A technical analysis of the Underground ransomware deployed by Storm-0978
Executive summary
The Underground ransomware is the successor of the Industrial Spy ransomware and was deployed by a threat actor called Storm-0978. The malware stops a target service, deletes the Volume Shadow Copies, and clears all Windows event logs.
The files are encrypted using the 3DES algorithm, with the key and IV being encrypted using an RSA public key. The ransomware deletes itself after the file encryption is complete. The extension of the encrypted files isn’t changed, but four specific bytes are added at the end of them.
Analysis and findings
SHA256: d4a847fa9c4c7130a852a2e197b205493170a8b44426d9ec481fc4b285a92666
The malware retrieves the command line arguments using the GetCommandLineW and CommandLineToArgvW functions:

The ransomware can run with a single parameter, which represents a single directory to be encrypted.
The GetWindowsDirectoryW API is used to obtain the path of the Windows directory (see Figure 2).

The malware implements the obfuscation technique called “stack strings”, which splits plaintext strings and constructs them at runtime:
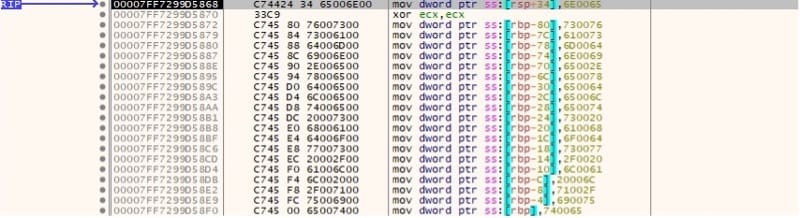
The malicious process deletes all Volume Shadow Copies using vssadmin.exe tool:
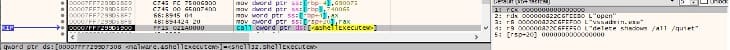
The time limit for disconnected RDP sessions is modified using the ShellExecuteW method, as highlighted in Figure 5.
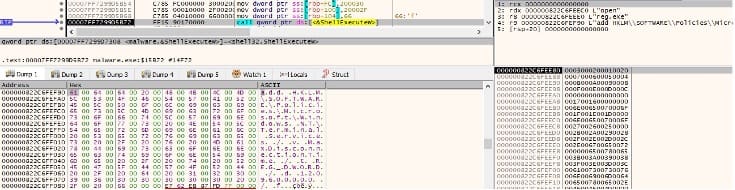
Finally, the binary stops the MSSQLSERVER service:

The process creates a new thread that executes the StartAddress function:
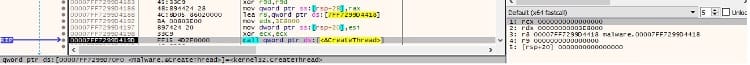
Thread activity – StartAddress function
The ransomware embedded an RSA public key that will be used to encrypt the 3DES key and IV:
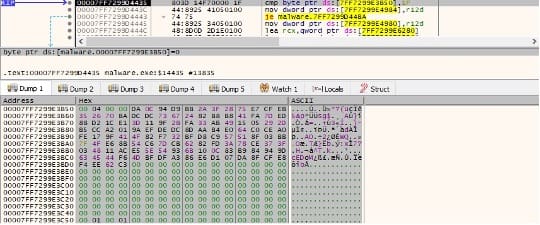
The ransom note content can be also identified in the malware’s body:
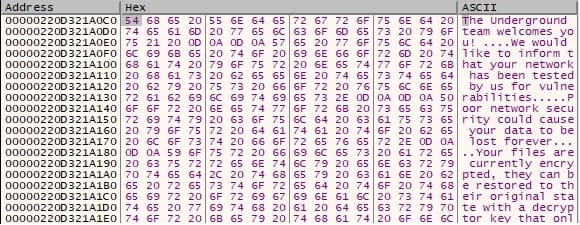
The executable computes the MD5 hash of the RSA modulus, which represents the victim’s ID:
The ransom note containing a TOR link and credentials is modified to include the above victim’s ID:
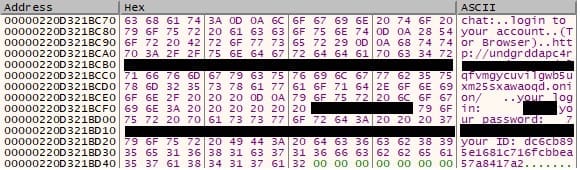
The FindFirstVolumeW API is utilized to begin scanning the volumes on the machine:

