Operation 99: North Korea’s Cyber Assault on Software Developers
On January 9, the SecurityScorecard STRIKE team uncovered Operation 99, a cyberattack by the Lazarus Group, North Korea’s state-sponsored hacking unit. This campaign targets software developers looking for freelance Web3 and cryptocurrency work. If you thought fake job offers from the group’s Operation Dream Job campaign were bad, this latest move is a masterclass in deception, sophistication, and malicious intent.
Here’s why Operation 99 demands your attention.
Why Software Developers? Why Now?
Developers are the backbone of tech innovation, particularly in Web3 and cryptocurrency. Targeting them starts a ripple effect of compromised individual systems through the supply chain. Operation 99 takes advantage of this dynamic, exploiting trust within developer communities.
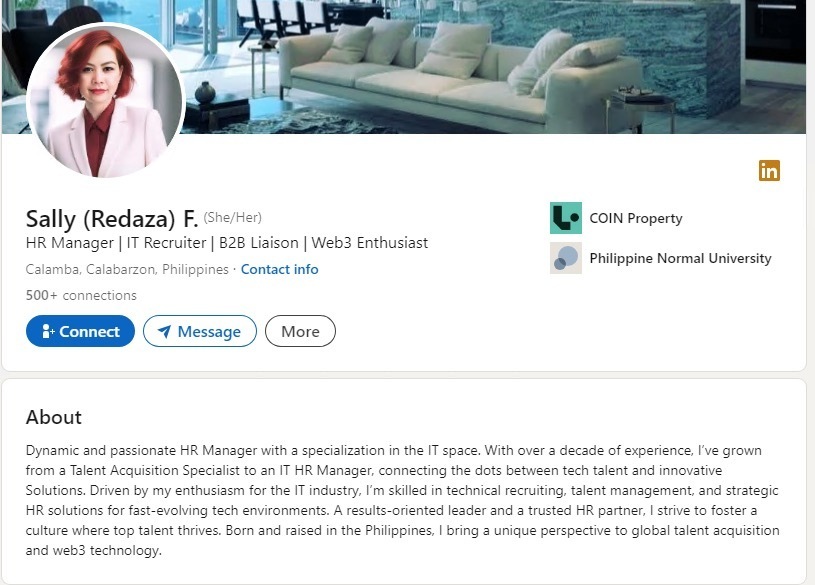
The campaign begins with fake recruiters, posing on platforms like LinkedIn, luring developers with project tests and code reviews. Once a victim takes the bait, they’re directed to clone a malicious GitLab repository—seemingly harmless, but packed with disaster. The cloned code connects to Command-and-Control (C2) servers, embedding malware into the victim’s environment.
The Lazarus Group’s New Arsenal
1. Modular Malware: A Shape-Shifting Threat
The attack features a multi-stage malware system with modular components. These include:
- Main99: A downloader that connects to C2 servers, retrieving additional payloads.
- Payload99/73: Implants capable of keylogging, clipboard monitoring, and file exfiltration.
- MCLIP: A dedicated implant for keyboard and clipboard monitoring.
This modular framework is as flexible as it is dangerous. It works across platforms—Windows, macOS, and Linux—embedding itself into developer workflows with surgical precision. By adapting malware to each target, the Lazarus Group ensures maximum impact with minimum detection.
2. Advanced Command-and-Control Infrastructure
The C2 servers for Operation 99 are hosted by “Stark Industries LLC”, deploying heavily obfuscated Python scripts. These scripts compress data using ZLIB and tailor payloads to specific victims, making detection nearly impossible. By dynamically adjusting the malware, the attackers maintain a persistent connection to the victim’s system while keeping their activities under the radar.
3. Targeting High-Value Data
What’s the endgame? Yes, it’s about disruption; it’s about theft—intellectual property, sensitive configurations, and cryptocurrency wallet keys. These attackers want it all:
- Source Code: Exploiting repositories to siphon intellectual property.
- Secrets: Configuration files, API keys, and credentials.
