Complete Third-Party Risk Management (TPRM) Guide for 2025
Third-party risk management (TPRM) is the structured process of identifying, assessing, and mitigating cybersecurity risks posed by external vendors, suppliers, and service providers. These risks can include cyber threats, data breaches, regulatory violations, and financial instability, all of which can severely impact your organization’s security and compliance posture.
Managing third-party risks allows businesses to reduce vulnerabilities from external partners and gain critical visibility into vendor relationships across the vendor lifecycle. With real-time, high-quality data, they can actively monitor these connections, safeguard sensitive information, maintain operational continuity, and ensure regulatory compliance.
This guide dives into what TPRM is, why it’s essential for safeguarding your business, and how you can implement a strong TPRM strategy. You’ll learn to evaluate vendors, assess their level of risk, and maintain continuous risk monitoring to stay ahead of potential threats.
Built on the expertise of SecurityScorecard’s global experts, this guide will help you navigate the growing complexities of third-party risk in 2025. We’re here to help ensure your organization remains secure and compliant in an interconnected world.
Key Takeaways
- Third-party risk management (TPRM) actively shields your organization from cyber threats and operational breakdowns. It identifies weak links in your vendor network, helping you build a strategy that directly tackles these vulnerabilities. A focus on risk posture ensures that vendors are continually meeting the standards your organization requires.
- Effective TPRM requires constant vigilance, from upfront third-party risk assessment to continuous risk monitoring of vendors in real time and securely offboarding them. Each step demands a structured approach to prevent gaps that attackers could exploit.
- Leveraging AI and real-time monitoring tools transforms your vendor risk management program. These tools provide insights and alert you to risks before they spiral into a full-blown crisis. SecurityScorecard MAX, with its continuous monitoring, ensures you’re not caught off guard by shifts in risk scores that might indicate new vulnerabilities.
- Strengthening your TPRM fortifies your supply chain, data security, and reputation. By adopting these practices, you’ll actively boost your overall security posture, ensuring your organization stays ahead of threats.
What is Third-Party Risk Management?
Third-party risk management (TPRM) is the structured process of identifying, assessing, and managing the risks introduced by external vendors and suppliers. In today’s business environment, where outsourcing is routine, TPRM is vital for organizations to maintain security, compliance, and operational stability.
This isn’t just about managing vendors; TPRM is a holistic strategy to protect your organization’s cybersecurity. The process involves identifying risks, conducting third-party risk assessments, applying mitigation strategies, and continuously monitoring third parties. A well-executed TPRM plan minimizes the likelihood of third-party breaches, safeguarding your data and systems while keeping tabs on critical vendors.
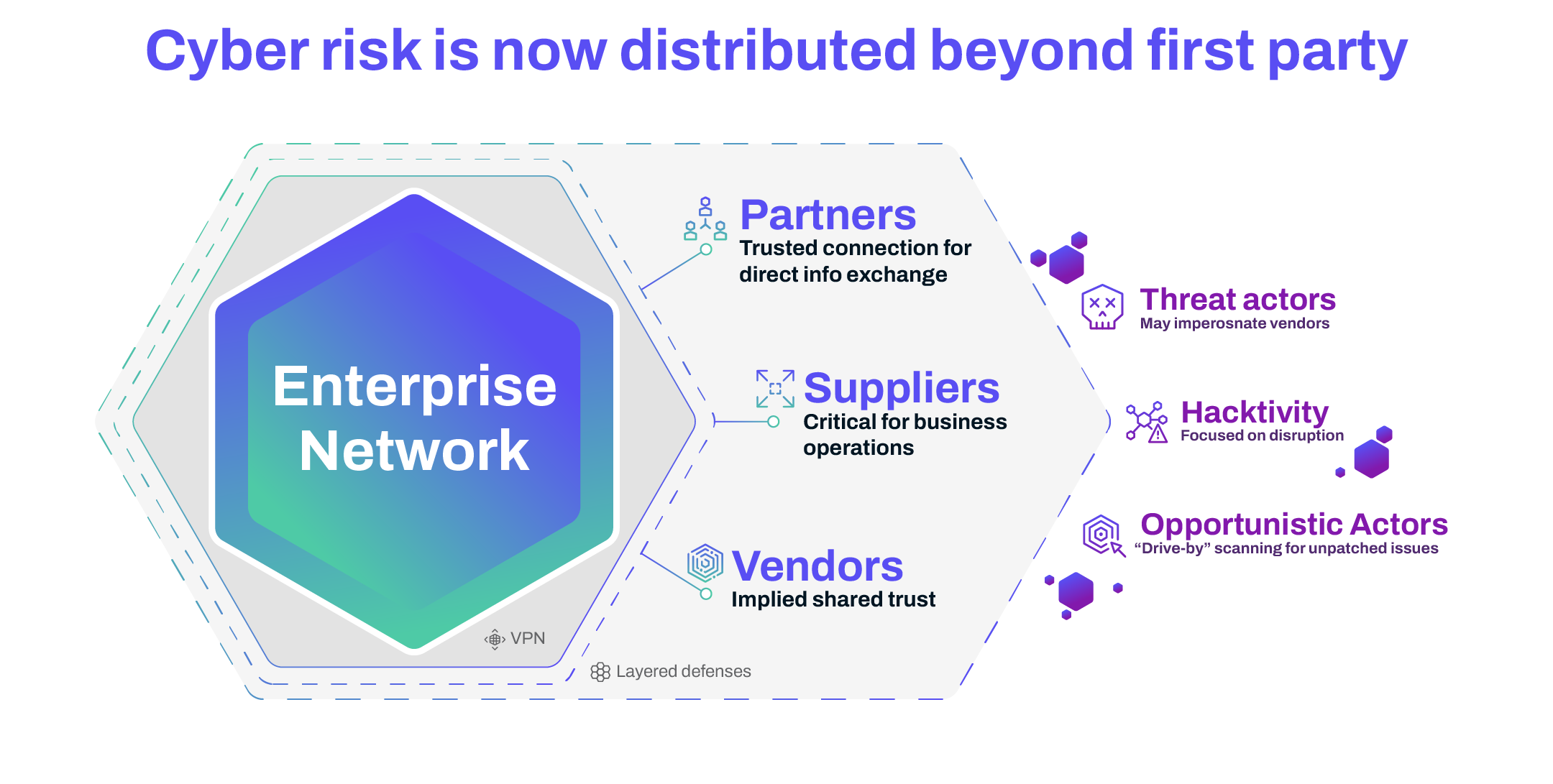
Vendors and service providers are crucial to modern business operations, but they also bring digital risks, such as data breaches and compliance failures. With the growing complexity of these risks, a well-defined third-party risk management process will be more important than ever in 2025.
