Introducing MAX — Take supply chain cyber risk management to the MAX
BlackCat Ransomware Group Claims Attack on Healthcare Service Provider

Executive Summary
- On January 17, the BlackCat ransomware group added an entry for an electronic health record (EHR) vendor to its extortion site., Bbut, as of January 21, the vendor’s entry no longer appeared there.
- Following the claim, the SecurityScorecard Threat Research, Intelligence, Knowledge, and Engagement (STRIKE) Team investigated the incident.
- By pairing its exclusive access to traffic data with public reporting on BlackCat’s tactics, techniques, and procedures (TTPs), STRIKE identified possible evidence of BlackCat-affiliated activity on target IP addresses.
- This evidence may reflect the use of the BlackCat group’s exfiltration tool, ExMatter/Fendr, on the vendor’s systems but suggests that the scope of the activity was relatively limited.
Background
On January 17, the BlackCat ransomware group added an entry for a major U.S. electronic health record (EHR) vendor to its extortion site.
Image 1: BlackCat added an entry for an EHR vendor to its data leak site on January 17 (source: DataBreaches.net).
On January 19, the vendor responded to these claims, reporting that they had observed no evidence that attackers had accessed customer data but noting that an investigation was ongoing. As of January 21, the vendor’s entry no longer appeared on BlackCat’s data leak site.
The BlackCat ransomware-as-a-service operation, also known as ALPHV, first surfaced in November 2021. It is widely understood to be a successor to the BlackMatter operation, which succeeded the DarkSide ransomware group and achieved widespread notoriety for its role in the Colonial Pipeline attack.
Since its appearance, the group has targeted U.S. organizations particularly heavily, including local governments and educational institutions. Although a spokesperson for BlackCat has declared that the group would not target medical institutions, the U.S. Department of Health and Human Services (HHS) identified BlackCat as a threat to the health sector on January 12.
Findings: Suspicious Traffic to Remote Access Service
When collecting traffic data for the affected organization, STRIKE researchers created a query dedicated to sampling traffic involving the IP addresses where remote access services appeared to be in use. Previous research has noted that BlackCat affiliates have sometimes leveraged compromised credentials to use remote access services for initial access to target organizations. STRIKE identified three vendor subdomains that suggested the use of such services and then collected traffic data involving the IP addresses hosting those subdomains to identify communications that may suggest attempts to compromise these services.
Between November 26 and January 17, forty-five unique IP addresses communicated with the two IP vendor addresses hosting remote access services. Of those, the vendors contributing to VirusTotal detected twenty-seven as malicious. One of these, 195.176.3[.]23, may be particularly likely to have been involved in an initial access attempt. It and a target company IP address communicated on December 3.
Members of the VirusTotal community have identified 195.176.3[.]23 as a TOR exit node and observed it in recent credential-stuffing attacks. In general, it is common for threat actors to use TOR to conceal the origins of their traffic. Still, this IP address’s recent involvement in credential-stuffing is particularly noteworthy, given that that is a tactic BlackCat affiliates have employed in previous attempts to access remote services.
Findings: Additional Traffic Data
In addition to the traffic to remote access services, researchers also collected a wider sample of traffic to and from all the IP addresses where SecurityScorecard’s ratings platform observed issues affecting the target organization’s security. Researchers consulted this traffic sample to identify other suspicious traffic that may reflect BlackCat activity leading up to and following suspicious communication with the remote access service on December 3.
Findings: Possible Reconnaissance
As a hypothesis accompanying the one that the suspicious traffic to the remote access service involved an attempt to authenticate it using compromised credentials, STRIKE investigated traffic from the weeks leading up to December 3 to identify evidence of possible reconnaissance that could have facilitated that access attempt.
Attackers could have acquired credentials through phishing or by infecting an employee device with information-stealing malware. Researchers sought out traffic that may reflect such activity. Between November 19 (the first day traffic data was available) and December 3, vendor-attributed IP addresses communicated with 374 unique IP addresses, of which cybersecurity vendors have linked 120 to malicious activity.
