New APT29 – Attributed Phishing Activity Targets Diplomatic Services
Executive Summary
- On April 13, Poland’s Computer Emergency Response Team (CERT.PL) and Military Counterintelligence Service released a group of joint advisories regarding newly-observed espionage activity attributed to a Russia-linked threat actor group.
- The activity involved the distribution of three different strains of malware, HALFRIG, QUARTERRIG, and SNOWYAMBER, through phishing targeting diplomatic personnel.
- The SecurityScorecard Threat Research, Intelligence, Knowledge, and Engagement (STRIKE) Team identified IP addresses linked to the campaign and analyzed traffic involving them to enrich the available indicators of compromise (IoCs).
- While the traffic data is inconclusive, it may reflect malware distribution to US targets.
Background
On April 13, Poland’s Computer Emergency Response Team (CERT.PL) and Military Counterintelligence Service released a group of joint advisories regarding newly-observed espionage activity they attribute to the advanced persistent threat (APT) group tracked as APT29, Nobelium, and Cozy Bear (among others), which the cybersecurity community understands to act on behalf of the Russian Foreign Intelligence Service (SVR). The activity involved three different strains of malware, each of which received its own report: HALFRIG, QUARTERRIG, and SNOWYAMBER.
SNOWYAMBER first appeared in October 2022. It is a dropper (malware that mainly serves to deliver additional malware to a target system) that uses the business collaboration tool Notion for communications and deploys Cobalt Strike and BruteRatel (legitimate but often-abused post-exploitation frameworks) as second-stage payloads. A new version, with features added in an apparent attempt to improve operational security, appeared in February 2023.
HALFRIG first appeared in February 2023. Like SNOWYAMBER, it deploys Cobalt Strike on infected systems. Unlike SNOWYAMBER, which uses its command and control (C2) communications to download its second-stage payload, HALFRIG contains encrypted shellcode for its Cobalt Strike beacon. HALFRIG’s division into four separate modules responsible for different stages of its deployment, which culminates in the fourth module’s staging of a Cobalt Strike beacon, is a key distinction between it and the single-file SNOWYAMBER and QUARTERRIG.
Analysts first observed QUARTERRIG in March 2023. Although it and HALFRIG’s code overlap, its obfuscation methods differ from HALFRIG’s: HALFRIG’s modules spawn multiple threads throughout execution as an anti-analysis measure. QUARTERRIG instead uses opaque predicates and multi-stage execution combining shellcode and PE files for its obfuscation.
Whichever strain of malware they attempted to distribute, attackers used phishing for initial access. Most of the recently-observed cases employed ENVYSCOUT, a delivery script APT29 has used since 2021, to lead to the downloads of SNOWYAMBER, QUARTERRIG, or HALFRIG.
The advisories also provided file and network indicators of compromise (IoCs) that STRIKE Team researchers used to investigate the campaign further. These included the names, hashes, and sizes of the files involved, the URLs that served downloads of the malicious files, and the Cobalt Strike C2 domains used in the campaign’s later stages.
Analytical Comment
While the later stages of these attacks took steps to avoid detection, the email samples contained in the advisories have certain inconsistencies that could have raised the alarm for attentive target employees or security personnel. While the advisories provide sample images of the messages in question, they do not explicitly highlight this feature of the activity.
The emails impersonate diplomatic correspondence, and while the emails’ signatures used addresses from the impersonated organizations, these do not correspond to the addresses in the messages’ sender fields. An email that impersonated the Spanish Ministry of Foreign Affairs and had an @maec[.]es email address in its signature actually came from sales@almaghrebar[.]com. Similarly, one that impersonated the Czech Ministry of Foreign Affairs had an @mzv[.]cz domain in its signature but an @seznam[.]cz address in its sender field.
