What is Threat Intelligence in Cybersecurity? A Comprehensive Overview
The evolving threat landscape necessitates proactive approaches to identify, assess, and mitigate potential cyber security risks. Threat intelligence is one of the most potent weapons we have against digital hazards. Yet, many organizations remain uncertain about what it entails, how to apply it effectively, and what threat intelligence solution to choose. This lack of understanding could be detrimental as cyber threats continue to evolve, becoming more sophisticated and disruptive.
So, what is threat intelligence, and how can it help bolster an organization’s security posture? This blog post aims to demystify this crucial cybersecurity element, diving deep into its key facets, answering these important questions:
- What is threat intelligence?
- How does threat intelligence work?
- What are the types of threat intelligence?
- What is the threat intelligence lifecycle?
- What are the benefits of threat intelligence?
What is threat intelligence?
Threat intelligence, also known as cyber threat intelligence, is a branch of cybersecurity that focuses on the collection and analysis of information about potential threats and vulnerabilities that an organization could face. This information comes in various forms, from raw, unprocessed data to finished intelligence ready for human consumption.
The objective of threat intelligence is to provide context—such as who is launching the attacks, their methods, their motivations, and what they’re after—to help organizations make informed decisions about their security. It can help predict potential attack vectors and prevent breaches before they occur. The process of generating threat intelligence typically follows a lifecycle, which includes direction, collection, processing, analysis, production, dissemination, and feedback.
Threat Data vs Threat Intelligence
Before moving on, it’s worth dialing into how threat data differs from threat intelligence. For a less technical spin, we’ll use an analogy of school bullies to explain the difference.
Threat data is a known list of information, such as threat actor names or bad IPs — without further context. In the analogy, it’s a list of bullies that could attack you.
On the other hand, with threat intelligence, you have a lot of pieces of important information available that you can use to make fast decisions. Focused threat intelligence is knowing that the bully will be wearing a plaid shirt and has blonde hair. He’s going to punch you in the stomach at 3PM on Tuesday by the monkey bars. You don’t need to sift through the noise of pieces of threat data to understand if there truly is a bully out to get you and to the level of harm he could cause.
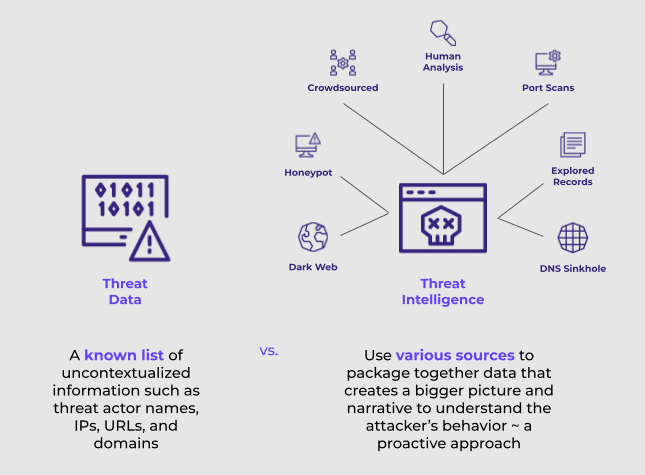
Threat intelligence is costly because it requires gathering different types of data such as CVEs, malware infections, leaked credentials, and more to understand the tactics, techniques, and procedures or TTPs of a threat actor. This information comes from different sources such as honeypots, sinkholes, port scans and more. Context rich threat intelligence correlates it for you, often curated by human analysis. When you’re using high quality and a variety of threat intelligence, you are able to proactively look for when a bully is out to get you and know in a matter of minutes how to protect yourself.
How does threat intelligence work?
Threat intelligence works by collecting, analyzing, and interpreting information about potential or current attacks that threaten an organization. It looks at issues like who is attacking you, what their motivations and capabilities are, and what techniques they’re using. The goal is to arm organizations with actionable insights they can use to protect themselves better and respond more effectively to cyber threats.
What are the types of threat intelligence?