The Foundation of Third-Party Risk Management
Third-party risk management (TPRM) is essential to any comprehensive risk management strategy. It revolves around identifying, assessing, and reducing risks linked to third-party vendors and service providers.
The purpose is to protect your reputation, financial health, and sensitive data from potential threats within these external relationships.
In an interconnected business ecosystem, reliance on third-party vendors has grown significantly. However, this dependence brings new strategic risks, such as cybersecurity breaches, data leaks, and operational failures. A structured third-party risk management program helps mitigate these risks by ensuring that vendors meet the same security and compliance standards as your organization.
The key components of a successful TPRM program include:
- Third-Party Identification: Identifying all third-party vendors and service providers that interact with the organization.
- Risk Assessment: Assessing the level of risks associated with each third-party vendor, including their risk posture, data handling practices, and compliance with regulatory requirements.
- Risk Mitigation: Implementing controls and measures to mitigate identified risks, such as contractual agreements, security audits, and ongoing monitoring.
- Ongoing Monitoring: Continuously monitoring third-party vendors to ensure they remain compliant with organizational standards and regulatory requirements.
- Vendor Risk Management: Managing the risks associated with third-party vendors by using vendor risk assessment questionnaires, conducting regular risk assessments, and implementing risk mitigation strategies.
By implementing a comprehensive TPRM program, organizations can reduce the risks associated with third-party relationships, protect their reputation and sensitive data, and maintain regulatory compliance. In the following sections, we will delve deeper into the world of TPRM, exploring its importance, key components, and best practices for effective implementation.
Why Third-Party Risk Management Matters
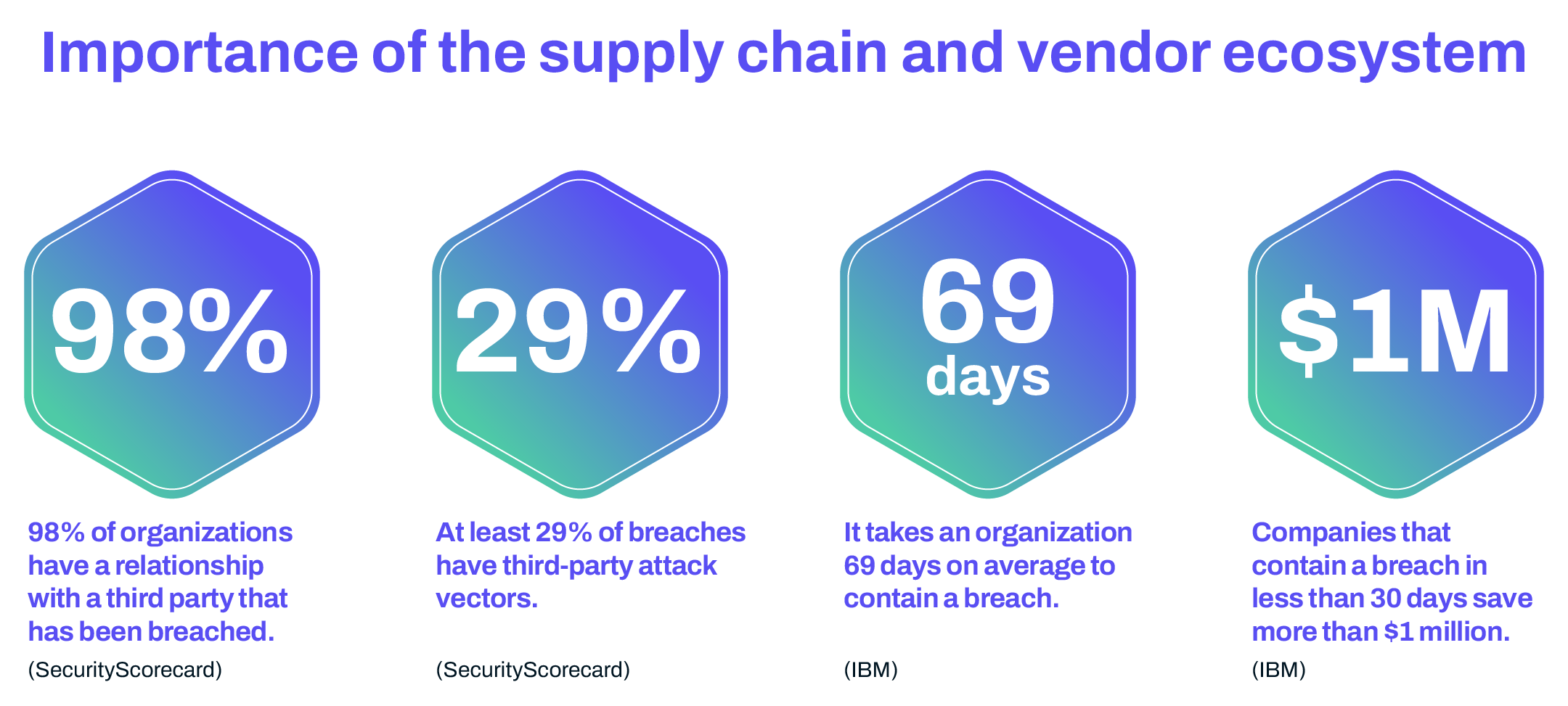
Third-party cyber risks are becoming more pervasive because attackers pursue the path of least resistance. If they encounter strong defenses within an organization, they shift to targeting third-party providers with weaker security measures. Research reveals that 29% of all data breaches originate from third-party vendors, highlighting the urgency for companies to strengthen third-party risk management practices.
