Identify Cybersecurity Vulnerabilities with Penetration Testing
Use simulated cyberattacks to find vulnerabilities in your systems. This proactive assessment helps identify entry points for malicious actors, preventing potential exploitation across your external attack surface.
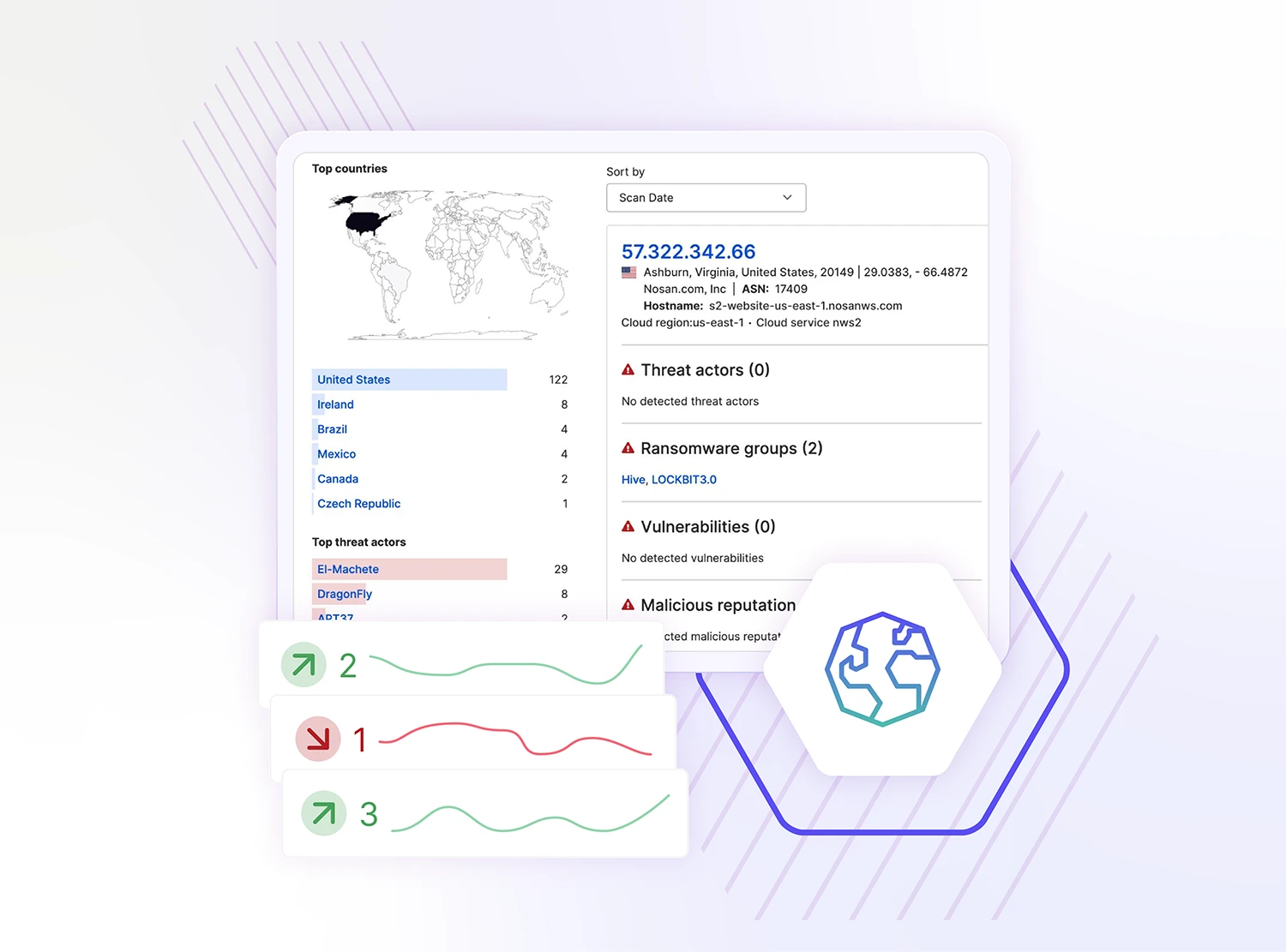


