A Deep Dive Into Black Basta Ransomware
Executive Summary of Black Basta Ransomware
Black Basta ransomware is a recent threat that compiled its first malware samples in February 2022. The ransomware deletes all Volume Shadow Copies, creates a new JPG image set as the Desktop Wallpaper and an ICO file representing the encrypted files. Unlike other ransomware families, the malware doesn’t skip files based on their extensions. However, it doesn’t encrypt critical folders that would make the system inoperable.
The files are encrypted using the ChaCha20 algorithm, with the key and nonce being encrypted using the RSA public key that is hard-coded in the sample. The malware can fully or partially encrypt a file depending on its size. The extension of the encrypted files is changed to .basta by the ransomware.
Black Basta Ransomware Analysis and findings
SHA256: ae7c868713e1d02b4db60128c651eb1e3f6a33c02544cc4cb57c3aa6c6581b6e
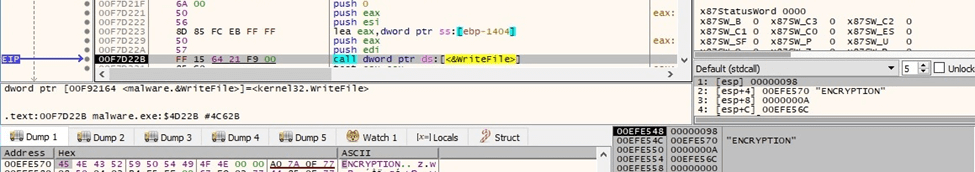
The process displays “ENCRYPTION” in the program window using WriteFile:

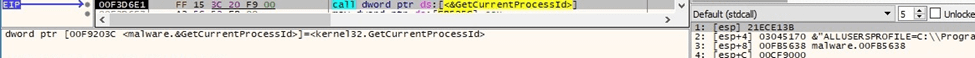
The binary retrieves the process ID via a function call to GetCurrentProcessId:
The malicious process detaches itself from its console by calling the FreeConsole API:

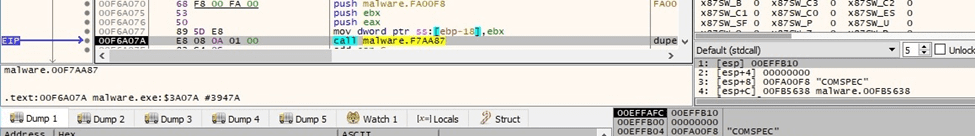
The executable obtains the “COMSPEC” environment variable value, which points to the command line:
