Introducing MAX — Take supply chain cyber risk management to the MAX

SecurityScorecard and CDW have partnered!
As a result of the partnership, all CDW customers can take advantage of:
- A complimentary SecurityScorecard Enterprise License that enables you to monitor your own organization as well as up to five vendors, suppliers, or competitors (the choice is yours).
- Customers who are already SecurityScorecard customers will be given the ability to monitor an additional five (5) third-parties at no additional cost.
To opt-in and take advantage of your complimentary access, fill out the form with your information.
*Offer terms may vary by region; contact [email protected] for details.

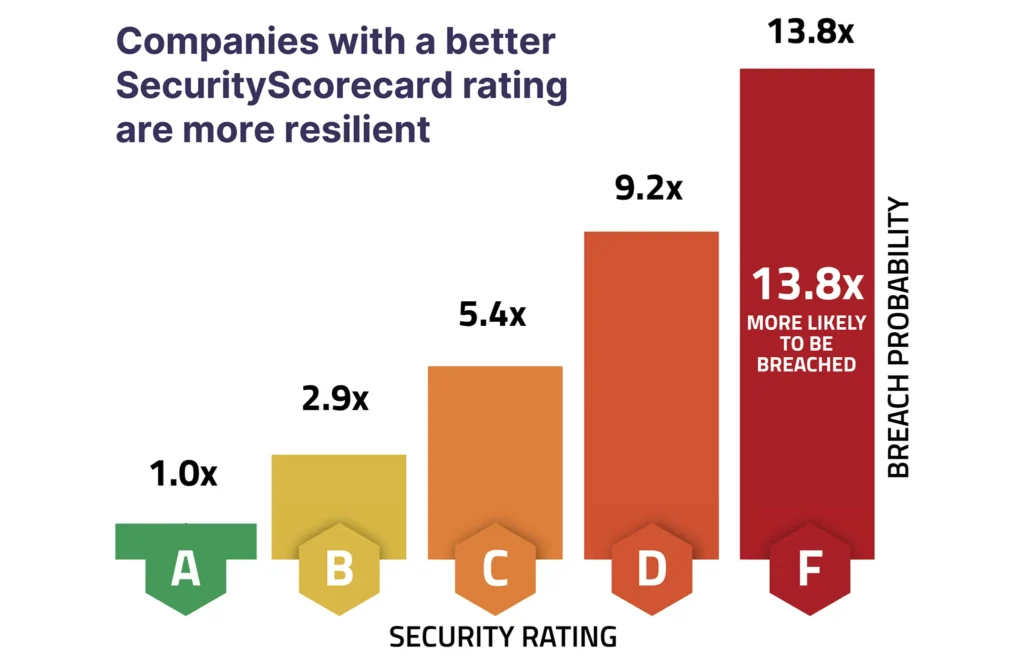
Evaluate any organization’s cybersecurity risk
SecurityScorecard Ratings evaluate an organization’s cybersecurity risk using data-driven, objective, and continuously evolving metrics that provide visibility into any organization’s information security control weaknesses as well as potential vulnerabilities throughout the supply chain ecosystem.