- Cryptocurrency: Wallet keys and mnemonics, often worth millions.
For a regime desperate for funds, this combination of intellectual property theft and financial fraud is a perfect storm.
Not Their First Rodeo: Building on Past Attacks
The STRIKE team’s analysis connects Operation 99 to earlier campaigns. Back in October 2024, a similar attack targeted developers, using comparable malware hosted on C2 servers. However, the January 2025 campaign reveals key upgrades:
- No Self-Destruction Mechanism: Unlike earlier implants, these don’t self-delete after execution, allowing attackers to maintain longer access.
- Refined Obfuscation: A 65-layer encoding scheme ensures payloads remain hidden, even during forensic analysis.
- Enhanced Modularity: The introduction of new endpoints, such as /payload, /brow, and /mclip, adds depth to the attack.
Digging Into the Details: How the Malware Works
Main99 and Main5346
These are the backbone of the operation. Main99 acts as a lightweight downloader, while Main5346 is its more robust counterpart. Both download and execute payloads tailored to the victim’s operating system. The implants stored in hidden directories (~/.n2) ensure persistence.
Payload99/73
This implant collects system data—operating system details, usernames, and UUIDs—and establishes a persistent connection to the C2 server. It supports commands to:
- Exfiltrate files.
- Upload clipboard data.
- Terminate browser processes like Chrome and Brave.
- Execute arbitrary scripts, enabling further attacks.
Brow99/73
Designed for browser credential theft, this implant is highly adaptable:
- Windows: Extracts AES keys via win32crypt.CryptUnprotectData.
- Linux: Accesses GNOME keyring for browser decryption.
- macOS: Retrieves passwords using the Keychain.
The result? Access to saved passwords and encrypted browser data.
MCLIP
This implant monitors and exfiltrates keyboard and clipboard activity. Captured data is sent to the C2 server in real time, allowing attackers to harvest sensitive information like credentials and API keys.
Deception at Its Core
Operation 99 thrives on deception. From fake recruiters with polished LinkedIn profiles to malicious repositories masquerading as legitimate projects, every element is designed to exploit trust. The STRIKE team uncovered one repository claiming to support a “coin voting and promotion system,” which lured developers into cloning malware-laden codebases.
By the time victims realized they’d been duped, their systems—and often their organizations—were compromised.
The Bigger Picture: Lazarus Group’s Financial Motive
For North Korea, hacking is a revenue generating lifeline. The Lazarus Group has consistently funneled stolen cryptocurrency to fuel the regime’s ambitions, amassing staggering sums. With Web3 and cryptocurrency industries booming, Operation 99 zeroes in on these high-growth sectors. In fact, a recent report reveals North Korea stole $1.34 billion in cryptocurrency just last year, cementing its place as a global cybercrime powerhouse.
The campaign’s focus on developers reflects a strategic evolution. By compromising the creators of technology, the attackers indirectly jeopardize the projects and enterprises these developers support. It’s a devastatingly efficient method of supply chain attack.
What Can We Learn?
Operation 99 shows how vulnerable the tech industry is to targeted attacks. Defending against this type of threat means taking specific, actionable steps.:
- Vigilance Against Social Engineering: Verify recruiters and job offers on platforms like LinkedIn.
- Repository Security: Scrutinize Git repositories before cloning, especially when working in high-stakes sectors.
- Endpoint Protection: Use advanced endpoint security solutions to detect unusual activity.
- Training and Awareness: Equip developers with the knowledge to identify red flags in emails, repositories, and LinkedIn profiles.
Closing Thoughts
The STRIKE team’s findings reveal an evolving strategy from one of the world’s most active threat actors. The Lazarus Group has upped its game, targeting developers with precision and leveraging malware frameworks designed for maximum adaptability.
Gain a deeper understanding of the tactics, techniques, and procedures behind Operation 99—and the steps you can take to stay ahead in STRIKE’s latest report. Developers are the first line of defense in this battle. Let’s make sure they’re equipped to fight back.