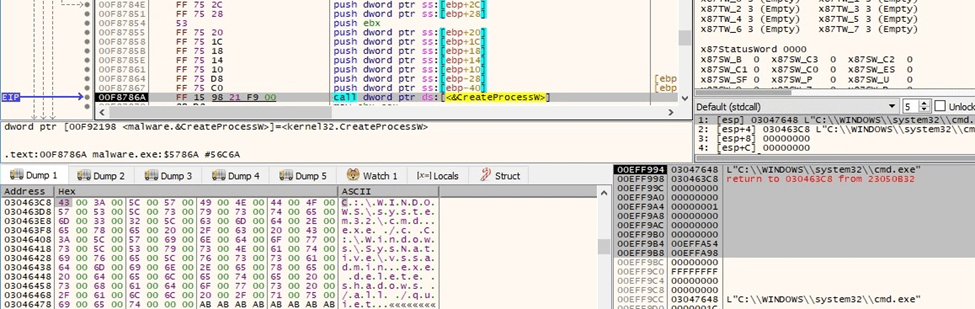
The ransomware deletes all Volume Shadow Copies by running the “C:\Windows\SysNative\vssadmin.exe delete shadows /all /quiet” command, as highlighted below:
The sample waits until the spawned process finishes using the WaitForSingleObject routine:
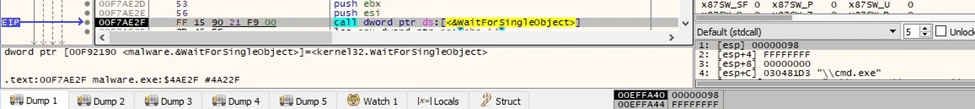
A similar process as above that deletes the Volume Shadow Copies is spawned:
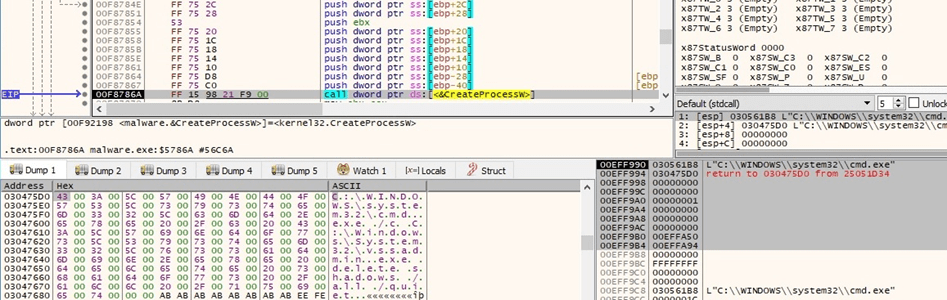
The binary extracts the path of the executable of the current process via a call to GetModuleFileNameW:
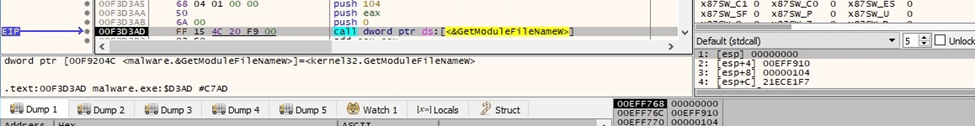
The GetTempPathW API is utilized to retrieve the path of the Temp directory:
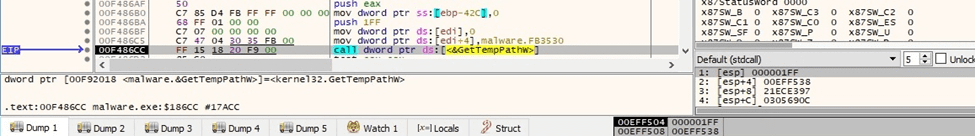
A file called “dlaksjdoiwq.jpg” is created in the Temp directory (0x40 = _SH_DENYNO):
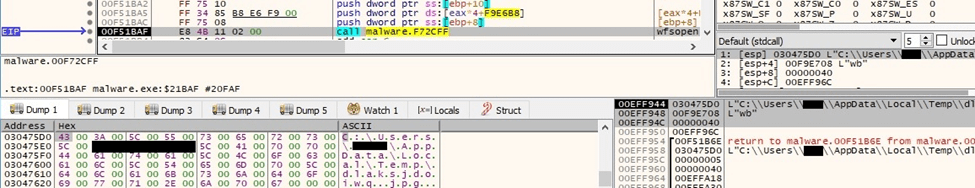
The process moves the file position indicator to the beginning of the file using the fsetpos function:
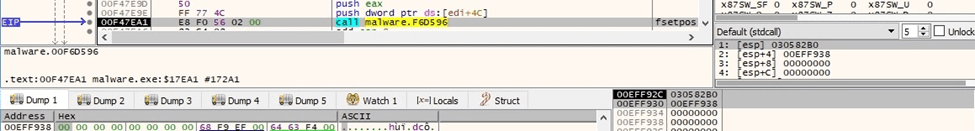
The WriteFile routine is used to populate the JPG file, which contains instructions from the threat actor:
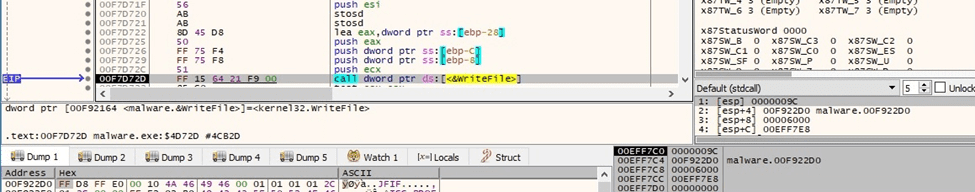

The newly created image is set as the Desktop Wallpaper using SystemParametersInfoW (0x14 = SPI_SETDESKWALLPAPER, 0x1 = SPIF_UPDATEINIFILE):
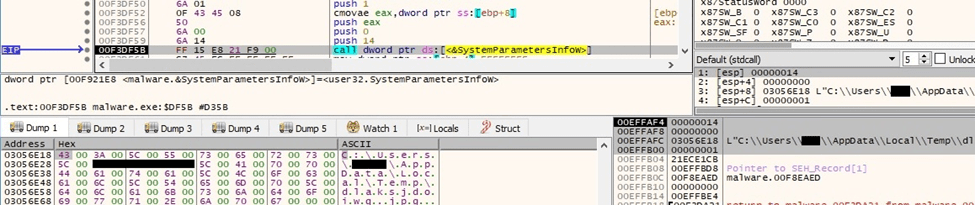