Despite the growing importance of TPRM, many organizations rely on outdated methods such as self-assessment questionnaires and compliance certifications. These tools often provide a false sense of security by only offering static, point-in-time assessments.
“ We see a challenge across the industry. Third-party risk management has traditionally used frameworks to evaluate risk, and those frameworks had six, seven, or eight different pillars, and cybersecurity was one of those pillars.
Cybersecurity is now expanding, it’s a reputational risk and a financial risk. It’s starting to take over a lot of the traditional TPRM frameworks. We need to simplify the messaging. Boards need to know what our biggest risk is from a cybersecurity perspective. The problem is, we used to report that based on a point-in-time inspection, right? Whether it was NIST gap framework, cybersecurity framework assessment, ISO 27 001, or a SOC 2 assessment.
These are the common things that businesses were adjudicated on. Cybersecurity is organic. It’s fast moving. It’s fast-changing. These traditional assessment methods are not keeping up.
So Max steps in and provides not just that point-in-time assessment, but we can provide continuous monitoring at a faster pace than traditional cybersecurity ratings companies do.
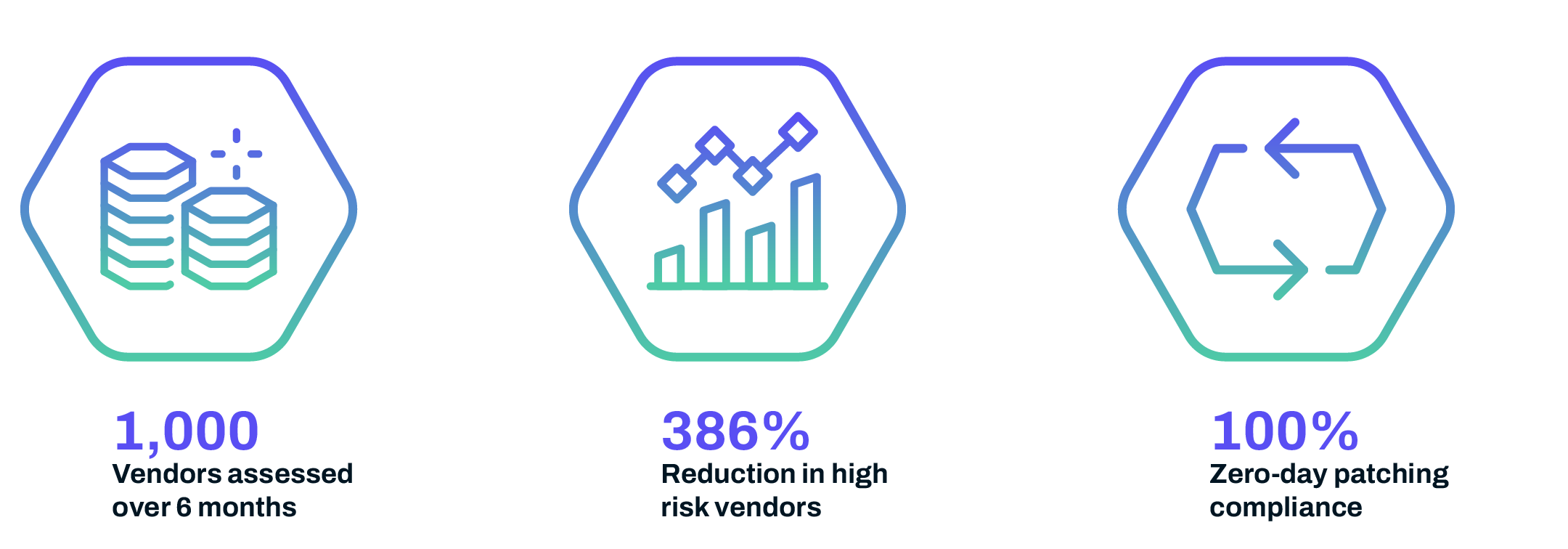
So we could provide an overview of a thousand vendors. We could provide their score. We could provide a low, medium, high criticality of chance of breach and give a nice chart with green, yellow, and red that lets boards quickly identify which of our vendors we should be most worried about?” – Larry Slusser, global vice president of Cyber Risk Solutions for SecurityScorecard
Cautionary Third-Party Risk Tales
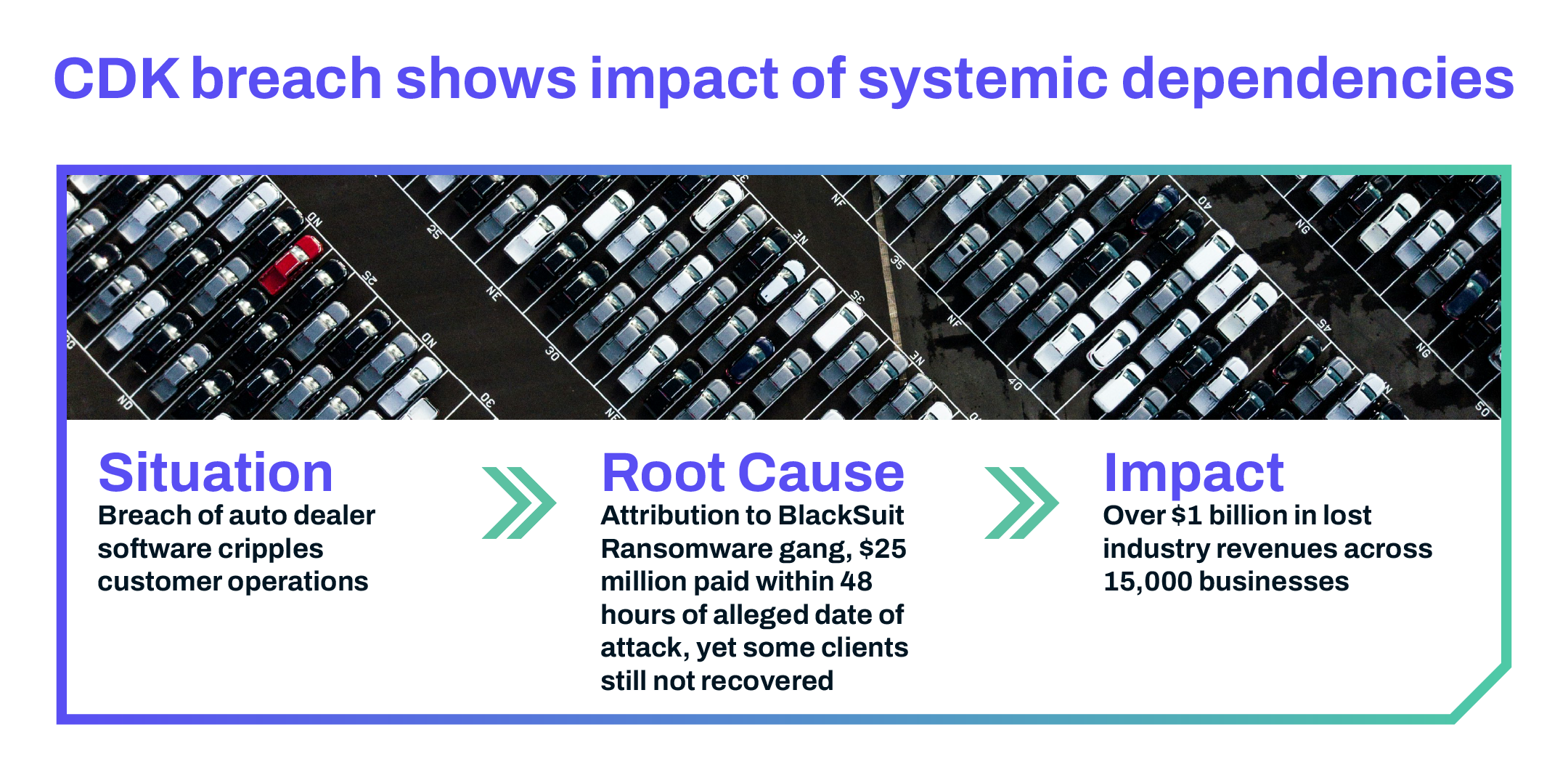
The CDK Global ransomware attack didn’t just cause a blip—it took down 15,000 automotive dealerships. A single vendor’s security failure froze operations and rippled across the entire supply chain. This is what happens when businesses rely on third parties without actively managing their risks. CDK might have been the initial target, but the damage spread far and wide, showing how one weak link can take the whole system down.
