The Forrester Wave™: Cybersecurity Risk Ratings Platforms, Q2 2024
Cyber Risk Intelligence Update: Hacktivist Involvement in Israel-Hamas War Reflects Possible Shift in Threat Actor Focus
The SecurityScorecard Threat Research, Intelligence, Knowledge, and Engagement (STRIKE) Team has continued its monitoring of threat actors involved in the war between Israel and Hamas and has integrated this monitoring into its ongoing deep and dark web (DDW) collections.
Key takeaways
Analysis of these collections appears, as of October 20, to support the following conclusions:
- Relatively low-sophistication hacktivist groups, motivated mainly by attention, have remained the most prominent cyber actors involved in the conflict.
- These groups’ recent message histories suggest that some of the most prominent groups’ targeting of organizations in Israel may have slowed somewhat after an initial period in approximately the first week of the war (October 7-14) in which they circulated a notably high volume of claims of attacks against Israeli organizations.
- Some groups have claimed no new attacks, while others appear to have focused more on targets outside Israel. The group-specific findings listed below are also discussed at greater length in the appendices following the conclusion of this update.
- The Persian-language, pro-Palestinian hacktivist channel Solomon’s Ring has not claimed an attack since October 8.
- KillNet Palestine (whose name suggests it is a Palestine-based or especially pro-Palestinian affiliate or sub-group of the Russian hacktivist group KIllNet) has posted no new content since the message announcing its channel’s foundation on October 13.
- The most recent claims of some groups, including both Cyber Av3ngers (a hacktivist group believed to act in support of Iranian interests) and the purportedly Palestinian Electronic_Tigers_Unit, are both non-specific and unsubstantiated.
- The pro-Palestinian, Arabic-language Force Electronic Quds channel has most recently highlighted its defensive capabilities rather than claiming attacks.
- Two of the three attacks the self-described “Yemeni Hackers” 1915 Team claimed on October 20 targeted Indian organizations.
- On October 15, Anonymous Sudan began claiming attacks against Kenyan targets in response to the Kenyan government’s support for Israel.
- Dark Storm Team’s most recent claim (October 18) was against Snapchat.
- KillNet’s most recent claim (made on October 14) was against a Ukrainian energy company.
Claims of attacks against Israeli targets have not, of course, stopped entirely.
- Anonymous Sudan claimed a DDoS against RedAlert (an Israeli missile attack alerting app targeted earlier in the conflict) on October 20.
- Ghosts of Palestine claimed attacks against Israeli government sites on October 19 and 20.
- The Moroccan Black Cyber Army claimed an attack against an Israeli gaming site and a theft of sensitive Israeli documents on October 20.
- The pro-Palestinian Muslim Cyber Army claimed one of the same attacks as Ghosts of Palestine on October 19 and it claimed a breach of Israeli citizens’ personal data on October 20.
- The long-standing Turkish hacktivist group AslanNeferler Tim claimed attacks against an Israeli weapons manufacturer on October 19 and the Israeli Air Force on October 15.
- SS Cyber Team made unsubstantiated claims of access to an Israeli database on October 17.
- As with the Muslim Cyber Army’s claim, this breach is unconfirmed and may simply re-circulate data exposed prior to the war.
Conclusion
While the claimed targeting of non-Israeli organizations is not a novel dimension of the cyber activity that has accompanied this war, its persistence appears noteworthy, especially when considered alongside the apparent decrease in some groups’ targeting of Israeli organizations. While the ground war continues to present risks of regional escalation, the recent attacks against Kenyan and Indian organizations illustrate just how far beyond the region the cyber conflict has already expanded.
Appendices: Group-Specific Findings
KillNet
Killnet’s most recently claimed attack occurred on October 14 and targeted a Ukrainian energy company. Given that KillNet has operated in support of Russian geopolitical interests for much of its history,and focused on targets related to the war in Ukraine for much of that history, this may reflect a return to form for the group.
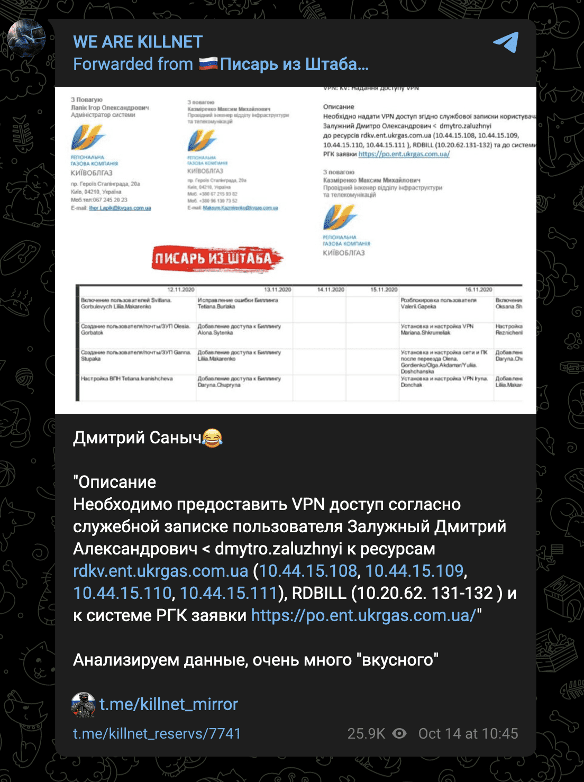
Image 1: KillNet’s most recent attack claim, an attempt against a Ukrainian energy company on October 14.
KILLNET PALESTINE
The Palestine-specific KillNet channel KILLNET PALESTINE was created Oct. 13, but as of October 20, has posted no new messages since then.

Image 2: KILLNET PALESTINE’s only post
Solomon’s Ring
This Persian-language, pro-Palestinian (and presumably Iranian) hacktivist group has been active since October 2022 and circulated its most recent claim regarding an attack (an unsupported claim to have stolen data from an “important Israeli data center”) on October 7, 2023.

Image 3: On October 7, Solomon’s Ring posted, “By Divine Power and Strength, one of Israel’s important data centers was hacked by the Solomon’s Ring hackers. Information is currently being downloaded. All of the data will be published shortly.”
As of October 20, the group has not circulated the data it claimed to be downloading on October 7 or provided other evidence that it compromised an Israeli data center. Indeed, it has not posted new content of any sort since October 11.
Dark Storm Team
Despite its avowed pro-Palestinian stance, Dark Strom [sic] Team has claimed attacks on targets—both inside Israel and out—throughout its history, and appears to have commercial motivations in addition to political ones. These aspects of its history suggest an outlook similar to KillNet’s.