The executable creates an ICO file called “fkdjsadasd.ico” in the Temp directory:
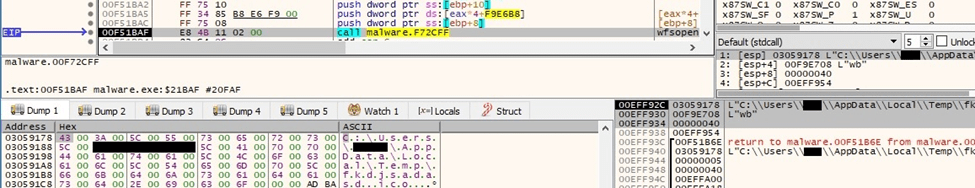
The ransomware writes content to the ICO file, which will represent the icon of the encrypted files:
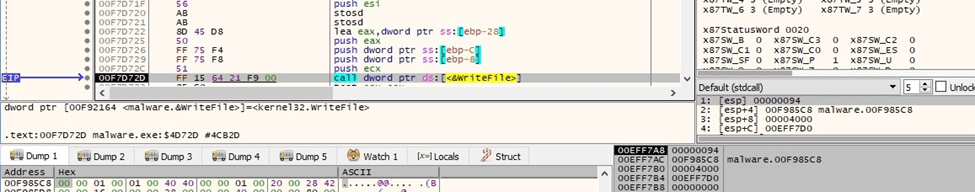

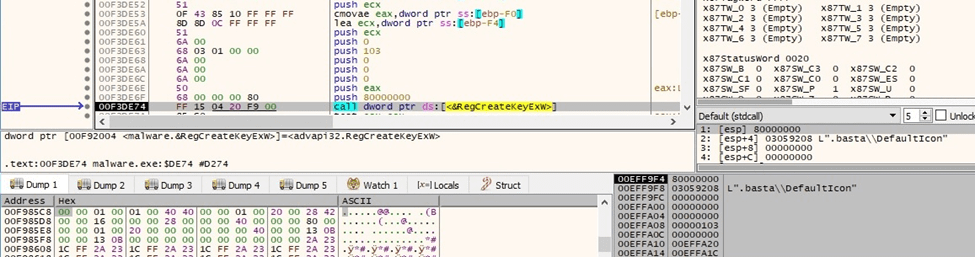
Black Basta ransomware creates the “.basta\DefaultIcon” registry key using RegCreateKeyExW (0x80000000 = HKEY_CLASSES_ROOT, 0x103 = KEY_WOW64_64KEY | KEY_SET_VALUE | KEY_QUERY_VALUE):
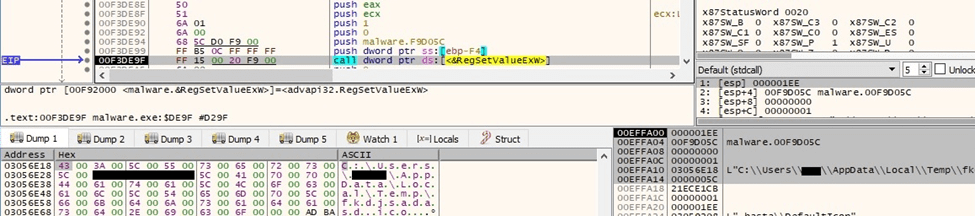
The “(Default)” value of the above key is set to the path of the ICO file:
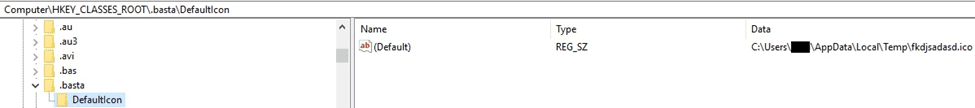
The malicious binary notifies the system that the icon has been changed by calling the SHChangeNotify function (0x08000000 = SHCNE_ASSOCCHANGED, 0x3000 = SHCNF_FLUSHNOWAIT):
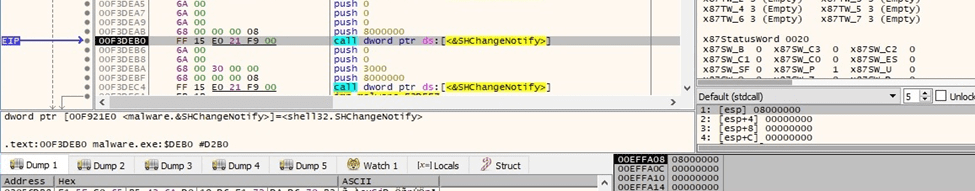
The malware starts scanning for volumes on the system using FindFirstVolumeW:
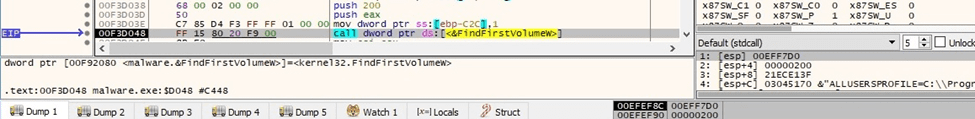
GetVolumePathNamesForVolumeNameW is utilized to obtain the list of drive letters and mounted folder paths for the volume:
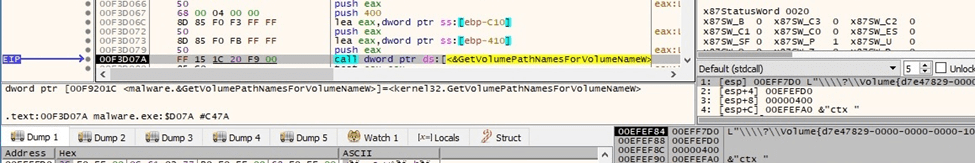
For each drive found, the process performs a call to the GetVolumeInformationW API (see figure 25). As opposed to other ransomware families, Black Basta only targets the mounted volumes and doesn’t mount the hidden volumes.
