ESXiArgs Ransomware Campaign Targets VMWare ESXi Vulnerability
-
May 21, 2025Defending The Financial Supply Chain
-
May 19, 2025The Cybersecurity of France’s Top 100 Companies
-
February 24, 2025Massive Botnet Targets M365 with Stealthy Password Spraying Attacks
-
February 13, 2025Lazarus Group is Infecting Open-Source Code. Are You at Risk?
-
February 6, 2025Insurance Carriers Face Unprecedented Supply Chain Cyber Threats
Executive Summary
- On February 3, European hosting providers and computer emergency response teams (CERTs) began warning of a widespread ransomware campaign exploiting CVE-2021-21974, a VMWare ESXi vulnerability for which a patch has been available since February 2021.
-
Shortly after the warnings’ publication, SecurityScorecard developed an emergency informational signal to give customers visibility into potentially impacted servers. SecurityScorecard researchers also created a tool for hunting ESXiArgs using SecurityScorecard datasets, available here: https://lnkd.in/gXvytttW
-
The SecurityScorecard Threat Research, Intelligence, Knowledge, and Engagement (STRIKE) Team began an investigation into this new campaign in response to the advisories about it.
-
Our Attack Surface Intelligence (ASI) tool has revealed a population of servers that may be subject to this vulnerability, and our global network flow (netflow) analysis capability (available via professional services) has uncovered possible communication between target IP addresses and infrastructure involved in the exploitation of this vulnerability.
Background
Beginning on February 3, European hosting providers and computer emergency response teams (CERTs) began warning of a widespread ransomware campaign exploiting CVE-2021-21974, a VMWare ESXi vulnerability for which a patch has been available since February 2021. In their initial warning regarding the vulnerability, French cloud service provider OVH linked this activity to the Nevada ransomware group, but subsequently retracted this attribution. The cybersecurity community has instead taken to tracking the campaign as ESXiArgs, as the ransomware involved creates a file with a .args extension once it encrypts a file.
Especially in light of OVH’s retraction, it may bear noting that ESXiArgs is not the only ransomware campaign to target ESXi; Croatia’s CERT published a flowchart that specifically helps distinguish ESXiArgs activity from that of the aforementioned Nevada ransomware group, indicating that the Nevada group does indeed target ESXi services as well, but that this activity is distinct from ESXiArgs. Similarly, research circulated on February 5 noted that the Royal ransomware group had also begun targeting ESXi, and recent years also have also seen the Black Basta, LockBit, BlackMatter, AvosLocker, REvil, HelloKitty, RansomEXX, and Hive ransomware groups targeting it.
SecurityScorecard’s Attack Surface Intelligence (ASI) tool reveals that ESXi is, in general, fairly widespread, detecting some version of it in use at 139,491 IP addresses worldwide.
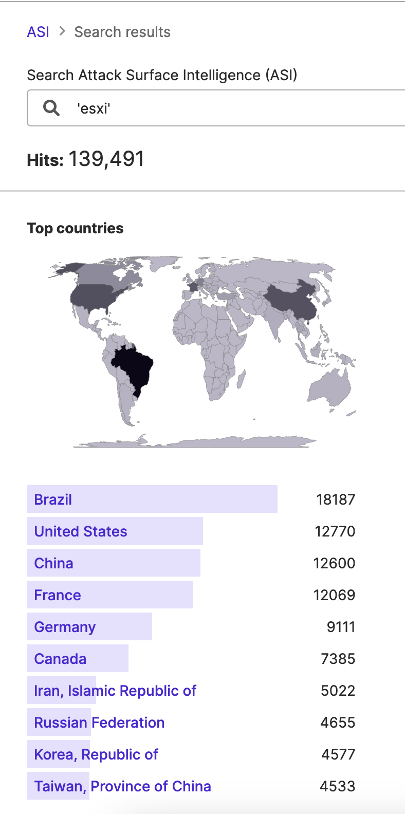
Additionally, Attack Surface Intelligence (ASI) has identified ninety-two IP addresses attributed to previous ransomware victims where ESXi is also in use; this may reflect other ransomware groups’ targeting of these services prior to the announcement of the ESXiArgs campaign.