The channel was created on August 18, 2023 and claimed its attack, which focused on Israel, on August 21.
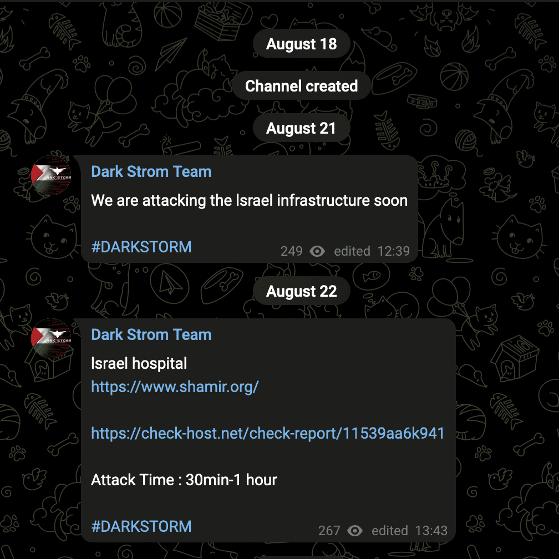
Image 4: Dark Storm Team’s first attack targeted an Israeli hospital.
With the start of the current war, the group targeted the Israeli government and sensitive industries in a series of claims on October 8 and 9.
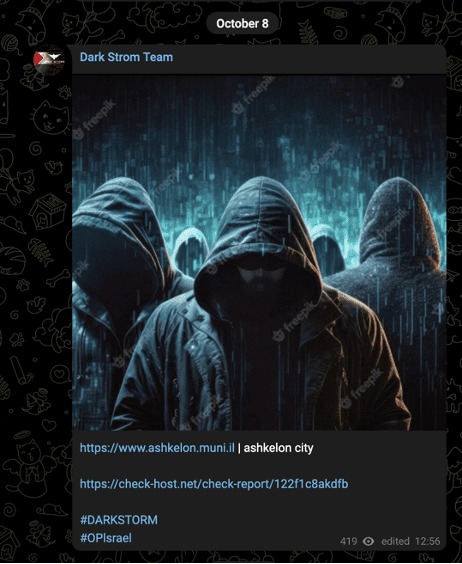
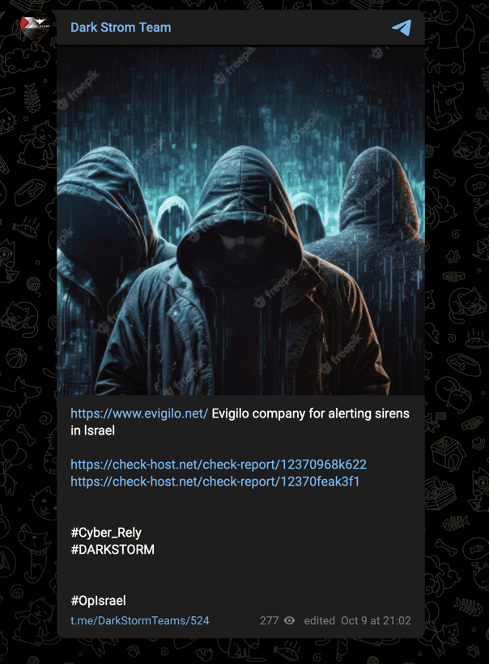
Images 5-6: The group claimed attacks against an Israeli municipality and alerting company early in the current conflict.
However, on October 15, the group claimed a DDoS attack against John F. Kennedy International Airport (JFK) in New York on the grounds that it is “the most welcoming airport for the Zionist entity.”
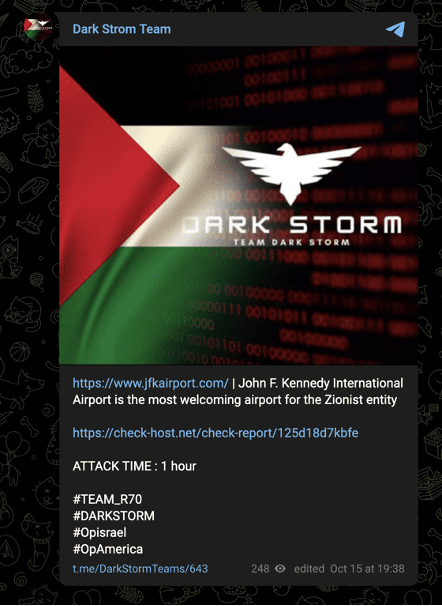
Image 7: Dark Strom Team claimed an attack against JFK airport on October 15.
This attack appears to prefigure an October 17 declaration that the group would target any entity perceived to support Israel.
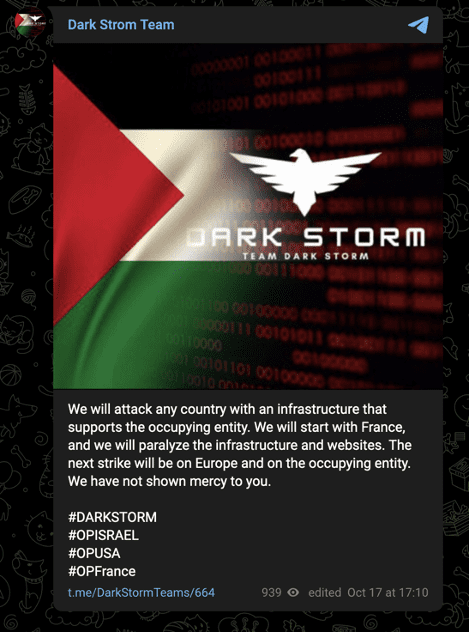
Image 8: The group declared it would target “any country…that supports the occupying entity” on October 17.
As of October 20, the most recent attack claim circulated by the channel was of an attempt against Snapchat on October 18, which may speak to the group’s international focus.
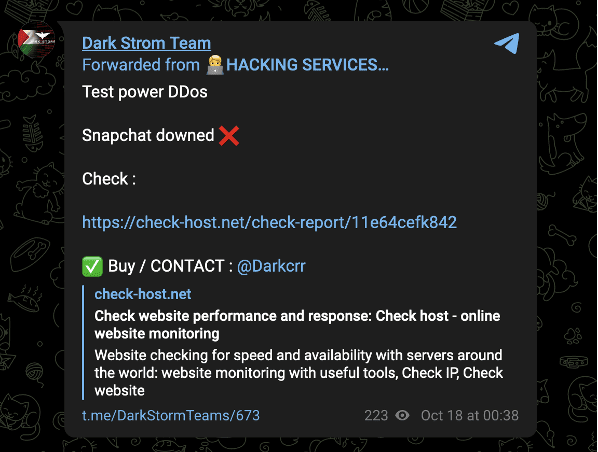
Image 9: Dark Strom Team claimed a disruption to Snapchat on October 18.