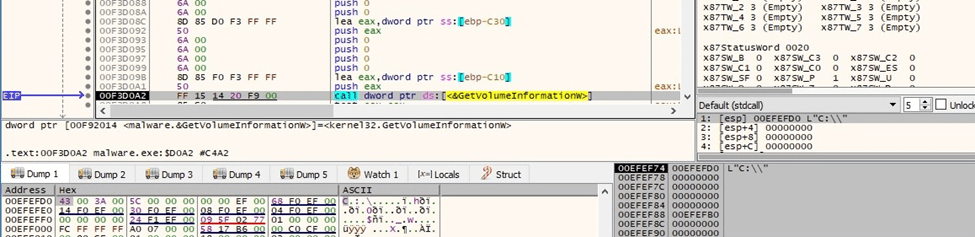
The volume’s enumeration continues by calling the FindNextVolumeW routine:
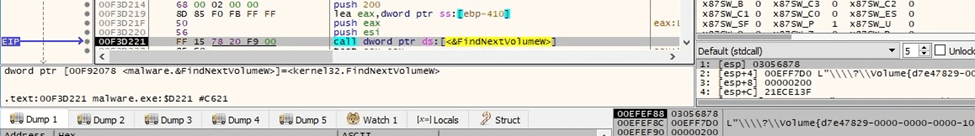
The ransomware extracts a standard set of attribute information from the drives found via a function call to GetFileAttributesExW (0x0 = GetFileExInfoStandard):
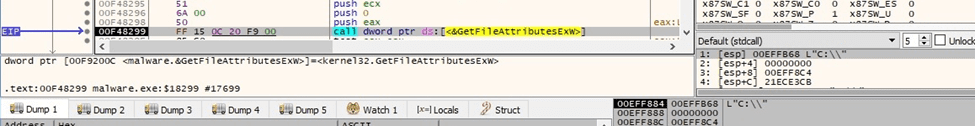
The ransomware creates a ransom note called “readme.txt” in every directory that is traversed, as highlighted in figure 28:
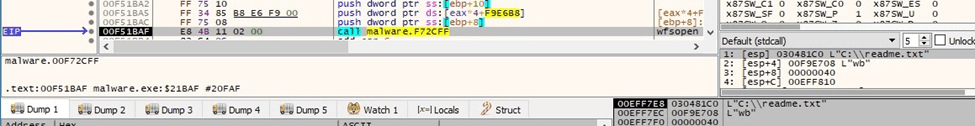
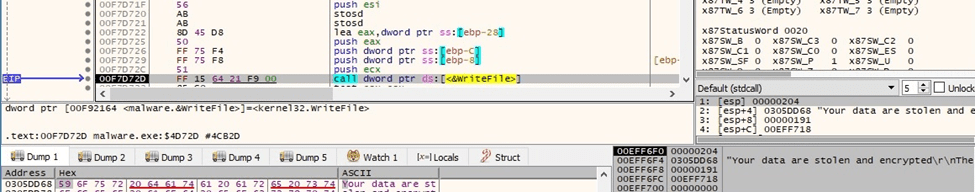
WriteFile is used to populate the ransom note:
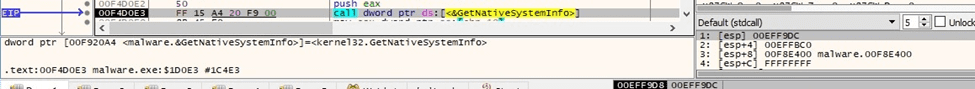
The binary retrieves information about the current system by calling the GetNativeSystemInfo function:
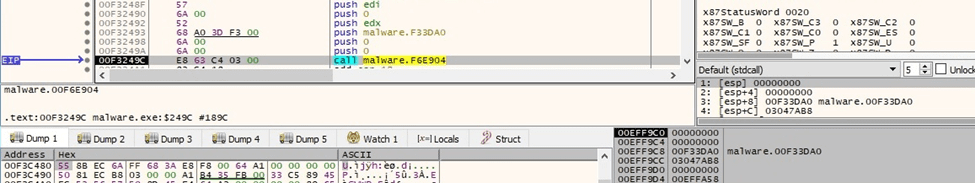
The malware creates multiple threads that will handle the file encryption. The function responsible for encryption is sub_F33DA0 and not the starting address of the thread:
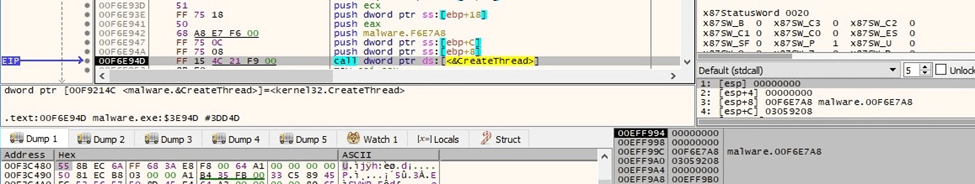
The malicious process starts enumerating the files on the drive using FindFirstFileW:
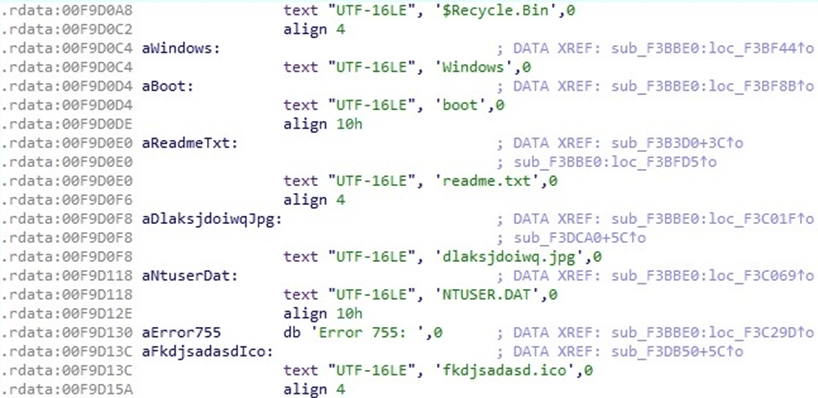
