations based in the U.S. and South Korea and that a recent campaign using some of the same files targeted the energy sector.

Image 3: Researchers’ narrowed Attack Surface Intelligence query returned 229 results
Finally, researchers leveraged SecurityScorecard’s exclusive access to NetFlow data traffic that may reflect related malicious activity involving the identified IP address. From there, they collected a one-week sample of traffic in light of reports that the compromised update first began circulating a week prior to the query. They searched these results with the IP addresses found to have hosted the malicious domains to identify possible beaconing, selected the largest transfers of data (since large data transfers can reflect exfiltration), and finally searched for any transfers roughly equal in size to the malicious files distributed in the campaign.
Findings
One of the available reports has already linked two email addresses to the campaign: cliego.garcia@proton[.]me and philip.je@proton[.]me. These are, respectively, the registrant email addresses in the WHOIS records for two of its beaconing domains: azureonlinestorage[.]com and pbxcloudeservices[.]com. In addition to these, though, STRIKE Team researchers identified three more email addresses in other domains’ WHOIS records. These, and the related registrant names, are available in an appendix below.
Of the IP addresses returned by Attack Surface Intelligence when researchers searched for possibly affected energy-sector organizations based in the United States, researchers selected one attributed to a gas company for use when collecting a traffic sample using SecurityScorecard’s NetFlow data.
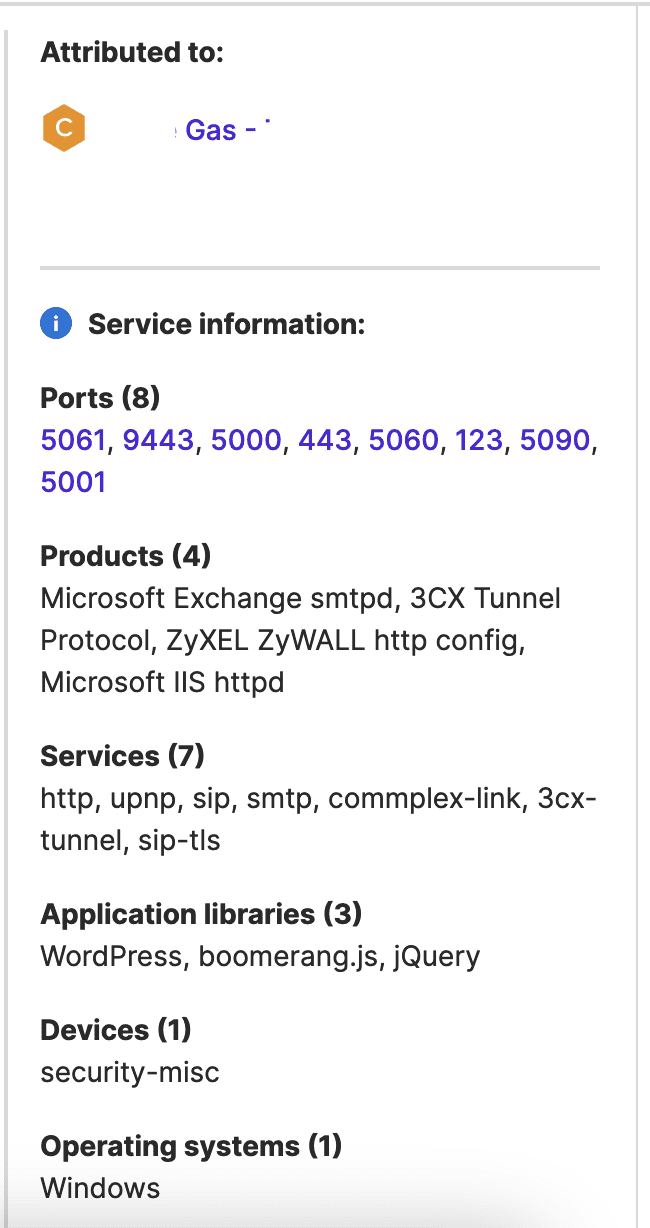
Image 4: Attack Surface Intelligence revealed a 3CX product in use at an IP address attributed to a gas company.
Searching the traffic sample involving this IP for communication with the IP addresses that hosted the beaconing domains returned no results. However, they did identify one transfer approximately the same size as the compromised binary file ffmpeg.dll (identified by the SHA-256 hash 7986bbaee8940da11ce089383521ab420c443ab7b15ed42aed91fd31ce833896), which other analysts have termed “the primary fulcrum” of the campaign. That file is 2.68 MB in size; the affected gas company-attributed IP address was involved in a transfer of a roughly similar size on March 24. While this traffic may be benign, it may merit additional attention for the sake of caution, if nothing else.
Additionally, researchers identified eight IP addresses (available in an appendix below) involved in large data transfers with the possibly affected IP address. While not necessarily related to the new Labyrinth Chollima-attributed campaign, these transfers may be cause for concern, as large data transfers can sometimes represent exfiltration by a threat actor.
Other cybersecurity vendors have already linked one of these eight, 45.55.41[.]244, to malicious activity, and all of them belong to large hosting providers. While this traffic could represent expected behavior, such as transfers to backups, given that threat actors have also abused these services in the past, these transfers may also merit attention, even if they are not related to the 3CX supply chain attack.
Recommended Mitigations
As of April 5th, 3CX has not yet released new versions of the affected software, but intends to make them available shortly. Currently, 3CX and Mandiant are conducting a full investigation of the attack and recommend the following mitigations.
- Continuous Endpoint Detection & Response (EDR) and Antivirus (AV) Scans for potential malware.
- Update affected software once an update is available.
- Ensure that the server application is updated.
- Uninstall the desktop application and use the 3CX web client (PWA) instead.
To assess possible impacts on their organization, readers can use the following queries in ASI: (and attributed_domain:'[organization’s domain]’ (and (or os_type:’Windows’ os_type:’Mac OS’ (and (or service:’3cx’ )))))
Appendix
Domain Registrant Information Not Previously Reported
- Msedgepackageinfo[.]com
- Registrant Name: Simpson Remey
- Registrant Email: Remey.Simpson@outlook[.]com
- Officeaddons[.]com
- Registrant Name: Jackie Caudill
- Registrant Email: jackiewcaudill@gmail[.]com
- Pbxphonenetwork[.]com
- Registrant Name: Harold Marable
- Registrant Email: haroldjmarable@gmail[.]com
IP Addresses Involved in Large Data Transfers
- 166.78.201[.]132
- 45.55.41[.]244
- 143.198.182[.]38
- 162.242.237[.]95
- 45.55.132[.]168
- 162.242.248[.]195
- 165.227.86[.]31
- 162.242.237[.]95




