The Role of Supply Chain Cyber Risk in U.S. Healthcare: Inside SecurityScorecard’s new report
In late February of this year, Change Healthcare experienced a massive ransomware attack. The company, a subsidiary of United Healthcare, is the largest clearinghouse for insurance billing and payments in the U.S, processing 15 billion medical claims each year. The attack had broad consequences across the healthcare sector, and highlighted how one breach or one vulnerability can cripple the entire healthcare ecosystem
Previous SecurityScorecard research found that healthcare has some of the highest rates and numbers of third-party breaches. Meanwhile, our separate research on the S&P 500 found that its member healthcare companies had some of the lowest security ratings on that U.S. stock index.
As a result, SecurityScorecard STRIKE threat hunters set out to examine supply chain cyber risk in this vital sector. The new report, “The Cyber Risk Landscape of the U.S. Healthcare Industry,” examines historical breach data and security ratings to provide insights for healthcare organizations to stop supply chain breaches. In the wake of Change Healthcare, SecurityScorecard investigated the overall cyber hygiene and the most critical risks faced by the 500 largest U.S. healthcare companies. While the healthcare sector gets a “B+” security rating for the first half of 2024, it faces a critical vulnerability: supply chain cyber risk. Below are more key highlights from the report.
Healthcare industry gets a B+
The U.S. healthcare industry’s security ratings were better than expected, with an average score of 88. Companies with a B rating are 2.9x times more likely to be victims of data breaches than those with an A rating. A relatively low 5% of the organizations experienced publicly reported breaches in the past year, while 6% had evidence of a compromised machine on their networks in the past 30 days.
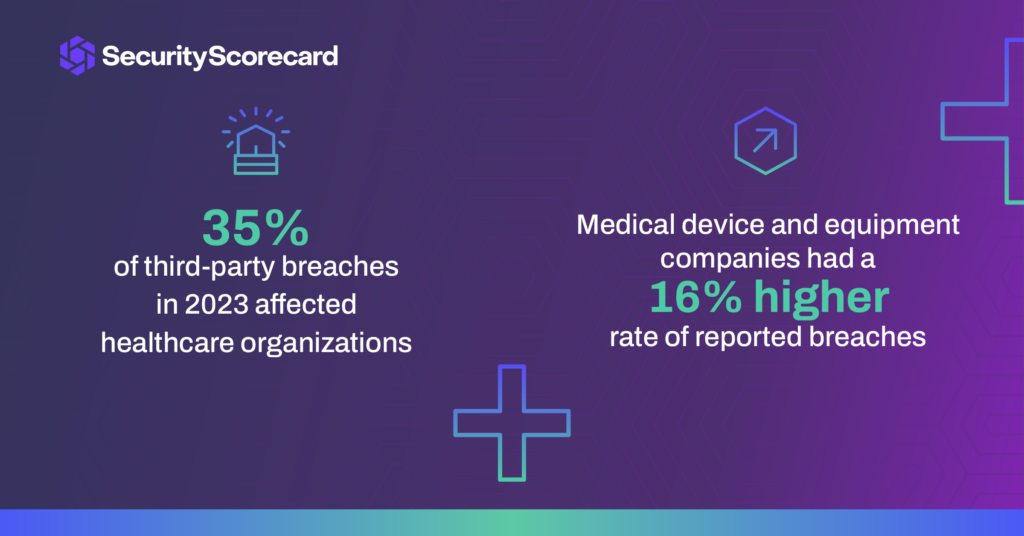
Medical device organizations have a higher risk of compromise
Medical device manufacturers and vendors of medical equipment and supplies scored 2-3 points lower than those of the overall healthcare sample. These organizations also had a 16% higher rate of reported breaches and compromised machines than those in other healthcare sectors. We attribute this to differences in their attack surfaces, some of which may resemble those of non-healthcare manufacturers more than those of other healthcare organizations.
Historically, security professionals have focused on medical devices as particularly vulnerable components of the attack surface of care providers, such as hospitals. Our findings warrant a more expansive view of cyber risks associated with the manufacturers of these devices, along with other vendors of medical equipment and supplies. As members of the only sector of the healthcare industry with noticeably lower scores in our sample, they warrant greater scrutiny from the third-party risk management (TPRM)/vendor risk management (VRM) teams of organizations in other sectors of the healthcare industry that do business with them. Such TPRM/VRM scrutiny should expand beyond the traditional focus on vulnerabilities in medical devices and the frequent difficulty of patching them to consider other risks, such as:
- the compromise of PHI/PII for the patients of care providers that receive devices from these vendors, as in the case of TransMedics;
- the exposure of billing and other financial details in transactions with these vendors;
- the potential use of any compromised infrastructure of these vendors as an attack vector against their customers; and
- medical supply chain disruptions that could result from ransomware attacks on these vendors
AppSec is the biggest attack surface threat
Application security issues are among the most significant flaws in healthcare attack surfaces – with 48% of organizations scoring the lowest in this category. Endpoint security issues, specifically outdated web browsers, are a less common source of security risk, but their impact is more severe.
The number and breadth of Application Security issues that we found in our sample makes it hard to pin down more specific areas for improvement, beyond that general rubric. Nonetheless, many Application Security issues that our platform factors into its scoring come from an organization’s public-facing website, so that would be a good place to start. Frequent testing, audits, and reviews can catch many problems, and our platform is also useful for self-monitoring, not just monitoring one’s vendors. In contrast, the solution to the one Endpoint Security issue that stood out in our findings is quite clear: require and enforce frequent web browser updates.
Final thoughts
Just last week, it emerged that cyberattacks on America’s healthcare system rose a staggering 128% in just one year. This is most likely because this field in particular has more numerous, diverse, and specialized third-party relationships that enable third-party breaches. But healthcare is also a prime ransomware target for another major reason: because of the critical nature of their business, healthcare operators can’t afford to have life-saving services taken offline for long periods of time, and are more likely to pay ransoms to get back up and running quickly.
A proactive approach to increasing the cyber resilience of critical infrastructure is necessary to ensure the continued delivery of vital services. And the move towards metrics, regulations, and strengthening the supply chain all point to a more secure future. One where all stakeholders will benefit by improving their individual cybersecurity health for the sake of the greater good. With a more transparent and measurable view of cyber risk, critical infrastructure institutions can not only become more sustainable but preserve trust as well.