Was the Explosion at Freeport LNG a Result of a Russian Cyber Attack?
Executive Summary
- On June 8, an explosion–which some commentators hypothesized was the result of a Russian cyber attack–took place at Freeport LNG’s liquefied natural gas (LNG) export facility in Quintana, Texas.
- SecurityScorecard’s platform revealed a number of vulnerabilities an attacker could have exploited.
- SecurityScorecard researchers observed some traffic involving Freeport IP space that may have initially appeared suspicious in the weeks leading up to the explosion, but further analysis did not offer additional evidence of malicious activity.
- Although the observed vulnerabilities are cause for concern, they, alongside the available network flow data, do not appear to constitute conclusive evidence of a Russian attack.
Background
On June 8, an explosion took place at Freeport LNG’s liquefied natural gas (LNG) export facility in Quintana, Texas. The company later explained that the explosion resulted from a rupture in an over-pressurized pipeline, but did not comment as to how the pressure built up enough to cause such a rupture. In the wake of the explosion, Freeport reported that the outage resulting from it would persist until September, after which the facility would only resume partial operations. Because the facility is responsible for a considerable portion of US LNG exports to Europe, disruptions to its operations drove price increases in European gas markets, where supply had already decreased as a result of the Russian invasion of Ukraine and the resulting decrease in European consumption of Russian gas. The sensitivity of LNG imports for European states has contributed to speculation that the June 8 explosion was the result of malicious Russian cyber activity.
On June 21, The Washington Examiner published an opinion piece hypothesizing that Russian advanced persistent threat (APT) activity was responsible for the explosion. The author argues in support of this claim on the following grounds:
- US LNG exports to Europe are a long-standing strategic concern for Russia since they could undermine its position in European gas markets. Freeport LNG is responsible for a considerable portion of these exports.
- Two unidentified sources claimed that the GRU, Russia’s main military intelligence service, had conducted reconnaissance against Freeport LNG in February 2022.
- Another unidentified source informed the author that the Federal Bureau of Investigation (FBI) was investigating the explosion, which led the author to speculate that it was specifically the FBI’s Cyber Division that was involved in the case. Freeport LNG announced that it is coordinating its investigation with state and local officials, but did not specifically name the FBI or its Cyber Division. As the author notes, the FBI has not confirmed its involvement in the case.
- The piping where the overpressure event that caused the explosion took place likely had safety features that would have prevented such events in normal circumstances. Because the facility’s control, including these safeguards, were likely networked, a threat actor could have disabled them, allowing pressure in the piping to build up enough to cause the explosion.
- The TRITON malware attributed to the XENOTIME threat actor group, which researchers have linked to the Russian Ministry of Defense’s Central Scientific Research Institute of Chemistry and Mechanics, specifically targets industrial control systems used in oil and gas facilities.
- The FBI warned that threat actors were still targeting the energy sector with TRITON in March and April 2022, despite its first having come to prominence in 2017.
Freeport LNG responded to these claims June 23, reporting that it had ruled out malicious cyber activity as a cause of the explosion, noting that its security systems were functioning properly at the time of the incident and did not observe evidence of compromise. The author of the Washington Examiner piece argued that Freeport LNG lacked the systems necessary to monitor ICS/OT systems, so it was impossible to rule out a cyber attack without a more thorough forensic investigation.
With this in mind, SecurityScorecard researchers undertook an investigation into Freeport LNG’s systems to assess the likelihood of an attack.
Scorecard Findings
SecurityScorecard’s platform has observed several issues that could have contributed to an attack against Freeport LNG. As of June 25, nine domains attributed to the company lack Sender Policy Framework (SPF) records. SPF can reduce a phishing attack’s chances of success by detecting attempts to spoof emails. However, without SPF, an attacker could more easily impersonate a Freeport LNG employee by using the affected domains to send emails that appear to have come from within the company.
SecurityScorecard’s platform also found Freeport LNG’s websites, including one hosted at the same IP address discussed above, to use GoDaddy TLS certificates. GoDaddy experienced a breach that exposed data for users of its TLS certificates in September 2021. This could have affected Freeport LNG, which may, in turn, have put the company at risk of other compromises.The exposed data could, for example, inform phishing activity. While the available research into TRITON does not indicate that attackers have used phishing to distribute it, phishing remains a common method of initial access for a wide variety of threat actors, both nation-state backed and purely criminal.
