Cyber Risk Intelligence: Exploitation of CVE-2023-47246
Executive Summary
- On November 8, SysAid disclosed that the Cl0p ransomware group had exploited a previously unknown vulnerability, now tracked as CVE-2023-47246, in SysAid’s on-premise IT Service Management (ITSM) software.
- The SecurityScorecard Threat Research, Intelligence, Knowledge, and Engagement (STRIKE) Team consulted SecurityScorecard’s Attack Surface Intelligence data and a partner’s network flow (NetFlow) data to identify possible targets of the exploit.
- The prevalence of both the vulnerability and its exploitation appears more limited than previous, similar Cl0p activity.
- While SecurityScorecard’s data suggests that the scope of the campaign is relatively small, it has nonetheless identified one particularly likely target IP address.
Background
On November 8, SysAid reported that the threat actor group that Microsoft tracks as DEV-0950 or Lace Tempest, better known as the Cl0p ransomware group, had recently exploited a previously unknown vulnerability in SysAid’s on-premise IT Service Management (ITSM) software now tracked as CVE-2023-47246. The report also provided indicators of compromise (IoCs) linked to the campaign exploiting the vulnerability, including IP addresses observed conducting command and control (C2) communications with malware distributed as part of the same activity.
The exploit is the latest in a series of zero-day vulnerabilities the Cl0p group has exploited, which speaks to the group’s continued ability ability to identify and exploit new vulnerabilities, with Cl0p having previously (and somewhat more famously) exploited vulnerabilities in Accellion and MOVEit file transfer software in campaigns that resulted in large numbers of data breaches.
Findings
The STRIKE Team has identified a group of queries for SecurityScorecard’s Attack Surface Intelligence module, through which users can identify versions of SysAid that the vulnerability may affect. Researchers further conducted a preliminary review of traffic data involving the IP addresses named as IoCs to assess the campaign’s possible scope.
The following Attack Surface Intelligence queries can identify possibly affected versions of SysAid’s software:
- (http_title:”SysAid Help Desk Software”
- (http_title:”SysAid Mobile”)
- (http_favicon_hash:”Unknown favicon MD5: 5F30870725D650D7377A134C74F41CFD”)
Users can additionally run all three queries simultaneously by formatting them as follows:
- (http_title:”SysAid Help Desk Software” OR http_title:”SysAid Mobile” OR http_favicon_hash:”Unknown favicon MD5: 5F30870725D650D7377A134C74F41CFD”)
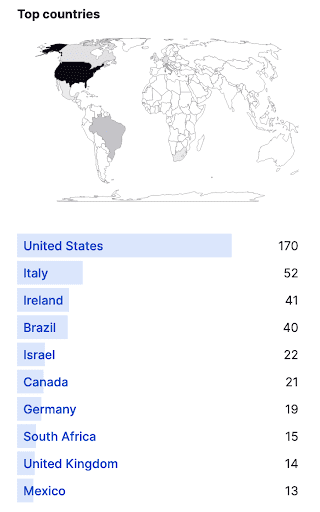
These queries return a combined total of 576 IP addresses attributed to 330 different organizations distributed across 36 countries, with the United States appearing to host the highest concentration of observed IP addresses (170 of 576).
The STRIKE Team additionally set out to further investigate possible activity linked to exploitation of the vulnerability by drawing inferences from traffic involving the IP addresses that SysAid named as IoCs when reporting the vulnerability. Researchers consulted a strategic partner’s network flow (NetFlow) data to collect and analyze a sample of the traffic that these IP addresses experienced, as communication with them may suggest that the campaign targeted the organizations using the IP addresses observed communicating with those named as IoCs.
When paired with the detections in Attack Surface Intelligence, the available traffic sample suggests that the scope of the campaign exploiting the vulnerability is somewhat limited compared to the Cl0p group’s previous campaigns exploiting other zero-day vulnerabilities: only one IP address where Attack Surface Intelligence observed possibly affected software appears in the traffic sample. This IP address may be particularly likely to be a target of the campaign, given that it both communicated with an IoC and appears to host SysAid software.
Conclusion
The STRIKE Team’s analysis of the possible impact and scope of exploitation of CVE-2023-47246 is ongoing. However, its research has offered some preliminary suggestions regarding the prevalence of the vulnerability and its exploitation. SecurityScorecard’s Attack Surface Intelligence tool has identified a collection of IP addresses where possibly vulnerable SysAid versions are in use. The available NetFlow sample suggests that only one of these IP addresses communicated with IoCs linked to the campaign exploiting the vulnerability. While this suggests that that particular IP address may be especially likely to have been a target, it also suggests that the campaign’s scope was, at least within the period of the traffic sample, fairly limited.
The appearance of only a single IP address in both the Attack Surface Intelligence results and traffic sample may suggest that recent exploitation (at least exploitation involving the IoCs SysAid named) has not been particularly extensive. News of the exploit nonetheless reflects the Cl0p ransomware group’s ongoing ability to discover and leverage new vulnerabilities, as its previous (and apparently more widespread) activity targeting what were, at the time, zero-day vulnerabilities in Accellion, GoAnywhere, and MOVEit products can also illustrate.