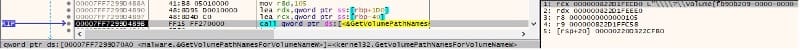
The malicious process obtains a list of drive letters for the specified volume via a function call to GetVolumePathNamesForVolumeNameW:
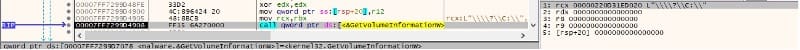
GetVolumeInformationW is used to extract information about the file system and volume associated with the drives:
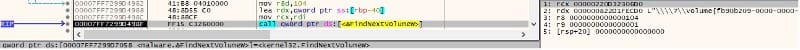
The ransomware continues the volume search by calling the FindNextVolumeW method:
For each of the drives to be encrypted, the binary creates a thread that handles the files encryption (Figure 17).
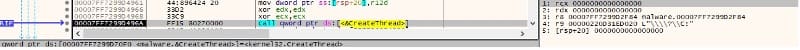
Thread activity – Files encryption
The process enumerates the files found in a directory using the FindFirstFileW and FindNextFileW functions:


The malware doesn’t encrypt a file called “VIPinfo.txt” and the folders containing the following strings:
Windows
Microsoft
google\chrome
mozilla\firefox
\opera\

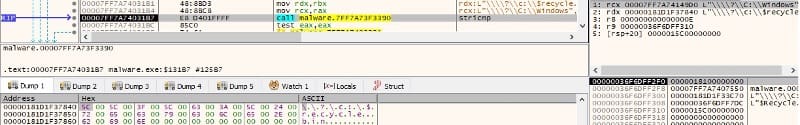
The file’s extension is obtained via a function call to PathFindExtensionW (see Figure 22).

The following file’s extensions will be skipped by the ransomware:
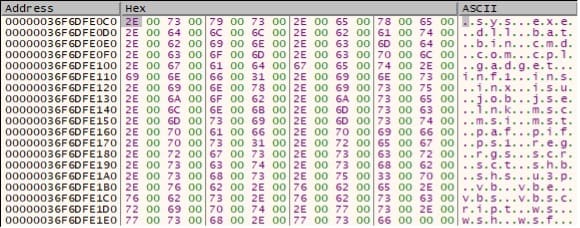
The malware also skips the ransom note called “!!readme!!!.txt”:
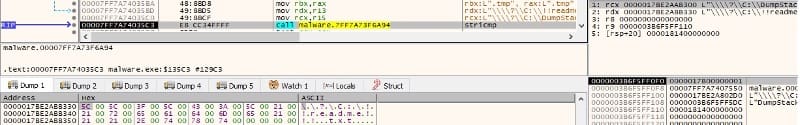
A file is opened using the CreateFileW API (0xc0000000 = GENERIC_READ | GENERIC_WRITE, 0x1 = FILE_SHARE_READ, 0x3 = OPEN_EXISTING):
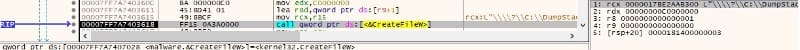
If any of the target files are opened by another process, the binary uses the Restart Manager APIs to kill that process.
The malware starts a new Restart Manager session using the RmStartSession function:

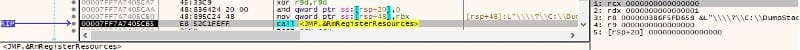
The ransomware determines the process that locked the target file using the RmRegisterResources and RmGetList methods:

The executable kills the above process using the OpenProcess and TerminateProcess APIs, as shown below:


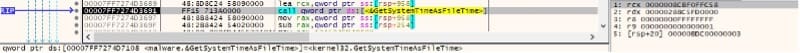
GetSystemTimeAsFileTime is utilized to obtain the system date and time (Figure 31).
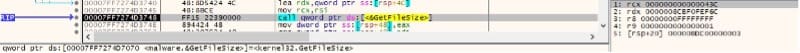
The malicious process retrieves the size of the target file:
The SetFilePointer API is used to move the file pointer within the target file:
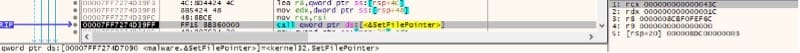
The last four bytes are extracted and compared with “1AY&”, which corresponds to a file that was previously encrypted by Underground ransomware:
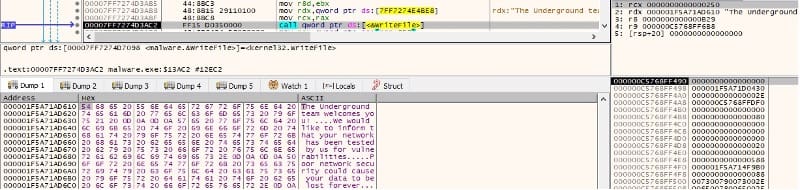
The malware creates a ransom note called “!!readme!!!.txt” in every traversed directory:
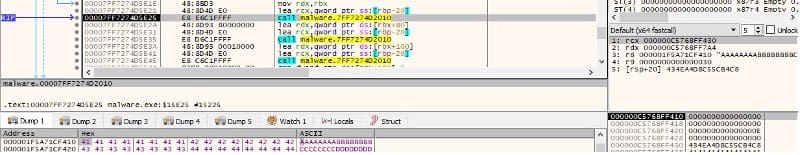
The binary extracts the processor time stamp using the rdtsc instruction and generates 24 pseudo-random bytes twice. The second 24 bytes represent the 3DES key and the first eight bytes from the first iteration represent the IV that will be used for file encryption:
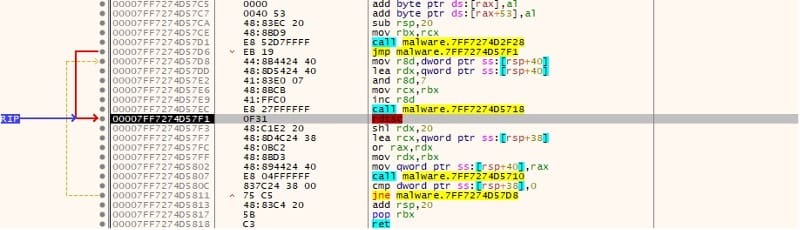