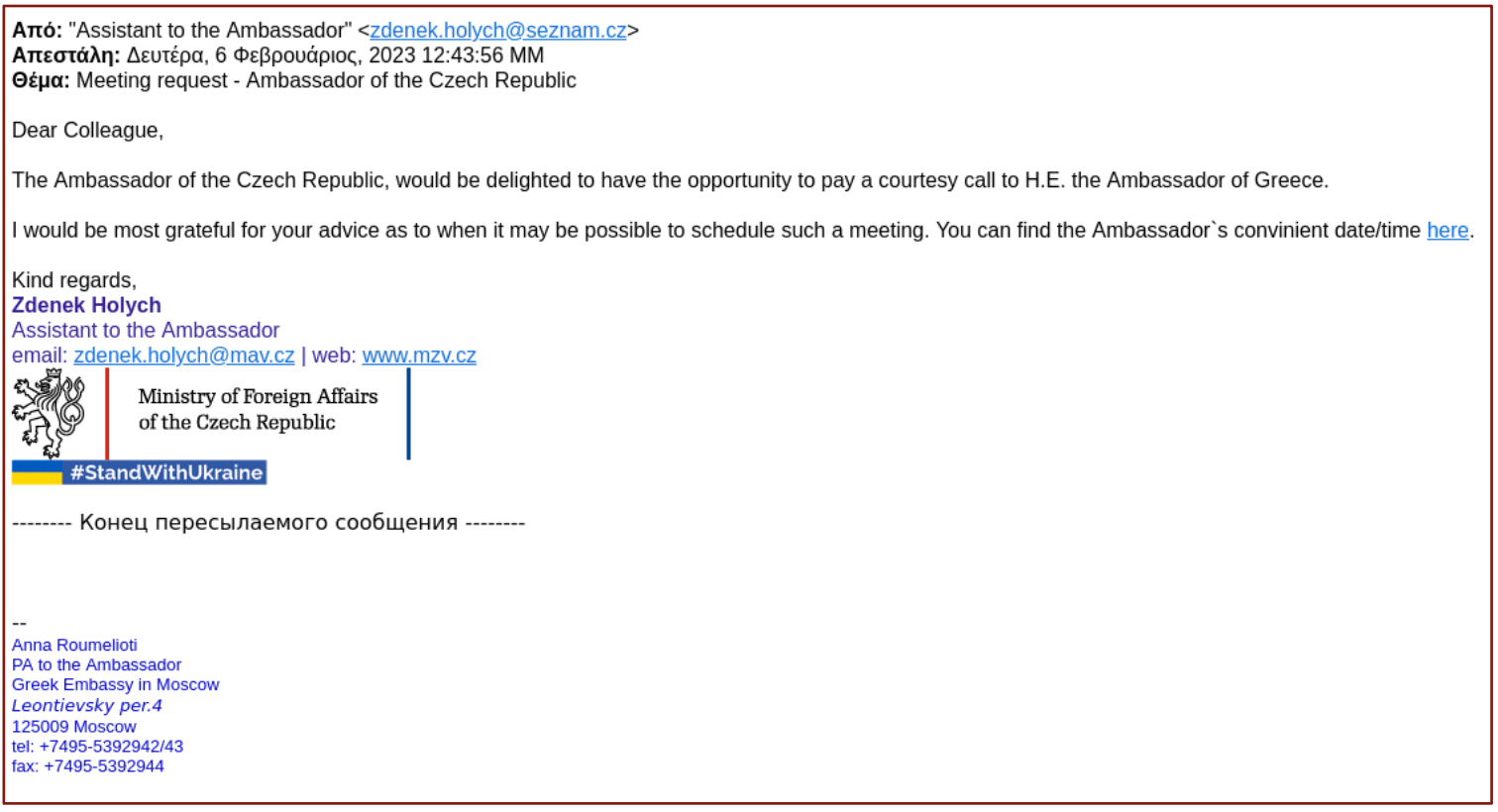
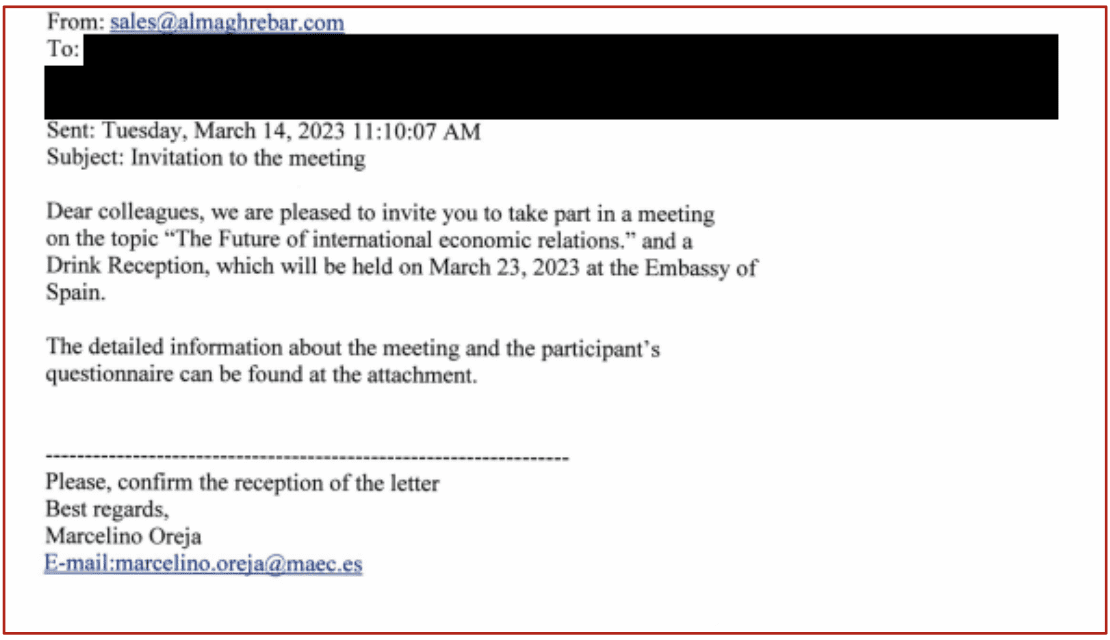
Images 1-2: Phishing emails linked to the recent activity contain errors and inconsistencies that could raise the suspicions of careful readers (Source: joint advisories regarding QUARTERRIG and SNOWYAMBER.)
Earlier phishing activity attributed to APT29 also featured fairly obvious spelling errors. For example, using ‘transfered’ rather than ‘transferred’ and ‘epideniological’ rather than ‘epidemiological’ in a 2022 lure.
Errors and inconsistencies such as these can indicate that something is amiss. Attentive, risk-aware personnel would be likely to notice them. While they may simply be unintentional errors, they could also aid in the campaign’s targeting: personnel who do not notice them may be less likely to notice other inconsistencies or unexpected behavior as a compromise progresses and could therefore represent more consistently vulnerable targets than more attentive personnel.
Traffic Analysis Methodology
Researchers leveraged SecurityScorecard’s exclusive access to network flow (NetFlow) data to identify communications that may reflect the distribution of the malware strains discussed in the advisory. They first consulted a strategic partner’s passive DNS data to identify the IP addresses to which the domains hosting the malicious downloads resolved and then used that partner’s NetFlow tool to collect traffic samples involving each IP address. Researchers next searched the results for transfers of the same approximate size as the malicious files and then, finally, consulted public registrant data and SecurityScorecard’s Attack Surface Intelligence tool to identify the organizations that own or use the IP addresses involved in those transfers to assess the possibility that they were targets of the recent APT29 activity.
Traffic Analysis Findings
While the available traffic data did reveal data transfers of roughly the same size as some of the files involved in the APT29 activity discussed in the report, these results are ultimately inconclusive. It first bears noting that many of the IP addresses hosting the domains involved in the activity also host other, likely unrelated domains. So,o transfers involving those IP addresses may not necessarily involve the APT29-linked domains.
Additionally, none of the similarly-sized transfers in the dataset involved IP addresses with apparent connections to possible targets of the campaign. Most belonged to large hosting providers such as Digital Ocean, Rackspace, or Hostinger, and neither public registrant data nor SecurityScorecard’s attribution data indicated that diplomatic services used any of them.
However, researchers did identify the locations of the involved IP addresses with the hope that noting the geographical distribution of these data transfers may offer additional information regarding the activity’s targeting.
The largest number of transfers to occur were those similar in size to the DLL files comprising HALFRIG’s four modules; ninety-four such transfers took place, and a majority (sixty-two) of these involved U.S. IP addresses.