SecurityScorecard observed outdated software in use at a Freeport LNG IP address and additionally detected outdated versions of Chrome at 50.59.84[.]1 on June 7 and 8 (the day of the explosion). This may also reflect a broader pattern.
SecurityScorecard previously detected other outdated versions of Chrome at 50.59.84[.]1 eight times between December 2021 and May 2022. Analysts have not specifically linked the distribution or execution of TRITON to the exploitation of vulnerabilities affecting outdated web browsers. Attackers do, in general, often exploit vulnerabilities in unpatched software.
Other breaches have also affected a variety of Freeport LNG employee information, including email addresses, passwords, and other personal information. It is fairly common for threat actors to use exposed employee credentials to access internal systems of target organizations, so these exposures may have put Freeport LNG at risk, if they involved credentials shared between the exposed account and the employee’s Freeport LNG account. To take ransomware as one example, SecurityScorecard’s research indicates that these issues are much more prevalent among ransomware victim organizations than their peers. Two of SecurityScorecard’s categories for monitoring exposed information–leaked credentials and exposed personal information–were respectively found to affect 71% and 64% of ransomware victims, but only 44% and 25% of non-victims.
Together, these vulnerabilities and exposures suggest that Freeport LNG may have been at risk of attack prior to the explosion. But, they do not offer evidence to link them specifically to a TRITON attack or other Russian APT activity.
Additional SSC Research
After identifying the above issues SecurityScorecard found to affect Freeport LNG, researchers consulted additional datasets in order to identify possible links between Russian APT activity in general and the XENOTIME/TRITON ICS malware in particular, which the author of the opinion piece in the Washington Examiner highlights as a possible cause of the explosion. Other researchers have published on TRITON fairly widely since 2017. Based on those previous reports, SecurityScorecard researchers specifically identified exposed VPN gateways and traffic involving ports 1502, 443, 4444, 8531, and 50501 as particular areas of concern.
Mandiant’s April 2019 analysis advised that anomalous VPN activity could indicate the use of TRITON. And as noted in an early 2022 CISA alert, Russian APT groups have historically exploited vulnerabilities affecting certain Citrix products. In light of both of these warnings, SSC’s observation of a Citrix VPN gateway at 50.59.84[.]81, to which a Citrix-specific Freeport LNG subdomain, citrix.freeportlng[.]com, resolves, may be particularly noteworthy.
Though SecurityScorecard’s platform and Attack Surface Intelligence (ASI) product do not indicate any vulnerabilities at that IP address, even if the particular Citrix product in use is not vulnerable, the subdomain could have been enough to attract a threat actor’s attention. Upon seeing Citrix mentioned, an attacker may have at least attempted to assess whether the relevant vulnerability affected the Citrix products in use, or they may have attempted to log in using previously exposed credentials belonging to a Freeport LNG employee.
Because Mandiant also advised to “look for inbound and outbound connections from and to non-standard IP ranges, especially from international VPS providers,” SecurityScorecard next analyzed the network flows (netflow) involving 50.59.84[.]81, identifying 737 flows and 23 other unique IP addresses between April 19 and June 8. While this traffic included a considerable number of flows involving foreign IP addresses (17 of the 23 other IP addresses, responsible for 572 of the 737 flows observed, are located in India), this traffic may reflect routine business operations rather than malicious activity. It is fairly common for IP addresses to mostly communicate with other IP addresses located in the same country, so at first glance, the heavy representation of foreign traffic within this sample appears somewhat anomalous. Within the wider sample of traffic involving Freeport LNG-attributed IP addresses, only approximately 17% of flows (7,606 of 44,942) involved Indian IP addresses, and the percentage was much higher (approximately 78%–or 572 of 737 flows) when researchers narrowed the search to traffic involving 50.59.84[.]81. However, additional research into these flows raised the possibility that the traffic is more routine than it first appeared.
