What is Security Information and Event Management (SIEM)?
With cyber threats constantly evolving, organizations need robust mechanisms to protect their data and IT infrastructure. Security Information and Event Management (SIEM) has emerged as a critical component of modern cybersecurity strategies, serving as the central nervous system for enterprise security operations.
This comprehensive blog post delves into SIEM, its core functionalities, benefits, and why it’s essential for organizations of all sizes in today’s threat landscape.
Understanding SIEM
SIEM is a comprehensive solution that provides real-time analysis of security alerts generated by applications and network hardware across diverse IT environments. The term SIEM, coined around 2005, combines two essential aspects of security management: Security Information Management (SIM) and Security Event Management (SEM).
While SIM focuses on collecting, analyzing, and reporting log data from disparate sources, SEM is concerned with real-time monitoring and security incident management.
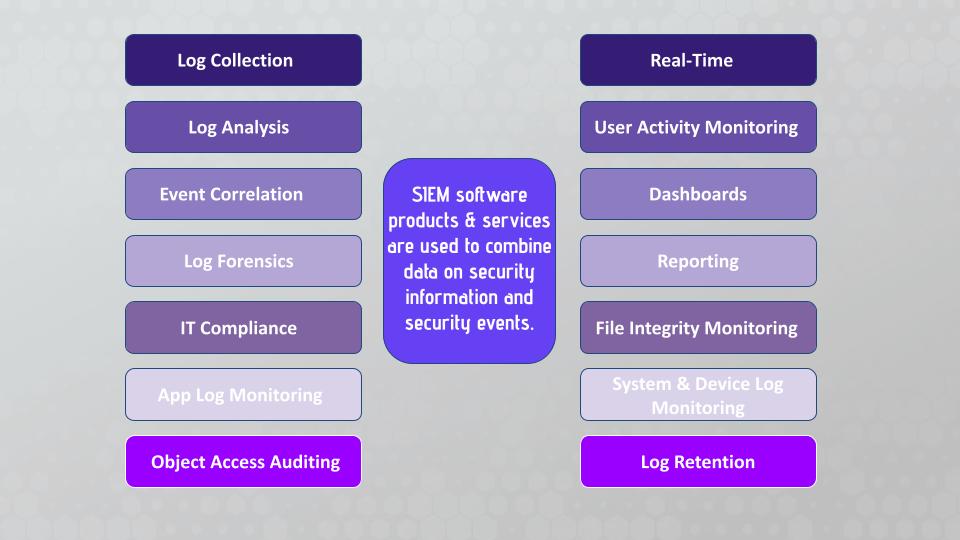
A Security Information and Event Manager (SIEM) is a unified platform that enables organizations to identify, investigate, and respond to security threats more efficiently than traditional point solutions.
Modern SIEM systems have evolved beyond simple log management to incorporate advanced capabilities like behavioral analytics, threat intelligence integration, and automated response mechanisms.
What sets SIEM apart from other security tools is its ability to aggregate security event data from across an organization’s entire digital ecosystem, from user devices and cloud environments to network infrastructure and applications.
This holistic approach provides security analysts with the comprehensive visibility needed to detect sophisticated attack vectors that might go unnoticed.
What are the primary features of a Security Information Event Management (SIEM) tool?
Understanding SIEM’s core functionalities is crucial for organizations evaluating their security infrastructure needs. Here are the six main functionalities that define modern SIEM capabilities:
Data collection and aggregation
SIEM systems excel at log collection from various sources such as network devices, servers, firewalls, antivirus software, user devices, active directory systems, and cloud environments. This data includes logs, events, and other relevant security information from both on-premises and cloud-based security systems. By aggregating this data, SIEM provides a centralized view of an organization’s security posture.
The system’s ability to ingest data from disparate sources—whether endpoint detection and response (EDR) tools, network security appliances, or application logs—creates a comprehensive view of an organization’s security posture.
Modern SIEM platforms can handle massive volumes of security event data, processing millions of events per second while maintaining real-time analysis capabilities.
Normalization and log management
The collected data is often in different formats, making analysis challenging. SIEM systems normalize this data, converting it into a standard format, facilitating easier analysis and data correlation. This normalization process is critical for effective log management, as it standardizes diverse data formats from various vendors and systems into a unified structure.
Effective normalization enables security analysts to quickly identify patterns and anomalies across different systems without needing to understand each vendor’s unique log format. This standardization is particularly valuable in complex environments where organizations use security tools from multiple vendors.
Event correlation and correlation rules
One of SIEM’s most powerful features is its ability to correlate data from different sources through sophisticated correlation rules. By correlating events and logs, SIEM can identify patterns that may indicate a security threat. For example, multiple failed login attempts from different locations within a short period could be flagged as a potential brute-force attack.
Data correlation extends beyond simple rule-based detection. Advanced SIEM platforms incorporate AI algorithms to identify subtle patterns that traditional correlation rules might miss. This capability is essential for detecting advanced persistent threats (APTs) and other sophisticated attack vectors that span multiple systems and timeframes.