Closer study of the group’s history suggests that its motivations may be less strictly pro-Palestinian than they initially appear. Despite its declared sympathies with the Palestinian cause, it also advertises DDoS-as-a-service and commercial malware offerings, while also claiming attacks outside of Israel. This may simultaneously serve to bolster the group’s reputation (and thus drive business) and reflect a pro-Russian geopolitical orientation.
Indeed, the channel’s most recent messages additionally suggest that the group’s financial motivations have remained strong, despite the outbreak of the war. As of October 20, the six most recent messages displayed in the channel have all been advertisements.
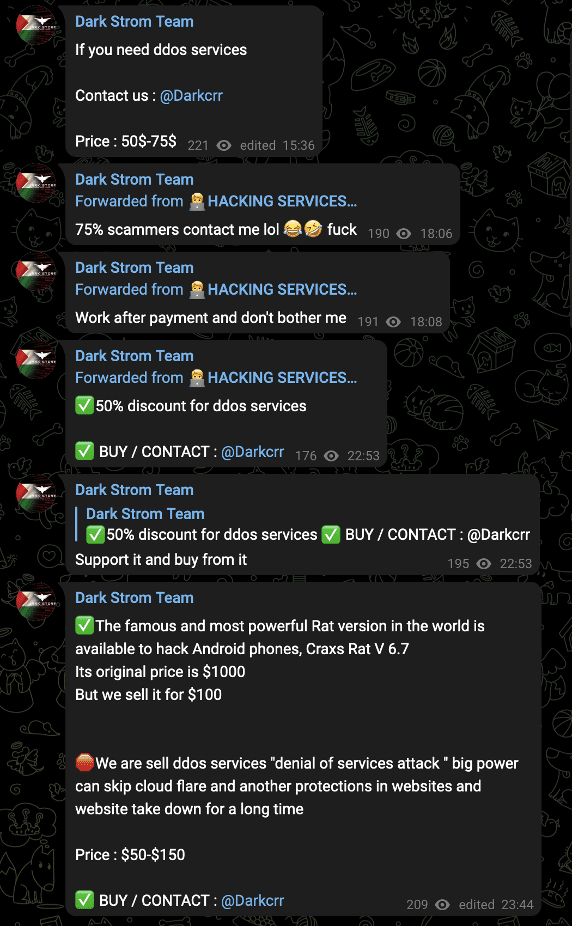
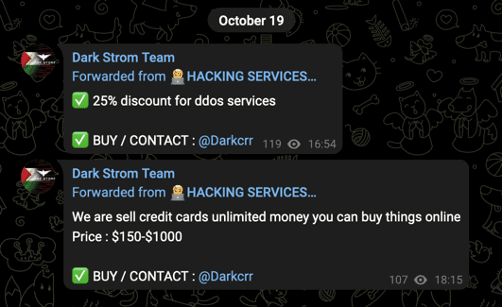
Images 10-11: Dark Strom Team’s most recent posts advertised cybercrime-as-a-service and commercial malware offerings.
These recent posts resemble earlier ones that also suggested financial motivations. The group offered a discount on its services on September 16 and circulated a “menu” of hacking services on September 22:
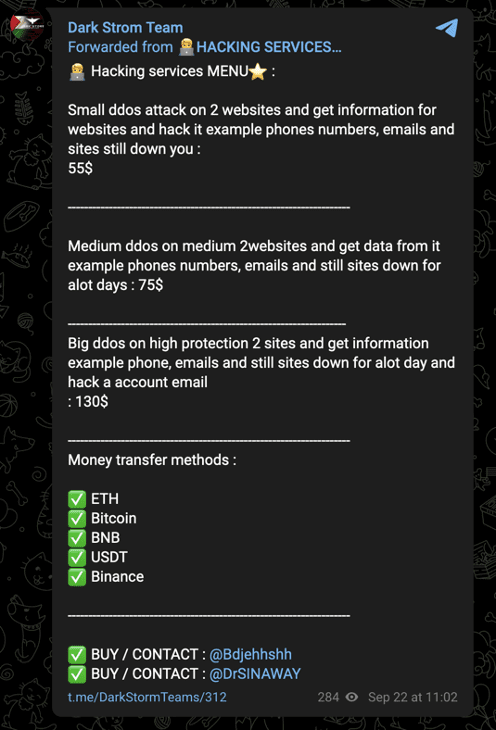
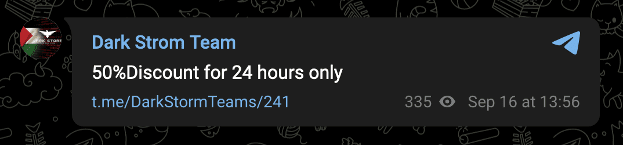
Images 12-13: Pre-war posts by Dark Strom Team reflect financial motivations.
The group’s long history of targeting entities outside of Israel may reflect attempts to build a reputation for commercial purposes, but may also suggest a broader anti-NATO (and therefore possibly pro-Russian) geopolitical outlook instead of a strictly pro-Palestinian one. The group claimed an attack against another U.S. airport’s website before the start of the war, and made no mention of American support for Israel when claiming the attack.
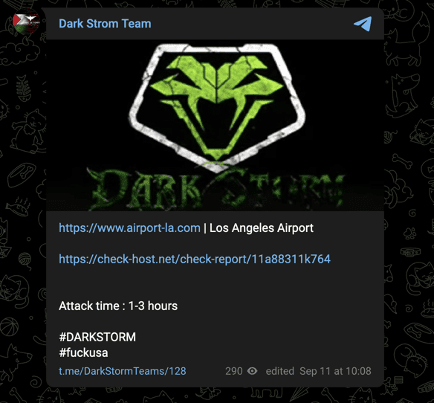
Image 14: the group claimed a previous attack against Los Angeles Airport on September 11.
This may suggest that the group’s activities have been less uniquely focused on the Palestinian cause than they initially appeared and may offer a point of comparison between Dark Strom Team and KillNet, which has also attempted attacks against US airports.
