The Forrester Wave™: Cybersecurity Risk Ratings Platforms, Q2 2024
Compliance, collaboration, and communication: The benefits of NIST CSF 2.0
As regulatory mandates and frameworks continue to emerge, cybersecurity leaders must continue to adapt to more than just the latest threat actor tactics, techniques, and procedures. As part of our ongoing webinar series centered on compliance, SecurityScorecard’s Senior Product Marketing Manager, Devaney Devoe, moderated a discussion with Adam Bixler (Principal, Squadra Ventures), Christopher Strand (SecurityScorecard’s Global Risk Officer), and Steve Cobb (CISO, SecurityScorecard). The panel dissected the latest updates for NIST CSF 2.0, focusing on the importance of the revised framework, how it can facilitate collaboration across teams, and how security practitioners can use it strategically.
In 2014, the National Institute of Standards and Technology (NIST) released its Cybersecurity Framework (CSF) following a presidential executive order to help organizations better understand, reduce, and communicate cybersecurity risk. As a result, NIST CSF has become one of the most widely recognized and utilized frameworks globally, built upon five key functions: Identify, Protect, Detect, Respond, and Recover.Ten years later, NIST has now released Version 2.0 of its CSF. The new NIST CSF 2.0 empowers cybersecurity leaders to proactively address evolving threats and safeguard their organization’s assets, operations, and reputation.
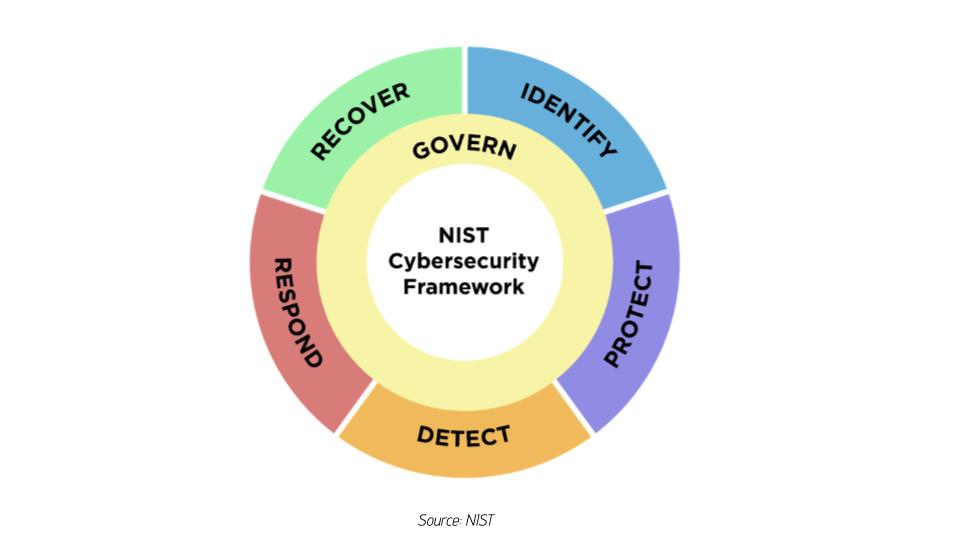
The importance of NIST CSF
According to Strand, NIST has meant a lot to the cybersecurity community because of the steep rise in cybersecurity incidents in the last decade. Before its introduction in 2014, the world lacked a common language or framework in cybersecurity — specifically for critical infrastructure, let alone more broadly. After NIST CSF was implemented, there was a default mechanism in place for the audit and GRC communities to refer back to. In other words, a global, unified framework could now be used to audit cyber posture for organizations.
Fast forward to February of this year, when NIST 2.0 was unveiled. Whereas the original version of the NIST CSF incorporated five key functions, version 2.0 has a new function: Govern. This is a strategic position for the framework, and it emphasizes the growing importance of governance and compliance in cybersecurity.
Strand says this new governance category will bring a wider swath of a business and its management levels into the cybersecurity policy role who will be more responsible to answer on the company’s enterprise risk management posture. This is in line with other recent regulations, specifically from the Securities and Exchange Commission (SEC), which mandates disclosure and analysis of the security leadership function, its roles, and responsibilities, as well as its components as a mandatory function in the wake of a security incident. Additionally, the EU’s Digital Operational Resilience Act (DORA) mandates banks, financial entities, and select third-party providers adopt robust cybersecurity measures to reinforce the EU’s financial system against the risks posed by digital technologies. And France’s new cyberscore law will require Internet-facing platform companies to disclose “report cards” on cyber resiliency based on third-party audits of systems and processes.
In Strand’s view, NIST 2.0 also gives CISOs a way to further justify the ROI of cybersecurity budgets if they can map solutions and tools to a framework that’s becoming industry-standard.
“We’ll come out with better, more mature organizations. And at the end of the day, that helps all of us.”
–Steve Cobb
The CISO’s perspective on NIST 2.0
While Cobb is a proponent of the NIST CSF 2.0, he did note that CISOs and security practitioners may have a tempered response to this framework, or any new framework for that matter. The reason? Any new framework or policy usually brings with it more effort, more budget requirements, and more discussions and with executives. All of these considerations require more planning and effort on the part of the CISO. That said, Cobb agrees with Strand that NIST 2.0 will produce better outcomes: “We’ll come out with better, more mature organizations. And at the end of the day, that helps all of us.”