As shown in figure 35, the following files/directories will be skipped:
- $Recycle.Bin
- Windows
- boot
- readme.txt
- dlaksjdoiwq.jpg
- NTUSER.DAT
- fkdjsadasd.ico
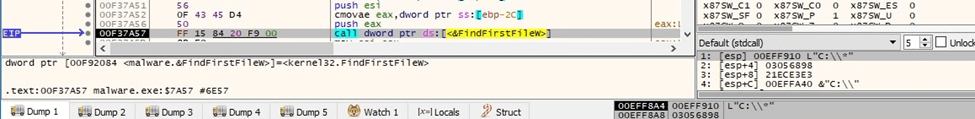
The FindNextFileW routine is utilized to continue the files enumeration:
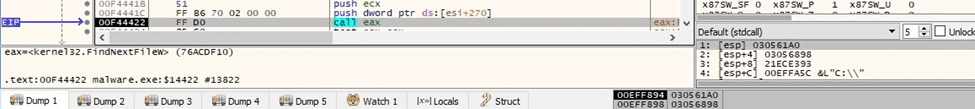
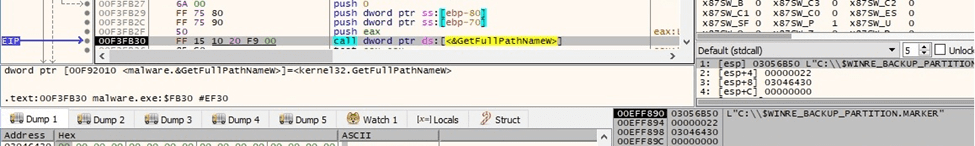
Black Basta ransomware calls the GetFullPathNameW API with a targeted file as a parameter:
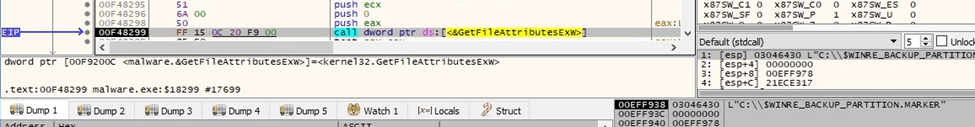
The process obtains a standard set of attribute information for the file via a call to GetFileAttributesExW:
The ransomware has embedded a list of extensions (.exe, .cmd, .bat, and .com) in a section; however, it still encrypts these file extensions.
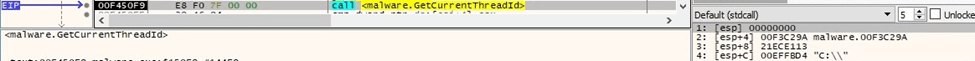
The executable retrieves the thread identifier of the calling thread using GetCurrentThreadId:
The malicious process blocks the main thread until all encryption threads finish execution (see figure 40).
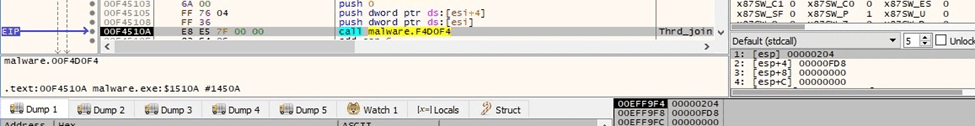
Thread activity – sub_F33DA0 function