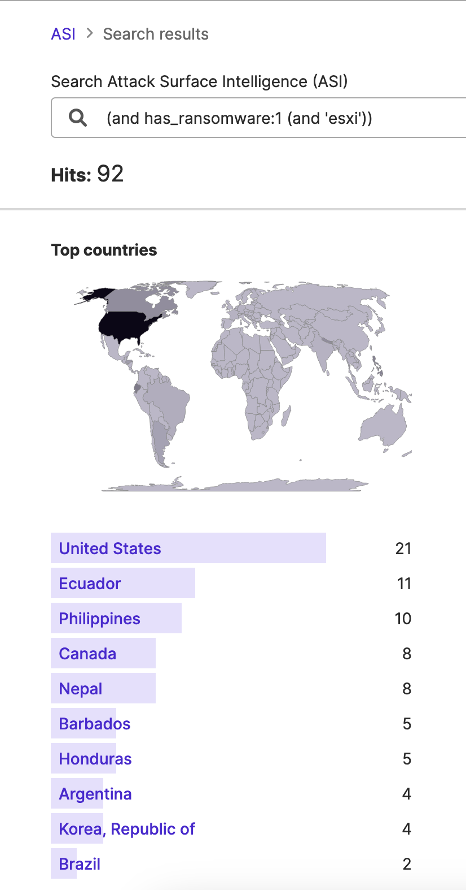
Findings: Possibly Affected Services
While other ransomware groups have previously exploited other ESXi vulnerabilities in the past, Attack Surface Intelligence (ASI) has revealed the three versions of ESXi that this specific vulnerability may affect: V (versions 6.5, 6.7, and 7.0) are in use at seven, eight, and fifty-eight IP addresses respectively.
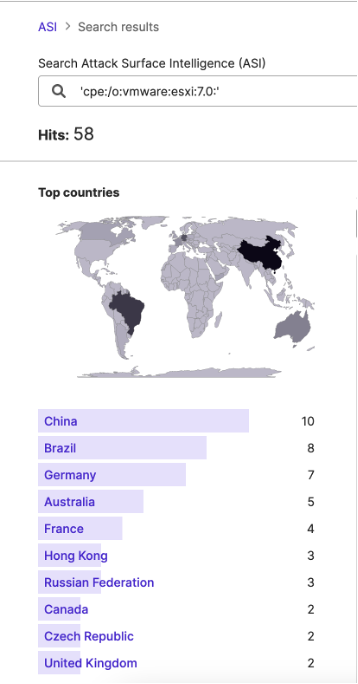
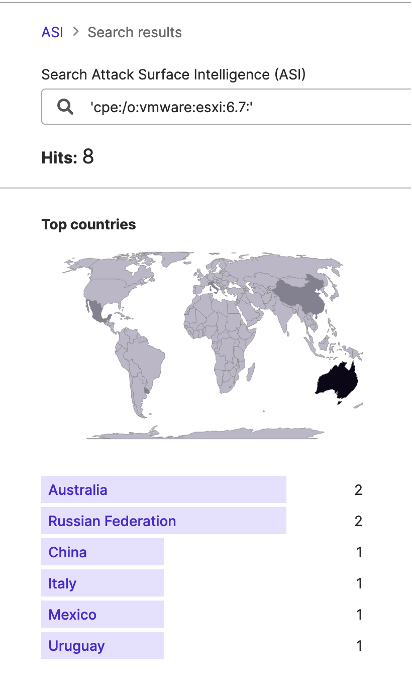
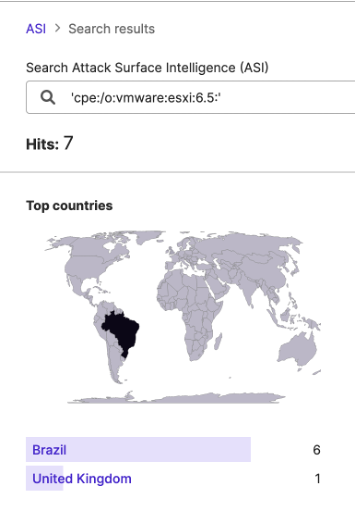
The STRIKE Team then used these Attack Surface Intelligence (ASI) results to identify IP addresses from which to collect a sample of traffic that may reflect ESXiArgs activity; given European CERTs’ particular concern with ESXiArgs, researchers selected the French, Italian, and British IP addresses where versions 7.0, 6.7, and 6.5 are in use, respectively, in hopes of identifying potential attempts by ransomware groups to target these services.