There are three primary types: strategic (sometimes integrated), operational, and tactical (sometimes technical) threat intelligence. Taking a closer look at each:
1. Strategic Threat Intelligence
Strategic threat intelligence is high level information on changing risks that isn’t too technical. It focuses on long-term, high-level insights into the strategies and tactics of threat actors. This enables executives and decision-makers who need to understand the wider landscape of threats to shape their organization’s cybersecurity strategy and align with business goals.
Also in this category is integrated threat intelligence. This is where vendor risk managers look at information coming from their third party vendors, specifically focusing on threats that impact those vendors. This helps more proactively alert the more tactical and operational teams on threats that could harm your organization.
2. Operational Threat Intelligence
This level tends to fall between strategic and tactical levels; operational threat intelligence provides detailed insights relevant to ongoing cyber security operations, specific cyber threats, and how they operate. This information includes indicators of compromise (IOCs) and tactics, techniques, and procedures (TTPs) used by threat actors. It aids cybersecurity teams in preparing for, detecting, and responding to these threats. It also enables the broader security team to strengthen defenses across people, processes, and/or technology.
3. Tactical Threat Intelligence
Tactical threat intelligence focuses on the here and now. It involves real-time information about immediate threats to an organization. Tactical intelligence helps front-line security teams understand and mitigate the latest cyber threats. This is also where system admins and the more technical teams — including SOC and IR teams — use intelligence to make decisions on how to remediate cyber vulnerabilities.
What is the threat intelligence lifecycle?
The threat intelligence lifecycle is a framework that outlines the process of gathering, analyzing, and applying threat intelligence. It comprises a series of steps, each designed to convert raw data about potential threats into actionable insights that can be used to enhance an organization’s security posture. Here are the common steps involved:
1. Direction (or Planning)
This first step involves defining the objectives and scope of the threat intelligence activity. What are the key assets that need to be protected? What are the main threats to these assets? The answers to these questions help set the direction for the subsequent stages of the lifecycle.
2. Collection
In this step, data is gathered from a variety of sources. These sources can include open source intelligence (OSINT), social media, deep and dark web, threat intelligence feeds, human intelligence (HUMINT), internal system logs, and more.
3. Processing
Once the data is collected, it is then processed. This involves cleaning the data, filtering out irrelevant information, and converting it into a format that can be easily analyzed. This step may also involve enrichment, which means adding context to the raw data to make it more useful.
4. Analysis
In this crucial step, the processed data is analyzed to identify patterns, trends, and anomalies that could indicate a potential threat. Analysts use various techniques, such as data mining, statistical analysis, and machine learning, to interpret the data and extract meaningful insights.
5. Production
After analysis, the results are then compiled into a threat intelligence report. This report provides a comprehensive overview of the identified threats, the assets they could potentially impact, and recommended countermeasures.
6. Dissemination
The threat intelligence report is then distributed to the relevant stakeholders within the organization. This could include IT teams, security operations centers (SOCs), executive leadership, and any other parties who need to be aware of the threats and how to mitigate them.
7. Feedback/Review
The final step in the threat intelligence lifecycle is to gather feedback on the effectiveness of the threat intelligence provided, and review and adjust the direction, collection, processing, and analysis methods as needed to improve future threat intelligence activities.
It’s important to note that this is an iterative process. As the cyber threat landscape evolves, the threat intelligence lifecycle continually repeats, constantly updating the organization’s understanding of threats and enhancing its ability to protect itself.
What are the benefits of threat intelligence?
Now that we understand what threat intelligence is and the different types it encompasses, let’s examine how it benefits organizations and helps fortify their cybersecurity infrastructure:
Proactive Defense
Threat intelligence enables organizations to shift from a reactive security posture to a proactive one. By understanding the potential threats, companies can implement measures to prevent attacks before they happen.
Informed Decision-Making
With detailed insights about the nature of threats, their potential impact, and the possible mitigation strategies, organizations can make well-informed decisions about allocating resources, investing in security tools, and planning their overall security strategy.