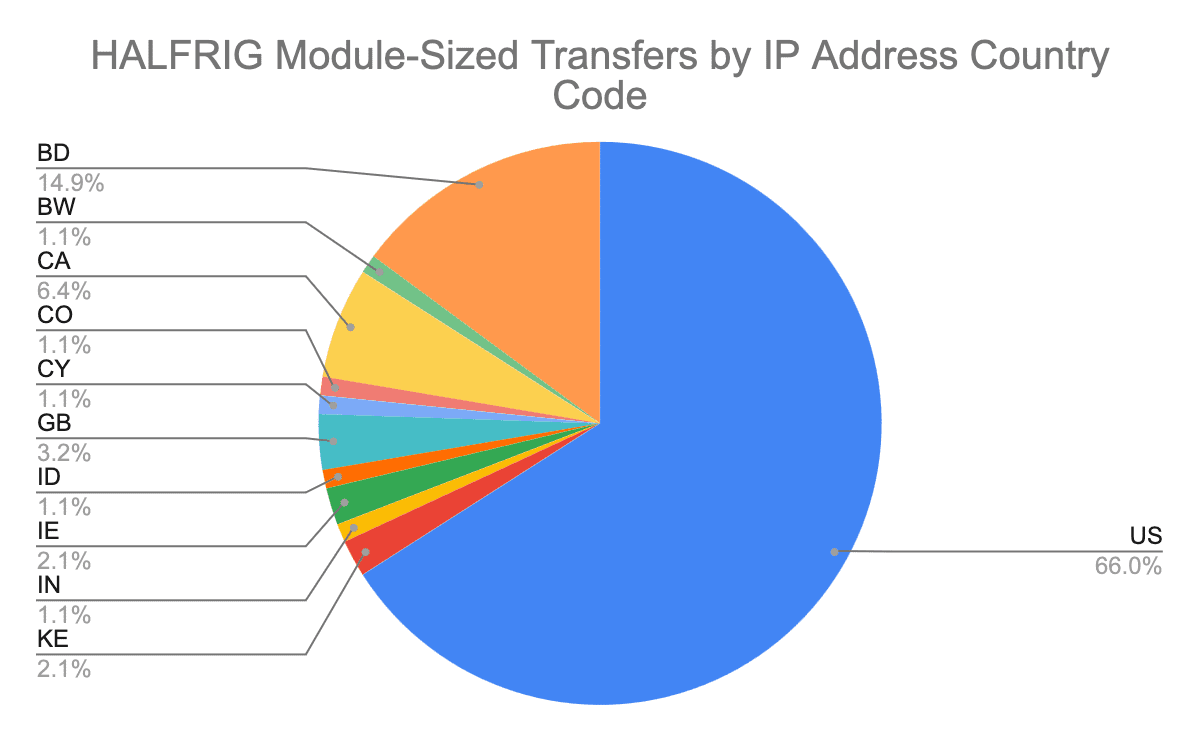
Image 3: A majority of transfers with byte counts similar to those of HALFRIG’s four files involved US IP addresses.
Two IP addresses were involved in transfers roughly the same size as the legitimate executable file attackers used to side-load the file containing QUARTERRIG’s first stage. One is in the United Kingdom, and the other in Germany.
Four IP addresses, all in the U.S., were involved in transfers of a similar size to the QUARTERRIG loader.
A single Brazilian IP address was involved in a transfer of the same approximate size as SNOWYAMBER. Five IP addresses (three in the U.S., one in Brazil–a different IP address than that involved in the previous transfer, and one in South Africa) were involved in transfers roughly the same size as the second-stage payloads SNOWYAMBER delivers.
In light of the geopolitical context, the traffic to IP addresses in the US, UK, and Germany could reflect targeting by APT29. The sample phishing emails provided in the joint advisories indicated that the campaign had targeted European states’ diplomatic personnel, and, given the prominent role the US and UK have played in supporting Ukraine throughout its conflict with Russia (and a long history of espionage predating it), it would make sense for a Russia-linked APT group to target US and UK organizations. However, in light of the considerations discussed above, aside from the location of the IP addresses, the available traffic data does not offer clear evidence indicating that it represents APT29 activity.
Conclusion
While the QUARTERRIG and HALFRIG droppers are new features of this activity, this campaign is generally not a radical departure from familiar APT behavior. Diplomatic personnel are common targets for espionage, including that conducted by APT groups acting on behalf of nation-states. It is similarly common for these groups to use phishing emails impersonating fellow diplomats or other professionals in foreign-policy-related fields for initial access. The group responsible for this recent campaign, APT29, also has a history of using phishing to target diplomatic personnel.
Just as these attacks follow a familiar pattern, so do the defenses against them. Organizations this activity may target can use the IoCs available in the original malware analysis reports to inform their defense against it; they can integrate the file IoCs into their anti-virus solutions and monitor their networks for traffic involving the network IoCs. However, the employees who might receive initial phishing emails remain the first line of defense and the standard guidance for defending against phishing (not opening links or attachments from unknown or untrusted senders and paying particularly close attention to spelling errors or inconsistencies, especially in the sender information) can still do much of the work to prevent a compromise.