Much of the data involving these IP addresses indicates short, one-off transfers of small amounts of data, which likely reflects low-level scanning and probing activity unrelated to the claimed attack.
However, researchers did identify twelve IP addresses engaged in repeated communication with the vendor network, which may reflect more sustained malicious activity that enabled later stages of the attack. These IP addresses are available in an appendix below.
Findings: Traffic Data Suggesting Use of ExMatter
While reviewing the traffic data they collected, STRIKE researchers observed evidence that may reflect the deployment, or attempted deployment, of the BlackCat group’s exfiltration tool (ExMatter/Fendr) on the vendor’s network.
Previous research into ExMatter has found that it hosted most of its command and control (C2) infrastructure on DigitalOcean IP addresses and exfiltrates data to a remote server over port 22. Knowing this, STRIKE first filtered its traffic sample by port, identifying 957 flows over port 22. These involved 404 IP addresses from outside the vendor’s network. A majority (341) of those IP addresses belong to Digital Ocean.
Researchers then consulted SecurityScorecard’s Attack Surface Intelligence (ASI) tool to identify the DigitalOcean IP addresses capable of acting as a remote server. Those IP addresses would have port 22 open (or a similar port running SSH services, such as ports 2222 and 8222) was open, suggesting that the IP address could have been used to establish a tunnel with the vendor IP addresses involved in this traffic over port 22. ASI revealed port 22, 2222, or 8222 to be open at 328 of the 341 DigitalOcean IP addresses, suggesting they were possible exfiltration destinations.
ASI additionally revealed that port 22 was open at both vendor-attributed IP addresses involved in this traffic, which indicates that exfiltration from port 22 of those IP addresses would be feasible. This bears noting because it may help differentiate this traffic from scanning, which can often attempt to contact IP addresses at port 22, even when it is closed, simply to identify IP addresses where it is open.
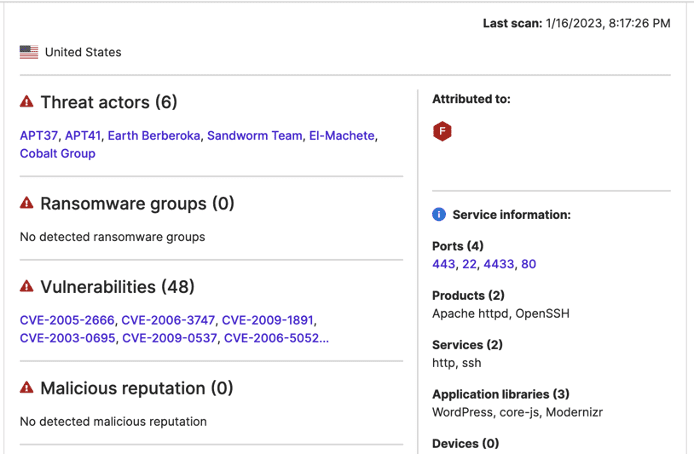
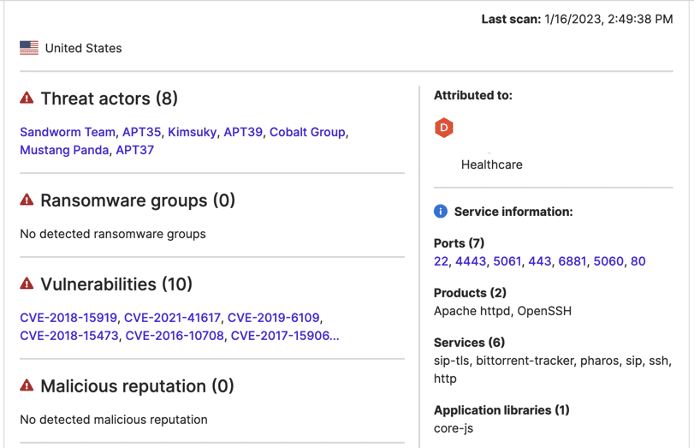
Images 2-3: ASI found port 22 to be open, and vendor IP addresses were observed communicating with suspicious external IP addresses.
