The Forrester Wave™: Cybersecurity Risk Ratings Platforms, Q2 2024
Attack Surface Intelligence Identifies Additional Cuba Ransomware-Linked Indicators of Compromise
Executive Summary
- Following the publication of a report regarding the Cuba ransomware group’s recent activities, the SecurityScorecard Threat Research, Intelligence, Knowledge, and Engagement (STRIKE) Team leveraged SecurityScorecard’s unique data to enrich the indicators of compromise (IoCs) linked to this activity.
- STRIKE Team researchers identified additional IoCs not explicitly linked to the Cuba threat actor group in prior public reporting.
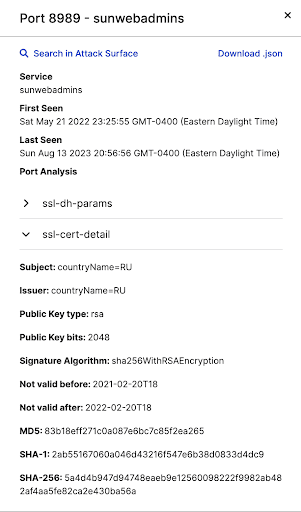
- These include a certificate observed by SecurityScorecard’s Attack Surface Intelligence tool, which users can track using the SHA-256 hash 5a4d4b947d94748eaeb9e12560098222f9982ab482af4aa5fe82ca2e430ba56a.
- SecurityScorecard recommends that organizations in sectors and geographies the Cuba ransomware group regularly targets add the IP addresses bearing the same certificate and SHA-256 hash discussed above to blocklists and update these blocklists regularly.
- Attack Surface Intelligence and other tools like it can support these efforts by enabling users to identify new servers with the same certificates by searching them for the certificate’s SHA-256 hash.
Background
On August 17, BlackBerry published a report on recent attacks by the Cuba ransomware group, some of which targeted critical infrastructure in the US. The report highlighted a novel feature of the Cuba group’s operations, exploitation of CVE-2023-27532, a vulnerability affecting Veeam Backup & Replication software.
The Cuba ransomware group has operated since 2019 but attracted greater attention from the cybersecurity community beginning in 2021. Previous alerts regarding the group’s operations note that it has targeted U.S. organizations in at least five different critical infrastructure sectors: Government Facilities, Financial Services, Healthcare and Public Health, Information Technology, and Critical Manufacturing and that its tactics, techniques, and procedures (TTPs) for initial access include exploitation of vulnerabilities in public-facing applications, phishing, and collaboration with initial access brokers. Additional research has linked other, more distinctive tooling to the group, highlighting its use of a custom strain of malware tracked as BUGHATCH for command-and-control (C2).
Findings
Researchers identified an IP address that recently served downloads of the BUGHATCH malware used by the Cuba Ransomware group, 64.235.39[.]82. They further identified a certificate identified by the SHA-256 hash 5a4d4b947d94748eaeb9e12560098222f9982ab482af4aa5fe82ca2e430ba56a, which appears to correspond to Cuba (or an affiliate)’s use of that IP address and others where that hash appears. The IP address and SHA-256 hash are therefore likely to be additional Cuba-linked indicators of compromise.
Methodology
STRIKE Team researchers consulted the indicators of compromise (IoCs) BlackBerry published in its report to identify others that may be linked to Cuba. Upon searching the SHA-256 hash of the BUGHATCH sample BlackBerry provided, 58ba30052d249805caae0107a0e2a5a3cb85f3000ba5479fafb7767e2a5a78f3, in cybersecurity information-sharing platform VirusTotal, researchers noted that one IP address, 64.235.39[.]82, served downloads of the file in April 2023.
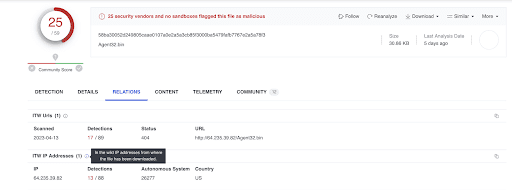
- 38.108.119[.]121
- 38.135.122[.]130
- 195.206.181[.]198
- 144.172.83[.]13
Publicly available information has already linked three of these IP addresses, 38.108.119[.]121, 38.135.122[.]130, and 144.172.83[.]13, to the Cuba ransomware group. 38.108.119[.]121 and 144.172.83[.]13 appeared in a #StopRansomware alert about Cuba that CISA published in August 2022 and 38.135.122[.]130 appears in a VirusTotal collection about BUGHATCH, the aforementioned strain of malware Cuba is known to use. While not specifically linked to Cuba, VirusTotal has linked 195.206.181[.]198 to other malicious activity.
These results, taken alongside the appearance of the same hash at an IP address that served a download of Cuba-specific malware, suggest that the certificate suggests the use of the IP addresses where it appears by either the Cuba ransomware group or a threat actor linked to it.
Conclusion
While Cuba’s exploitation of CVE-2023-27532 speaks to the group’s adaptability and suggests that it is ready and willing to exploit new vulnerabilities as they appear, it is not especially novel; while Cuba has not exploited this particular CVE before, other groups have, and analysts have observed Cuba exploiting other known vulnerabilities in the past. This likely indicates that Cuba, like many other threat actor groups, will attempt to exploit new vulnerabilities as they (and PoC exploits for them) appear; in general, a larger number of attackers will tend to attempt to exploit a given vulnerability as word of the vulnerability and exploits for it circulate more widely over time.
The exploitation of a Veeam Backup & Replication vulnerability in particular may additionally reflect a wider imperative for ransomware groups to apply pressure to victims and increase the likelihood of a ransom payment, in this case by limiting victims’ chances of recovery. Ransomware operators often rely on victims having no option to access their data other than paying for the attackers’ decryption key. When secure, data backups can help limit ransomware’s impact by offering victim organizations the opportunity of using them to restore their systems rather than paying attackers for a decryption key. However, if attackers can also compromise these backups (by, for example, exploiting a vulnerability in backup software like Veeam’s), they can further limit their victims’ options and, in the process, make them more likely to pay a ransom.
Recommendations
In addition to the public recommendations already circulated, including promptly updating software affected by published vulnerabilities (such as CVE-2023-27532), SecurityScorecard recommends that organizations in sectors and geographies the Cuba ransomware group regularly targets add the IP addresses bearing the same certificate and SHA-256 hash discussed above to blocklists and update these blocklists regularly. Attack Surface Intelligence and other tools like it can support these efforts by enabling users to identify new servers with the same certificates by searching for the certificate’s SHA-256 hash.


