Prepare for Zero-Day Threats: Military and Private Sector Leaders Share Their Insights
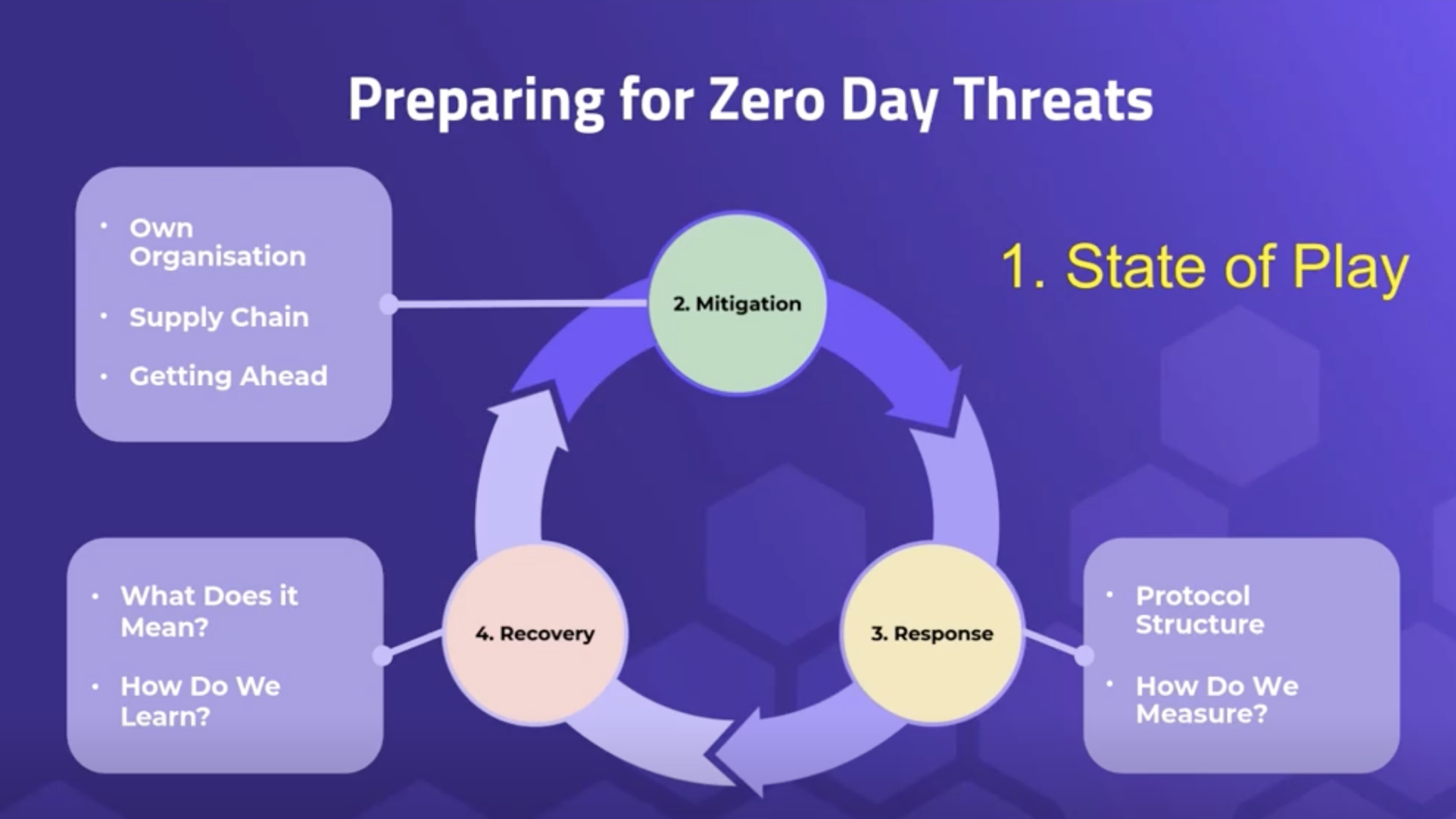
Preparing for zero-day threats within your organization and within your supply chain can be difficult.
Leading cybersecurity experts Major General John F. Wharton, (US Army retired); Oleg Strizhak, Shell’s Digital Supply Chain Risk Manager; and Sam Curry, the CISO of Zscaler, recently sat down with SecurityScorecard’s President of International Operations Matthew McKenna to discuss how organizations can prepare themselves and their supply chains for zero-day attacks as well as best practices for supply chain risk management.
5 ways to prepare for zero-day threats
By nature, zero-days can be difficult to predict and respond to in a timely manner, especially when your organization — and those within your supply chain —may lack the expertise and resources. This makes preparing beforehand all the more critical.
During the webinar, the experts all agreed on the importance of preventing cyber incidents in the first place; Strizhak stressed:
“Don’t wait until you discover a zero-day vulnerability; be proactive and have a clearly defined heat map of all your digital assets… which ones are high risk and low risk.”
