Cyber Risk Intelligence: County Government Cyber Incident May Have Involved Social Engineering and Targeting of Vulnerable SSH Services
Executive Summary
-
A U.S. county government announced on September 11 that a recent cyber incident strongly resembling a ransomware attack had disrupted its online services.
- SecurityScorecard researchers identified evidence suggesting two possible (and not mutually exclusive) paths by which the threat actors may have accessed county systems:
-
Two files linked to the Cryxos trojan may have enabled social engineering attacks against county employees.
-
Our network flow (netflow) and Attack Surface Intelligence (ASI) data revealed communication between vulnerable county IP addresses and IP addresses linked to malicious activity targeting vulnerable services.
-
-
The suspicious traffic may indicate activity similar to that identified in a previous ransomware investigation, suggesting a possible overlap in the tactics, techniques, and procedures (TTPs) of the threat actors responsible for these two incidents.
Background
The government of a U.S. county announced on September 11 that a recent cyber incident had disrupted its online services. Subsequent coverage of the event has noted that it strongly resembles a ransomware attack. The disruption comes against a backdrop of frequent ransomware activity targeting state and local governments and the education sector. While some observers warned of increasing ransomware attacks against local governments since before the pandemic, incidents increased over the last three years and warnings persist.
On Mar 30, 2022, the Federal Bureau of Investigation (FBI) issued a private industry notification (PIN) warning of continued targeting of local governments by ransomware operations, noting that local Government Facilities Sector (GFS) entities were the second-most frequent victims to report ransomware incidents to the FBI in 2021. The notification highlights four recent incidents that affected county governments and identifies phishing, remote desktop protocol (RDP) compromise, and exploitation of vulnerable software as the three most common means by which threat actors initially accessed victims’ systems. Last month the Cybersecurity and Infrastructure Security Agency (CISA) issued an alert regarding the disproportionate targeting of the education sector by one particular ransomware group, Vice Society. SecurityScorecard’s findings about recent ransomware incidents affecting local governments and educational institutions have led researchers to hypothesize that in recent incidents, attackers may have employed two newer variations on the by-now familiar TTPs discussed in the 2022 CISA and FBI alerts. In one incident, social engineering may have taken the form of tech support fraud or voice phishing (“vishing”) rather than the more familiar email-based phishing. In another, attackers may have compromised exposed SSH services before encrypting victim systems. Upon learning of the incident, SecurityScorecard researchers consulted both in-house and strategic partnership data sources to investigate it further. In investigating this newer incident, SecurityScorecard researchers encountered evidence that attackers may have employed both of these approaches.
Possible Initial Compromise: Cryxos Trojan
While consulting external threat intelligence data sources, SecurityScorecard encountered two malicious files from Spring and Summer 2022 that may have facilitated social engineering attacks against the county government. Other vendors have linked both to the Cryxos trojan.
Cryxos refers to a family of malicious JavaScript files that display fraudulent alerts to users when they visit the webpages hosting those files. These files typically enable tech support scams: they warn the user that their computer has been infected by a virus and direct them to call a threat actor-controlled telephone number. Usually, the attackers will take the call as an opportunity to collect payment information from the victim. However, in some cases, attackers will use the call to direct the victim to install software that gives the attackers remote access to their computer; this could entail the abuse of legitimate remote access software like TeamViewer or the distribution of any number of remote access trojans (RATs).
The first file that appears to imitate a county government webpage in order to serve malicious content appeared on VirusTotal on May 14 and contains a county government URL. The file, identified by the SHA-256 hash b5a9d168349bc37148e2b73d6be55f0afde5c7a7318b9104347be390a8ff0e12and a title including the phrase “county Fire Codes,” also contains an HREF resembles that page title. Ten of the twenty-two vendor detections linking it to malicious activity mention Cryxos, detecting it as JS:Trojan.Cryxos.6645,
JS:Trojan.Cryxos.D19F5, and JS.Trojan.Cryxos.43357, among others.
Other links in the file suggest that attackers intended the site hosting that file, hxxps[:]//disneygreenway970.weebly[.]com, to attract traffic from visitors with a variety of interests and therefore may have cast a wide net when targeting potential victims. In addition to county fire codes, the above file’s HREFs include /resident-evil-2-highly-compressed-pc-game-free-download.html, hxxps[:]//disneygreenway970.weebly[.]com/blog/best-new-vegas-quests, and hxxps[:]//disneygreenway970.weebly[.]com/blog/wrath-of-the-mummy-code. It is possible, then, that attackers hoped that search engines would lead users interested in Resident Evil 2, Fallout: New Vegas, and Wrath of the Mummy to the above pages after users searched for those titles and that some users would then follow the instructions in the warning displayed to them when they reached those pages.
A more recent Cryxos-linked HTML file identified by the SHA-256 hash 8cdf08db9b7b2a0ae5f8935b22d77ce43303eea97ea330a6fc81046cfb79b9c7 appeared on July 11. One vendor detects that file as Trojan.WIN32.cryxos.5913 and it contains another county government URL. That file’s title, which mentions a local church, suggests that it is not impersonating the county government, but that attackers may have instead compromised the website of a church that links to a county emergency services page to inform community members about local services. (It also links to a different emergency services page belonging to a specific town within the county). It is, however, possible that some visitors to the page may find it by searching for county emergency services.