The GetFileAttributesW API is utilized to retrieve file system attributes for a targeted file:
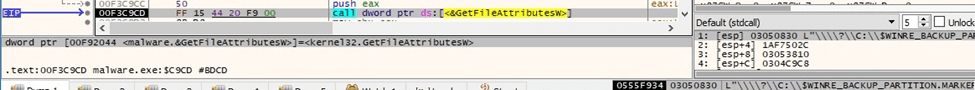
The malicious process opens a file for reading using wfsopen:
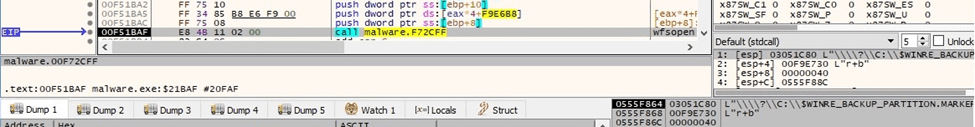
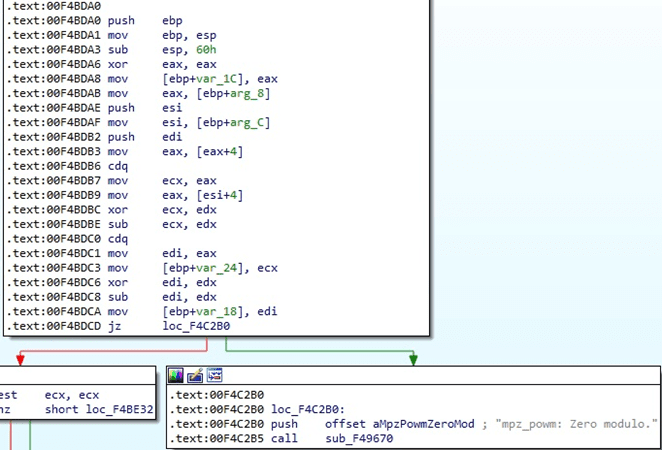
The ransomware moves the file pointer to the position of the last 4 bytes. Whether the file would be encrypted, these would represent the length of the encrypted ChaCha20 key and nonce, as we’ll see later on:
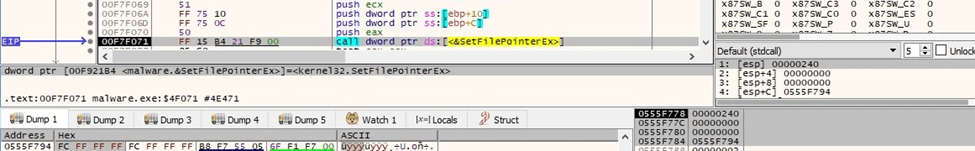
Black Basta ransomware generates 32 random bytes representing the ChaCha20 key and then 8 bytes representing the nonce using rand_s:
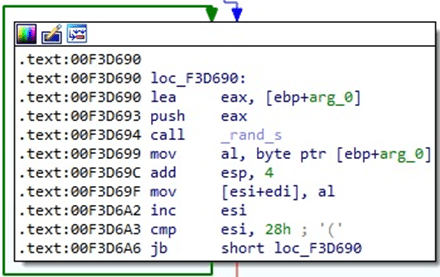

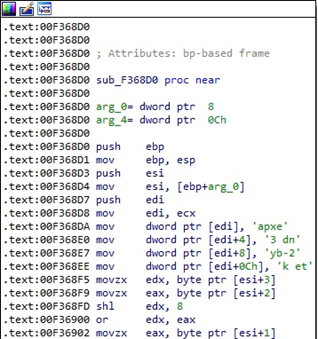
The binary implements the RSA algorithm using the Mini-GMP library, which is fully available on Github:
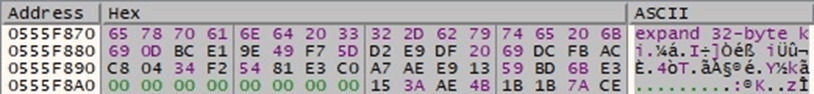
The RSA public key used to encrypt the randomly generated ChaCha20 key and the nonce is presented in the figure below:

The process constructs the initial state of ChaCha20 using the key, the nonce, and some constant values:
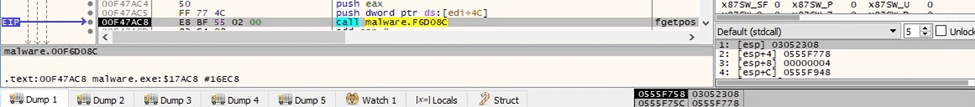
