Infosys McCamish Systems Third-Party Breach: Possible Attack Vectors and Infrastructure
In response to the identification of Infosys McCamish Systems (IMS) as the point of origin for a third-party data breach claimed by the LockBit ransomware group, SecurityScorecard researchers reviewed findings on the security hygiene of IMS. Our investigation identified attack vectors that the perpetrators could have used in a November 2023 compromise of IMS that the company disclosed. NetFlow data further identified possible malicious traffic directed at IMS in the weeks leading up to the incident. LockBit operators claimed responsibility for it and threatened to sell compromised data.
Previous security hygiene findings about IMS
SecurityScorecard data collections identified 23 possibly compromised IMS credentials and open SSH ports at 16 IP addresses belonging to Infosys BPM (of which IMS is a part). Compromised credentials are a common way for threat actors to gain access to targets. Open ports provide threat actors with attack surface to exploit with brute force, credential stuffing, and other malicious tactics. Analysis of October-November 2023 NetFlow data indicated that 68 IP addresses identified as malicious on VirusTotal communicated with port 22 – the usual SSH port – on those 16 Infosys BPM IP addresses 153 times. It is unclear if this suspicious activity was scanning, compromised credential testing, or other malicious functions.
Further NetFlow data analysis indicated that those 16 Infosys BPM IP addresses communicated 182 times with 51 suspicious IP addresses attributed to the TOR network, VPNs, and proxy services. Threat actors often use such infrastructure to provide anonymity for their attacks.
One of these 51 IP addresses in particular (45.115.113[.]94) communicated more frequently with Infosys BPM infrastructure than the others, possibly indicating ongoing attacker access to the target. SecurityScorecard’s Attack Surface Intelligence (ASI) module indicates that this IP address previously suffered a compromise enabling threat actors to route traffic through it. ASI further suggests that a MikroTik router was in use at that IP address. Threat actors often use compromised routers as proxies in attacks on other targets. Misconfigurations and unpatched vulnerabilities in router firmware often remain in place for extended periods of time, allowing attackers to compromise them and then route malicious traffic through them.
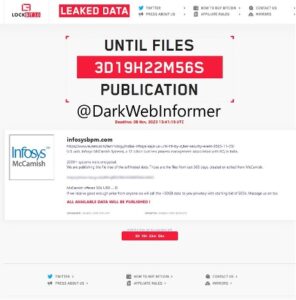 Image: The LockBit ransomware group claimed an attack against Infosys McCamish in November 2023 (Source: https://twitter.com/DarkWebInformer/status/1720868655037120602)
Image: The LockBit ransomware group claimed an attack against Infosys McCamish in November 2023 (Source: https://twitter.com/DarkWebInformer/status/1720868655037120602)
The importance of vetting vendors
Our above findings illustrate both the importance of vetting vendors and the means by which SecurityScorecard enables customers to do so. Technology and software vendors in particular should be a high priority for third-party risk management (TPRM) programs, as three-quarters of third-party breaches originate with them, according to the latest SecurityScorecard research. The above findings about the security hygiene of IMS are also examples of the ways in which our platform can enable customers to hold their vendors accountable for their security practices by highlighting significant and preventable risks. Pointing out security issues like compromised credentials or open ports helps to keep everyone safer, including both the vendor itself and its customers that might otherwise suffer the consequences of a third-party breach.