Findings: Netflow Analysis
STRIKE Team researchers leveraged SecurityScorecard’s exclusive access to global netflow data to analyze a month (January 3-February 3) of traffic involving the potentially affected IP addresses identified by Attack Surface Intelligence (ASI) (the four French IP addresses where ESXi 7.0 is in use, the Italian IP address where ESXi 6.7 is in use, and the British IP address where ESXi 6.5 is in use). They compared these three samples both to one another and to the samples from previous ransomware investigations. The latter comparison enabled researchers to identify possibly ransomware-linked IP addresses that communicated with these potential targets, while the former enabled researchers to narrow their focus further to those that may specifically have targeted vulnerable ESXi systems, as ESXi is a common trait of the target IP addresses.
The IP address that appears most likely to reflect an attempt by a ransomware group to exploit this vulnerability is 161.47.17[.]28.; Iit not only appeared in all three of the ESXi traffic samples collected in response to the recent advisories, but also appeared in multiple previous STRIKE Team ransomware investigations.
Three IP addresses (, 143.198.7[.]33, 159.89.246[.]130, and 159.89.188[.]11), appeared in both the French and British IP addresses’ traffic samples while also appearing in previous ransomware victims’ traffic samples, two , (41.94.22[.]2 and 131.108.156[.]113), appeared in both the Italian and French IP addresses’ traffic samples as well as previous ransomware victims’ traffic samples, and another two (, 134.213.193[.]62 and 103.235.46[.]191), appeared in both the Italian and British IP addresses’ traffic samples as well as previous ransomware victims’ traffic samples. These overlaps suggest that, of the IP addresses to appear in the possible targets’ traffic samples, these may be especially likely to have been involved in the ESXiArgs campaign. That said, though, without internal visibility into the target networks, STRIKE researchers cannot determine the specific activity this traffic represents with certainty.
In addition to the above, researchers identified 402 other IP addresses that the cybersecurity vendors who contribute to VirusTotal have linked to malicious activity, forty-six other IP addresses that appeared in previous ransomware investigations (but which VirusTotal does not detect), and five IP addresses that communicated with multiple potential target IP addresses but did not appear in previous ransomware investigations. While less likely to specifically be involved with the ESXiArgs campaign, these IP addresses may nonetheless be suspicious. T; they are available in appendices below.
Recommendations
- Apply the relevant update to any still-unpatched servers as soon as possible. If, for some reason, you cannot apply the patch, deactivate OpenSLP services (or limit access to them to a list of trusted IP addresses).
- Take the standard precautions against ransomware:
- Maintain up-to-date backups of data threat actors may target for encryption;
- Only expose services to the wider internet when necessary; and
- Consistently monitor network traffic for any unexpected behavior.
Attack Surface Intelligence and Managed Threat Hunting with Cyber Risk Intelligence
In addition to the visibility offered by the new signal in our ratings platform, SecurityScorecard’s other tools and services can support organizations’ efforts to respond to and defend against these vulnerabilities and their exploitation. SecurityScorecard’s new Attack Surface Intelligence (ASI) solution gives you direct access to SecurityScorecard’s deep threat intelligence data through a global tab on the ratings platform and via API, all of which can contribute to improved visibility into internal and external resources, supporting the infrastructure management advised above.