The sample obtains the current position in the targeted file by calling the fgetpos function:
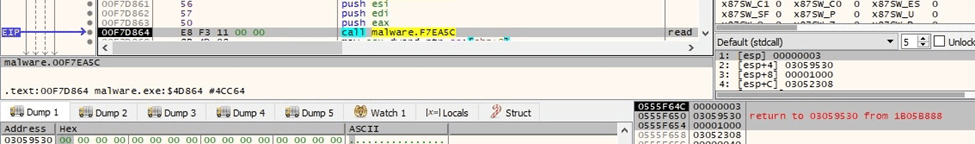
The file content is read by the process via a call to the _read function:
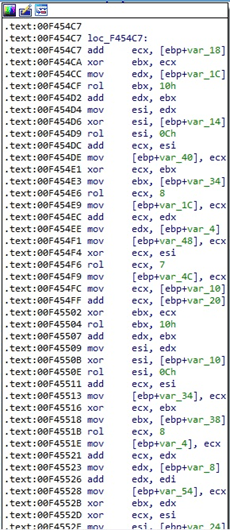
The content is encrypted by the ChaCha20 algorithm 64 bytes at a time:
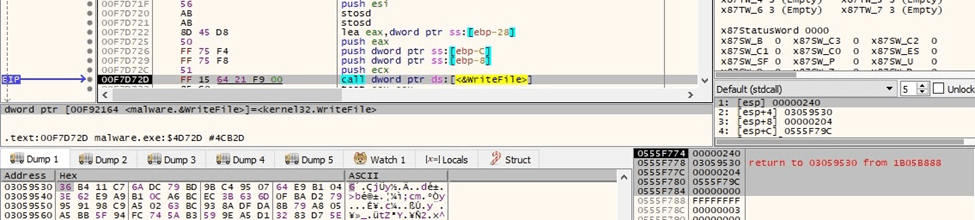
The encrypted data is written back to the file using the WriteFile API:
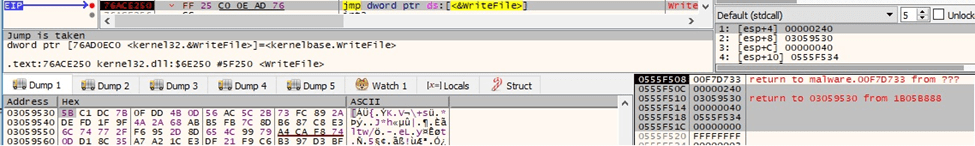
The buffer containing the RSA encrypted ChaCha20 key and nonce is appended to the encrypted file. The length of the encrypted information (0x200 = 512) is added as well:
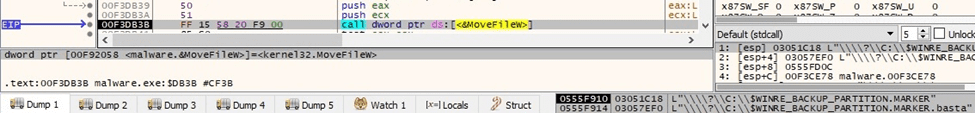
The encrypted file extension is changed to “.basta” using MoveFileW:
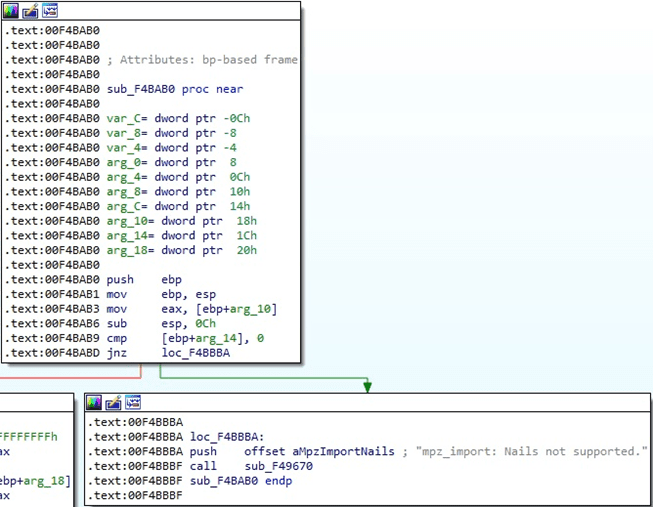
Black Basta Ransomware Case 1 – File size < 704 bytes
In this case, the entire file content is encrypted by the ransomware:
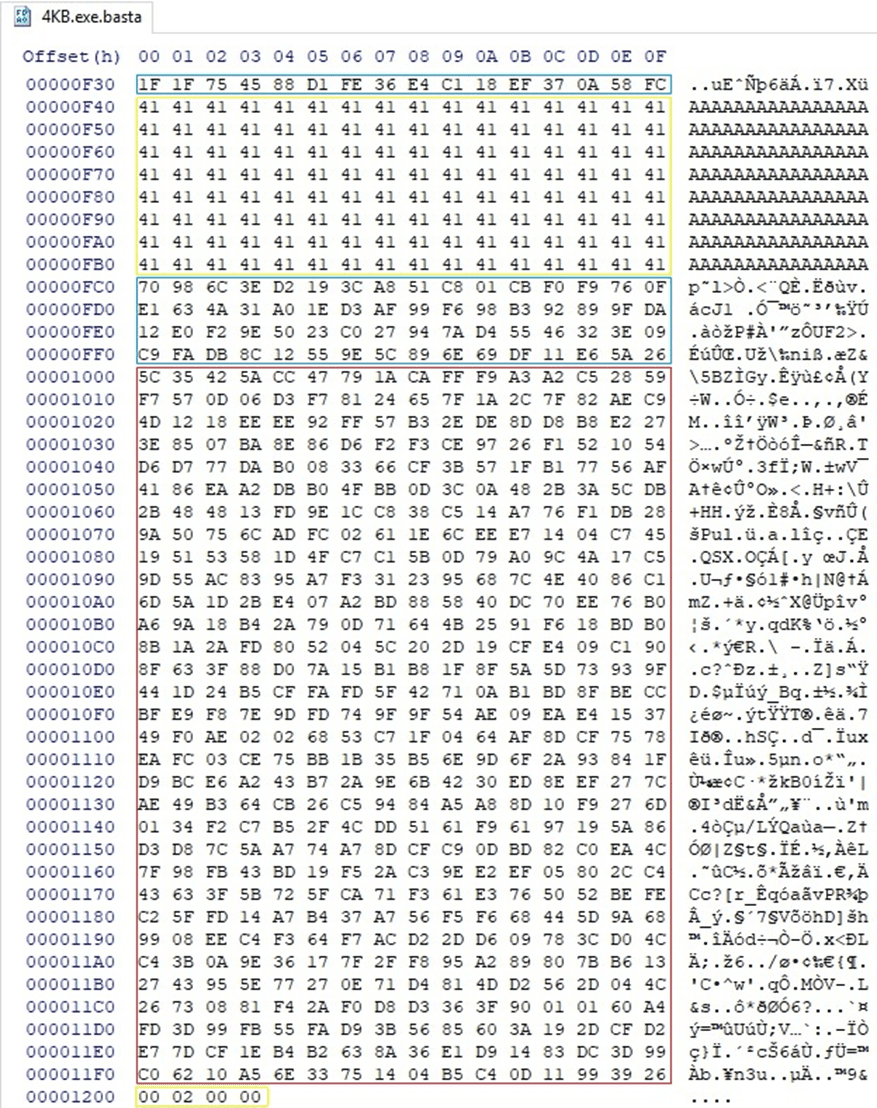
Black Basta Ransomware Case 2 – File size < 4KB
In this case, the file is partially encrypted. The ransomware encrypts 64 bytes, skips 192 bytes, encrypts 64 bytes again, and so on.