It may also bear noting that SecurityScorecard’s investigation into another ransomware attack against a school district uncovered evidence suggesting that attackers also employed Cryxos in their initial targeting. Against this background, it appears possible that in the case of this county government, attackers were able to obtain remote access to county systems when a county employee fell victim to social engineering. They may, for example, have called the number displayed in a warning that appeared when they visited a webpage purporting to offer information about local fire codes or emergency services and installed remote-access software when directed to by attackers masquerading as support personnel.
SecurityScorecard Platform Findings
Among the other issues affecting the county, SecurityScorecard’s ratings platform detected an open Telnet port at one of its IP addresses. The availability of these ports allows attackers to engage in authentication bypass attacks (such as brute-forcing attempts, remote buffer overflows, and blank passwords). An attacker can leverage this access to pivot access into further enterprise resources. Researchers pivoted off of this finding when analyzing the available netflow data.
Netflow Data
Using SecurityScorecard’s access to exclusive network flow (i.e. netflow) data, researchers identified suspicious traffic that may reflect malicious activity targeting the county in the months leading up to the disruption announced on September 11. This traffic involved IP addresses that SecurityScorecard’s Attack Surface Intelligence (ASI) tool and other vendors have linked to malicious activity communicating with county assets with open ports and vulnerable software and, in some cases, additionally featured anomalously large (one GB or more) data transfers, which may represent data exfiltration. Without internal visibility into the county’s network, SecurityScorecard cannot confirm that these flows indicate malicious activity, but SIEM logs would likely offer the necessary information to make a more thorough assessment.
Netflow Data: Port 23
Based on the above-mentioned platform finding, researchers first searched our netflow data for traffic involving port 23 (the port where Telnet normally runs) of the affected IP address, identifying sixteen flows. Thirteen of these flows transferred relatively small amounts of data, but three may merit closer attention due to having transferred slightly larger amounts of data.
142.93.204[.]250 transferred 352.26 KB to a county IP address on July 12 and may be involved in malicious activity: members of the VirusTotal community have previously included it in a blocklist and observed it conducting SSH brute force attacks, and SecurityScorecard’s Attack Surface Intelligence tool has linked to the Mirai botnet and targeting of Telnet logins.
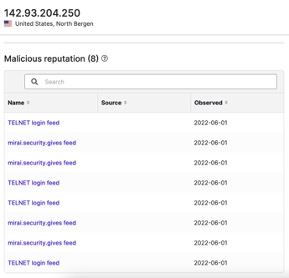
120.57.42[.]39 transferred 129 KB on July 23. No vendors have linked this address to malicious activity.
A county IP address transferred 360.45 KB to 139.59.130[.]20 on July 29. Eight vendors have linked 139.59.130[.]20 to malware or malicious activity, and members of the VirusTotal community have observed it carrying out SSH brute force attacks. SecurityScorecard’s Attack Surface Intelligence (ASI) tool has also revealed that 139.59.130[.]20 suffers from twenty-nine vulnerabilities, which ASI links to active exploitation by eight different threat actor groups. It is possible, then, that actors first exploited these vulnerabilities to compromise 139.59.130[.]20 and subsequently used it in attacks against other organizations.
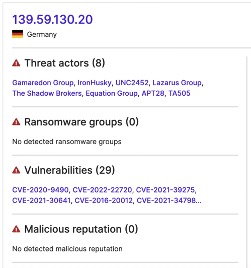
Another county IP address transferred 327.68 KB to 139.59.130[.]20 on August 11. Given 139.59.130[.]20’s possible links to malicious activity, traffic to it from county IP addresses may indicate C2 communications or data exfiltration.
Netflow Data: Large Data Transfers
Between July 12 and September 9, 935 flows transferred large amounts of data (a gigabyte or more) to or from county IP addresses. It does bear noting, though, that some of this traffic could be benign. For example, many of the IP addresses discussed below belong to DigitalOcean. Because DigitalOcean provides various services, many of which are legitimate, it is possible that the transfers discussed below do not represent malicious activity. For example, the many large transfers from DigitalOcean IP addresses to district IP addresses discussed below could indicate data transfers to county systems from backups. However, considering that the county suffered an attack, this traffic (especially traffic involving the IP addresses that other vendors have already deemed malicious) likely merits additional scrutiny.
Of the IP addresses involved in these large transfers, other vendors have linked 30 to malicious or suspicious activity. Discussions of individual IP addresses are available from SecurityScorecard upon request. Broadly speaking, they fall into two categories: IP addresses linked to malware and likely involved in command-and-control (C2) communications, and IP addresses linked to phishing. IP addresses in the first category often appear most frequently because malicious executable (.exe) files, many of which VirusTotal links to the delivery of second-stage payloads, communicate with them. In contrast, vendors have often linked the IP addresses in the second group specifically to phishing. While these latter addresses usually appear in a smaller number of files, the files containing them are almost always emails, which may lend further credence to their involvement in phishing.