Attack Surface Intelligence (ASI) analyzes billions of sources to provide deep threat intelligence and visibility into any IP, network, domain, or vendor’s attack surface risk, from a single pane of glass. This helps a variety of customers do more with the petabytes of data that form the basis of SecurityScorecard Ratings, including identifying all of an organization’s connected assets, exposing unknown threats, conducting investigations at scale, and prioritizing vendor remediation with actionable intelligence.
Attack Surface Intelligence (ASI) is built into SecurityScorecard’s ratings platform through an enhanced Portfolio view or Global search across all Internet assets, leaked credentials, and infections and metadata from the largest malware sinkhole in the world. Access Attack Surface Intelligence (ASI) today on the SecurityScorecard platform with 20 free search queries per month or request a demo on our website.
SecurityScorecard’s threat research and intelligence services could be the competitive advantage organizations need to stay ahead of fast-moving threat actors like those exploiting these new vulnerabilities. For more custom insights from our team with 100+ years of combined threat research and investigation experience, or more details on these findings, please contact us to discuss our Cyber Risk Intelligence as a Service (CRIaaS) offering. The above investigation can offer a trustworthy but preliminary view of our capabilities. Our team can continue diving into these details, especially with the ability to provide further support by working with on-site staff.
If you believe your organization to be under immediate threat from actors linked to ESXiArgs and other threats like it, SecurityScorecard also provides managed incident response and digital forensics teams as a professional service driven by a large group of former law enforcement and private sector experts with decades of experience in the space. For immediate support from our teams, please contact us.
Appendix: VirusTotal-Detected IP Addresses Communicating with Possible Targets
- 167[.]99[.]184[.]51
- 167[.]71[.]16[.]153
- 41[.]94[.]22[.]2
- 45[.]232[.]73[.]46
- 43[.]129[.]33[.]99
- 104[.]248[.]246[.]104
- 193[.]57[.]40[.]49
- 45[.]232[.]73[.]56
- 143[.]198[.]28[.]117
- 147[.]182[.]182[.]55
- 45[.]232[.]73[.]51
- 146[.]190[.]85[.]130
- 162[.]243[.]189[.]2
- 188[.]166[.]160[.]164
- 46[.]101[.]128[.]25
- 137[.]184[.]149[.]253
- 183[.]82[.]13[.]80
- 137[.]184[.]58[.]169