Take a deeper look at your external attack surface
- Identify and pinpoint vulnerabilities within your systems through rigorous cyber penetration testing
- Conduct simulated cyberattacks that closely mimic real-world scenarios to assess system resilience
- Discover potential entry points for malicious actors, allowing for proactive mitigation
- Gain a comprehensive understanding of the cybersecurity risks specific to your organization
- Receive practical insights and recommendations for strengthening your security posture
- Tailor testing scenarios to match your unique business environment and potential threat landscape. Each penetration test is customized to identify specific vulnerabilities and security gaps
- Ensure adherence to industry regulations and standards by addressing identified vulnerabilities
- Establish a foundation for continuous improvement by addressing and mitigating identified risks
-
Our team of experts
SecurityScorecard’s penetration testing services team consistently provides valuable guidance for companies looking to optimize their security measures. They ensure the efficient establishment and enhancement of cybersecurity practices for sustained resilience.
- The team consists of highly qualified professionals, including certified ethical hackers, penetration testers, and experts with industry-recognized certifications like CISSP and OSCP
- With diverse expertise and extensive experience, the team possesses a deep understanding of security principles and best practices, ensuring the delivery of robust and effective penetration testing services for our clients

Outcomes
-

Go a level deeper
In-depth assessments identify and pinpoint vulnerabilities within your systems and across your attack surface
-
Realistic simulations
Conduct simulated cyberattacks closely resembling real-world scenarios, providing insights into your system’s resilience
-
Strategic entry point discovery
Identify and neutralize potential entry points for malicious actors before your business gets hit with a crippling breach
-
Actionable recommendations
Receive practical insights and recommendations, empowering your organization to strengthen its overall cybersecurity posture
Hear From Our Customers

-
“SecurityScorecard has allowed me and my team to automate and scale many of the functions of our vendor risk management program as well as continuously monitor their internal and third-party security posture.”
Virgin Pulse Chief Information Security Officer1 / 0
FAQs
What is Penetration Testing?
Penetration testing, or pen testing, is a cybersecurity practice where a simulated attack is conducted on a system to identify and exploit security weaknesses. It helps assess how well security controls can withstand real-world attacks.
What types of penetration testing are available?
Penetration tests can target external networks, web applications, or internal systems. Different types include black-box, white-box, and gray-box testing, each offering unique insights into exploitable vulnerabilities.
What are the benefits of penetration testing?
Penetration tests provide a comprehensive report detailing critical security vulnerabilities and recommendations for remediation, helping security teams strengthen defenses and reduce cyber attack risks. They also help organizations meet compliance requirements for security standards.
How does cybersecurity penetration testing differ from a vulnerability assessment?
While a vulnerability assessment identifies and classifies security weaknesses, cyber penetration testing goes further by attempting to exploit those vulnerabilities, simulating real-world attacks to evaluate the effectiveness of security controls.
What can security teams expect from a comprehensive penetration test report?
The report provides detailed findings on exploitable vulnerabilities, including risk levels and suggested remediation steps. It helps the security team prioritize fixes and strengthen defenses against potential cyber-attacks.
What is the role of penetration testing in assessing external network security?
Penetration tests on external networks simulate cyber attacks to uncover vulnerabilities that could be exploited by malicious actors, helping to secure the organization’s digital perimeter defenses.
How often should penetration testing be conducted?
It’s recommended to perform penetration testing annually or after significant changes to the infrastructure, such as deploying new systems or applications, to ensure continuous protection against evolving threats. Organizations with higher risk profiles, such as those in finance, healthcare, or critical infrastructures, may benefit from more frequent testing.