Of the Indian IP addresses communicating with 50.59.84[.]81, 183.83.143[.]114 appeared the most regularly: it was involved in 250 of the 572 flows. SSC attributes 183.83.143[.]114 to Beam Telecom, an Indian telecommunications company acquired by Atria Convergence Technologies (another Indian telecommunications company) in 2009. Given that 50.59.84[.]81 hosts a VPN login, this recurring traffic could represent an India-based employee or contractor’s remote access to internal Freeport LNG systems.
Eleven of the sixteen other Indian IP addresses observed belong to Capgemini Technology Services India Limited. Capgemini is a technology-focused consultancy that counts the energy sector as one of its areas of specialization and has collaborated with Freeport LNG in the past. It is also quite possible that this collaboration is ongoing. That being the case, traffic between Freeport LNG and Capgemini assets could reflect this collaboration (and would therefore be benign).
CISA’s February 2019 advisory regarding TRITON noted that some of its communications occur over port 1502, and in the above-cited report, Mandiant noted that it uses ports 443, 4444, 8531, and 50501. It is incredibly common for traffic to take place over port 443, so in the absence of other data (especially Freeport LNG’s internal data), the appearance of port 443 in this dataset is unlikely to offer evidence of Russian APT activity or the use of the TRITON malware. However, SSC researchers consulted the available netflow data for traffic over the ports mentioned, as they are less common and may therefore offer clearer indications of anomalous activity.
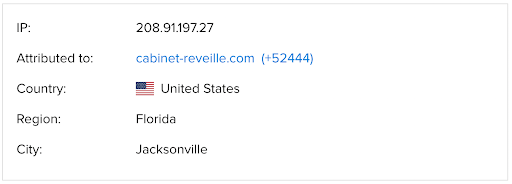
Two flows, both to the same Freeport LNG-attributed IP address, 208.91.197[.]27, used port 4444. In one, 45.70.185[.]146 communicated with 208.91.197[.]27 over port 4444 on May 23, and in the other, 170.82.124[.]222 did on June 6. Between April 19 and June 8, 182 flows to the same Freeport LNG-attributed IP address took place over port 8531, and 28 occurred over port 50501. However, 208.91.197[.]27 appears to be a shared resource: SSC attributes it to 52,445 organizations. That being the case, traffic to it is not particularly likely to represent particularly focused targeting of Freeport LNG, especially given that it is the only Freeport LNG-attributed IP to have seen any such traffic.
Moreover, SecurityScorecard’s scan data did not reveal any industrial applications in use at the address. NetworksDB indicates that it hosts over 900,000 domains, which may suggest that it is used for web hosting, further reducing the likelihood that the above-mentioned traffic represents targeted activity involving ICS malware like TRITON.
These findings represent the results of researchers’ initial reflections upon some of the data about Freeport LNG’s systems available to external observers. An investigation by Freeport LNG and federal authorities is ongoing. And, given investigators’ access to the internal data necessary to inform such conclusions, is more likely to yield definite findings regarding the cause of the explosion. In the absence of that data, there is little in the way of unequivocal evidence to support claims of a Russian attack against Freeport LNG. SecurityScorecard’s findings do suggest that Freeport LNG may have been susceptible to phishing, but taken in isolation, that need not indicate nation-state activity.
Similarly, while some of the netflow data analyzed by SecurityScorecard may appear suspicious, it too offers little definite evidence of an attack using TRITON. The risk of destructive attacks against critical US infrastructure by state-sponsored Russian threat actors has undoubtedly increased as a result of the war in Ukraine. Still, outside of the geopolitical context, the initially available technical data does not favor the suggestion that the explosion in Quintana, Texas is the result of such activity.
About SecurityScorecard
SecurityScorecard offers a 360-degree approach to security prevention and response. For more information, request a demo. SecurityScorecard’s threat research and intelligence could be the competitive advantage SLED organizations need to stay ahead of today’s fast-moving threat actors.
For more custom insights on a regular basis through our team’s 100+ years of combined threat research and investigation experience, or more details on these findings and the other keywords that were provided, please contact Ranell Gonzales for a discussion of our Cyber Risk Intelligence as a Service (CRIaaS) offering. Should you have already suffered a breach, SecurityScorecard’s Digital Forensics Solutions can empower your post-breach actions.