- 89[.]248[.]165[.]166
- 177[.]39[.]196[.]112
- 167[.]172[.]40[.]239
- 27[.]0[.]183[.]209
- 138[.]197[.]32[.]222
- 217[.]147[.]224[.]94
- 102[.]220[.]13[.]85
- 5[.]188[.]87[.]3
- 138[.]68[.]76[.]27
- 201[.]150[.]126[.]212
- 164[.]92[.]176[.]210
- 134[.]209[.]124[.]226
- 131[.]108[.]156[.]1
- 89[.]203[.]249[.]28
- 97[.]74[.]81[.]123
- 64[.]225[.]50[.]135
- 192[.]206[.]6[.]96
- 161[.]35[.]140[.]163
- 167[.]172[.]43[.]20
- 89[.]203[.]150[.]42
- 131[.]108[.]156[.]113
- 131[.]221[.]37[.]179
- 139[.]59[.]47[.]1
- 177[.]85[.]4[.]41
- 132[.]255[.]53[.]97
- 82[.]196[.]7[.]246
- 134[.]122[.]88[.]171
- 157[.]230[.]237[.]83
- 64[.]227[.]3[.]24
- 138[.]68[.]91[.]192
- 157[.]230[.]15[.]216
- 45[.]232[.]73[.]185
- 159[.]223[.]184[.]185
- 104[.]131[.]190[.]193
- 188[.]166[.]58[.]179
- 162[.]243[.]48[.]133
- 159[.]223[.]148[.]18
- 46[.]101[.]175[.]103
- 157[.]230[.]83[.]80
- 157[.]230[.]218[.]88
- 206[.]81[.]24[.]160
- 159[.]203[.]179[.]230
- 142[.]93[.]14[.]124
- 143[.]110[.]183[.]17
- 209[.]97[.]160[.]227
- 178[.]128[.]55[.]198
- 188[.]166[.]146[.]208
- 159[.]203[.]85[.]196
- 159[.]65[.]11[.]5
- 142[.]93[.]116[.]249
- 206[.]81[.]4[.]81
- 128[.]199[.]77[.]201
- 106[.]51[.]3[.]214
- 138[.]197[.]32[.]150
- 68[.]183[.]27[.]133
- 104[.]236[.]7[.]248
- 165[.]227[.]83[.]174
- 159[.]65[.]129[.]227
- 41[.]63[.]1[.]226
- 84[.]88[.]59[.]1
- 165[.]22[.]59[.]229
- 128[.]199[.]154[.]5
- 14[.]97[.]218[.]174
- 147[.]182[.]188[.]81
- 159[.]65[.]154[.]92
- 161[.]35[.]125[.]167
- 167[.]71[.]166[.]90
- 207[.]154[.]215[.]181
- 134[.]122[.]8[.]241
- 137[.]184[.]215[.]213
- 139[.]59[.]105[.]82
- 170[.]210[.]46[.]4
- 41[.]93[.]31[.]73
- 165[.]22[.]16[.]134
- 46[.]101[.]224[.]184
- 85[.]152[.]57[.]60
- 154[.]68[.]232[.]20
- 138[.]197[.]80[.]24
- 104[.]236[.]111[.]25
- 137[.]184[.]135[.]135
- 142[.]93[.]178[.]56
- 159[.]223[.]95[.]166
- 154[.]68[.]225[.]162
- 164[.]90[.]231[.]253
- 138[.]197[.]19[.]166
- 162[.]243[.]237[.]90
- 138[.]197[.]175[.]169
- 134[.]122[.]20[.]244
- 147[.]182[.]145[.]89
- 103[.]246[.]240[.]28
- 167[.]71[.]33[.]249
- 157[.]230[.]34[.]158
- 61[.]2[.]224[.]84
- 164[.]92[.]142[.]65
- 134[.]209[.]162[.]114
- 45[.]55[.]180[.]7
- 178[.]128[.]229[.]120
- 167[.]71[.]170[.]172
- 142[.]93[.]201[.]51
- 142[.]93[.]50[.]8
- 134[.]122[.]74[.]24
- 104[.]131[.]68[.]23
- 68[.]183[.]104[.]78
- 103[.]246[.]240[.]30
- 188[.]166[.]247[.]82
- 178[.]62[.]105[.]122
- 170[.]210[.]203[.]211
- 206[.]189[.]185[.]21
- 104[.]248[.]146[.]84
- 68[.]183[.]170[.]149
- 174[.]138[.]64[.]63