And even though the group’s messaging focuses on the Palestinian cause, it may (like KillNet and Anonymous Sudan) act in support of Russian geopolitical interests. For much of its history, it has targeted NATO member states and others that have declared their support for Ukraine.
One of the group’s first attacks on August 23 targeted Denmark, a September 10 attack targeted the Netherlands, and Dark Strom Team stated its intent to launch further attacks against NATO on September 14.
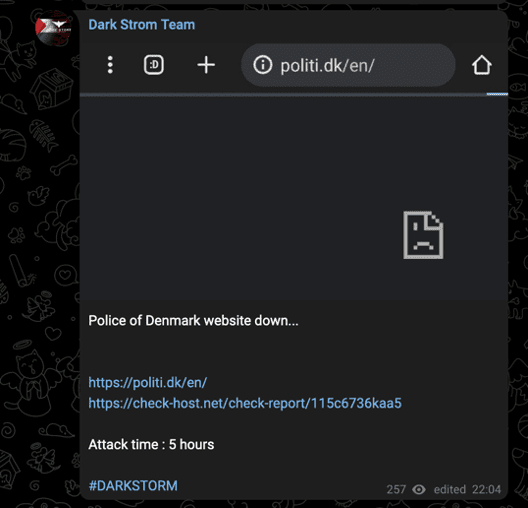
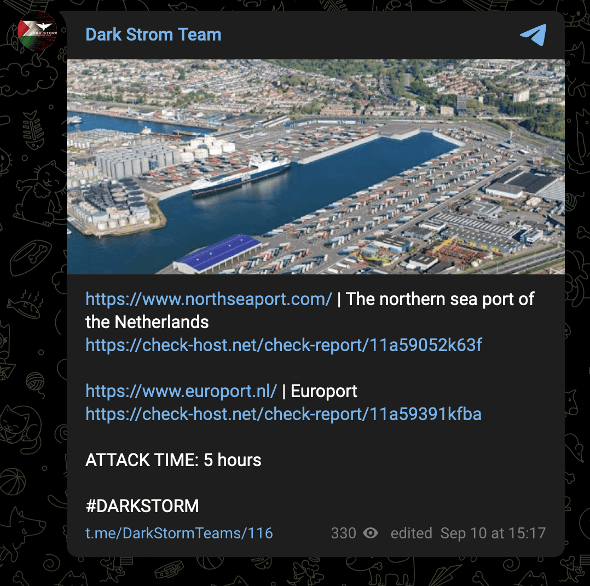
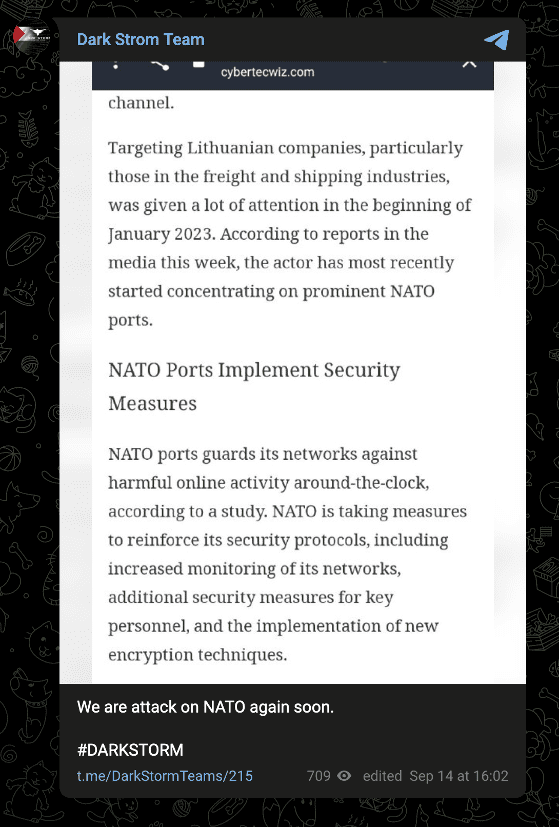
Images 15-17: The group has previously declared its intent to attack NATO-affiliated targets.
Taken together, the group’s cybercrime-as-a-service offerings and stated hostility to NATO suggest a profile similar to KillNet. Though it seemed to have strictly financial motivations at the time of its founding as a DDoS-as-a-Service group, it appears to have acquired more explicitly political motivations since the outbreak of the war between Russia and Ukraine. Subsequently, it has claimed a wide variety of attacks against entities in NATO member states.
1915 Team
1915 Team circulated images of a supposed leak of an Israeli military spokesperson’s personal data on October 20. The image may, however, be fabricated or the data may be outdated, as the image features a password dating back to 2019.
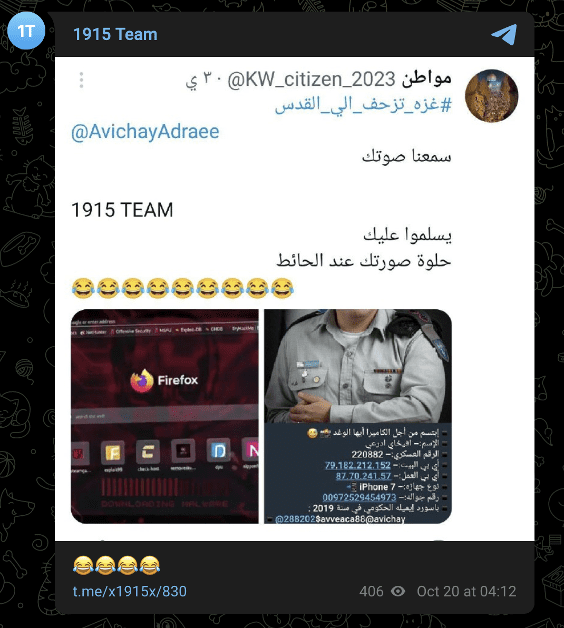
Image 18: The “Yemeni Hackers” of the 1915 Team circulated images purporting to contain an Israeli military spokesperson’s personal data on October 20.
Before that, the most specific claim they made regarding cyber activity was an October 11 announcement that they would launch ransomware attacks against Israel. However, these claims remain unsubstantiated as of October 20.