Improved Incident Response
Threat intelligence informs organizations about the nature of the threat, thus reducing response time in case of a breach. Knowing what you’re up against allows for quick, effective actions, minimizing the impact of an attack.
Risk Management
By understanding the threat landscape, organizations can identify and prioritize the risks that pose the greatest danger. This information can guide the development of a robust risk management strategy.
Who benefits from threat intelligence?
Threat intelligence benefits a wide array of entities as it provides insights into potential threats and cybersecurity risks. Here are some entities that can significantly benefit:
Businesses and Organizations: These entities often have valuable data that, if compromised, could lead to significant financial and reputational loss. Threat intelligence can help them identify potential threats, understand the tactics and techniques of adversaries, and implement preventative measures before an attack occurs. This is particularly crucial for sectors that handle sensitive information, such as the financial, healthcare, and tech sectors.
Government Agencies: Governments need to protect not only their internal data but also the infrastructure and services they provide to citizens. Threat intelligence can provide insights into potential nation-state actors or terrorist groups that might be planning cyberattacks.
Individuals: On a smaller scale, individuals can also benefit from threat intelligence. While they might not access detailed threat reports, they can make use of the advice and guidelines provided by cybersecurity organizations based on threat intelligence to protect their personal data.
Non-Profit and Non-Governmental Organizations (NGOs): These entities often work in sensitive areas and deal with crucial data. Threat intelligence can help them safeguard their information and maintain the trust of their donors and the communities they serve.
Law Enforcement and Legal Entities: Understanding the current cyber threat landscape can help law enforcement agencies be proactive in their investigations and legal entities to frame their arguments or judgments correctly.
What is the future of threat intelligence?
There are several trends shaping the future of threat intelligence and its increasing importance for effective risk management:
AI and Machine Learning
The use of artificial intelligence (AI) and machine learning algorithms is expected to become more prevalent in threat intelligence. These technologies can aid in detecting patterns, predicting threats, and identifying potential vulnerabilities faster than human analysts. Generative AI across industries will do “more crunching of the data” so that teams can focus on more action.
More vulnerabilities
2023 is on track to have more vulnerabilities than years prior, and this upwards trend will likely continue as attack surfaces and sophistication grow. Advanced Persistent Threats (APTs,) in particular, are becoming more common. These types of attacks, often state-sponsored, are meticulously planned and can infiltrate systems undetected for long periods.
Integration of threat data
As digital and physical worlds merge, security systems will need to adapt. Integrated security systems, including intrusion detection, video surveillance, access control, fire, and life safety, network security, etc., managed from a unified platform, will be essential. These systems would use artificial intelligence, machine learning, and big data analytics to detect, analyze, and respond to threats across the physical-digital divide.
How to apply threat intelligence
To effectively apply threat intelligence, one must begin with a clear understanding of the organization’s assets and the potential risks associated with them. This can range from customer data and financial information to proprietary software. Knowing the importance of these assets and their vulnerabilities allows for a more targeted and efficient application of threat intelligence. Once key assets and risks are understood, organizations need to collect intelligence from reliable and relevant sources, which can include subscription-based feeds, open-source intelligence, industry groups, or even government agencies.
After the collection phase, the raw data needs to be meticulously analyzed for valuable insights. This can involve spotting patterns or trends, cross-referencing data from different sources, or assessing the credibility of an identified threat. Based on the analysis, it is then essential to implement protective measures to guard against the identified threats. These protective measures might include software updates, firewall improvements, staff training on recognizing phishing attempts, or modifying protocols for managing sensitive information.
In the evolving landscape of cyber threats, it’s crucial to share relevant intelligence with other entities in the network or industry, provided it is legally and ethically appropriate. Lastly, a continuous review and adaptation strategy should be in place, ensuring the effectiveness of protective measures against the dynamic nature of cyber threats.
Access threat intelligence tailored to your organization
Interested in more threat intelligence content? Watch our webinar “Threat Intelligence 101” on-demand or join us for Threat Talk Thursday!
And, as always, you’re welcome to request a demo of Attack Surface Intelligence and test drive how your organization can benefit from threat intelligence.