- 159[.]89[.]141[.]221
- 170[.]210[.]83[.]90
- 178[.]128[.]214[.]153
- 159[.]65[.]223[.]90
- 143[.]244[.]172[.]59
- 104[.]248[.]252[.]80
- 138[.]197[.]180[.]102
- 95[.]85[.]34[.]53
- 206[.]189[.]80[.]198
- 161[.]35[.]0[.]70
- 157[.]245[.]218[.]29
- 174[.]138[.]16[.]16
- 159[.]65[.]63[.]94
- 178[.]62[.]17[.]94
- 137[.]184[.]104[.]77
- 104[.]131[.]181[.]4
- 104[.]236[.]78[.]19
- 165[.]227[.]106[.]20
- 161[.]35[.]210[.]148
- 207[.]154[.]241[.]112
- 165[.]22[.]66[.]147
- 159[.]65[.]218[.]99
- 139[.]59[.]27[.]92
- 64[.]227[.]120[.]10
- 170[.]210[.]45[.]123
- 104[.]248[.]20[.]85
- 134[.]209[.]69[.]41
- 137[.]184[.]154[.]154
- 103[.]16[.]202[.]187
- 147[.]182[.]128[.]252
- 159[.]65[.]235[.]114
- 157[.]245[.]195[.]132
- 139[.]59[.]76[.]127
- 167[.]99[.]84[.]28
- 177[.]91[.]79[.]21
- 137[.]184[.]21[.]86
- 157[.]245[.]193[.]85
- 157[.]245[.]207[.]215
- 128[.]199[.]204[.]124
- 128[.]199[.]171[.]119
- 206[.]81[.]9[.]31
- 46[.]101[.]249[.]11
- 115[.]113[.]11[.]143
- 159[.]223[.]80[.]140
- 159[.]65[.]163[.]42
- 161[.]35[.]124[.]45
- 165[.]22[.]181[.]245
- 165[.]227[.]114[.]124
- 167[.]172[.]190[.]215
- 102[.]215[.]196[.]206
- 128[.]199[.]45[.]37
- 134[.]209[.]244[.]230
- 182[.]156[.]1[.]58
- 157[.]230[.]111[.]25
- 187[.]243[.]248[.]114
- 167[.]99[.]15[.]190
- 134[.]209[.]211[.]170
- 143[.]110[.]185[.]99
- 178[.]128[.]29[.]118
- 64[.]227[.]35[.]112
- 206[.]189[.]226[.]38
- 103[.]129[.]108[.]14
- 134[.]122[.]30[.]150
- 147[.]182[.]185[.]145
- 178[.]128[.]248[.]121
- 104[.]131[.]3[.]1
- 165[.]22[.]184[.]212
- 104[.]131[.]249[.]57
- 142[.]93[.]187[.]197
- 165[.]227[.]148[.]167
- 104[.]131[.]39[.]193
- 128[.]199[.]64[.]114
- 128[.]199[.]192[.]230
- 46[.]101[.]49[.]191
- 161[.]35[.]4[.]85
- 138[.]68[.]8[.]161
- 157[.]230[.]229[.]202
- 68[.]183[.]20[.]198
- 167[.]99[.]67[.]143
- 146[.]190[.]27[.]250
- 37[.]186[.]127[.]96
- 161[.]35[.]177[.]39
- 165[.]227[.]193[.]157
- 188[.]166[.]5[.]84
- 134[.]209[.]106[.]24
- 128[.]199[.]194[.]1
- 157[.]245[.]156[.]72
- 41[.]63[.]10[.]8
- 167[.]71[.]196[.]217
- 41[.]93[.]33[.]2
- 104[.]248[.]51[.]246
- 165[.]22[.]55[.]238
- 164[.]92[.]152[.]140
- 104[.]248[.]253[.]245
- 161[.]35[.]152[.]153
- 134[.]122[.]63[.]199
- 45[.]114[.]195[.]2
- 192[.]241[.]169[.]184
- 157[.]245[.]143[.]248
- 147[.]182[.]169[.]252
- 143[.]244[.]161[.]152
- 143[.]110[.]255[.]245
- 164[.]90[.]172[.]83
- 165[.]22[.]221[.]230
- 139[.]59[.]121[.]188
- 159[.]223[.]38[.]199
- 159[.]203[.]81[.]114
- 184[.]168[.]122[.]62
- 162[.]243[.]80[.]57
- 159[.]223[.]97[.]88