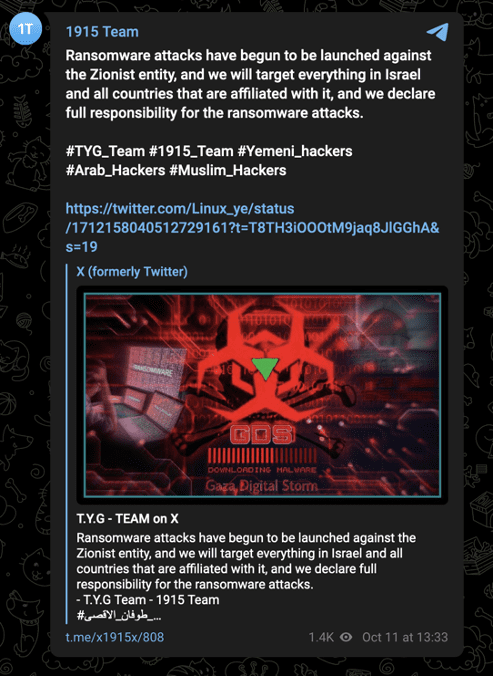
Image 19: 1915 Team previously shared claims of new ransomware attacks against Israeli and allied targets on October 11.
Electronic_Tigers_Unit
The Electronic_Tigers_Unit describes itself as a politically independent group of cyber actors committed to defending Muslims and resisting Israel. Its most recent post was on October 18, but its most recent claims of specific cyber activity occurred two days prior. On October 16, it circulated unsubstantiated claims of access to Israeli supervisory control and data acquisition (SCADA) systems and other critical infrastructure.
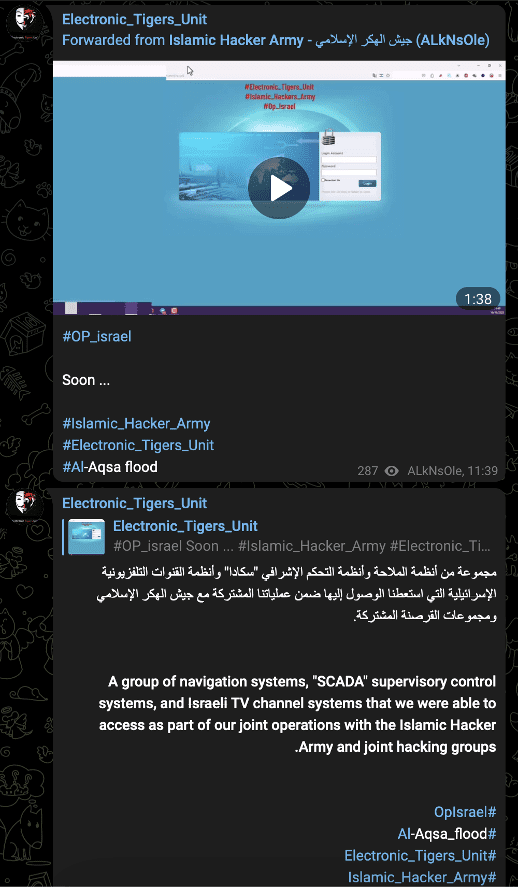
Image 20: Electronic_Tigers_Unit shared claims of access to Israeli infrastructure on October 16.
However, the video the group shared in support of these claims may not indicate access to uniquely sensitive systems specifically located in Israel; the only support for the claim is the video’s use of satellite imagery of a location in Israel sourced from Google Maps:
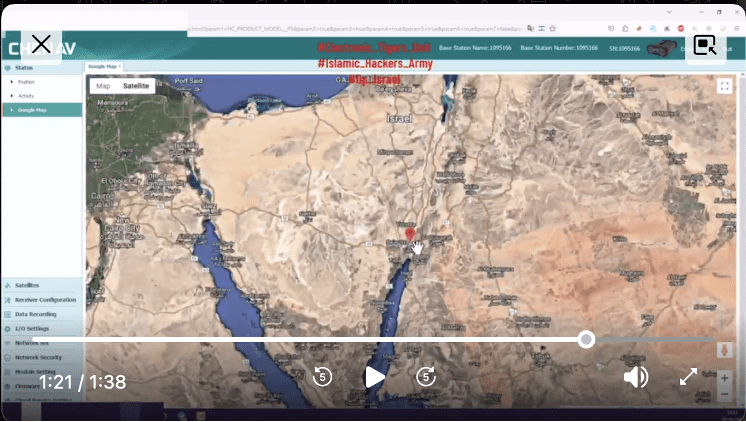
Image 21: Electronic_Tigers_Unit shared images apparently originating from Google Maps to support its claims of access to sensitive Israeli targets.
On the same date, the group also claimed access to Israeli police data but offered little evidence to support the claim.
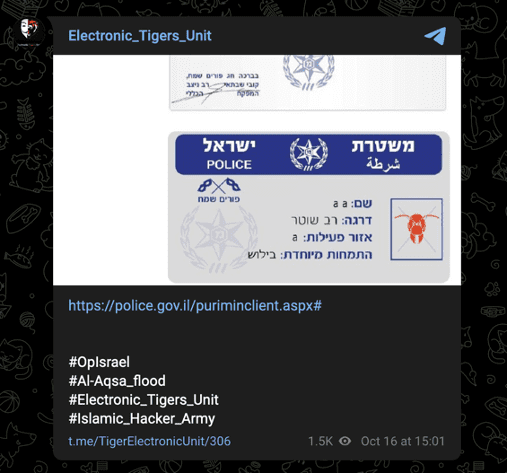
Image 22: Electronic_Tigers_Unit also claimed access to Israeli police data on October 16.
Force Electronic Quds
The most recent claims made on the pro-Palestinian, Arabic-language channel Force Electronic Quds (a literal, if somewhat unnatural, English rendering of its Arabic name, فليق القدس الاكتروني; “the Electronic Quds Force” would be the more likely word order in English) have highlighted the group’s defensive capabilities rather than claimed attacks against Israel, as indicated by two posts made on October 16:
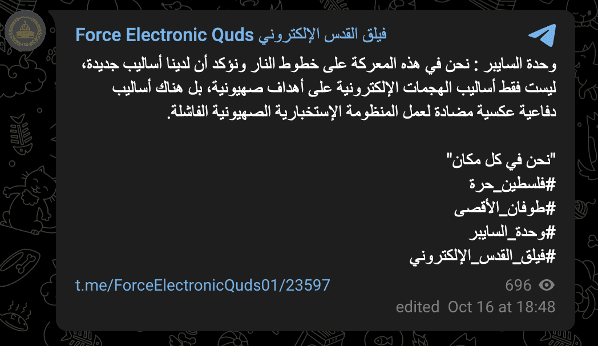
Image 23: In one of its October 16 posts, Force Electronic Quds wrote, “We are in the line of fire in this battle, and we emphasize that we have new methods, not only methods of electronic attacks on Zionist targets but [also] defensive methods that counter the work of the failed Zionist intelligence system.”