Real-time monitoring and alerting
SIEM continuously monitors the aggregated data in real time, providing security operation centers with immediate visibility into potential security incidents. It generates alerts for the security team when it detects suspicious activities or anomalies—such as Distributed Denial-of-Service (DDoS) attacks, phishing emails, or unusual user activity monitoring patterns.
These alerts are often prioritized based on the severity of the threat and configured security policies, enabling teams to respond promptly to the most critical issues. Modern SIEM platforms also incorporate User and Entity Behavior Analytics (UEBA) to reduce false positives and provide more contextual alerts to security analysts.
Incident response and security orchestration
Beyond alerting, many SIEM systems have built-in incident response capabilities and can integrate with Security Orchestration, Automation, and Response (SOAR) platforms. This integration can include automated actions such as blocking IP addresses, isolating compromised systems, or triggering predefined response protocols.
Combining SIEM with security orchestration enables organizations to respond to threats at machine speed, significantly reducing the time between threat detection and containment. This automated response capability is particularly valuable for addressing high-volume, low-sophistication attacks while freeing security analysts to focus on more complex threats.
Reporting and compliance management
SIEM provides detailed reporting capabilities and audit logging features, helping organizations understand their security posture and comply with regulatory requirements such as PCI DSS, HIPAA, SOX, and GDPR. SIEM’s forensic capabilities allow security teams to conduct thorough investigations by analyzing historical data and identifying the root cause of incidents in the event of a security breach.
Compliance reporting features automate the generation of reports required by various regulatory frameworks, reducing the administrative burden on security teams while ensuring consistent compliance documentation. This capability is particularly valuable for organizations in highly regulated industries where demonstrating continuous monitoring and compliance is essential.
Top 7 benefits of SIEM
Security Information and Event Management (SIEM) systems offer powerful tools for monitoring, detecting, and responding to cyber threats in real time. In this section, we’ll explore SIEM’s top seven benefits and how they help organizations strengthen their overall security posture.
1. Enhanced threat detection and threat protection
SIEM’s ability to correlate data from multiple sources significantly enhances threat detection capabilities. It can identify complex attack patterns that might go unnoticed by traditional security tools, including sophisticated threats that leverage multiple attack vectors simultaneously.
Integrating threat intelligence feeds from external sources further enhances detection capabilities by providing context about known malicious indicators and emerging threat patterns. This intelligence-driven approach enables organizations to defend against both known and unknown threats proactively.
2. Improved incident response and threat hunting
With real-time alerts and automated response mechanisms, SIEM reduces the time it takes to detect and respond to security incidents. This quick response can significantly mitigate the potential damage caused by cyber threats. Additionally, SIEM platforms provide security analysts with the tools needed for proactive threat hunting, enabling them to search for hidden threats within their environment.
The platform’s comprehensive logging and correlation capabilities make it easier for security teams to investigate incidents, understand attack methodologies, and implement appropriate countermeasures. This improved incident response capability is crucial for maintaining business continuity and minimizing the impact of security breaches.
3. Regulatory compliance and audit support
Many industries are subject to stringent regulatory requirements regarding data protection and privacy. SIEM helps organizations comply with these regulations by providing detailed logs, reports, and audit trails.
The automated compliance reporting features save significant time and resources while ensuring consistency in compliance documentation. This capability is particularly valuable for organizations that must regularly demonstrate their security controls to auditors and regulatory bodies.
4. Comprehensive visibility across hybrid environments
SIEM offers a holistic view of an organization’s IT environment, including on-premises infrastructure, cloud environments, and hybrid deployments. This comprehensive visibility is crucial for identifying vulnerabilities, understanding the security landscape, and making informed security investment decisions.
Cloud SIEM capabilities have become increasingly important as organizations migrate to cloud platforms and adopt hybrid architectures. Modern SIEM solutions can seamlessly integrate data from cloud services, providing unified visibility across complex, distributed environments.
5. Cost efficiency and resource optimization
By centralizing and automating many security processes, SIEM can reduce the need for manual intervention and streamline security operations. This efficiency can lead to significant cost savings in the long run by optimizing staff expertise utilization and reducing the time spent on routine security tasks.
For organizations lacking sufficient internal security expertise, managed SIEM services provide access to advanced security capabilities without the need to build extensive in-house teams. This approach can be particularly cost-effective for smaller organizations or those with limited security budgets.
6. Advanced analytics and behavioral detection
Modern SIEM platforms incorporate behavioral analytics and User and Entity Behavior Analytics (UEBA) capabilities that go beyond traditional signature-based detection. These advanced analytics can identify subtle anomalies in user behavior, network traffic, and system performance that may indicate compromise.
Behavioral analytics help reduce false positives while improving the detection of insider threats, compromised accounts, and advanced persistent threats that traditional security controls might miss. This capability is essential for detecting sophisticated attacks that blend in with normal network activity.
