6 Myths About Cybersecurity Ratings (and 1 Truth): The Current State Of The Cybersecurity Ratings Industry And Where It Can Improve
Today, electricity is so ubiquitous that it’s difficult to perform even basic tasks without it. But when electricity was first introduced, it took decades for broad acceptance and adoption because it was misunderstood and misused. Slowly, the benefits began to outweigh the cons.
As with any innovation, there are setbacks, but electricity has overwhelmingly been a force for good. The same can be said about cybersecurity risk ratings. Are they perfect? No. But they can make the world safer — that is, if they are understood.
The lightbulb moment
Years ago, when I was the CISO at Gilt Groupe, I signed with a SaaS vendor who submitted a pen test report by one of the large, top 4 accounting firms.
After discovering unencrypted credit card information, I had an “aha” moment. I had no visibility into my own organization’s security posture or that of my partners.
The security industry needed to evolve. The world needed a standardized measure of cyber health, with meaningful metrics and KPIs. This is what sparked the idea for SecurityScorecard security ratings.
Cybersecurity trust and transparency
With cyberattacks on the rise, there’s now a greater emphasis on measuring cybersecurity and the need for a more transparent approach to cyber health. The White House’s new National Cybersecurity Strategy explicitly calls for a “data-driven” approach to cybersecurity. Forthcoming cyber regulations from the SEC, the EU’s (DORA), NIS-2, and France’s Cyberscore Law all seek to provide visibility about the cyber hygiene of organizations across multiple critical infrastructure sectors. You can’t fix what you can’t measure. Quite simply: metrics matter.
Cybersecurity ratings are instrumental in providing transparency into cybersecurity risk, which increases trust between board members, insurers, regulators, and vendors. While security ratings have room for improvement (like any technology), they can also be misunderstood. With that in mind, the most common myths about cybersecurity ratings are below.

1. Myth #1: Cybersecurity ratings are “pay to play”
There are a few big misconceptions regarding cybersecurity ratings:
- One myth is that an organization has to pay to access a rating in the first place.
- The other myth is that an organization has to pay a fee (e.g., subscribe to the SaaS service) to improve or challenge its rating.
False. Organizations can see their scores for free.
With any reputable cyber rating company, any organization can access its scorecard for free and annotate it with internal information (such as SOC2 documentation and compliance certifications) to ensure its voice is heard.
In turn, we share recommendations on how they can improve to an “A” and become more resilient. SecurityScorecard is not perfect, and attribution can be a difficult undertaking. However, if we get it wrong, we work with the affected organization to correct errors. This can all be done free of charge.