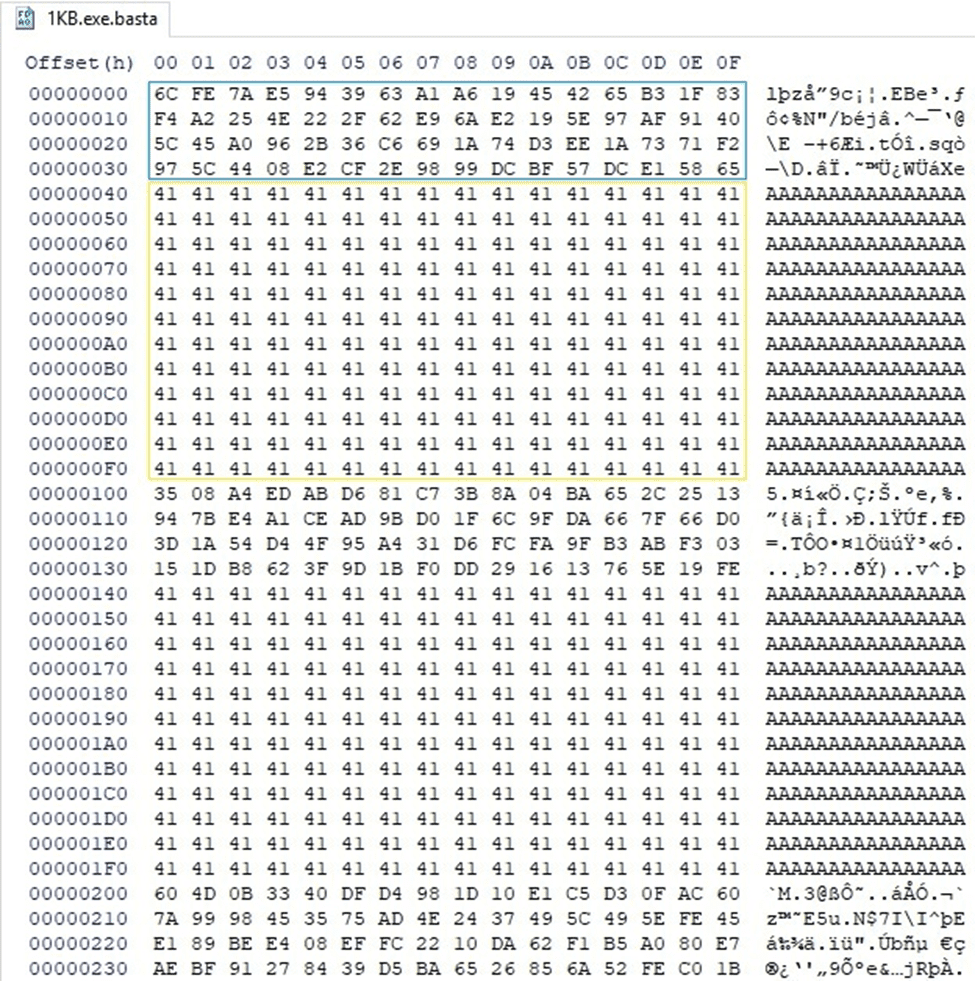
Black Basta Ransomware Case 3 – File size > 4KB
In this case, the file is partially encrypted. The ransomware encrypts 64 bytes, skips 128 bytes, encrypts 64 bytes again, and so on.
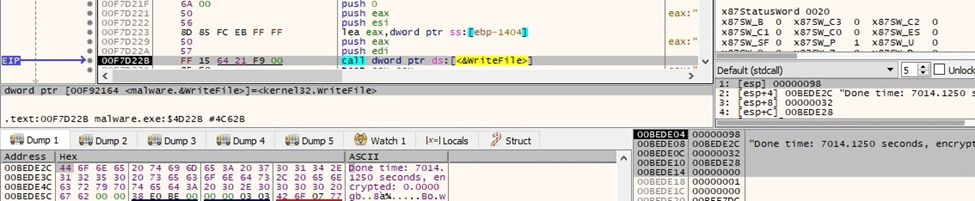
Finally, the ransomware tries to write the time spent during the execution and the total size of encrypted files to the console; however, it raises an error because the process was detached from its console:
Indicators of Compromise of Black Basta Ransomware
Black Basta Ransom Note
readme.txt
Files created
%Temp%\fkdjsadasd.ico
%Temp%\dlaksjdoiwq.jpg
Processes spawned
cmd.exe /c “C:\Windows\SysNative\vssadmin.exe delete shadows /all /quiet”
cmd.exe /c “C:\Windows\System32\vssadmin.exe delete shadows /all /quiet”
Registry key created
HKEY_CLASSES_ROOT\.basta