Then there was the MOVEit zero-day vulnerability in 2023. Hackers exploited a hidden flaw in a widely used file transfer tool, leading to massive data breaches across multiple organizations.
This attack exposed a harsh truth: your biggest vulnerability may not be within your own network but hidden in the software of your vendors. One overlooked flaw became a massive security breach for countless businesses.
These incidents are increasing and are clear reminders that if your third-party risk management stops after onboarding, you’re not ready.
Continuous monitoring and real-time responses are now essential. If you’re not staying on top of vendor security, you’re just waiting for the next cyber disaster to hit.
Understanding the Lifecycle of TPRM
The TPRM lifecycle begins with recognizing potential risks and continues through continuous monitoring. External vendors can range from material suppliers to service providers. They may have access to sensitive data, making your organization vulnerable to financial, reputational, and security risks.
The ever-evolving nature of cyber threats and tightening regulations increases the need for strong TPRM practices. Identifying and addressing vulnerabilities is essential to minimizing third-party risks.
Conducting thorough risk assessments, adopting protective measures, and maintaining ongoing supervision ensures your company remains secure against vendor-related breaches.
A well-structured TPRM strategy fosters accountability and resilience, ensuring that all parties understand their responsibilities in managing these risks.
Key Components of a Third-Party Risk Management Program
A strong third-party risk management (TPRM) program includes several crucial elements: risk assessment, due diligence and vendor selection, contract management, ongoing monitoring, and offboarding. Each part works together to manage risks from external vendors, ensuring security, compliance, and operational integrity.