7. Integration with Extended Detection and Response (XDR)
Leading SIEM platforms now integrate with XDR and Endpoint Detection and Response (EDR) solutions, creating a more comprehensive security ecosystem. This integration provides deeper visibility into endpoint activities and enables a coordinated response across multiple security layers.
Combining SIEM with XDR/EDR technologies creates a more effective defense strategy, as security teams can correlate endpoint data with network and application intelligence to gain a complete picture of potential threats.
Why SIEM is essential in today’s threat landscape
As cyber threats become more sophisticated, the need for robust security measures is more critical than ever. Traditional security tools often operate in silos, lacking the integration necessary to detect advanced threats that span multiple systems and attack vectors. SIEM bridges this gap by providing a unified platform that collects, analyzes, and responds to security data across the organization.
The increasing reliance on cloud services, remote work, and IoT devices expands the attack surface, making comprehensive security monitoring indispensable. Modern threat actors employ sophisticated techniques, including social engineering, advanced malware, and multi-stage attacks that require the kind of comprehensive visibility that only SIEM can provide.
Moreover, the growing complexity of regulatory requirements demands sophisticated compliance management capabilities. Organizations must protect their assets and demonstrate their security controls through detailed audit logging and compliance reporting. SIEM platforms provide the documentation and reporting capabilities to meet these evolving requirements.
Threat intelligence integration into SIEM platforms has become increasingly crucial as threat actors share tactics, techniques, and procedures across different campaigns. By incorporating external threat intelligence feeds and implementing proactive defenses, organizations can stay ahead of emerging threats.
Implementation considerations and best practices
Before implementing SIEM, organizations should evaluate their existing security infrastructure and actual needs. Many already possess monitoring capabilities that may address immediate requirements without SIEM complexity.
Do you actually need a standalone SIEM?
Modern organizations often have significant monitoring coverage through existing tools like EDR, IAM systems, CASB, WAF/API gateways, and firewall IDS/IPS. These tools are primarily preventative rather than reactive, potentially offering better security value than SIEM alone.
For organizations lacking internal security expertise, Managed Detection and Response (MDR) services may provide better value than standalone SIEMs. They combine technology with skilled analysts while satisfying compliance requirements for centralized monitoring.
Essential planning considerations
Scope and requirements: Assess your data volumes, retention needs, and primary use cases (real-time alerting, compliance reporting, threat hunting). Cloud SIEM pricing is often based on data ingestion, making volume planning crucial for budget management.
Organizational readiness: Consider your team’s expertise with different platforms and integration complexity with existing systems.
Ongoing operational requirements
SIEM deployment requires continuous tuning to reduce false positives, develop custom detection rules, and optimize costs through data parsing tools and retention policies. Without proper ongoing maintenance, teams become overwhelmed with irrelevant alerts, defeating the platform’s purpose.
These considerations are fundamental to achieving full value from your SIEM investment and ensuring long-term success in threat detection capabilities.
The future of SIEM
The SIEM landscape continues to evolve with emerging technologies and changing threat landscapes. Key trends shaping the future of SIEM include:
- Cloud-native SIEM: As organizations migrate to cloud environments, cloud-native SIEM solutions offer better scalability and reduced infrastructure overhead.
- AI and machine learning integration: Advanced analytics capabilities are becoming standard features, enabling more sophisticated threat detection and reduced false positives.
- Security orchestration integration: The integration of SIEM with SOAR platforms is creating more automated and efficient security operations.
- Extended detection and response: The convergence of SIEM with XDR technologies is providing more comprehensive threat visibility and response capabilities.
These technological advancements are transforming SIEM from a reactive logging platform into a proactive, intelligent security nerve center that can anticipate and respond to threats before they cause significant damage.
Final thoughts
SIEM is undoubtedly a cornerstone of modern cybersecurity strategies. Its capabilities in data aggregation, correlation, real-time monitoring, and incident response provide organizations with the tools they need to defend against an ever-growing array of cyber threats. By enhancing threat detection, improving incident response, and ensuring regulatory compliance, SIEM systems are not just beneficial, but also essential for maintaining robust security in today’s digital world.
Organizations that invest in properly implemented and maintained SIEM solutions, whether through internal resources or managed services, are better equipped to protect their data, maintain trust, and navigate the complexities of the modern cybersecurity landscape. As threats continue to evolve and regulatory requirements become more stringent, SIEM will remain a critical component of enterprise security architecture.
The key to successful SIEM implementation lies in understanding your organization’s specific needs, ensuring proper integration with existing security systems, and maintaining the platform through ongoing tuning and optimization. With the right approach, SIEM can transform your organization’s security posture from reactive to proactive, enabling you to stay ahead of emerging threats while efficiently meeting compliance requirements.


Request a demo
Unsure if your organization needs a full SIEM deployment? SecurityScorecard's security experts can help assess your current security infrastructure and recommend the most effective approach.
Free Account Trial