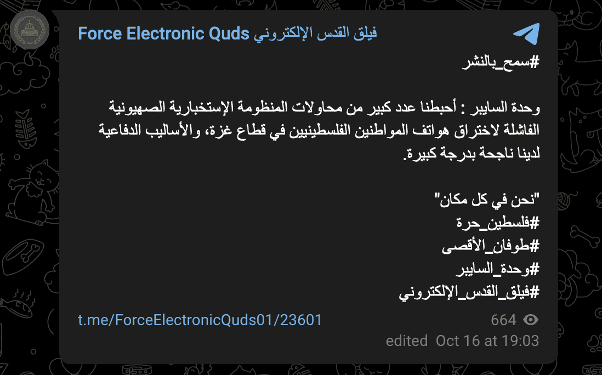
Image 24: in another of its posts on October 16, Force Electronic Quds claimed, “We thwarted a large number of failed attempts by the Zionist intelligence system to hack the phones of Palestinian citizens in the Gaza Strip, as our defensive methods are highly successful.”
Aslan Neferler Tim
The long-standing Turkish hacktivist group Aslan Neferler Tim’s most recently-claimed attack came on October 19, when it purportedly disrupted the operations of an Israeli arms company’s website.
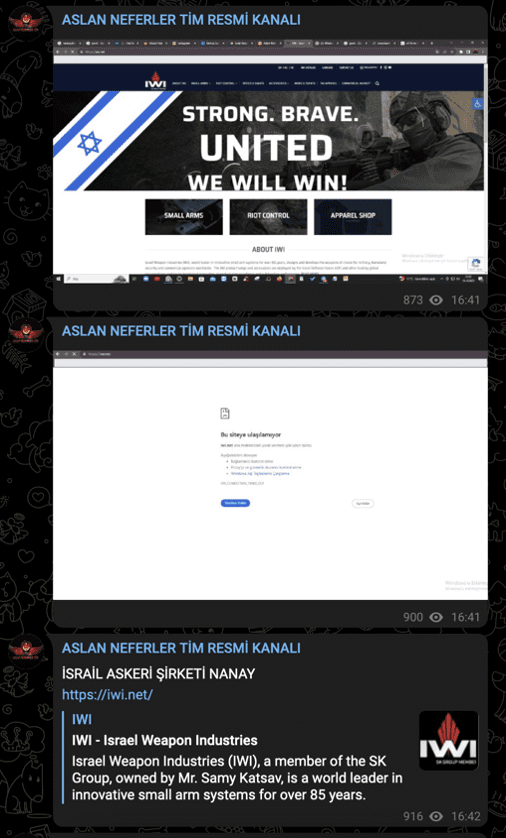
Image 25: Aslan Neferler Tim claimed to have interrupted the service of Israel Weapon Industries (IWI)’s website on October 19.
Prior to the claimed attack against Israel Weapon Industries (IWI), Aslan Neferler Tim similarly claimed to have disrupted the Israeli Air Force’s website on October 15:
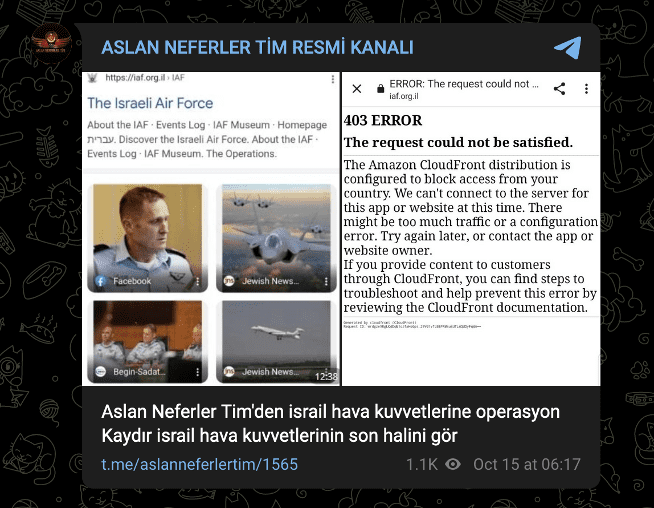
Image 26: Aslan Neferler Tim claimed an attack against the Israeli Air Force on October 15.
Anonymous Sudan
Anonymous Sudan claimed attacks against Israeli alerting app RedAlert’s website on October 20. However, these claims would not necessarily indicate that the attack affected the alerting service itself, given that the alerting application and website likely use different infrastructure. However, especially given previous attacks against the same service earlier in the conflict, these claims, if circulated widely enough, could still have a psychological effect.
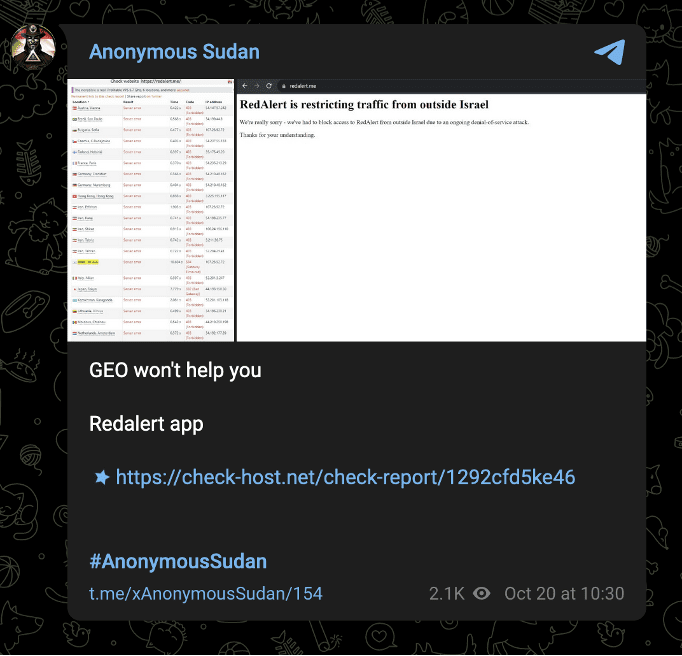
Image 27-28: Anonymous Sudan claimed to have disrupted the operations of RedAlert’s website, despite its geographically-specific traffic restrictions, on October 20.