Risk Assessment
Risk assessment forms the foundation of a successful TPRM strategy. It begins with a thorough review of third-party vendors to understand their practices and assess risk scores for their impact on operations. You’ll want to look at financial and strategic vulnerabilities, the vendor’s role in your operations, and their ability to manage those risks.
A risk profile should align with your organization’s risk appetite, so you can evaluate whether their practices meet your standards.
An accurate vendor inventory is key here. Catalog all your third-party partners and update this regularly. This practice helps you stay on top of risks as they change over time.
Classifying vendors by risk level allows you to focus resources where they’re needed most. Incorporating technology into this process enhances data analysis, enabling faster and more accurate risk identification.
Due Diligence and Vendor Selection
Selecting the right vendors requires due diligence. This means reviewing each vendor’s risk posture, business continuity plans, and governance structures. Detailed questionnaires help assess whether their operations align with compliance standards and security requirements. Critical factors to evaluate include industry standards, security policies, and the vendor’s specific role in your organization.
Criticality ratings can streamline vendor selection. By prioritizing vendors based on their importance, you can focus on those that have the most significant impact on your business.
Contract Management
Effective contract management is a safeguard in TPRM. Contracts should include clear service level agreements (SLAs) and terms covering security obligations and regulatory compliance.
These agreements set expectations for vendor performance and help protect your organization from unexpected risks. Pay attention to critical clauses—especially those that outline compliance, data protection, and risk mitigation responsibilities.
By defining these expectations upfront, you gain more control over your third-party relationships and ensure that vendors remain accountable for their performance.
Ongoing Monitoring
Managing third-party risks doesn’t end after the contract is signed. Continuous risk monitoring is crucial for maintaining compliance and detecting emerging risks.
Automation and real-time monitoring tools make it easier to track changes in a vendor’s security profile. These tools alert you to potential vulnerabilities as they arise, enabling swift action.
Continuous Security Monitoring (CSM) tools provide automated oversight, reducing the manual work required to keep tabs on vendor security and compliance. This ongoing process ensures that you stay ahead of potential issues before they escalate into larger problems.
Offboarding
Offboarding vendors securely is as important as onboarding them. When a third-party relationship ends, ensure all access privileges are revoked, and any company assets are returned.
This step closes potential security gaps and prevents lingering access that could be exploited later. Proper offboarding protects your organization from risks associated with former partners who no longer need access to sensitive systems or data.
Common Types of Third-Party Risks
A well-rounded third-party risk management (TPRM) strategy evaluates risks that primarily stem from cybersecurity threats. These include operational risks like service disruptions from cyberattacks, reputational damage due to vendor breaches, financial risks from hacking incidents, and compliance failures tied to security lapses.
Understanding how these cyber risks can impact your organization is crucial for developing a plan that effectively mitigates threats and protects your business.
Operational Risk
Operational risks arise when third-party disruptions impact your business. These could be anything from service outages to supply chain delays. If a critical service provider goes down, your business could face costly downtime and missed deadlines.
To prevent this, it’s important to evaluate a vendor’s operational resilience before engagement.
Reputational Risk
Reputational risk is when a vendor’s actions harm your company’s image. Whether it’s a data breach or unethical business practices, these incidents can destroy customer trust.
Monitoring vendors regularly and ensuring they align with your company’s values is crucial. A damaged reputation can take years to rebuild, so preventing it should be a priority.
Financial Risk
Financial risk refers to the possibility that a vendor might fail to meet its financial obligations, leading to direct losses for your business. If a vendor can’t deliver, you could face revenue drops, legal fees, or fines.
Properly vetting a vendor’s financial stability upfront and tracking changes over time helps protect your bottom line.
Compliance Risk
Compliance risk emerges when a third-party fails to meet industry regulations, which can lead to legal penalties for your organization. Keeping up with regulatory requirements and regularly assessing your vendors ensures you stay in the clear. Regulations shift, so staying informed and proactive with compliance monitoring is key.
Each type of risk requires a clear strategy, but they are all connected. Building a TPRM plan that addresses these risks helps protect your organization from both predictable and unforeseen threats.
Overcoming Challenges in Implementing Third-Party Risk Management
Implementing Third-Party Risk Management (TPRM) comes with its own set of challenges. These challenges, including limited resources, communication breakdowns, and lack of visibility, can lead to significant operational, regulatory, and reputational risks. Addressing these issues is crucial to creating an effective TPRM program.
Resource Constraints
Many organizations face resource constraints when rolling out a TPRM program. Competing financial priorities and limited personnel often leave third-party risks unaddressed.
The key is showing decision-makers how investing in TPRM can prevent costly incidents. By focusing on the long-term cost savings of reducing risks, businesses can justify the investment. Not only does this help mitigate current risks, but it also prepares the organization for future challenges in vendor management.
Lack of Visibility
One of the biggest challenges in managing third-party risks is the lack of visibility into vendor activities, particularly when dealing with 4th and Nth parties—vendors beyond your direct partners.
Without a unified system, it’s difficult to track each vendor’s risk level and ensure they meet your security standards. Automated solutions can close this gap by offering real-time insights into both direct and indirect vendor performance.
These tools reduce blind spots, making it easier to catch vulnerabilities in your extended vendor network and prevent security breaches or compliance failures across your supply chain.
Communication Issues
Poor communication can derail even the best TPRM programs. If risk policies aren’t clearly communicated to vendors, confusion sets in, making it hard to manage risks effectively. Gathering responses to security questionnaires, for example, is often a slow, error-prone process.