Of 404 IP addresses communicating with vendor assets over port 22, 341 belong to DigitalOcean. Of those, ASI found port 22 (or similar ports running SSH services, such as ports 2222 and 8222) to be open at 328, suggesting that they could have been used to establish a tunnel with port 22 of the vendor IP addresses involved in this traffic.
Conclusion
While the traffic data may reflect the use of ExMatter on the vendor’s systems, this traffic constitutes a comparatively small portion of the total traffic sample. The relatively low traffic volume may therefore indicate either that the group’s exfiltration attempts were unsuccessful or that they resulted in the theft of a relatively small amount of data.
As of January 21, the affected vendor claims not to have observed evidence that the attackers exfiltrated client data and the company’s entry no longer appears on BlackCat’s breach site, which raises three possibilities: that negotiations are ongoing, successfully concluded, or that the group’s claim was false or exaggerated and that it has retracted it when confronted with this fact.
While BlackCat does not have as prominent a public record of making false or exaggerated claims as other ransomware groups, it would not be unheard of for a threat actor to assert that a breach was more significant than it actually was. While some data available to SecurityScorecard suggests activity resembling previous BlackCat TTPs, it does not necessarily indicate the successful encryption or exfiltration of data from the target organization. It may, however, help inform future efforts to defend against BlackCat and other ransomware operations by identifying assets those groups may use, like the suspicious IP addresses listed in the appendices below.
APPENDIX: IP ADDRESSES INVOLVED IN POSSIBLE RECONNAISSANCE
- 89[.]203[.]251[.]217
- 195[.]176[.]3[.]20
- 128[.]199[.]196[.]6
- 195[.]176[.]3[.]24
- 195[.]176[.]3[.]23
- 45[.]64[.]156[.]212
- 45[.]64[.]156[.]213
- 45[.]64[.]156[.]214
- 138[.]197[.]75[.]72
- 157[.]245[.]57[.]169
- 27[.]0[.]182[.]115
- 68[.]235[.]38[.]50
APPENDIX: POSSIBLE EXFILTRATION TARGETS
- 104[.]248[.]153[.]95
- 138[.]197[.]32[.]150
- 134[.]209[.]212[.]125
- 157[.]230[.]178[.]127
- 167[.]71[.]16[.]200
- 161[.]35[.]125[.]167
- 157[.]230[.]53[.]66
- 137[.]184[.]55[.]79
- 128[.]199[.]210[.]191
- 167[.]99[.]135[.]53
- 128[.]199[.]233[.]192
- 159[.]223[.]50[.]39
- 157[.]230[.]237[.]83