To encourage confidence in security ratings, the U.S. Chamber of Commerce established an industry-wide approach called the Principles for Fair and Accurate Security Ratings. It states that “any rated organization will be able to see and challenge their rating irrespective of whether they are a customer of the rating company.” These are lofty goals to aspire to, and SecurityScorecard works diligently to align with them.
2. Myth #2: Cybersecurity ratings are inaccurate and ratings companies collect low-fidelity data only to calculate score
There is an assumption that security ratings are created by scanning the Internet with open-source (OSINT) tools and publishing ratings without first sanitizing data. This is incorrect.

Combining all of this data in a concise, meaningful, and actionable way is the power of our platform. Particularly, the breadth and fidelity of our data is on par with Attack Surface Management (ASM) products on the market. Our data is searchable and actionable for Security Operations to protect their organizations. Many customers use our Attack Surface Intelligence (ASI) to proactively find issues on their own attack surface and that of their vendors. And SecurityScorecard can show that organizations with poor security ratings are more likely to get hacked. However, some risk corridors have limitations, such as:
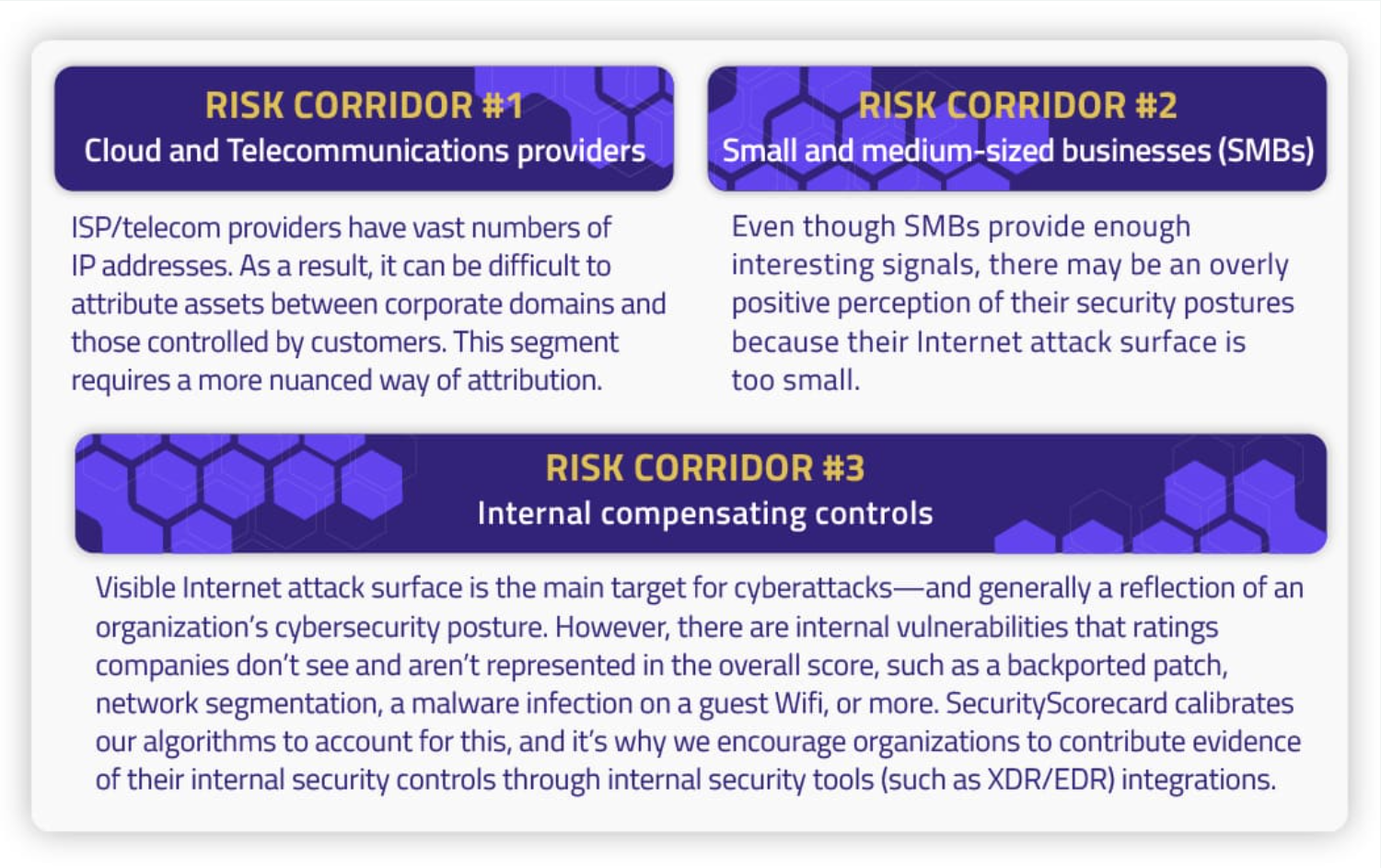
3. Myth #3: Your rating doesn’t reflect my entire security posture. What about my internal security?
An organization’s digital footprint can often indicate internal security issues. Due to the volume of data across ten factors, SecurityScorecard’s platform provides unparalleled context into an organization’s holistic cybersecurity risk. For instance, SecurityScorecard can measure how diligently a browser’s operating system is patched or the reaction time to malware. Wide and deep outside-in scanning can identify trending security issues that can help you tune your other tools, such as next-gen firewalls and EDR solutions. By gaining visibility into new exploits, you enhance your security arsenal before it becomes an issue.
Cybersecurity ratings become more accurate when organizations supplement their scorecards with the following types of inside-out information:
- Technical: Customers can list network designations; their security policies and procedures; points of contact; and the name of their CISO.
- Compliance: Customers can provide documentation to support compliance with SOC2, payment card industry (PCI) standards, HIPAA, and more.
- Views and opinions: Customers can provide feedback to inform us if something is incorrect. In turn, we investigate and make it right.
4. Myth #4: My company is too small to benefit from security ratings, and we already do pen testing.
When it comes to cybersecurity ratings, size doesn’t matter: whether your organization has one IP address or one million, our cybersecurity ratings are designed to find signals on any company, big or small. It costs nothing to manage a security rating — what’s more, your organization probably has a score already associated with it, so it’s in your best interest to manage it.
Organizations use paid penetration tests (pen tests) to test their systems for exploitable vulnerabilities. While this provides a point-in-time snapshot of your cybersecurity posture, continuous outside-in monitoring provides deeper insight across all your external-facing systems and assets to see what hackers see.