The lack of clarity and the fragmented communication methods make tracking vendor compliance and remediation efforts more difficult than it needs to be. Streamlining communication with more efficient tools and clear expectations can smooth out this process.
Mitigating Third-Party Risks
Mitigating third-party risks focuses on applying controls that reduce the likelihood and impact of vendor-related threats.
Rather than duplicating concepts already covered under key components like contractual agreements, audits, and security measures, this section dives deeper into actionable strategies for minimizing vendor risks throughout their lifecycle.
- Contractual Safeguards: Ensure contracts clearly define security obligations, data protection protocols, and performance metrics. This reinforces accountability and establishes a legal framework for managing risks.
- Proactive Risk Assessments: Beyond initial evaluations, regularly update vendor risk profiles to capture new vulnerabilities. This step helps you stay ahead of emerging threats as the business environment evolves.
- Continuous Monitoring: Employ AI-driven tools and real-time monitoring systems to flag potential risks before they escalate. These technologies allow for immediate action, reducing your exposure to breaches or operational failures.
- Incident Response Planning: Prepare for the worst-case scenario by establishing clear communication protocols and incident response plans. This ensures quick action when issues arise, limiting damage and preserving business continuity.
By integrating these tactics, organizations can minimize disruptions, maintain compliance, and fortify their defenses against third-party risks.
The Benefits of a Proactive TPRM Program
By adopting a proactive third-party risk management approach, organizations can not only avoid the high costs of breaches but also unlock strategic benefits. Companies with strong vendor security postures benefit from:
- Lower insurance premiums: Improved cyber hygiene reduces risk exposure, leading to better insurance terms.
- Stronger vendor relationships: Transparent communication fosters trust and reduces operational friction.
- Regulatory compliance: Continuous monitoring ensures alignment with evolving cybersecurity regulations, such as the SEC’s recent disclosure requirements, and minimizes the potential impact of breaches from third-party vendors.
Third-Party Risk Management Tools and Software
Third-party risk management (TPRM) tools are critical for simplifying and automating the complex process of managing vendor risks. With the increasing reliance on external vendors, it’s essential to have the right tools in place to assess, monitor, and mitigate risks efficiently.
These TPRM tools allow organizations to maintain oversight of vendor relationships and ensure compliance with security standards.
Key Features and Functions
- Risk Assessment and Scoring: Automating the evaluation process ensures that vendors are accurately assessed based on risk factors like cybersecurity, financial stability, and compliance. This allows organizations to prioritize high-risk vendors and address concerns early.
- Vendor Onboarding and Offboarding: Automation in these areas reduces the risk of errors during the critical phases of bringing on or removing vendors. It ensures that security protocols, such as revoking access to sensitive data, are consistently followed.
- Contract Management and Compliance: Centralized contract management tracks key contract terms, renewal dates, and ensures that vendors meet compliance requirements. This feature keeps organizations on top of legal obligations and security commitments.
- Incident Response and Reporting: Tools that provide real-time alerts and detailed reporting make it easier to track and respond to vendor-related incidents. This rapid response capability is vital for minimizing damage in the event of a breach.
- Continuous Monitoring and Risk Assessment: Continuous monitoring tools offer real-time insights into the evolving risk profiles of vendors. Platforms like SecurityScorecard excel in this area, giving you the ability to act on changes in a vendor’s security posture immediately, rather than waiting for periodic reviews.
- Data Analytics and Visualization: The ability to analyze risk data and visualize it through dashboards helps organizations make data-driven decisions and communicate risks effectively to stakeholders.
Factors to Consider When Choosing TPRM Tools
- Ease of Use: Look for tools that seamlessly integrate into your existing systems and offer a user-friendly interface. The platform should be intuitive enough for both risk management teams and other stakeholders who rely on the data.
- Scalability: As your organization grows, so will the complexity of your vendor relationships. Choose a tool that can scale with your needs, accommodating more vendors and increasing regulatory demands without sacrificing performance.
- Customization Options: Every organization has unique requirements. A good TPRM tool should allow you to customize workflows, questionnaires, and reporting to fit your specific risk management process.
- Real-Time Monitoring: Continuous monitoring is crucial in today’s dynamic threat environment. Platforms like SecurityScorecard, which offer real-time updates on a vendor’s risk status, provide the advantage of immediate response to any emerging threats.
- Comprehensive Insights: Opt for a platform that not only tracks individual vendors but offers a holistic view of your entire vendor ecosystem. SecurityScorecard’s MAX service does just that, delivering comprehensive security ratings and actionable intelligence across all your third-party relationships, helping you strengthen the overall security of your supply chain.
By using platforms that offer advanced features like those from SecurityScorecard, you can enhance your TPRM processes, ensuring that risks are managed proactively rather than reactively.
A well-chosen tool will not only safeguard your organization but also improve your overall operational resilience and compliance in the face of third-party risks.
Best Practices for Effective Third-Party Risk Management
Building a strong third-party risk management (TPRM) program requires more than just setting up policies. It demands action.
To fully protect your organization, you need to rank vendors based on importance, automate processes where you can, and extend your risk considerations beyond just cybersecurity. Here’s how to start taking control.
Prioritize Vendor Inventory
First, rank your vendors. Group them by their criticality to your operations—some will be more important than others. High-risk vendors should get the most scrutiny. Begin by assessing their security posture, financial stability, and compliance track record.
From there, establish ongoing monitoring to continuously track changes in their risk profiles. This way, you can focus on vendors that pose the greatest risk and adjust your strategy as needed.
