What is Supply Chain Detection and Response (SCDR)?
A New Framework for Supplier Ecosystem Security
What Is SCDR?
Supply Chain Detection and Response (SCDR) is a new cybersecurity framework that identifies, prioritizes, and remediates vulnerabilities across an organization’s vendor ecosystem.
Its purpose is preventing supply chain attacks from threat actors and mitigating concentration risk when critical providers experience outages or security failures.

Moving from Measurement to Action
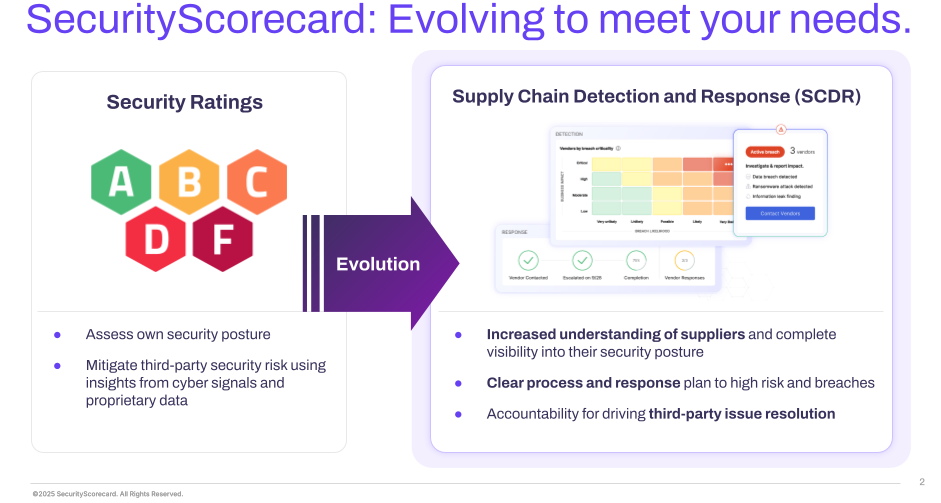
SCDR evolves traditional Third-Party Risk Management (TPRM) and security ratings into an active operational framework. Where TPRM programs assess vendors and security ratings measure risk posture, SCDR drives action and results.
It transforms static assessments into concrete remediation steps that strengthen your entire supply chain cybersecurity. It streamlines communication with affected vendors and tracks resolution progress.
This action-oriented approach significantly reduces the time between identifying issues and resolving them.
Extending Security Beyond Your Perimeter
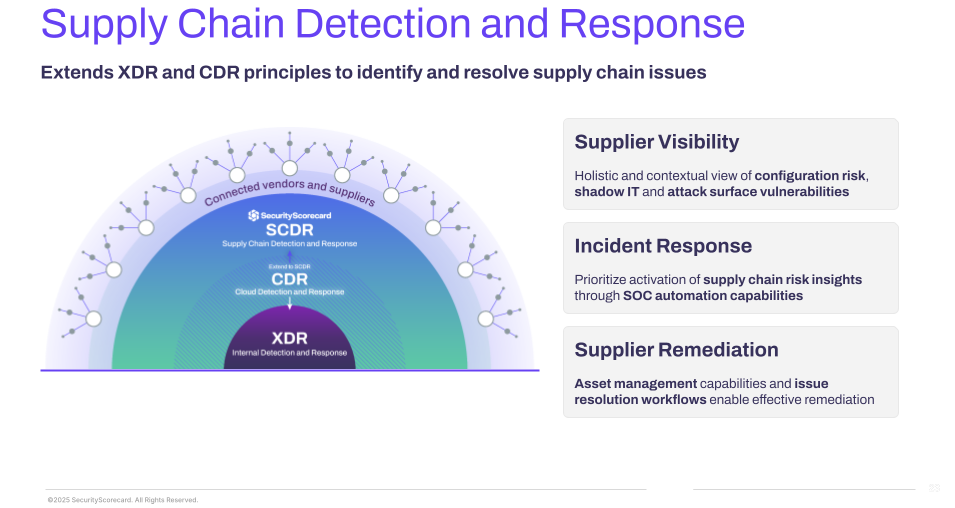
Just as EDR protects endpoints, XDR correlates data across security tools, and CDR defends cloud environments, SCDR extends these proven detection and response principles to the supply chain. The key difference is that SCDR operates beyond your network perimeter to secure the extended attack surface where third, fourth and nth-party risks originate.
Who Benefits from SCDR?
SCDR addresses a critical gap in third-party risk management. It particularly benefits CISOs, security operations teams, risk and compliance officers, and third-party risk managers who struggle to translate security ratings and vulnerability lists into meaningful supplier engagement.
Security organizations can respond more effectively to threats while GRC (Governance, Risk and Compliance) teams gain auditable evidence of due diligence. The solution enables organizations to satisfy regulatory requirements (such as NIST2 and DORA) for vendor oversight and demonstrate mature risk management to boards and regulators.
Why Organizations Need SCDR Now
Companies today face two major digital supply chain dangers at once. Concentration risk creates single points of failure as companies increasingly rely on the same critical service providers. Simultaneously, threat actors increasingly target supply chains as an efficient attack vector.
According to the 2025 World Economic Forum Global Cybersecurity Outlook report, 72% of organizations report rising cyber risks, while 54% of large organizations identify supply chain security as their top barrier to cyber resilience. Perhaps most concerning, 71% of cyber leaders believe small vendors have reached a breaking point in their security capabilities.
Most companies lack visibility into their supply chain risks. Without established response processes, breaches spread across partner networks before detection occurs. Traditional tools fall short in addressing these challenges. Security ratings provide valuable insights but leave a critical gap in response capabilities. Companies receive ratings with long lists of issues but lack structured ways to engage suppliers effectively.
SCDR fills this operational gap by helping organizations monitor, detect, and respond to supplier risks before they escalate into breaches.