“For ratings of any kind there is always a level of angst about rating accuracy. Most organizations that are rated on anything devote time and effort to manage these ratings. They also establish industry-wide governance to shape the production and use of ratings.…it can often make simple economic sense to make sure your rating is as accurate as it can be — or at least not inaccurate.” -Phil Venables, Chief Information Security Officer, Google Cloud Source
5. Myth #5: It’s unclear how ratings work, and they’re too difficult to challenge
Not all cybersecurity ratings are created equal. Some providers have gaps in their offerings, which has increased confusion about the industry as a whole. At SecurityScorecard, we fundamentally believe that reputable ratings services must be: grounded in robust data, open about their methodology, and responsive to data validation questions and requests. Here are the areas where SecurityScorecard stands out:
- Quality of data: By collecting the right data points in the highest fidelity possible, security practitioners can have peace of mind when making critical decisions. SecurityScorecard has built and maintained our own scanning infrastructure, and we own 97% of our data. We scan 4.1B IPs every 1.5 weeks across 1,400 ports globally, with honeypots in over 65 countries and 120 distinct sensors that grab hundreds of millions of active attacks daily. This enables us to continuously monitor over 12 million organizations, track over 10,000 high-severity CVEs, and detect over 100 Billion vulnerabilities and attributions each week.
- Transparency: SecurityScorecard has a trust portal that explains the methodology behind our data, how scores are created, and our accuracy metrics. Not all providers do this. We invite customers and non-customers alike to visit this page and discover for themselves just how we operate.
- Refute process: None of our users go it alone, and if you believe your score is inaccurate, we work with you to make it right. We offer a simple, collaborative, and straightforward process that is equally open to customers and non-customers. We encourage users to validate and make corrections as needed.
6. Myth #6: An organization with an “F” score will be breached & one with an “A” score won’t
Much like credit ratings, security ratings package risk into a handful of quantifiable factors. We conducted a study with the Marsh McLennan Global Cyber Risk Analytics Center and found seven factors that drive cyber risk and can be predictive of a breach, including endpoint security; patching cadence; ransomware score; DNS health; IP reputation; cubit score; and network security.
Credit ratings are predictive of how likely a borrower is to pay back a loan in time. Hhowever, they can’t guarantee that the borrower won’t default. If a determined group of hackers or a nation-state decides to target an organization — even one with an “A” rating — it will get breached. Conversely, plenty of organizations with an “F” rating haven’t been breached because they’ve either flown under the radar or might not have anything hackers want to target. That said, organizations with poor security ratings are 13.8 times more likely to experience a breach.
“I take the view that we should not only live with [ratings], but work together to improve them because the wider use of even marginally accurate ratings will be a net positive over time.” -Phil Venables, Chief Information Security Officer, Google Cloud Source
TRUTH: Ratings are not the only security technology that you need
SecurityScorecard doesn’t claim to be a substitute for all security technologies; ratings are not a silver bullet. The industry is still evolving, but ratings are an important start because they are a universal and easy-to-understand measurement for cybersecurity.
In fact, using more than one cybersecurity ratings service can provide valuable alternative views of your cyber posture. For example, banks and lenders use more than one credit bureau (S&P, Moody’s, and Fitch), which calculates and processes information differently, thus providing a more complete view of creditworthiness.
Beyond ratings, organizations should make other investments in their security programs including intelligent firewalls; zero trust & cloud security solutions, Extended Detection & Response (XDR); and Security Automation (SOAR) technologies, among others.
Some believe pen testing, security audits, and tabletop exercises are sufficient. However, security ratings supplement these efforts by measuring and scaling risk continuously.
No single security team has the time and resources to keep tabs on all of its third and fourth-party vendors. SecurityScorecard provides a way to validate and assess vendors at scale. Furthermore, cybersecurity ratings enhance board reporting because they help security practitioners communicate risk in easy-to-understand financial terms. Additionally cybersecurity ratings help organizations obtain lower cyber insurance quotes, and insurers use ratings to evaluate risk more accurately.
Conclusion
In this increasingly digital world, there is a growing need for a standardized metric to measure the cyber health of organizations and protect digital supply chains. SecurityScorecard’s mission is to make the world a safer place, and cybersecurity ratings are a transparent and consumable way to understand cyber risk and quantify trust.
But not all ratings vendors offer the same level of transparency. Its up to each organization to conduct their due diligence on a ratings vendor by assessing: their scoring methodology; data quality; refute process; third-party validation; insurance and regulatory industry adoption; and adherence to the U.S. Chamber of Commerce Principles for Fair and Accurate Ratings.
Security ratings are in their teenage years. While there has been significant progress, more growth and maturity is still to come. As the CEO of SecurityScorecard, I fundamentally believe in the importance of industry dialogue and debate as a means to help drive innovation in this space. And I welcome any opportunity to shed light on these vital issues.
I’d like to hear from you. Do you believe that more dialogue and transparency are needed in the security space today? I welcome your perspective.
Email me at [email protected]