The 3DES key and IV are encrypted using the hard-coded RSA public key, as displayed below:
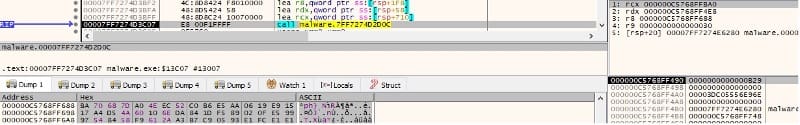
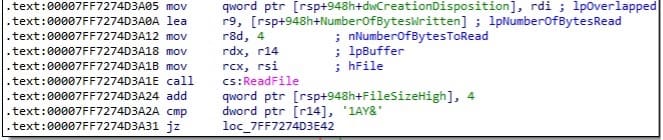
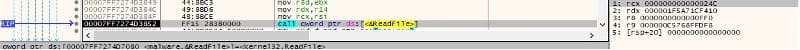
The malicious binary reads the file content via a function call to ReadFile:
The content is encrypted using the 3DES algorithm. The implementation of the algorithm is highlighted below:
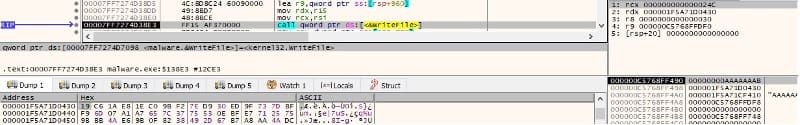
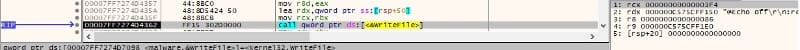
The ransomware writes the encrypted file content, the RSA-encrypted 3DES key and IV, the initial file’s length, and 4 bytes indicating that the file was encrypted:
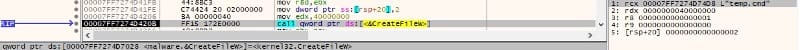
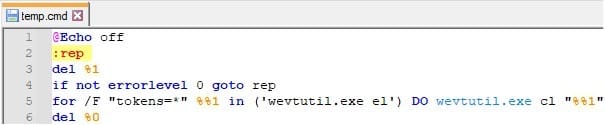
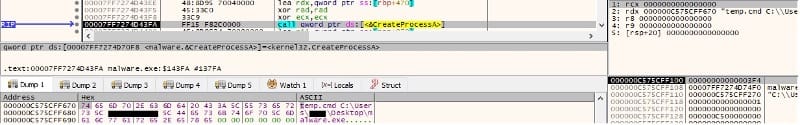
After the encryption is complete, the process creates a CMD file called “temp.cmd” and populates it with the following instructions:
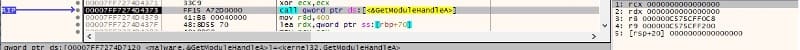
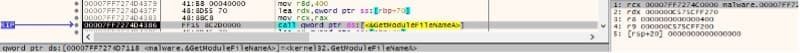
The path of the current executable is obtained using the GetModuleHandleA and GetModuleFileNameA APIs:
The purpose of the CMD file is to clear all event logs using wevtutil and to delete the initial executable as well as the file itself afterwards:
Indicators of Compromise
SHA256
d4a847fa9c4c7130a852a2e197b205493170a8b44426d9ec481fc4b285a92666
Underground Ransom Note
!!readme!!!.txt
Processes spawned
vssadmin.exe delete shadows /all /quiet
reg.exe add HKLM\SOFTWARE\Policies\Microsoft\Windows NT\Terminal Services /v MaxDisconnectionTime /t REG_DWORD /d <Value> /f
net stop MSSQLSERVER /f /m
temp.cmd <Executable path>