1. Examine the role of infrastructure in preparing for zero-day threats
Our critical infrastructure systems run smoothly, in large part, because they are all interconnected. Whether it’s energy, transportation, telecommunications, water, or healthcare, critical infrastructure is part of an ever-expanding attack surface, with innumerable configurations, devices, and platforms that can be exploited. With that expanding attack surface comes the rise of data breaches and ransomware attacks.
That number grows when vendors enter the picture, as Curry observes: “Whenever there’s a transition from one system to another, one vendor to another… you’re going to find more vulnerabilities. How we glue this stuff together matters.”
Major General Wharton’s experience in the military has given him a unique perspective on cybersecurity risk, and what it takes for all organizations to prepare themselves for disruptions: “You need to operate left of the boom to prevent and deter an attack, not just right of the boom.” He adds: “Many companies just look at their own lane but not at where they’re connected and other vulnerabilities along that connection. Are you being situationally aware of everyone coming in?”
Earlier this year, during the World Economic Forum’s (WEF) Annual Meeting in Davos, we released a report on critical infrastructure, which found that cyber resilience is getting worse, not better. Cyberattacks on critical infrastructure have slowly been increasing in severity over the last year; and the cost has gone up by $1.17 million to $5.4 million per incident, largely due to the growing number of third- and fourth-party vendors. Furthermore, nation-state attacks on critical infrastructure have doubled in frequency over the last year. And high severity vulnerabilities detected across publicly exposed digital footprints have increased 38%. With an average time of 14 days for an exploit to be released into the wild following the detection of a vulnerability, precise prevention and response strategies are essential.
2. Avoid a prescriptive approach to regulations
With the growing landscape of cybersecurity regulations at the local, state, national, and international level, that panel agrees that the adoption of regulatory frameworks is important. But if these guidelines aren’t implemented correctly—and if resources aren’t allocated correctly—they won’t do any good. Curry points out that it’s tempting to be prescriptive with cyber regulations, but that’s the wrong approach because it’s a rapidly-evolving field. “It’s really about how you do cyber as opposed to what you do in cyber,” he said.
Major General John F. Wharton added:
“You need to operate left of the boom to prevent and deter an attack, not just right of the boom.”
3. Prepare your Incident Response team
Having the right team in place is critical when responding to a zero-day or cyber event. Strizhak asserts that once a zero-day is discovered, the clock is already ticking, so you need to have the right people ready to detect, triage, and analyze what you’re dealing with. He stresses the importance of training your employees and knowing how to reach your vendors if the usual means of communication are down.
4. Conduct a zero-day postmortem with empathy
In the aftermath of a cyber incident, look at what was done and how systems and processes can be improved. In addition to examining your own organization’s missteps, it’s also key to look at your vendors, suppliers, and consultants. Though it may be tempting to play the blame game, Curry stresses this isn’t the time for that.
“It’s not to bayonet the wounded, that’s not why you’re doing this. There are perfectly good reasons why people have zero days—it’s not a reason to toss out a vendor or a supplier.”
We need to acknowledge that everyone has vulnerabilities, and this can happen to anyone. What we can judge an organization on is how it handles the response to a zero-day.
In addition to evaluating your zero-day response, it’s also crucial to assume that cybersecurity vulnerabilities may still exist in your systems, which is why it’s recommended to take preventive actions. Major General Wharton likens this to regular maintenance on a car: “You can wait for a vehicle to break down, or you can do preventative maintenance along the way.” The ability to respond to zero days is correlated with your ability to prepare, and knowing the variables you can control, such as patching networks, understanding security gaps, and conducting assessments.
5. Move forward with metrics that matter
The network is never going away. The more we move to digitization—in both physical and digital assets—the more vulnerabilities we’ll encounter. How then can we mature our ecosystems and know we’re improving? “If you can’t measure it, you can’t measure it,” Curry notes. Finding a solution to evaluate cyber posture is imperative to staying secure and resilient. It’s also critical not to copy someone else’s program because what works for them might not necessarily work for your organization.
In closing, the panel concurs that staying proactive is the key to mitigating the risk of zero-day vulnerabilities. According to Strizhak, the basics are everything:
“Don’t wait for zero-day to knock at your door. Get your act together and work beforehand. Get the basics right, and it’ll set you up for success. It will instill resilience not just within your organization but within your supply chain.”
Prepare for zero-day threats with SecurityScorecard
SecurityScorecard has integrated itself into the response process to help customers prepare for and respond to zero-day vulnerabilities.
Attack Surface Intelligence can quickly query a zero-day or CVE that’s been exploited, and cross-validate it against portfolios of companies we monitor. Automatic Vendor Detection can understand the extended supply chain that’s been compromised. And our security ratings platform provides organizations with vendor cyber risk at scale.
Most recently, we’ve launched Zero-Day-as-a-Service (ZDaaS) to help alert organizations to new and emerging potential zero-day threats across their vendor ecosystem.
To learn more about managing vendor risk, securing supply chains, and safeguarding critical systems and data, visit SecurityScorecard.com.


The Current State of Critical Infrastructure
How to Prepare for Zero Day Threats in Your Supply Chain
Watch the Webinar On-Demad