Notably, however, before October 20, Anonymous Sudan’s most recent claims occurred on October 15, when the group declared it would target Kenyan organizations due to Kenya’s support for Israel—this may speak to the growing international scope of the cyber conflict.
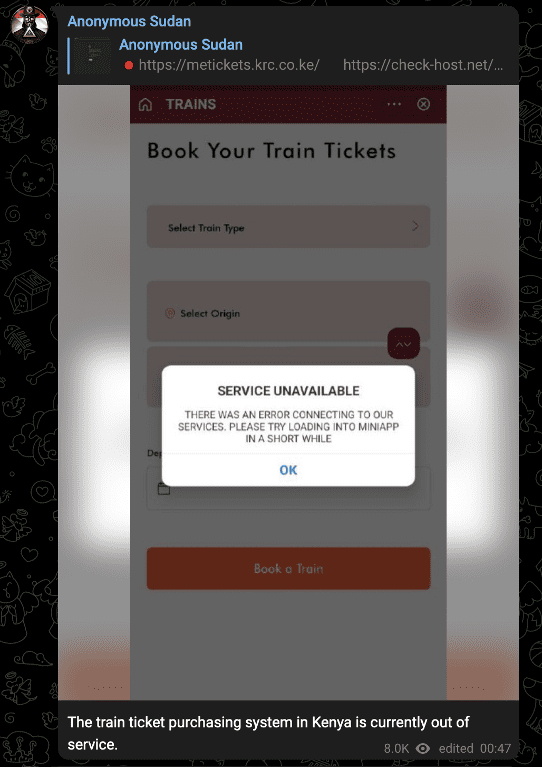
Images 29-30: Anonymous Sudan claimed attacks against the Kenyan rail service on October 15.
Ghosts of Palestine
Ghosts of Palestine’s focus has remained on Israeli targets. The group most recently claimed an attack against govforms.gov[.]il on October 20 and claimed attacks against the Israeli Ministry of Education one day prior.
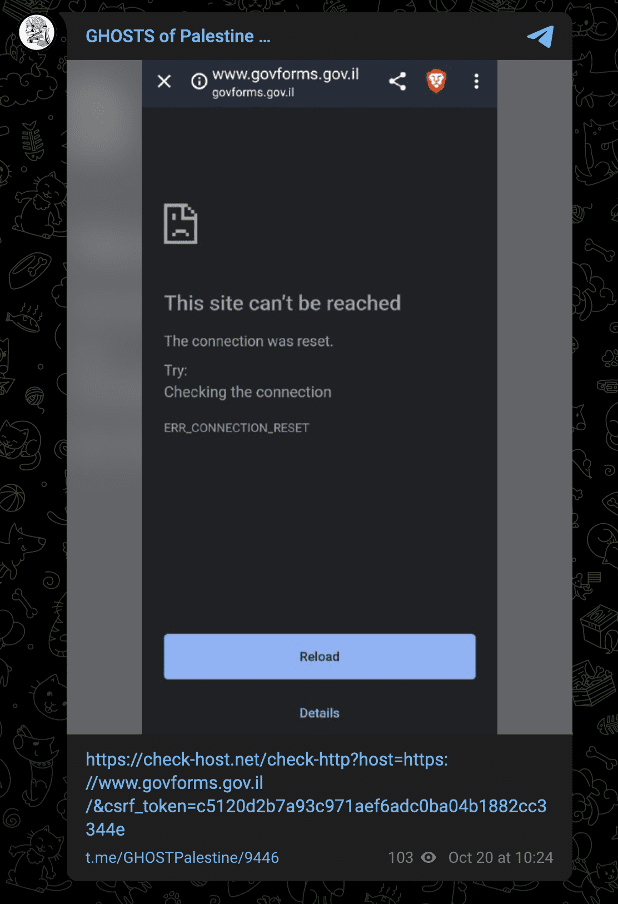
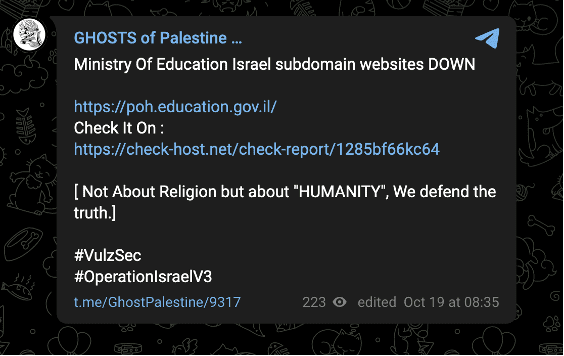
Images 31-32: Ghosts of Palestine claimed attacks against an Israeli government site on October 20 and an attack against the Israeli Ministry of Education on October 19.
Moroccan Black Cyber Army
Similarly, the Moroccan Black Cyber Army’s most recent claims are of a DDoS attack against an Israeli gaming site and a theft of sensitive Israeli documents on October 20.
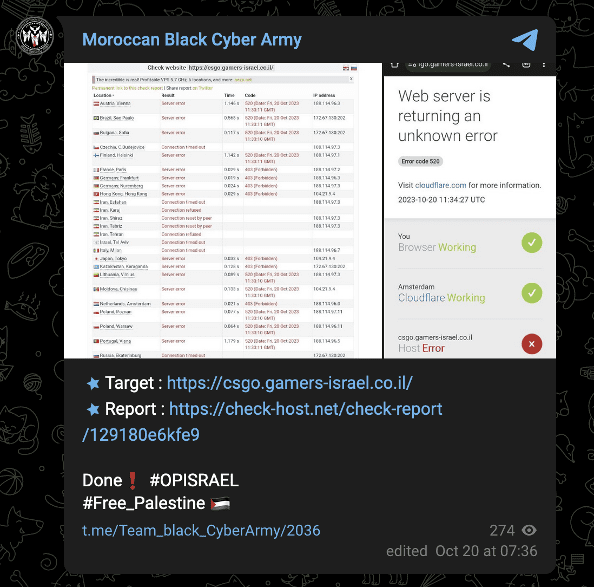
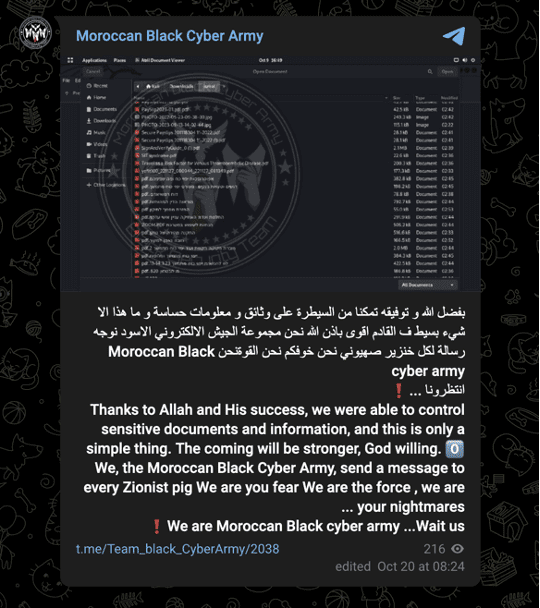
Images 33-34: The Moroccan Black Cyber Army made unsubstantiated claims of attacks against Israeli organizations on October 20.