Automate Where Possible
Manual processes eat up time and leave room for error. Automation fixes that. Start by automating repeatable tasks like vendor onboarding and ongoing monitoring. Use tools that provide real-time alerts for any changes in vendor risk, allowing you to act fast. Implementing automation gradually lets you scale your TPRM efforts without overwhelming your team.
Look Beyond Cybersecurity
A good TPRM program doesn’t stop at cybersecurity. It should cover financial, operational, reputational, and compliance risks. Review each vendor’s impact on all these fronts. For example, check if they meet regulatory requirements, hold necessary certifications (like SOC 2), and perform annual reviews.
This broader focus strengthens your entire risk management framework and helps prevent issues beyond cyber threats.
Role of Internal and External Stakeholders in TPRM
Managing third-party risk is a team effort. Both internal and external stakeholders must work together to make TPRM effective.
Internal Stakeholders
Within your organization, accountability is key. Designate a specific person or team to oversee vendor relationships. This person will coordinate between departments—legal, procurement, and IT—to ensure that vendor risks are identified and addressed.
Make sure risk management is a shared responsibility across the company, with regular input from all teams involved.
External Stakeholders
Your vendors and external auditors are critical to maintaining a strong TPRM program. Engage vendors directly in the risk management process by requiring regular updates on their security and compliance practices.
Auditors should also play a key role, providing objective assessments of vendor performance. Their evaluations help identify any gaps in compliance or risk exposure, ensuring your vendors meet the required standards.
This process builds a comprehensive TPRM strategy that evolves with your business and vendor landscape, ensuring all risks are managed effectively.
The Future of Third-Party Risk Management
The future of third-party risk management (TPRM) is being shaped by the growing complexities of supply chain cybersecurity, as highlighted by SecurityScorecard’s shift towards Supply Chain Detection and Response (SCDR). This new approach addresses the evolving needs of security teams who must now act not only as risk managers but also as incident responders.
The increasing threats from third-party vendors, along with real-world examples like the Change Healthcare ransomware attack and the CrowdStrike outage, demonstrate the urgent need for more proactive and responsive TPRM strategies.
SecurityScorecard’s SCDR framework, designed to reduce vendor-related incidents by 75%, reflects the direction in which TPRM is headed.
As organizations adapt to these challenges, they must stay on top of emerging technologies and trends, which will be pivotal in managing vendor risks.
AI and Machine Learning Will Lead the Way
AI and machine learning are set to revolutionize TPRM by automating critical processes like risk assessments and vendor monitoring. These technologies can sift through large datasets, identify patterns, and predict risks before they become issues. By implementing AI-driven tools, organizations can shift from reactive to proactive risk management.
Cloud Computing Demands Stronger Security
As more businesses move their operations to the cloud, the security of cloud environments becomes a top priority. To manage third-party risks in this space, you’ll need to enforce stringent security measures that ensure your vendors comply with cloud security standards. This means monitoring vendor access and ensuring data protection protocols are always in place.
Blockchain Enhances Accountability
Blockchain technology will bring greater transparency and accountability to vendor relationships. Its ability to create immutable transaction records will make it easier for companies to track vendor activities and verify compliance. This offers a secure, verifiable way to manage third-party risks, especially in industries with high regulatory demands.
IoT Increases Risk Exposure
The growing use of Internet of Things (IoT) devices introduces new risks that need immediate attention. Each connected device creates potential vulnerabilities that attackers can exploit. Protecting IoT devices requires stronger security measures and consistent monitoring of how data flows between your organization and third-party vendors.
Data Analytics Will Sharpen Decision-Making
Advanced data analytics and visualization tools will offer deeper insights into your TPRM processes. These tools help you spot trends, assess vendor risks, and make more informed decisions. By leveraging data, you can fine-tune your risk management strategies to better anticipate future challenges.
Staying on top of these technological shifts will help you maintain an effective TPRM program, ensuring your business is prepared for the risks of tomorrow.
SecurityScorecard: Your Complete Solution for Third-Party Risk Management
Whether you want to be hands-on or prefer expert support, you have options.