- 128[.]199[.]163[.]55
- 157[.]230[.]113[.]181
- 178[.]62[.]205[.]28
- 46[.]101[.]171[.]235
- 128[.]199[.]129[.]68
- 134[.]209[.]175[.]24
- 159[.]223[.]179[.]50
- 159[.]223[.]235[.]198
- 165[.]227[.]166[.]247
- 139[.]59[.]249[.]123
- 159[.]223[.]86[.]231
- 128[.]199[.]249[.]246
- 159[.]65[.]127[.]239
- 104[.]236[.]228[.]230
- 104[.]248[.]56[.]93
- 178[.]128[.]39[.]97
- 157[.]245[.]207[.]191
- 134[.]209[.]69[.]41
- 143[.]198[.]125[.]15
- 157[.]230[.]228[.]27
- 142[.]93[.]150[.]113
- 167[.]71[.]232[.]83
- 167[.]71[.]24[.]233
- 159[.]65[.]43[.]192
- 159[.]65[.]240[.]232
- 167[.]99[.]76[.]44
- 45[.]55[.]33[.]125
- 68[.]183[.]26[.]236
- 192[.]241[.]149[.]141
- 206[.]189[.]192[.]163
- 198[.]199[.]86[.]89
- 167[.]99[.]79[.]238
- 192[.]241[.]156[.]50
- 167[.]71[.]33[.]249
- 167[.]71[.]86[.]3
- 178[.]128[.]148[.]229
- 104[.]131[.]46[.]166
- 68[.]183[.]145[.]59
- 143[.]110[.]243[.]154
- 134[.]209[.]190[.]88
- 167[.]99[.]89[.]165
- 138[.]68[.]108[.]97
- 157[.]230[.]6[.]213
- 157[.]230[.]228[.]223
- 167[.]71[.]243[.]218
- 157[.]230[.]232[.]227
- 139[.]59[.]224[.]111
- 206[.]189[.]233[.]82
- 64[.]225[.]22[.]216
- 165[.]227[.]64[.]201
- 68[.]183[.]230[.]224
- 143[.]198[.]209[.]48
- 206[.]189[.]198[.]237
- 167[.]172[.]148[.]74
- 209[.]97[.]183[.]120
- 159[.]203[.]129[.]103
- 164[.]92[.]177[.]69
- 159[.]65[.]34[.]202
- 68[.]183[.]79[.]205
- 104[.]248[.]30[.]183
- 159[.]89[.]176[.]200
- 138[.]197[.]138[.]123
- 165[.]232[.]69[.]156
- 174[.]138[.]21[.]174
- 128[.]199[.]32[.]98
- 143[.]198[.]165[.]210
- 139[.]59[.]102[.]10
- 159[.]223[.]168[.]165
- 159[.]223[.]96[.]209
- 167[.]71[.]250[.]96
- 164[.]92[.]158[.]95
- 128[.]199[.]77[.]201
- 159[.]223[.]38[.]244
- 159[.]223[.]74[.]73
- 157[.]245[.]218[.]29
- 167[.]71[.]108[.]81
- 134[.]209[.]32[.]88
- 138[.]68[.]72[.]245
- 162[.]243[.]233[.]102
- 178[.]62[.]214[.]246
- 161[.]35[.]24[.]136
- 167[.]71[.]196[.]217
- 178[.]128[.]35[.]197
- 159[.]203[.]66[.]111
- 68[.]183[.]26[.]35
- 164[.]90[.]164[.]106
- 134[.]209[.]127[.]189
- 206[.]189[.]130[.]185
- 159[.]65[.]205[.]214
- 164[.]90[.]191[.]216
- 164[.]90[.]194[.]61
- 167[.]99[.]126[.]215
- 206[.]189[.]184[.]66
- 142[.]93[.]194[.]20
- 164[.]92[.]155[.]137
- 159[.]203[.]81[.]114
- 206[.]189[.]83[.]207
- 188[.]166[.]121[.]147
- 137[.]184[.]148[.]244
- 142[.]93[.]100[.]226
- 143[.]198[.]123[.]124
- 159[.]203[.]42[.]233
- 165[.]227[.]193[.]194
- 167[.]172[.]142[.]20
- 167[.]172[.]150[.]24
- 157[.]230[.]63[.]218