Cyber Av3ngers
The Iran-linked Cyber Av3ngers hacktivist group claimed an attack on Israeli electric infrastructure on October 17. However, no public reporting supports this claim.
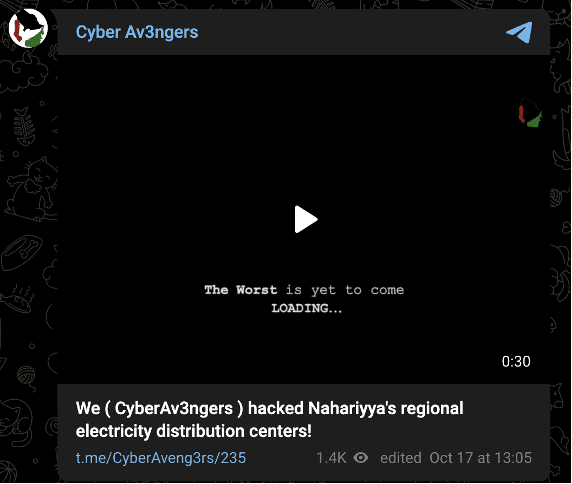
Image 35: Cyber Av3ngers made unsubstantiated claims of a disruption to Israeli energy infrastructure on October 17.
SS Cyber Team
The openly anti-Semitic SS Cyber Team most recently made an unsubstantiated claim to have breached Israeli databases on October 17.
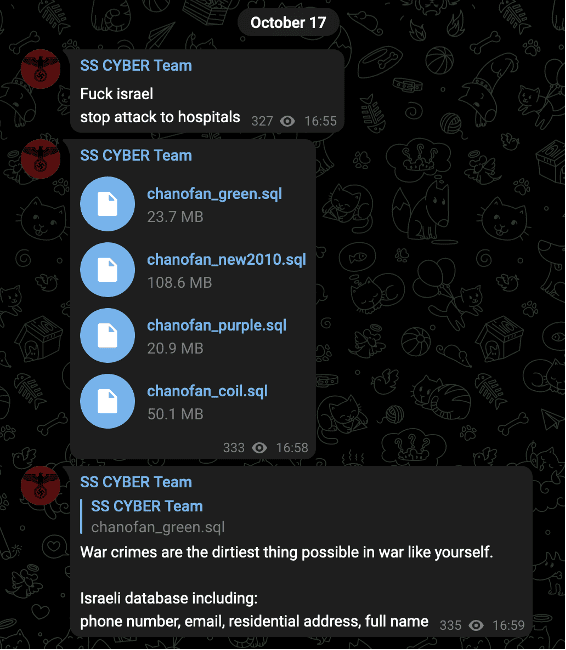
Image 36: SS Cyber Team circulated the contents of purportedly breached Israeli databases on October 17.
Muslim Cyber Army
Like Ghosts of Palestine, the Muslim Cyber Army claimed the October 19 attack against the Israeli Ministry of Education. More recently, the group claimed data thefts on October 19 and 20. The images circulated in support of these claims, however, may either be forged or taken out of context, and could contain data exposed prior to the war.
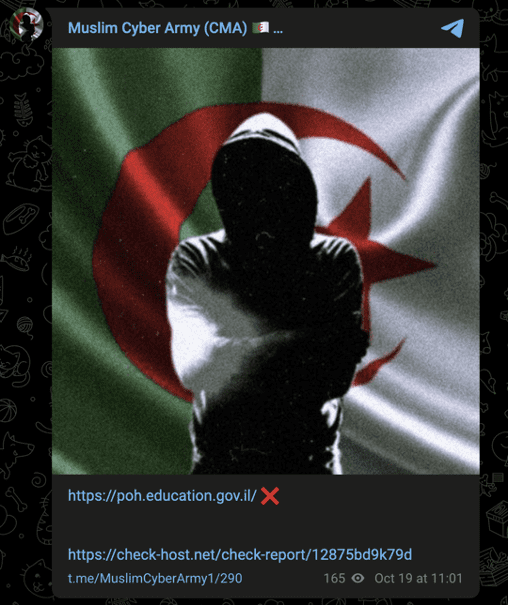
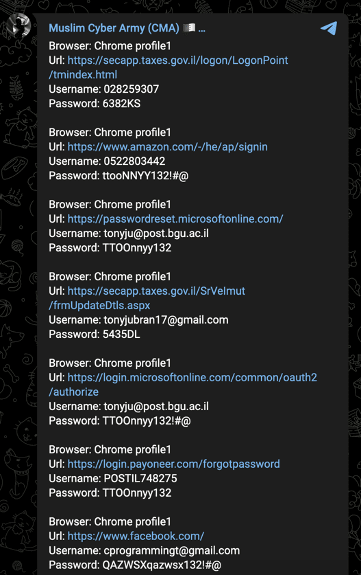
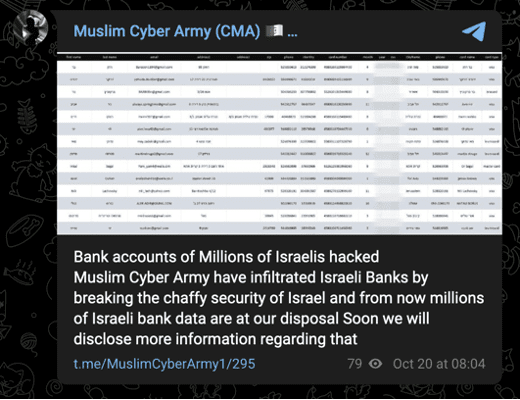
Images 37-39: The Muslim Cyber Army made unsubstantiated claims of attacks and data thefts against Israeli targets on October 19 and 20.