- 138[.]197[.]162[.]56
- 104[.]131[.]185[.]48
- 167[.]99[.]239[.]101
- 147[.]182[.]218[.]64
- 134[.]122[.]72[.]235
- 128[.]199[.]253[.]34
- 47[.]241[.]223[.]102
- 61[.]2[.]241[.]214
- 107[.]170[.]39[.]69
- 165[.]227[.]133[.]23
- 167[.]172[.]132[.]44
- 64[.]227[.]28[.]246
- 165[.]227[.]196[.]30
- 68[.]183[.]105[.]114
- 188[.]166[.]14[.]99
- 143[.]198[.]116[.]232
- 167[.]71[.]28[.]141
- 62[.]149[.]128[.]154
- 178[.]62[.]36[.]171
- 128[.]199[.]146[.]3
- 202[.]160[.]145[.]243
- 45[.]191[.]91[.]45
- 46[.]101[.]187[.]42
- 188[.]166[.]39[.]184
- 167[.]172[.]141[.]86
- 150[.]165[.]37[.]44
- 128[.]199[.]84[.]25
- 139[.]59[.]120[.]201
- 146[.]164[.]51[.]48
- 165[.]22[.]246[.]63
- 165[.]22[.]234[.]248
- 200[.]137[.]65[.]37
- 68[.]183[.]31[.]114
- 200[.]137[.]5[.]196
- 202[.]83[.]16[.]8
- 147[.]182[.]190[.]189
- 187[.]86[.]135[.]246
- 165[.]227[.]202[.]89
- 157[.]230[.]127[.]240
- 207[.]154[.]226[.]163
- 159[.]223[.]92[.]245
- 157[.]245[.]212[.]8
- 138[.]197[.]103[.]160
- 142[.]93[.]77[.]1
- 167[.]99[.]152[.]121
- 159[.]65[.]188[.]65
- 47[.]254[.]21[.]33
- 157[.]230[.]208[.]92
- 104[.]236[.]228[.]230
- 45[.]55[.]134[.]210
- 62[.]149[.]128[.]163
- 104[.]248[.]127[.]185
- 128[.]199[.]32[.]98
- 134[.]122[.]114[.]136
- 167[.]99[.]218[.]101
- 157[.]230[.]84[.]180
- 188[.]166[.]95[.]44
- 104[.]236[.]94[.]202
- 111[.]93[.]191[.]170
- 68[.]183[.]132[.]99
- 183[.]82[.]96[.]133
- 159[.]65[.]242[.]16
- 46[.]101[.]2[.]4
- 165[.]22[.]186[.]178
- 167[.]172[.]187[.]120
- 161[.]35[.]71[.]152
- 104[.]248[.]242[.]125
- 167[.]71[.]16[.]158
- 67[.]205[.]167[.]168
- 128[.]199[.]97[.]155
- 178[.]128[.]209[.]69
- 128[.]199[.]142[.]208
- 45[.]232[.]73[.]83
- 165[.]90[.]14[.]164
- 128[.]199[.]247[.]226
- 64[.]227[.]67[.]194
- 189[.]177[.]201[.]48
- 68[.]183[.]127[.]157
- 143[.]198[.]191[.]25
- 159[.]223[.]120[.]180
- 64[.]227[.]25[.]222
- 128[.]199[.]148[.]70
- 162[.]243[.]172[.]239
- 142[.]93[.]245[.]58
- 167[.]172[.]243[.]183
- 64[.]225[.]19[.]94
- 167[.]71[.]169[.]21
- 159[.]203[.]179[.]44
- 138[.]68[.]102[.]83
- 164[.]92[.]193[.]67
- 159[.]65[.]6[.]45
- 198[.]199[.]72[.]47
- 67[.]207[.]83[.]228
- 134[.]209[.]175[.]24
- 206[.]189[.]232[.]29
- 142[.]93[.]241[.]93
- 200[.]17[.]114[.]130
- 147[.]139[.]45[.]22
- 139[.]59[.]14[.]115
- 67[.]205[.]171[.]223
- 164[.]92[.]189[.]191
- 52[.]199[.]105[.]183
- 62[.]149[.]128[.]74
- 198[.]148[.]92[.]176
- 104[.]248[.]179[.]42
- 139[.]59[.]187[.]229
- 138[.]197[.]97[.]212
- 67[.]205[.]144[.]9
- 41[.]89[.]196[.]16
- 159[.]65[.]183[.]47
- 207[.]154[.]244[.]8