- 192[.]34[.]56[.]83
- 138[.]197[.]66[.]68
- 167[.]71[.]160[.]75
- 142[.]93[.]112[.]39
- 165[.]227[.]175[.]44
- 164[.]92[.]154[.]145
- 188[.]166[.]41[.]217
- 178[.]128[.]103[.]172
- 161[.]35[.]177[.]39
- 167[.]99[.]239[.]101
- 164[.]92[.]130[.]239
- 164[.]92[.]143[.]10
- 159[.]203[.]113[.]193
- 128[.]199[.]105[.]111
- 157[.]230[.]50[.]22
- 46[.]101[.]157[.]187
- 159[.]203[.]179[.]230
- 167[.]172[.]159[.]73
- 159[.]223[.]55[.]81
- 64[.]227[.]190[.]199
- 157[.]230[.]107[.]204
- 139[.]59[.]93[.]234
- 162[.]243[.]165[.]205
- 68[.]183[.]15[.]55
- 188[.]166[.]30[.]235
- 128[.]199[.]113[.]183
- 188[.]166[.]233[.]207
- 142[.]93[.]123[.]107
- 161[.]35[.]113[.]114
- 146[.]190[.]27[.]250
- 159[.]223[.]125[.]135
- 159[.]223[.]107[.]98
- 128[.]199[.]162[.]2
- 37[.]139[.]3[.]151
- 146[.]190[.]222[.]132
- 206[.]189[.]200[.]15
- 147[.]182[.]169[.]107
- 24[.]199[.]89[.]201
- 157[.]230[.]233[.]185
- 161[.]35[.]115[.]224
- 147[.]182[.]128[.]252
- 137[.]184[.]141[.]4
- 146[.]190[.]77[.]120
- 46[.]101[.]49[.]191
- 167[.]172[.]246[.]83
- 165[.]232[.]176[.]114
- 143[.]244[.]162[.]174
- 139[.]59[.]12[.]104
- 159[.]223[.]120[.]180
- 206[.]189[.]57[.]56
- 134[.]122[.]106[.]122
- 134[.]209[.]147[.]154
- 137[.]184[.]154[.]154
- 165[.]22[.]101[.]75
- 159[.]223[.]145[.]181
- 157[.]230[.]1[.]224
- 159[.]223[.]167[.]92
- 146[.]190[.]72[.]85
- 142[.]93[.]54[.]142
- 159[.]223[.]92[.]205
- 167[.]71[.]239[.]9
- 165[.]22[.]25[.]189
- 157[.]245[.]140[.]49
- 159[.]89[.]93[.]16
- 161[.]35[.]113[.]6
- 162[.]243[.]172[.]35
- 167[.]99[.]15[.]190
- 46[.]101[.]24[.]113
- 206[.]81[.]14[.]65
- 64[.]225[.]48[.]16
- 159[.]65[.]220[.]18
- 157[.]230[.]2[.]208
- 159[.]89[.]225[.]100
- 139[.]59[.]230[.]111
- 206[.]189[.]226[.]38
- 159[.]65[.]181[.]179
- 68[.]183[.]105[.]14
- 128[.]199[.]45[.]37
- 192[.]241[.]157[.]126
- 159[.]223[.]62[.]113
- 167[.]99[.]243[.]12
- 159[.]223[.]59[.]42
- 159[.]223[.]62[.]234
- 67[.]205[.]170[.]38
- 206[.]189[.]44[.]140
- 137[.]184[.]196[.]76
- 134[.]209[.]162[.]114
- 67[.]207[.]85[.]118
- 159[.]223[.]43[.]149
- 146[.]190[.]228[.]94
- 159[.]203[.]76[.]174
- 67[.]205[.]142[.]48
- 142[.]93[.]62[.]53
- 206[.]189[.]113[.]160
- 162[.]243[.]61[.]162
- 159[.]89[.]155[.]205
- 159[.]89[.]170[.]8
- 147[.]182[.]145[.]89
- 161[.]35[.]21[.]48
- 157[.]230[.]218[.]88
- 134[.]209[.]153[.]48
- 159[.]65[.]180[.]64
- 128[.]199[.]242[.]7
- 157[.]245[.]129[.]95
- 188[.]166[.]162[.]47
- 157[.]230[.]228[.]78
- 157[.]230[.]236[.]83
