Examining NIST CSF 2.0: Everything you need to know
In 2014, the National Institute of Standards and Technology (NIST) released its Cybersecurity Framework (CSF) following a presidential executive order to help organizations better understand, reduce, and communicate cybersecurity risk. In the decade since its introduction, NIST CSF has become one of the most widely recognized and utilized frameworks globally, built upon five key functions: Identify, Protect, Detect, Respond, and Recover.
Ten years later, NIST has now released Version 2.0 of its CSF. However, this is more than an update; it’s a major refurbishment of the standard that addresses the modern cyber threat landscape. While incorporating feedback and input from security and compliance professionals across the cybersecurity industry, Version 2.0 is aimed at organizations of all sizes and a greater variety of industry verticals.

What’s different about NIST CSF 2.0?
NIST CSF 2.0 encourages cybersecurity control implementation in a continuous fashion and is in line with the industry theme of ongoing policy improvement. Moreover, it helps to increase the realization for businesses that security, and control over security, are critical to understanding and measuring risk. There are many compelling changes to Version 2.0, as outlined below.
The most compelling changes in NIST CSF 2.0
The original version of the NIST CSF incorporated five key functions: Identify, Protect, Detect, Respond, and Recover. Version 2.0 has a new function: Govern. This is a strategic position for the framework, and emphasizes the growing importance of governance and compliance in cybersecurity.
Other changes to NIST include:
- The addition of cleaner language for a broader set of users.
- New, refined categories and subcategories to address the measurement of controls using a risk-based approach.
- Integration of data privacy throughout the sections.
- Help and guidance within other areas of the enterprise that haven’t had focus or scrutiny in the past version of the framework. It goes beyond critical infrastructure and includes recognition of the management and governance component of business as a player in security policy and maintenance.
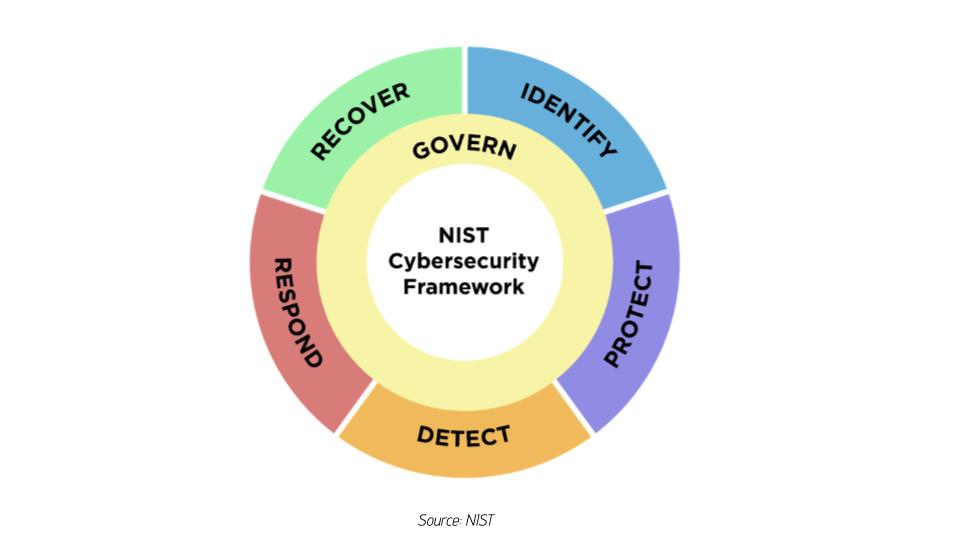
The new Governance category will bring a wider swath of a business and its management levels into the cybersecurity policy role who will be more responsible to answer on the company’s enterprise risk management posture. This follows other recent regulations, namely from the Securities and Exchange Commission (SEC), which mandates disclosure and analysis of the security leadership function, its roles, and responsibilities, as well as its components as a mandatory function in the wake of a security incident. It’s also worth pointing out that it’s been a year since the White House unveiled its National Cybersecurity Strategy, which was transformational in its data-driven approach to cybersecurity.
Sections and breakdown of the NIST CSF 2.0:
- CSF Core Framework: A listing of cybersecurity activities split across functions, categories, and subcategories, which provide a practical way to measure cybersecurity risks and policy.
- Organizational profiles: Customizable structures that allow organizations to align their cybersecurity actions, policy, and objectives to the CSF Core Framework, facilitating a custom approach to each businesses risk management and measurement procedures.
- Tiers: Priorities or levels that help apply a rating measuring the degree of enforceability and rigor of an organization’s cybersecurity risk management practices. This helps organizations align their individual or divisional cybersecurity practices around each security control with their risk management policy and objectives.
- Informative references: Guidelines and practices that outline how to achieve the business and technical outcomes defined in the NIST CSF Core framework.
Speeding up policy management
Auditors and security assessors will also benefit from NIST CSF 2.0, as the update accelerates the pre-gap analysis and information collection phase considerably. The approach within the new Govern section of the framework provides a template that will help to map out leadership roles and responsibilities and disclose the organizational policies and procedures. In the past, this necessary security assessment step was largely a manual process that lacked centralized guidelines and baselines. Moreover, the new guidance will provide a common template for both the business and the assessor/auditor to reference and use to measure security control risk against the cybersecurity policy. The new objectives will tighten up cybersecurity policy management as a whole.
The original NIST CSF was created to strengthen the cybersecurity of critical infrastructure, and the changes seek to harden it even more. Version 2.0 will have a positive influence, as the updated focus on controls to identify and triangulate security gaps and weaknesses will empower critical infrastructure to further enforce critical security controls that are often overlooked or periodically analyzed. The new framework, however, can also be adapted to apply to any sector.
Using metrics to optimize reporting
A controlled, proactive, and continuous baseline of the enterprise will help businesses get a head start on complying with the framework by disclosing an immediate control baseline realization and control. With the new Governance section of NIST CSF 2.0 framework, there is a requirement to map out the relation to the organizational policies and responsibilities against the enterprise stack. Having a complete and dynamic telemetry of systems (enterprise and third party) with their status across the enterprise complete with all associations will speed up the completion of the requirements in that section of the CSF.
There is also a further move towards continuous measurement of the security gaps within the business. Having a quick report on not only the changing risk of security vulnerabilities, but a full triangulation on how they are interrelated (or missing components and controls all-together), will enable risk managers to prove their ranking with irrefutable data.
Board reporting is another area where NIST shines. The relationship between Chief Information Technology Officers (CISOs) and boards typically involves stakeholders with very different backgrounds. While CISOs deal with technical details, boards assess business risk in financial terms. Bridging this gap is possible by ensuring that boards understand the cybersecurity frameworks in use—this is where NIST plays a key role. CISOs can then map key risk and performance indicators to these frameworks, making cyber risks tangible to the board.
Final thoughts
The NIST Cybersecurity Framework has a transformative approach when it comes to securing digital assets and our most critical infrastructures. And in the rapidly-expanding landscape of cyber threats, this new iteration is a welcome next step.
Stay tuned for more resources regarding NIST CSF 2.0 and other compliance-related topics. And check out our recent webinar, “How Cybersecurity Leaders are Navigating SEC Mandates.”