Two Powerful Choices: MAX Managed Service or Self-Managed Program
SecurityScorecard offers flexibility in how you manage risks:
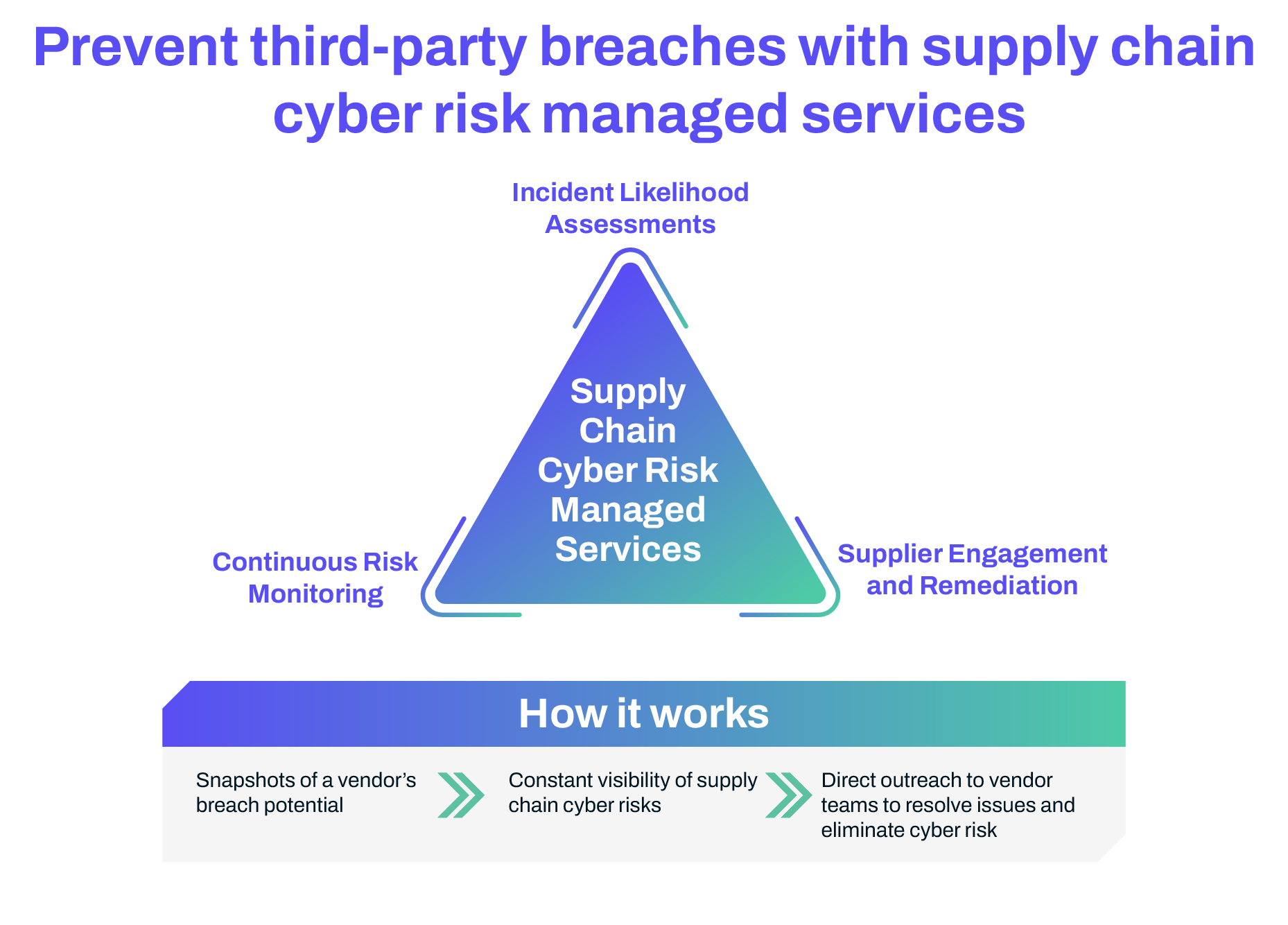
- MAX Managed Service: For those who want expert support, MAX provides 24/7 monitoring and hands-on help from SecurityScorecard’s team. With MAX, you’re not alone in managing risks—experts actively help you detect, respond, and mitigate security issues as they arise. It’s designed to reduce your workload while giving you the security insights you need in real-time.
- Self-Managed Program: If you prefer a more hands-on approach, the SecurityScorecard platform gives you all the tools and insights to handle third-party risks on your own. You get real-time scores, continuous monitoring, and the ability to work directly with your vendors on improving their security. It’s perfect for organizations that have the resources and prefer to keep the management in-house.
Why Industry Leaders Trust SecurityScorecard
Whether through MAX or the self-managed program, SecurityScorecard offers:
- 4th-Party Risk Identification: Discover hidden risks by identifying vendor relationships and uncovering 4th-party concentration that could impact your supply chain.
- Vendor Risk Assessments: Conduct comprehensive internal and external evaluations using detailed ratings and questionnaires to identify vulnerabilities early.
- Collaborative Remediation: Streamline vendor risk remediation by collaborating directly with vendors, enabling quicker resolution of potential security issues.
- Zero-Day Monitoring: MAX’s expert teams provide daily monitoring of emerging vulnerabilities, delivering real-time insights to prevent incidents like ransomware or data breaches.
- Incident Response Integration: MAX quickly identifies compromised vendors, helping organizations remediate issues and minimize the impact on business operations.
- Vendor Risk Ratings: MAX identifies critical vulnerabilities across 17 security categories, allowing you to prioritize high-risk vendors and address key issues.
The Choice is Yours
With SecurityScorecard, you decide how involved you want to be. You can lean on the MAX team for expert support or take control in-house with the regular program. Either way, you’re equipped with the tools to stay ahead of third-party risks and protect your business.
In 2024, the importance of third-party risk management (TPRM) became even more evident, with high-profile incidents such as the Change Healthcare ransomware attack and the CrowdStrike outage highlighting the vulnerabilities businesses face from their vendors. The Change Healthcare attack disrupted services across the healthcare sector, exposing the critical need for continuous vendor monitoring and stronger risk mitigation. Similarly, CrowdStrike’s faulty update bricked thousands of systems globally, showing that even the most trusted vendors can unintentionally cause massive disruptions.
These incidents reinforce the need for businesses to implement robust TPRM programs that go beyond initial risk assessments. Incorporating continuous monitoring and vendor evaluations throughout the lifecycle is essential to minimize risks and prevent significant operational outages.
By learning from cautionary tales and implementing best practices—such as using AI-driven monitoring tools and ensuring stronger disaster recovery plans—businesses can stay more secure from escalating third party risks.. This guide dives into how you can build such a strategy, leveraging key tools like continuous monitoring, as seen with SecurityScorecard’s solutions, to stay ahead of evolving threats.
Find out today why so many companies are trusting SecurityScorecard with their third-party risk management.