Cobb also pointed out that even though CISOs are the tip of the accountability spear for the organization, it’s still key for everyone in an organization to understand their role in implementing new cybersecurity solutions, processes, and procedures. Organizations must prove that they have the proper documentation, monitoring, and reporting. This all takes more effort from a broader cross-section of a company—from finance, HR, legal, and beyond—not just a single person.
“Are we going to align with industry standards and become mature, or are we going to continue to have reactive-based solutions in our cybersecurity program where we’re really just kind of playing whack-a-mole?”
–Steve Cobb
Cobb echoed Strand’s earlier point about ROI, especially because CISOs must continually prove the ROI of their cyber budgets to the C-Suite and the Board. As he put it: “Ensuring that your organization matures and aligns with industry standards is a much better solution than having a reactive-based program where you play whack-a-mole.”
Risk management with NIST 2.0
The introduction of the governance section in NIST 2.0 is really focused on how organizations plan to manage and measure risk, and what their cybersecurity policies look like.
More specifically, the update to NIST also includes:
- The addition of cleaner language for a broader set of users.
- New, refined categories and subcategories to address the measurement of controls using a risk-based approach.
- Integration of data privacy throughout the sections.
- Help and guidance within other areas of the enterprise that haven’t had focus or scrutiny in the past version of the framework. It goes beyond critical infrastructure and includes recognition of the management and governance component of business as a player in security policy and maintenance.
A bonus to NIST 2.0’s governance function means increased collaboration between compliance professionals and cybersecurity practitioners. In Strand’s view, this framework provides a roadmap based on measuring risk and measuring cybersecurity posture that gives shared nomenclature for cybersecurity professionals, auditors, assessors, and CISOs to start speaking the same language.
“This framework provides a roadmap based on measuring risk and measuring cybersecurity posture that gives shared nomenclature for cybersecurity professionals, auditors, assessors, and CISOs to start speaking the same language.”
-Chris Strand
Cobb added that there’s usually too much isolation between SecOps and GRC teams, which creates different objectives for teams when they should all be collaborating and marching towards the same goal. A new framework such as NIST 2.0 will help to spur more collaboration across teams, as well as create a common goal.
How NIST 2.0 is driving the conversation
Bixler also noted that cybersecurity frameworks like NIST 2.0 are helpful in driving conversations about risk. As someone who works with many companies supporting various government entities with volumes of sensitive information and valuable technology stacks, he sees firsthand that risk needs to be prioritized. He always tries to break risk down into a very simple equation: “It’s threat times vulnerability—what are the threats that you need to worry about and what exposures do you have that could be capitalized upon?” It would be a competitive advantage for some nation states if certain technologies were to be stolen.
“It’s not to say that we’re going to remove all risk. It’s just a way to inventory and understand which risks need the most attention.”
–Adam Bixler
Bixler added, “It’s not to say that we’re going to remove all risk. It’s just a way to inventory and understand which risks need the most attention, which ones are the most likely, which ones we do not need to worry about, which ones are we going to manage internally, and which ones are we going to outsource. Having the CSF in place allows us to have that common language.” Having the NIST CSF as the backdrop allows Bixler to have that base conversation to ensure that an organization’s risk posture is properly assessed.
Playing the long game
Cobb made it clear that implementing NIST 2.0—as with any framework—should not be a one-time discussion that you have with executives and then never talk about it again. This is something that CISOs need to look at as part of their strategic roadmap over the next 18-24 months.
Cobb also mentioned that CISOs would be wise to use tools that help with their roadmap; SecurityScorecard has one that can help match the controls they have in place to where they need to be. He went on to say, “Maybe you can’t get completely done or completely to 100% on some of those controls in a short timeframe, but you can at least track it and you can show ROI to executives that we are getting better and we are getting more mature.”
“…at Scorecard, we’re supporting SEC, this NIST CSF 2.0, DORA. So if you have a strong partner who is supporting you in these efforts, it really goes beyond just what we’re talking about today. It’s staying compliant and future-proofing yourself for future frameworks and mandates as well.”
–Devaney Devoe
Devoe pointed out that staying compliant with NIST, as well as other cyber regulations, can be an effective way to help future-proof your organization. Sheexpanded on that by saying, “I know at Scorecard, we’re supporting SEC, this NIST CSF 2.0, DORA. So if you have a strong partner who is supporting you in these efforts, it really goes beyond just what we’re talking about today. It’s staying compliant and future-proofing yourself for future frameworks and mandates as well.”
The panel agreed that being proactive about cybersecurity is a great way to show auditors, vendors, assessors, and more that your organization can be trusted. Cobb noted that SecurityScorecard’s focus on threat intelligence and professional services are key to helping businesses of all sizes combat third-party risk and zero day threats in their supply chain ecosystems.
Partnering with someone who can act as an extension of your security team can alleviate a lot of the burden when it comes to complying with new and/or updated security frameworks. Many organizations are not equipped to operationalize their supply chain cyber risk programs on their own. SecurityScorecard’s MAX significantly lowers the overall cost of managing vendors and business partners and allows customers to dramatically expand the number of vendors they monitor, further reducing risk while improving compliance with key regulation mandates. When SecurityScorecard resolves a critical cybersecurity issue, it is resolved for the entire ecosystem, demonstrating the power of collective defense.