- 157[.]230[.]23[.]46
- 45[.]55[.]134[.]67
- 64[.]225[.]20[.]153
- 13[.]212[.]228[.]23
- 167[.]172[.]243[.]126
- 157[.]245[.]138[.]97
- 212[.]62[.]96[.]86
- 43[.]153[.]2[.]147
- 167[.]172[.]146[.]169
- 178[.]128[.]87[.]65
- 165[.]227[.]194[.]124
- 157[.]230[.]133[.]15
- 165[.]22[.]190[.]39
- 18[.]142[.]120[.]133
- 134[.]209[.]107[.]178
- 174[.]138[.]23[.]45
- 192[.]241[.]182[.]74
- 167[.]71[.]160[.]75
- 103[.]134[.]44[.]42
- 206[.]81[.]16[.]240
- 138[.]197[.]6[.]174
- 178[.]128[.]195[.]69
- 103[.]83[.]158[.]66
- 159[.]223[.]221[.]95
- 143[.]110[.]217[.]201
- 137[.]184[.]111[.]153
- 62[.]149[.]128[.]157
- 143[.]198[.]182[.]160
- 62[.]149[.]128[.]160
- 178[.]128[.]167[.]226
- 113[.]190[.]245[.]2
- 103[.]235[.]46[.]191
- 103[.]82[.]242[.]27
- 147[.]182[.]173[.]182
- 52[.]221[.]209[.]153
- 134[.]209[.]218[.]186
- 64[.]227[.]77[.]252
- 164[.]92[.]179[.]157
- 203[.]115[.]99[.]220
- 143[.]198[.]33[.]14
- 198[.]199[.]86[.]89
- 134[.]209[.]119[.]196
- 159[.]203[.]92[.]179
- 134[.]209[.]212[.]251
- 45[.]55[.]42[.]227
- 138[.]185[.]172[.]129
- 103[.]210[.]44[.]190
- 69[.]164[.]45[.]0
- 168[.]167[.]69[.]86
- 159[.]65[.]255[.]251
- 193[.]0[.]14[.]129
- 64[.]225[.]16[.]177
Appendix: IP Addresses From Previous Ransomware Investigations
- 107[.]167[.]20[.]230
- 192[.]33[.]214[.]47
- 130[.]59[.]35[.]198
- 167[.]71[.]87[.]161
- 104[.]131[.]15[.]126
- 164[.]90[.]143[.]171
- 143[.]198[.]7[.]93
- 64[.]225[.]9[.]37
- 157[.]230[.]89[.]254
- 134[.]209[.]219[.]19
- 138[.]197[.]0[.]92
- 146[.]20[.]132[.]153
- 146[.]20[.]132[.]141
- 103[.]155[.]16[.]129
- 157[.]230[.]93[.]231
- 177[.]66[.]152[.]137
- 184[.]106[.]10[.]72
- 184[.]106[.]10[.]77
- 192[.]241[.]189[.]146
- 195[.]176[.]26[.]206
- 159[.]203[.]145[.]121
- 167[.]172[.]26[.]233
- 23[.]253[.]188[.]26
- 146[.]190[.]223[.]190
- 192[.]241[.]157[.]60
- 185[.]14[.]184[.]154
- 64[.]225[.]1[.]58
- 143[.]244[.]220[.]80
- 64[.]185[.]181[.]238
- 165[.]22[.]12[.]234
- 130[.]60[.]204[.]10
- 162[.]242[.]174[.]138
- 162[.]13[.]32[.]69
- 146[.]20[.]128[.]191
- 162[.]13[.]202[.]201
- 146[.]20[.]128[.]116
- 138[.]197[.]155[.]84
- 138[.]197[.]63[.]78
- 192[.]241[.]243[.]218
- 64[.]15[.]159[.]210
- 68[.]183[.]118[.]126
- 159[.]223[.]180[.]245
- 137[.]184[.]213[.]124
- 186[.]237[.]182[.]226
- 177[.]66[.]152[.]139
- 85[.]13[.]90[.]185
Appendix: IP Addresses Communicating With Multiple Potential Target IP Addresses
- 104[.]236[.]65[.]181
- 68[.]183[.]136[.]212
- 159[.]65[.]249[.]246
- 134[.]122[.]88[.]171
- 45[.]172[.]198[.]114




