Test your team’s readiness with Red Team Exercises
Get a comprehensive picture of your defensive capabilities, from exploit to detection and response, and see how your team would perform under real-world conditions
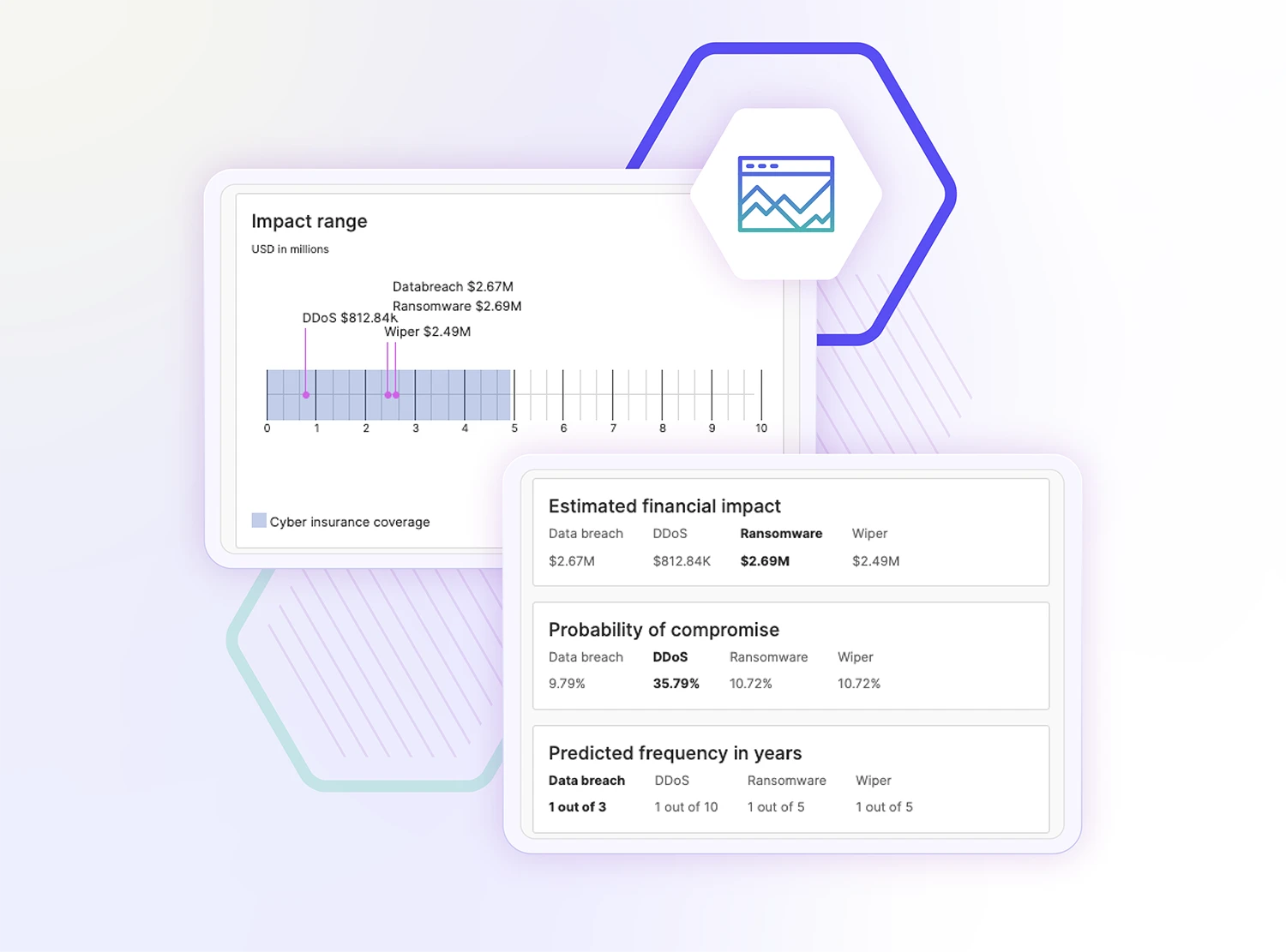