Netflow Data: Transfers Involving Vulnerable County IP Addresses
Researchers were additionally able to identify evidence suggesting a broader pattern of targeting vulnerable, open ports by focusing on two county IP addresses that not only figure prominently in the sample of traffic involving large data transfers, but also, upon further inspection, appear to suffer from other issues threat actors may have attempted to exploit prior to the county’s announcement.
SecurityScorecard first noted that a considerable portion (244 of 935) of the flows that transferred one GB or more used port 25, a port normally used for SMTP (an email relay protocol) that malware also frequently uses, of two particular county IP addresses. Researchers then consulted ASI to determine what other issues may face these IP addresses. Its data indicates that other ports open at these addresses may suffer from vulnerabilities under exploitation by at least seven different threat actor groups. It is possible, then, that attackers compromised these servers and used them to target other county assets. The large flows involving them may therefore suggest the distribution of malware, C2 communications, or data exfiltration. When considered in light of the frequent appearance of the above IP addresses in emails submitted to VirusTotal, the appearance of port 25 in these flows may additionally indicate phishing or malware distribution over email.
One address’s hostname suggests that it hosts an SMTP server and ASI also found ports 22, 443, and 161 to be open and revealed that SSH software running at port 22 of both addresses (OpenSSH 7.4) may suffer from ten vulnerabilities targeted by at least seven established threat actor groups. Thus, a threat actor may have compromised this address by accessing it through port 22 and exploiting the SSH vulnerabilities detected there.
Based on this ASI data, SecurityScorecard researchers consulted their netflow dataset to identify traffic to and from port 22 at these two IP addresses. The available netflow data contains sixty-six flows reflecting communication with the first address over port 22. These involved thirty-one unique, non-county IP addresses, of which vendors have linked thirty (available upon request) to malicious or suspicious activity. The first transfer to this address from a vendor-detected IP address occurred on July 14. Communication between it and the other IP addresses persisted until at least September 9.
Many of the flows to and from this address transferred 425.98 KB of data. Users have submitted fifty-eight malicious files of the same size to VirusTotal since July 1. The full list of these hashes is available upon request, but of these, the two files identified by the hashes 0455bfac0533d387187f9e26d9e37f43e0ff4005d4ccf5fb9cb5d5375276af6d and 0d95f157454f2ad4b1b0878fe75d3be22adaeec386fac15b7d09797047913a90 may be especially relevant. They both have the file name TeamViewer_Resource.dll. TeamViewer is a (sometimes legitimate) program that grants a user remote access to devices where it is installed. Tech support scams (like those enabled by the Cryxos trojan discussed above) often use it to access victim systems. It is possible that the flows transferring data the same size as these files may reflect these files’ use within the county’s networks.
The available netflow data additionally contains sixty flows reflecting communication with the second IP address over port 22. These involved twenty-seven unique, non-county IP addresses, of which vendors have linked twenty-six (available upon request) to malicious or suspicious activity.
In the case of both county IP addresses, given the flows’ frequency, relatively small byte counts, near-exclusive focus on port 22 at county IP addresses where the port was exposed, and many of the addresses’ previous links to SSH brute force attacks, some of this traffic may represent attacker targeting of vulnerable county SSH services or subsequent exploitation of compromised assets.
It bears noting that SecurityScorecard’s initial findings regarding SSH vulnerabilities at only two county IP addresses guided the research into the IP addresses above, as our netflow data indicates those IP addresses communicated with the vulnerable county addresses over port 22. While investigating the above IP addresses, researchers also observed frequent communication with additional county IP addresses. ASI has also found SSH vulnerabilities to affect software in use at port 22 of those addresses.
A broader view of traffic to port 22 at all of the IP addresses attributed to the county government may indicate additional targeting; over one thousand flows involving port 22 occurred between July 12 and September 12. Traffic to port 22 may be of particular concern in light of SecurityScorecard’s previous research, which suggests that threat actors targeted it in the lead-up to another ransomware attack.
Conclusion
The data collected and analyzed thus far has led researchers to hypothesize that the incident may have begun with social engineering or targeting of vulnerable SSH services.
This information was gathered and analyzed to briefly preview some of SecurityScorecard’s threat intelligence and investigation capabilities. SecurityScorecard was only able to query and contextualize some of its data. Thus, it should be noted that this is not an exhaustive list of issues related to the county’s overall cyber risk exposure and this particular incident.
Aside from the general observation that social engineering remains a common approach for ransomware groups, the appearance of the county government domains in files linked to the Cryxos trojan, which enables such activity, may support the hypothesis that county personnel fell victim to social engineering in the early stages of the attack. These stages may also have included SSH brute force attacks or exploitation of OpenSSH vulnerabilities, which the traffic between suspicious IP addresses and port 22 at vulnerable county IP addresses may suggest. However, given that SSH can facilitate file transfers, depending on its timing, frequency, and byte count, some of this traffic may additionally reflect exfiltration, C2 communication, or malware distribution after initial compromise rather than brute force attempts.