How Does SCDR Work?
Where previous methods focused on assessment and measurement, SCDR adds structured response capabilities and real-time vendor collaboration. This evolution supports supply chain incident responders with three integrated capabilities:
1. Continuous Threat Monitoring with Early Risk Detection
SCDR tracks specific threats affecting your vendors in real time. Instead of overwhelming you with hundreds of issues, it focuses on one or two actionable threats like:
- Malware infections
- Leaked credentials
- Ransomware and social engineering attacks
- Attack surface changes
The system prioritizes exploitable threats rather than generating long, unfocused lists.
2. Supplier Lifecycle Management with Set-It-and-Forget-It Automation
SCDR allows you to set security policies and automate their enforcement. It organizes vendor relationships based on business impact and risk levels. The system stores all supplier evidence and documentation in one location, creating a complete view of each vendor relationship.
3. Collaborative Remediation through Clear Communication
SCDR streamlines communication between companies and suppliers. Security teams can alert multiple suppliers simultaneously about threats. They can recommend specific fixes and request proof of resolution.
Every action receives tracking. Every issue gets assigned an owner
How Does SCDR Compares to Other Security Models?
SCDR builds on established security approaches but serves a different purpose. Each detection and response solution addresses specific security domains:
| Solution | Core Function | Protection Domain | Key Capabilities | Limitations for Supply Chain |
| EDR | Detects and responds to threats on endpoints | Laptops, workstations, servers | Real-time monitoring, malware detection, automated response | Limited to internal devices, blind to vendor systems |
| MDR | Provides managed monitoring and threat response | Internal networks and systems | 24/7 expert monitoring, threat hunting, guided remediation | Focuses on internal environments, not vendor ecosystems |
| XDR | Correlates data across multiple security tools | Network, endpoint, identity, cloud | Cross-platform threat detection, unified security data, automated workflows | May incorporate some vendor data but lacks supplier engagement capabilities |
| CDR | Identifies and mitigates cloud-specific threats | SaaS applications, cloud workloads | Cloud configuration monitoring, identity protection, data security | Cloud-focused, misses on-premise vendor risks and broader supply chain |
| SCDR | Detects and responds to supplier-originated threats | External vendors, third parties, supply chain | Ecosystem monitoring, vendor engagement, collaborative remediation | Requires organizational maturity to implement effectively |
Only SCDR specifically addresses the external attack surface and supplier ecosystem where third-party incidents originate. It extends security principles beyond organizational boundaries to help you monitor, detect, and respond to supplier risks before they become breaches.
How Does SCDR Help Security Teams?
SCDR equips security teams with capabilities essential to modern vendor risk operations:
- Discover shadow vendors: Identify unreported or unauthorized third parties accessing your environment
- Assess real-time security posture: Evaluate vendors using live threat intelligence and attack surface data
- Detect early compromise signals: Identify malware infections, leaked credentials, and unusual network activity
- Implement risk-based tiering: Categorize vendors by business impact and likelihood of security incidents
- Engage at-risk suppliers: Alert and collaborate with high-risk vendors through automated communications
- Validate remediation actions: Collect and verify evidence of security improvements through documentation
- Track metrics and outcomes: Report status, resolution times, and risk reduction to security leaders and boards
These capabilities transform third-party security from a compliance exercise into an active defense strategy. SCDR shifts the focus from annual assessments to continuous monitoring and rapid incident response.

MAX: SecurityScorecard’s SCDR Service
SecurityScorecard delivers SCDR through MAX, a fully managed service. MAX implements complete supply chain detection and response without requiring additional internal resources.
Our specialized team takes responsibility for the entire SCDR workflow:
- Continuous vendor monitoring: Tracking your entire supplier ecosystem for security issues 24/7
- Direct supplier engagement: Reaching out to vendors when risks appear, with clear remediation guidance
- Evidence collection: Gathering and validating documentation that proves resolution of security issues
- Response verification: Reviewing vendor responses for completeness and effectiveness
- Critical issue escalation: Bringing urgent matters to your attention with specific action recommendations
- Risk reduction measurement: Tracking key metrics to demonstrate security improvements over time
MAX: The most comprehensive option for organizations seeking to outsource their third-party risk management program.
Ready to strengthen your supply chain security? Transform your supply chain security posture from reactive to proactive? Detect vendor risk before it spreads? Demonstrate mature vendor security management to regulators and board?
Take a tour of SecurityScorecard MAX
SCDR FAQS
Is SCDR a product or a category?
Both.
SCDR is a new category of cybersecurity, like EDR or XDR, but focused on your vendors. It applies proven response strategies to third-party risk.
SecurityScorecard also offers a specific SCDR product, which delivers those capabilities through a managed service called MAX.
How does SCDR work in practice?
Supply chain incident responders use SCDR to:
- Find suppliers that aren’t on your radar
- Check their current security posture
- Get alerts on things like leaked credentials or active malware
- Group vendors by business impact and likelihood of incident
- Notify vendors of urgent issues and ask for proof of remediation
- Track resolution and report to internal teams
SCDR turns third-party risk into a workflow—not a spreadsheet.
How do we get SCDR today?
Right now, SCDR is available exclusively through MAX, our fully managed service.
If you want the benefits of SCDR without building your own program, MAX delivers it.