Experience immersive, real-world cyberattack simulations
- Evaluate your organization’s resilience against sophisticated cyber threats
- Stress-test your systems and people to find vulnerabilities and see how your team responds
- Learn from a comprehensive analysis of cyber risks specific to your organization derived from the red team exercise
- Acquire practical insights and recommendations for enhancing your security posture based on red team findings
- Customize red team scenarios to fit your unique business environment and potential threat landscape
- Establish processes for continuous assessment and improvement, fostering a culture of ongoing enhancement in your cybersecurity defenses
-
Our team of experts
SecurityScorecard’s Red Team services consistently deliver valuable guidance to companies seeking to optimize their security measures. They ensure the efficient establishment and enhancement of cybersecurity practices, fostering sustained resilience through proactive and targeted assessments.
- Comprising highly qualified professionals, including certified ethical hackers, penetration testers, and experts with industry-recognized certifications like CISSP and OSCP, our Red Team services bring together an elite group of specialists for comprehensive and impactful assessments
- Leveraging diverse expertise and extensive experience, our Red Team possesses a deep understanding of security principles and best practices, ensuring the delivery of meticulous and effective penetration testing services tailored to our client’s unique cybersecurity needs

Outcomes
-

Realistic threat simulation
Realistic simulations of sophisticated cyber threats, providing insights into your organization’s response capabilities
-

Vulnerability identification
Identify vulnerabilities and weaknesses in your systems by leveraging the focused assessments conducted by our Red Team
-
Strategic entry point discovery
Proactively identify and address potential entry points for malicious actors, facilitating targeted risk mitigation
-
Comprehensive risk analysis
Receive a comprehensive analysis of cyber risks specific to your organization, derived from the outcomes of the exercises
Hear From Our Customers

-
"SecurityScorecard has been a consistently reliable solution for SoftServe. I recently decided to enhance our security measures by incorporating the Red Team Service. The Open-Source Intelligence (OSINT) details provided by the Red Team were impressive."
AVP, InfoSec Michael Kropyva1 / 0
-
“SecurityScorecard has allowed me and my team to automate and scale many of the functions of our vendor risk management program as well as continuously monitor their internal and third-party security posture.”
Chief Information Security Officer, Virgin Pulse1 / 0
FAQs
What are Red Team exercises?
Red team exercises are simulated attacks designed to test an organization’s security team by mimicking real-world cyber threats, including brute force attacks and exploitation of potential vulnerabilities. They help assess the security posture and identify areas of improvement.
What is the purpose of Red Team training?
Red team training enhances a security team’s ability to detect and respond to sophisticated attack techniques and persistent threats.
How do Red Team exercises differ from Blue Team activities?
Red team exercises focus on attacking to uncover weaknesses, while the blue team activities defend against these simulated attacks. Together, they strengthen overall security through continuous team activities and collaboration.
What do Red Team services include?
Red team services involve thorough vulnerability assessments, analysis of attack vectors, and tailored simulations to expose weaknesses. This helps the cybersecurity team prepare for advanced threats.
What types of attack techniques are used during Red Team operations?
Red team operations utilize a variety of techniques, including social engineering, phishing, brute force attacks, and exploitation of attack vectors, to simulate persistent threats and test an organization’s defenses.
Can Red Team services be customized for different industries?
Yes, red team services are tailored to each organization’s unique environment and industry requirements, ensuring the most relevant and effective testing for potential vulnerabilities.
How do Red Team services help in strengthening my Blue Team's skills?
Red team services provide realistic scenarios that challenge your Blue Team, helping them improve their detection and response capabilities. This enhances overall team collaboration and operational efficiency.
Can Red Team operations identify new attack vectors?
Yes, red team operations often reveal previously unknown attack vectors, allowing organizations to strengthen their defenses against a wider range of cyber threats.