- 157[.]230[.]9[.]57
- 134[.]122[.]87[.]22
- 159[.]65[.]232[.]117
- 159[.]65[.]28[.]184
- 164[.]92[.]232[.]134
- 159[.]223[.]96[.]208
- 128[.]199[.]208[.]187
- 147[.]182[.]190[.]189
- 178[.]128[.]159[.]65
- 159[.]223[.]102[.]145
- 157[.]230[.]58[.]191
- 188[.]166[.]146[.]208
- 157[.]245[.]135[.]50
- 142[.]93[.]186[.]29
- 165[.]22[.]99[.]177
- 68[.]183[.]105[.]114
- 104[.]236[.]111[.]25
- 139[.]59[.]127[.]178
- 139[.]59[.]27[.]154
- 137[.]184[.]96[.]200
- 128[.]199[.]133[.]168
- 138[.]68[.]99[.]110
- 138[.]197[.]180[.]166
- 165[.]227[.]114[.]124
- 157[.]245[.]142[.]116
- 68[.]183[.]100[.]78
- 165[.]22[.]59[.]95
- 142[.]93[.]14[.]124
- 178[.]128[.]108[.]91
- 139[.]59[.]126[.]129
- 157[.]230[.]45[.]177
- 206[.]189[.]95[.]224
- 167[.]172[.]98[.]89
- 159[.]65[.]11[.]5
- 198[.]199[.]76[.]150
- 178[.]128[.]220[.]159
- 143[.]198[.]191[.]25
- 157[.]245[.]216[.]197
- 167[.]99[.]232[.]11
- 206[.]81[.]6[.]88
- 157[.]245[.]142[.]175
- 164[.]92[.]135[.]0
- 167[.]172[.]253[.]42
- 159[.]223[.]139[.]68
- 157[.]230[.]209[.]3
- 139[.]59[.]120[.]240
- 165[.]227[.]123[.]201
- 104[.]236[.]78[.]19
- 157[.]245[.]137[.]143
- 142[.]93[.]178[.]56
- 157[.]230[.]239[.]179
- 134[.]122[.]20[.]244
- 159[.]223[.]96[.]213
- 143[.]198[.]45[.]196
- 104[.]131[.]40[.]97
- 104[.]248[.]62[.]102
- 165[.]22[.]102[.]152
- 192[.]241[.]172[.]175
- 198[.]211[.]123[.]150
- 64[.]225[.]25[.]59
- 137[.]184[.]57[.]26
- 162[.]243[.]162[.]45
- 134[.]122[.]119[.]113
- 167[.]99[.]157[.]92
- 139[.]59[.]23[.]154
- 165[.]227[.]118[.]71
- 104[.]131[.]55[.]236
- 137[.]184[.]145[.]62
- 104[.]236[.]118[.]222
- 64[.]227[.]188[.]127
- 137[.]184[.]69[.]227
- 139[.]59[.]231[.]120
- 68[.]183[.]104[.]78
- 162[.]243[.]48[.]133
- 64[.]227[.]126[.]250
- 159[.]203[.]181[.]214
- 159[.]203[.]83[.]104
- 206[.]189[.]130[.]158
- 165[.]227[.]68[.]95
- 162[.]243[.]237[.]90
- 104[.]248[.]138[.]141
- 68[.]183[.]221[.]15
- 159[.]65[.]12[.]104
- 139[.]59[.]104[.]150
- 207[.]154[.]220[.]120
- 167[.]172[.]144[.]33
- 165[.]22[.]208[.]145
- 206[.]81[.]4[.]81
- 178[.]128[.]94[.]184
- 206[.]189[.]133[.]24
- 164[.]90[.]210[.]8
- 143[.]198[.]39[.]194
- 188[.]166[.]230[.]84
- 165[.]22[.]59[.]229
- 178[.]128[.]98[.]121
- 134[.]122[.]17[.]178
- 178[.]128[.]102[.]42
- 142[.]93[.]50[.]8
- 46[.]101[.]44[.]93
- 143[.]198[.]161[.]95
- 159[.]65[.]205[.]178
- 159[.]89[.]87[.]72
- 146[.]190[.]79[.]123
- 134[.]122[.]8[.]241
- 165[.]227[.]204[.]174
- 164[.]92[.]152[.]140


